Method, device and system for automatically extracting logs
An automatic extraction and log technology, applied in the field of information security, can solve the problems of repeated extraction, low extraction efficiency, delay in the progress of detecting network security incidents, etc., and achieve the effect of automatic extraction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
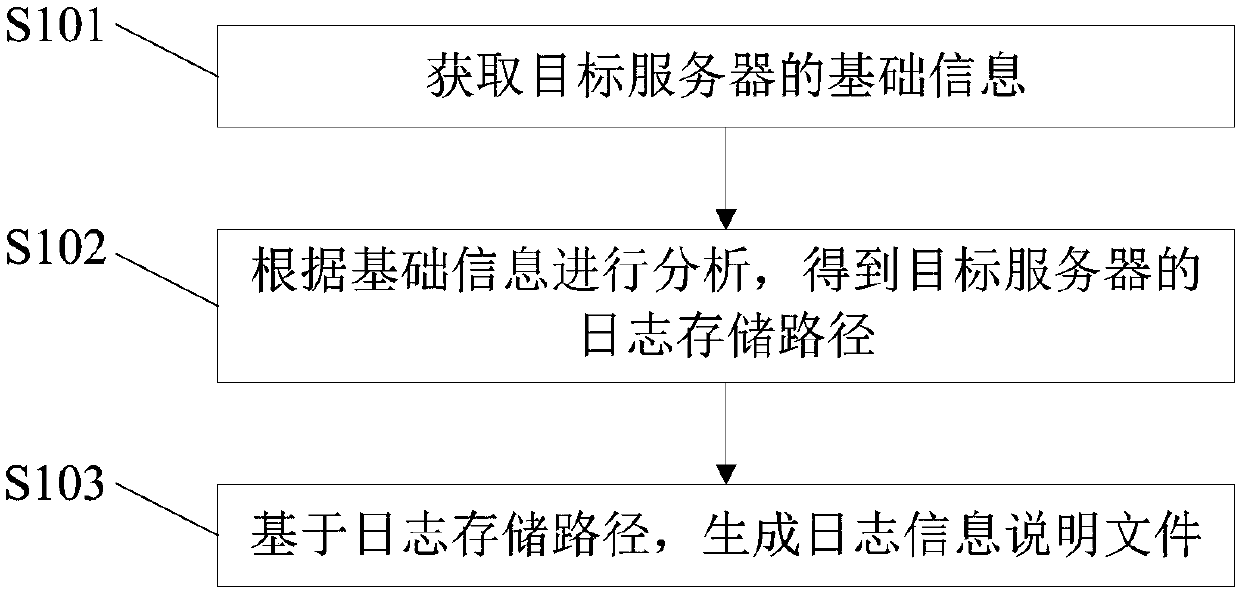
[0060] An embodiment of the present invention provides a method for automatically extracting logs. The method is executed on the side of a device for automatically extracting logs, and can automatically extract logs from a server connected to it. see figure 1 As shown, it specifically includes the following steps:
[0061] S101: Obtain basic information of a target server.
[0062] Wherein, the basic information includes: at least one of process information, service information, system information, and network port information.
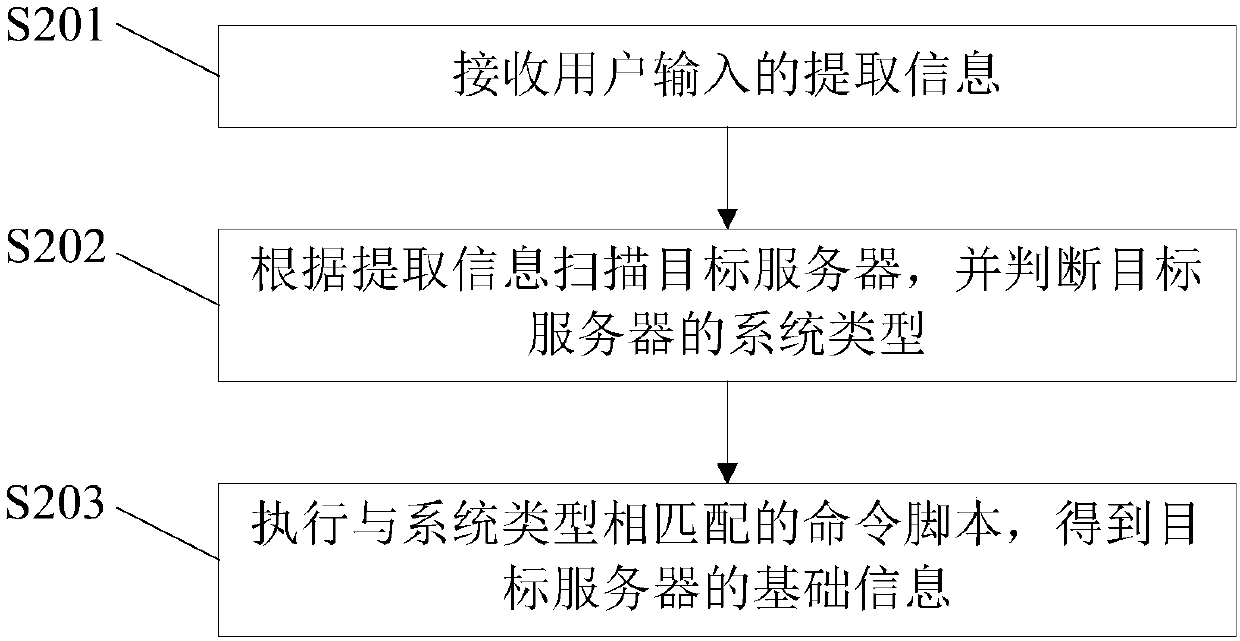
[0063] For the specific basic information acquisition process, see figure 2 shown, including the following steps:
[0064] S201: Receive extraction information input by a user.
