One-key login method and system, related devices and computer readable storage medium
A login method and login request technology, applied in the field of communication, can solve the problems of low security, information forgery in SIM cards, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
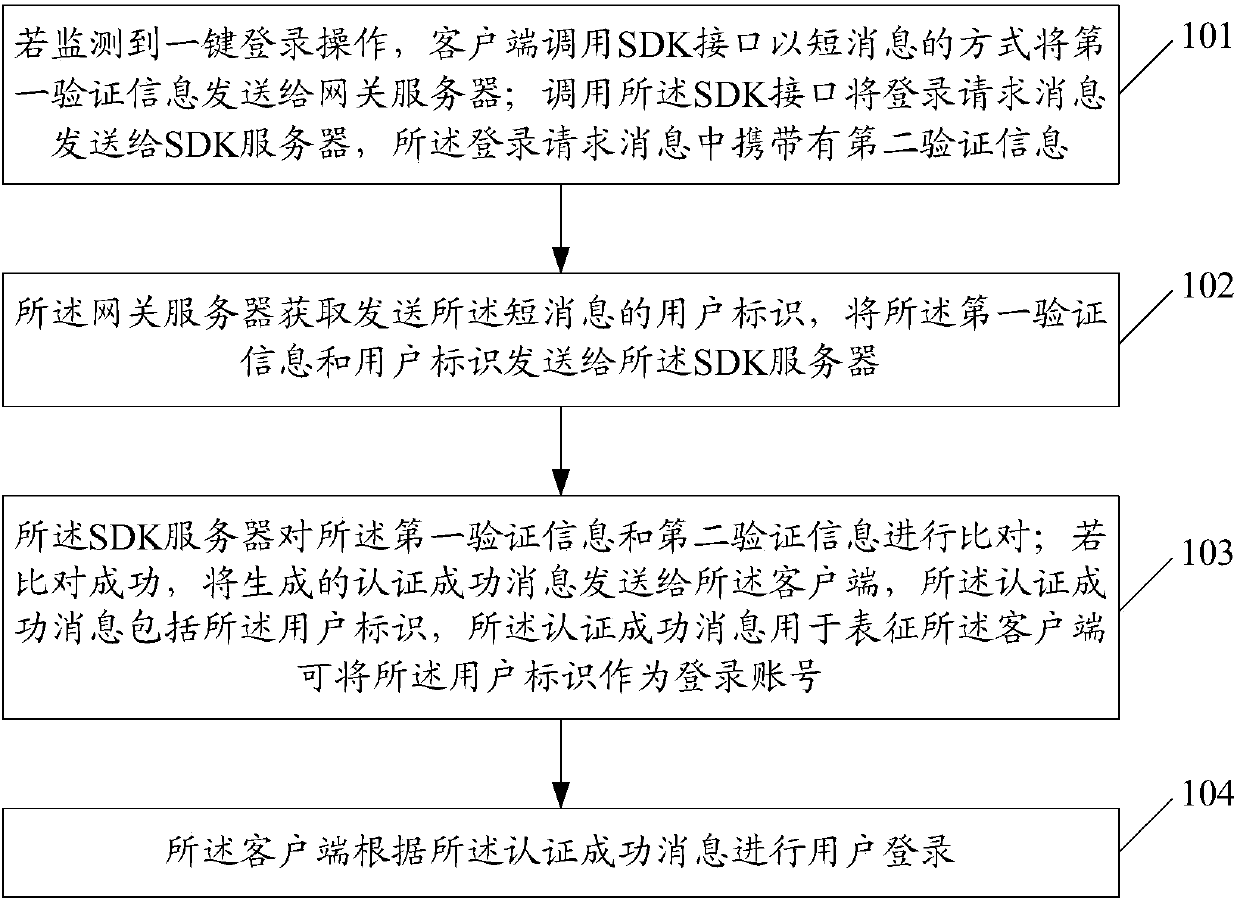
[0063] From the description of the background art, it can be seen that in the related art, when performing one-key login, if only relying on the SIM card to identify and confirm the user to log in to the application, there is a problem of low security.
