Login method, login verification method, corresponding device, and electronic device
A login method and login verification technology, applied in the login method, login verification method and corresponding devices, and electronic equipment fields, can solve problems affecting user information security, etc., and achieve the effect of avoiding account password leakage and ensuring personal information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
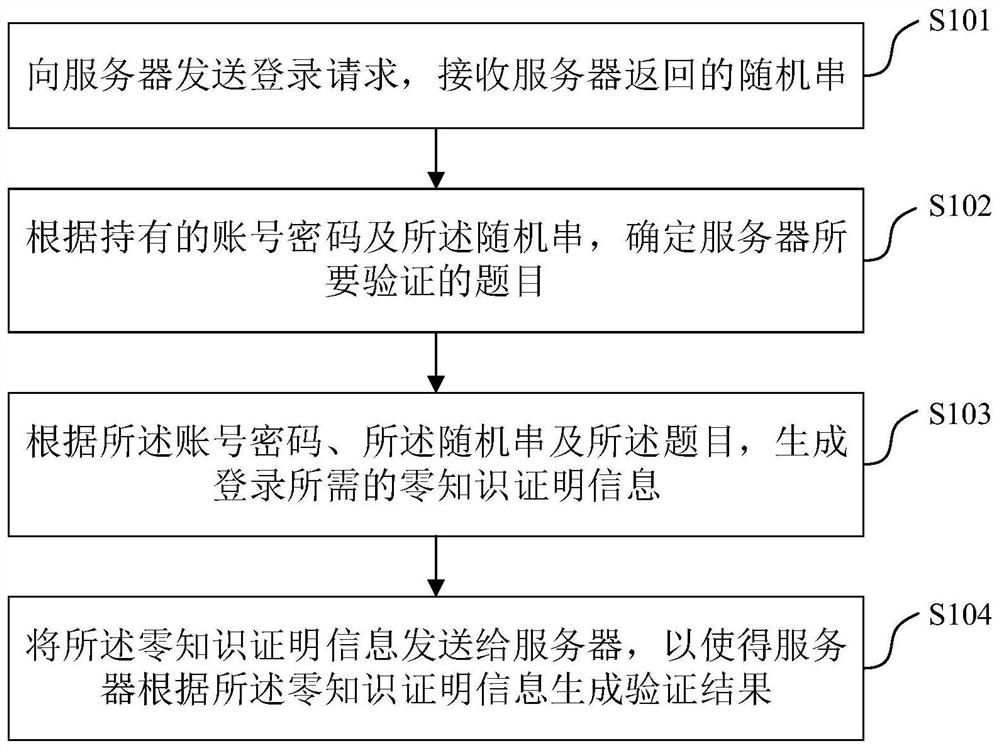
[0051] The embodiment of this application provides a login method, such as figure 1 As shown, the method includes:
[0052] Step S101: Send a login request to the server, and receive the random string returned by the server.
[0053] In this embodiment of the application, the method is executed by a client. In practical applications, the client may be an application program on an electronic device such as a computer, a tablet computer, or a mobile terminal, which is not limited in this embodiment of the application.
[0054] In this step, the login request sent by the client to the server may include user description information, such as address information, identity information, etc., so that the server can specify the client that needs to log in, and generate a random string to return to the client.
[0055] Wherein, besides random content, the random string can also be random in length, so that the random range can be further expanded without affecting the solution of the ...
Embodiment 2
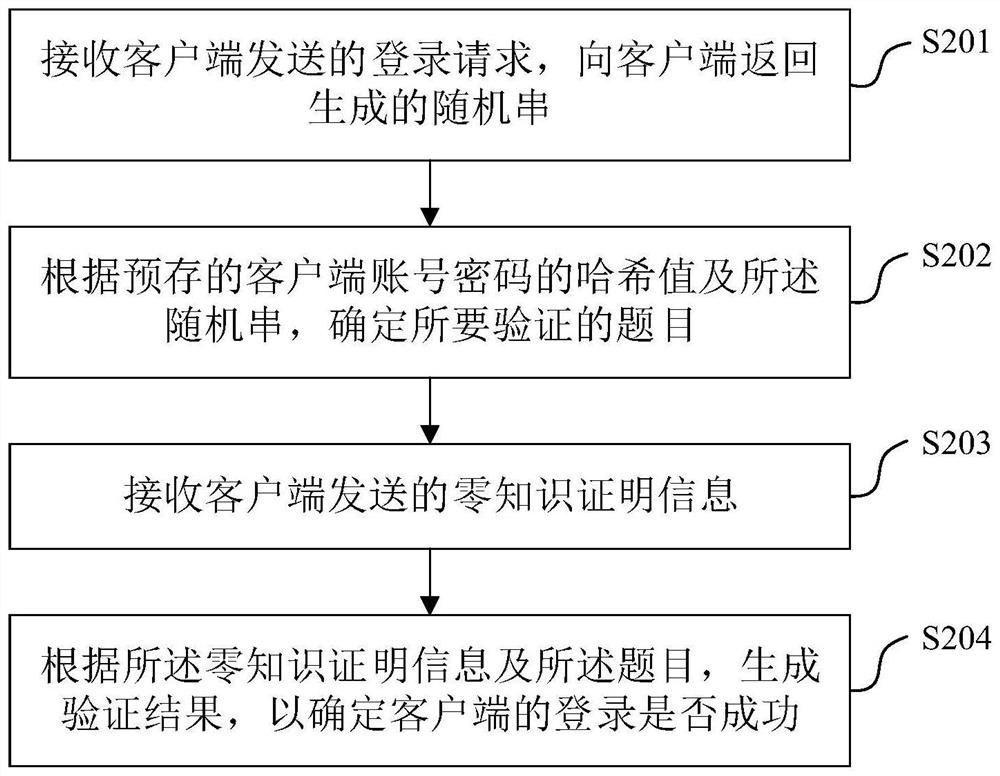
[0089] The embodiment of this application provides a login verification method, such as figure 2 As shown, the method includes:
[0090] Step S201: Receive the login request sent by the client, and return the generated random string to the client.
