Message reminding method, communication interception method, terminal and computer storage medium
A technology of message reminder and communication information, applied in the field of communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
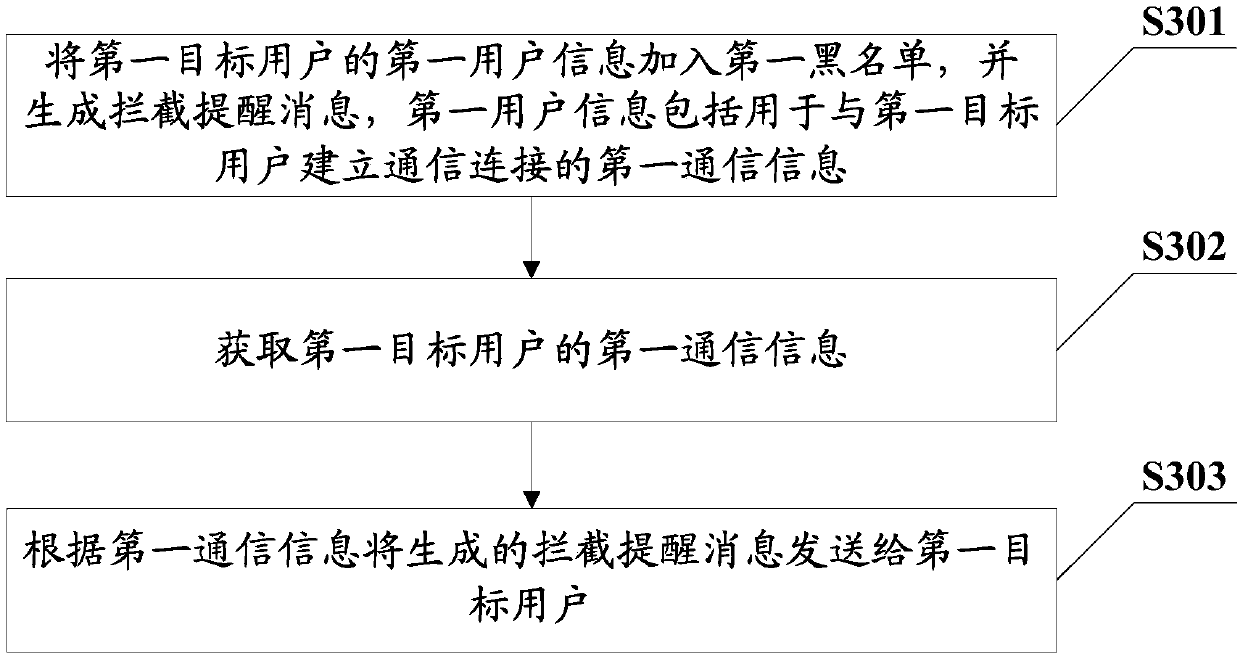
[0078] In order to solve the existing solution, when the second user sets the first user as a blacklist user, since the first user cannot know that he is a blacklist user of the second user, he will continue to send communication requests to the second user, resulting in communication resources For the problem of waste, this embodiment provides a message reminder method, please refer to image 3 shown, including:
[0079] S301: When adding the first user information of the first target user to the first blacklist, generate an interception reminder message, where the first user information includes first communication information for establishing a communication connection with the first target user.
[0080] It should be noted that the first communication information in this embodiment may be the first phone number of the first target user, and on this basis may also include the name of the first contact; or it may also be based on a certain application User identification in...
no. 2 example
[0107] In order to solve the existing solution, after the second target user sets the first target user as a blacklist user, since the first target user cannot know that he is a blacklist user of the second target user, he will continue to send communication requests to the second target user , the second target user will receive these communication requests and process these communication requests, causing the problem that the second target user misses the communication sent by other users while the line is busy. This embodiment provides a communication interception method, please refer to Figure 6 shown, including:
[0108] S601: Receive an interception reminder message sent by a second target user.
[0109] Specifically, the interception reminder message sent by the second target user in the above-mentioned first embodiment may be received, and in this case, the execution subject of step S601 is essentially the first target user.
[0110] S602: Acquire second user informa...
example 1
[0112] Example 1: If the first communication information includes the first phone number and the second communication information includes the second phone number, when the second target user adds the first phone number of the first target user to the first blacklist, an interception reminder can be generated message, and the interception reminder message can be sent to the first target user according to the first phone number, that is, the interception reminder message is sent by the second target user to the first target user, so the first target user receives the When the reminder message is intercepted, the corresponding second phone number of the second target user can be found. It should be noted that the second phone number in this embodiment can also be a mobile phone number.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com