[0064] For example, when there is only the SIM card's own information in the SIM card but no number information, it is impossible to confirm the user by comparing the number information at this time; for another example, if the user's SIM card is lost, the IMSI in the newly copied SIM card will The code must be different from the previous IMSI code. If the newly copied SIM card is used to directly log in to the application, the user will be prohibited from logging in because the IMSI code information cannot be matched successfully.
[0065] Therefore, if only relying on the SIM card to identify and confirm the user, there will be a problem of low security of one-key login.
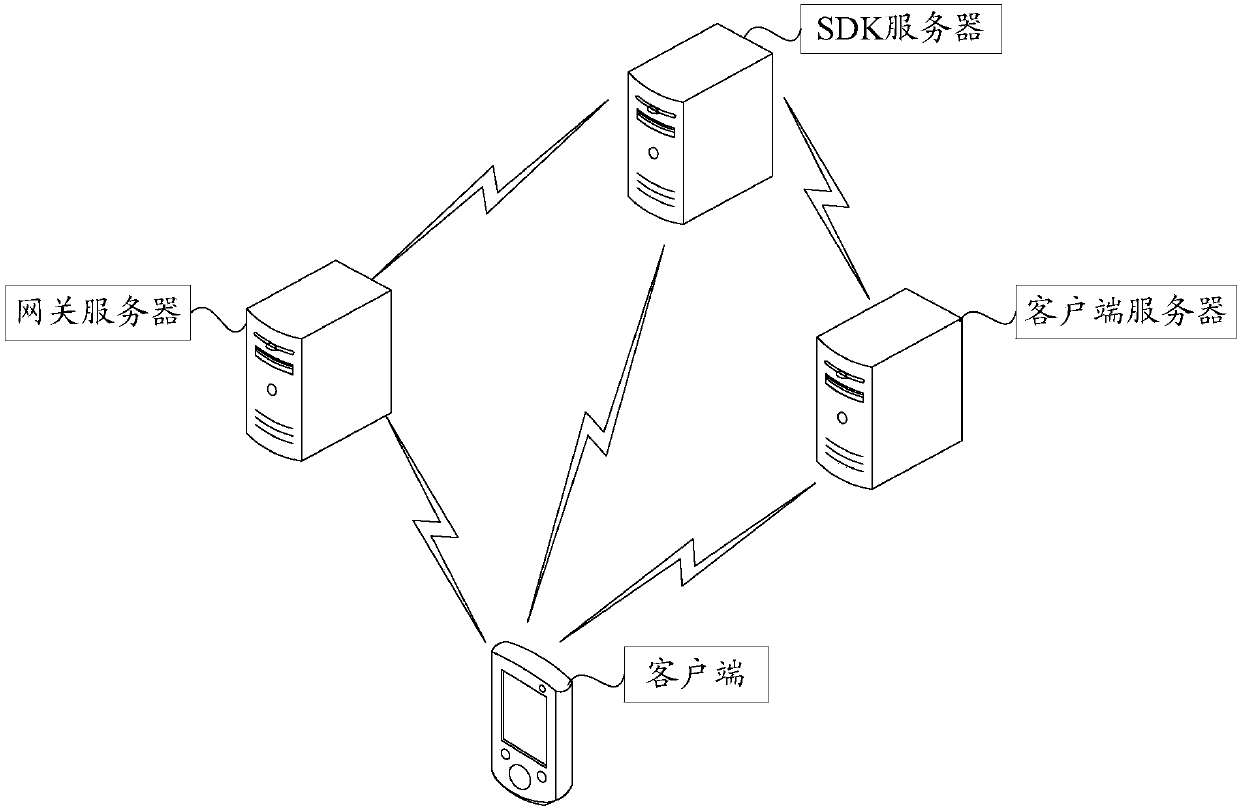
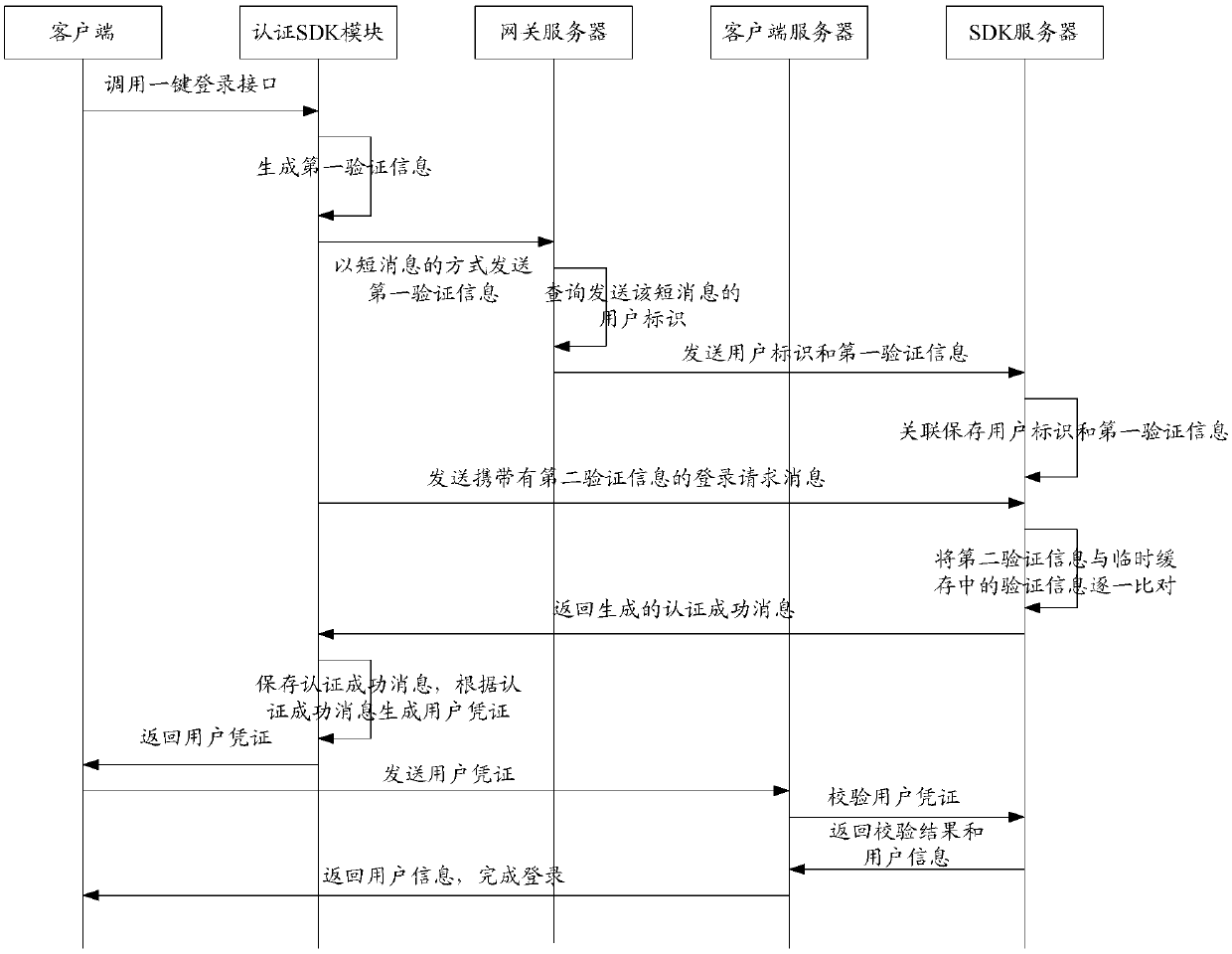
[0066] Based on this, in the embodiment of the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com