[0065] Wherein, the extracted information is the information of the extracted log. During specific implementation, the information of extracting logs may include the extraction request generated by pressing the button of the device for automatically extracting logs, and...
Embodiment 2
[0101] An embodiment of the present invention provides a device for automatically extracting logs, see Figure 8 As shown, the device includes: a basic information acquisition module 81 , an analysis module 82 , and a log extraction module 83 .
[0102] Wherein, the basic information acquisition module 81 is used to obtain the basic information of the target server; the basic information includes: at least one item of process information, service information, system information, and network port information;
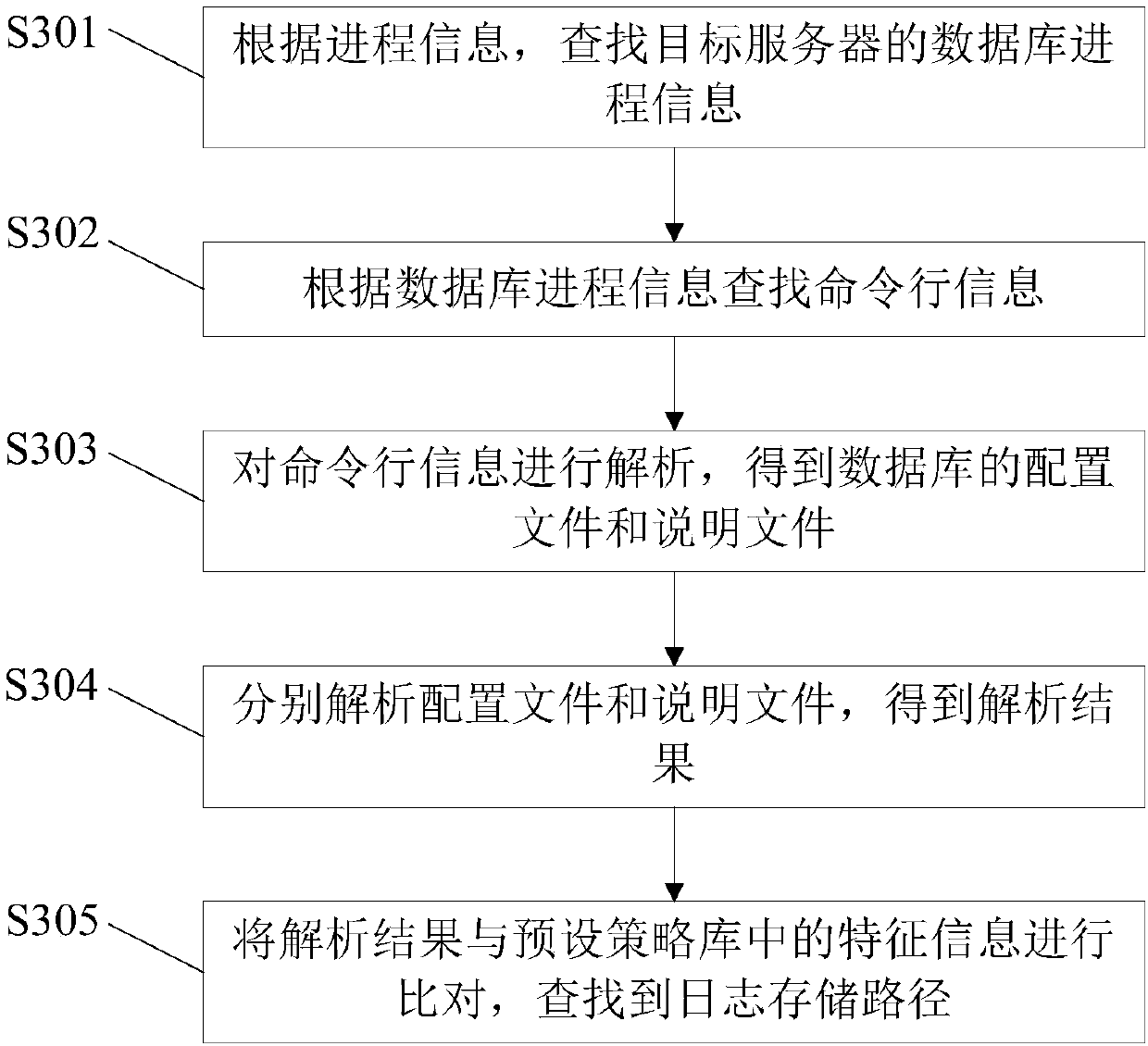
[0103] Analysis module 82, is used for analyzing according to basic information, obtains the log storage path of target server;
[0104] The log extraction module 83 is configured to extract log content and generate a log information description file according to the log storage path.
[0105] The device for automatically extracting logs provided by the embodiment of the present invention has the same technical features as the aforementioned method for automatically ext...
Embodiment 3
[0107] The embodiment of the present invention also provides a system for automatically extracting logs, see Figure 9 As shown, the system includes: a server 91 and a device 92 for automatically extracting logs as described in Embodiment 2; the device 92 for automatically extracting logs is connected to the server 91 .
[0108] Specifically, the device 92 for automatically extracting logs can be connected to the server 91 that needs to extract logs through USB, or can be connected to the server 91 that needs to extract logs through wireless communication.
[0109] In the system for automatically extracting logs provided by the embodiments of the present invention, the specific interaction process between the server and the device for automatically extracting logs has the same technical features as the aforementioned method for automatically extracting logs, so the above functions can also be realized. For the specific working process of the server and the device for automatic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com