[0091] In the embodiment of the present application, the executing subject of the method is the server.
[0092] In this step, the login request sent by the client may include user description information, such as address information, identity information, etc. After receiving the login request sent by the client, the server specifies the client that needs to log in, and generates a random string and returns it to the client. client.
[0093] Wherein, the server may generate a random string according to a preset random algorithm or a random string generator approved by the State Cryptography Administration, which is not limited in this embodiment of the present application.
[0094] In the embodiment of this application, the ra...
Embodiment 3
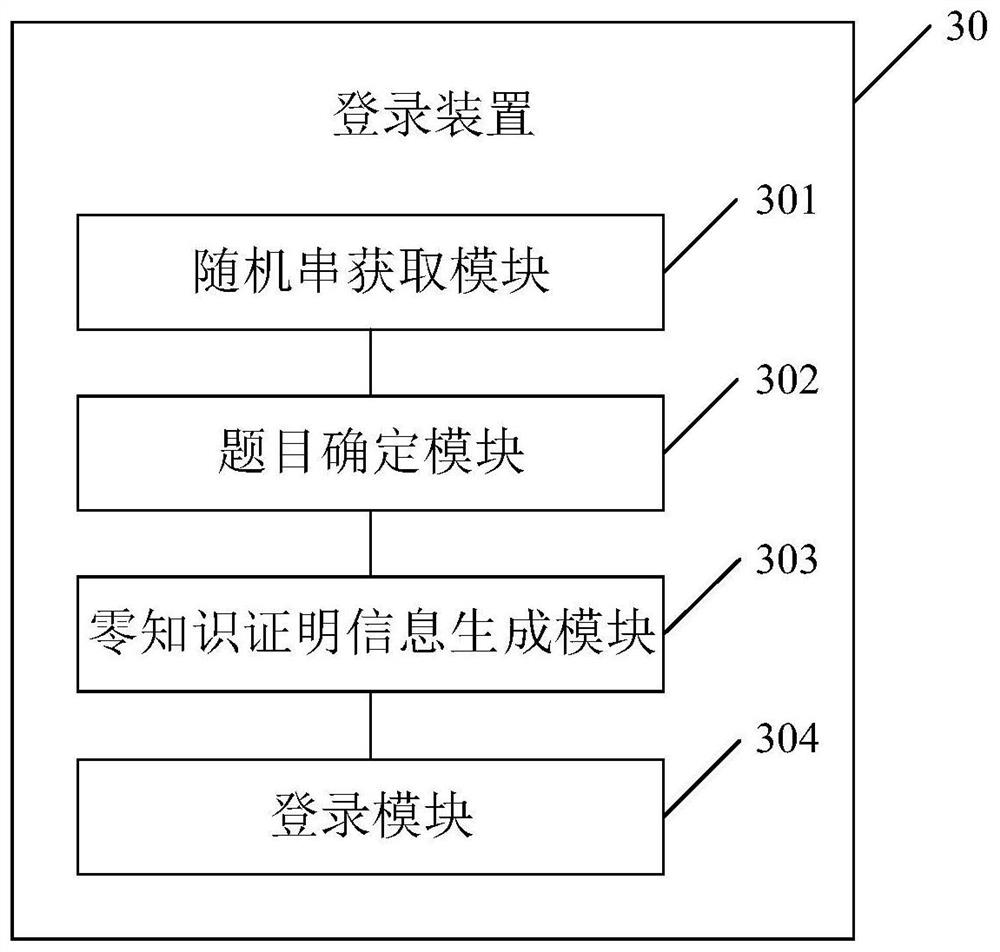
[0119] The embodiment of this application provides a login device, such as image 3 As shown, the login device 30 may include: a random string acquisition module 301, a topic determination module 302, a zero-knowledge proof information generation module 303, and a login module 304, wherein,
[0120] Random string acquisition module 301, configured to send a login request to the server, and receive the random string r returned by the server;
[0121] The topic determination module 302 is used to determine the topic to be verified by the server according to the held account password ps and random string r;
[0122] The zero-knowledge proof information generation module 303 is used to generate zero-knowledge proof information required for login according to the account password ps, random string r and title;
[0123] The login module 304 is configured to send the zero-knowledge proof information to the server, so that the server generates a verification result according to the z...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap