A method and device for defending against attacks
A technology for preventing attacks and attacking packets, applied in the field of network communication, can solve the problem of BRAS being vulnerable to attacks, and achieve the effect of accurate statistics and reduction of the number of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
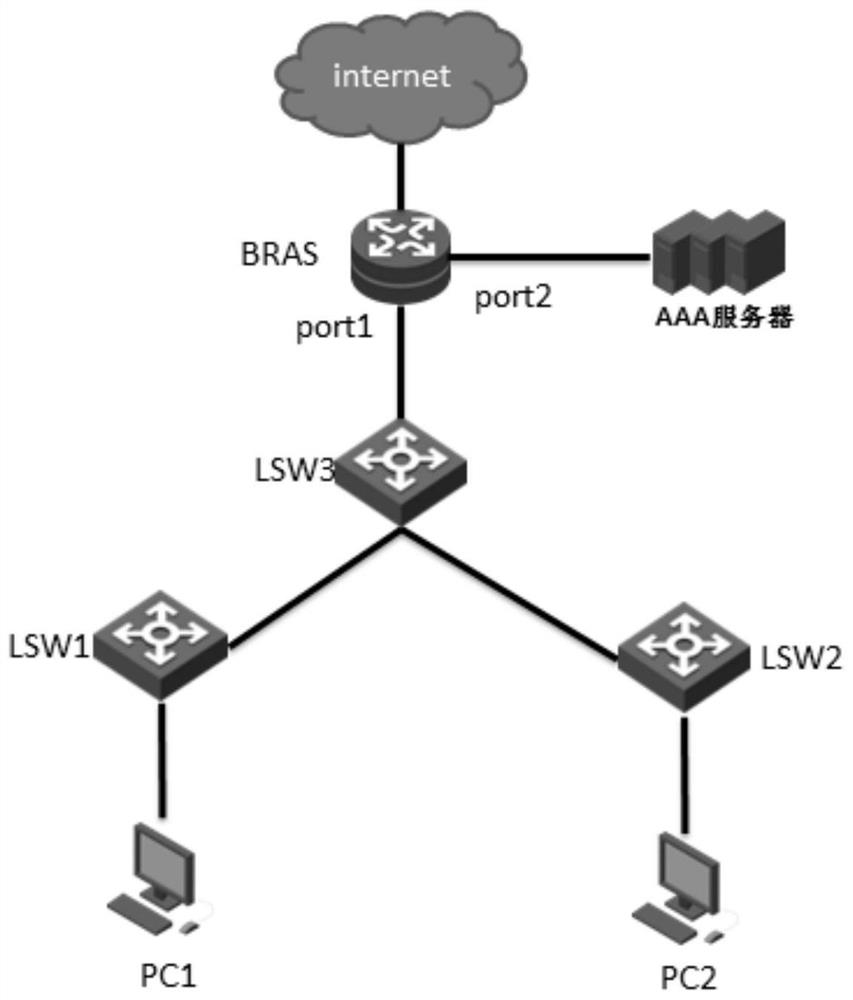
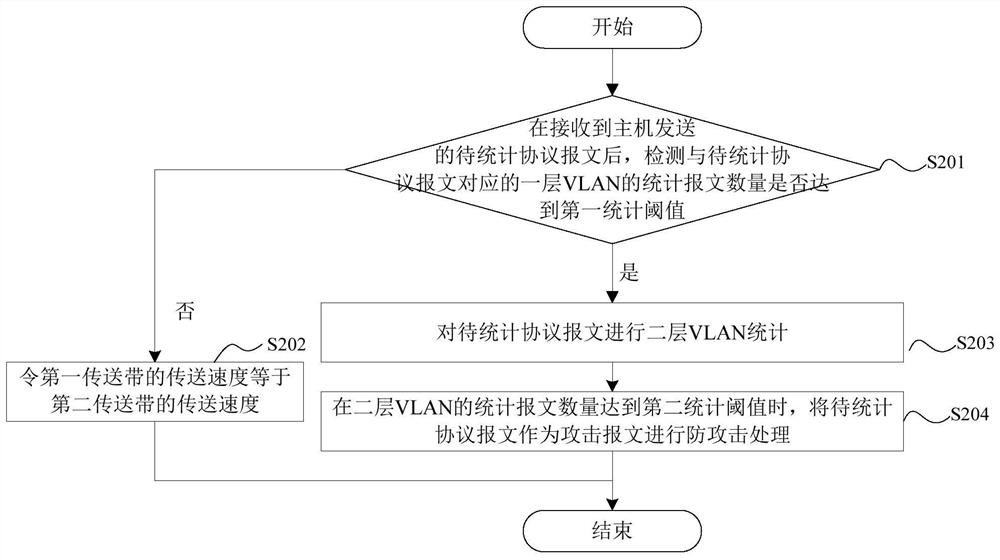
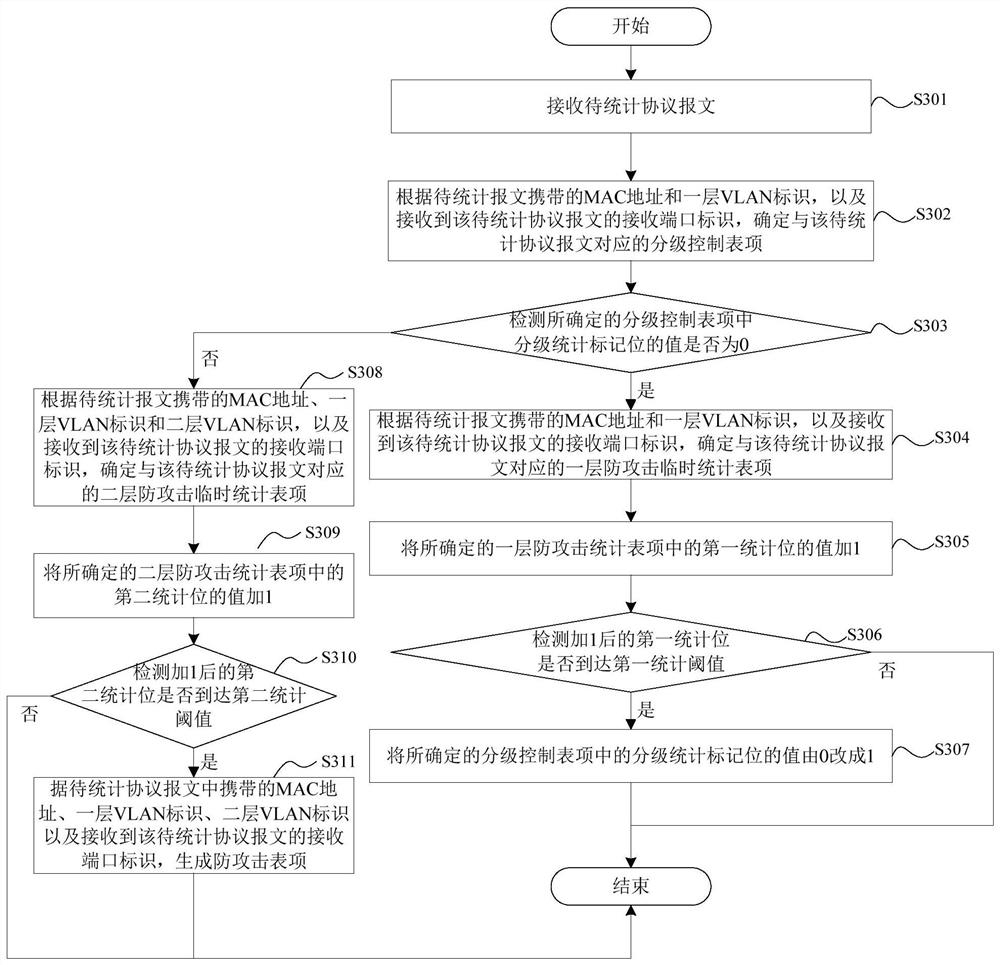
[0041] When the BRAS performs layer-1 VLAN statistics on the protocol packets, it is based on the layer-1 anti-attack temporary statistical table; the layer-1 anti-attack temporary statistical table includes multiple layer-1 attack temporary statistical table items. A layer-1 attack defense temporary statistics table item carries a MAC address, a layer-1 VLAN ID, a receiving port ID of a protocol packet, and a first statistical bit, which is used to record the layer-1 VLAN statistics on the protocol packet The current number of statistical packets at that time.
[0042] For example, the temporary statistical table of layer 1 defense attack is shown in Table 1:
[0043] Table 1
[0044] Index MAC Svlan interface first statistic 1 mac1 1 port1 40 2 mac2 1 port1 21
[0045] Among them, Index is the serial number of the first-layer anti-attack temporary statistical entry; MAC is the MAC address; Svlan is the VLAN ID of the first layer; I...
example 2
[0048] A new classification control table is added on the BRAS; the classification control table includes multiple classification control entries; each classification control entry carries a MAC address, a layer of VLAN identification, a receiving port identification, and classification statistics flag bits; if the classification If the value of the statistics flag bit is 0, it indicates that layer-1 VLAN statistics are performed on the newly received protocol packets corresponding to the hierarchical control entries; if the value of the hierarchical statistics flag bit is 1, it indicates that the newly received Layer 2 VLAN statistics are performed on protocol packets corresponding to hierarchical control entries. The protocol message corresponding to the hierarchical control table item refers to the protocol message whose MAC address, first-level VLAN ID, and receiving port ID are the same as those carried in the hierarchical control table item. .
[0049] For example, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com