Method and system for calculating dynamic wind power penetration power limit
A technology that penetrates power and calculation methods, and is applied to wind power generation, electrical components, circuit devices, etc., and can solve problems such as the inability to determine reliable wind power access capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
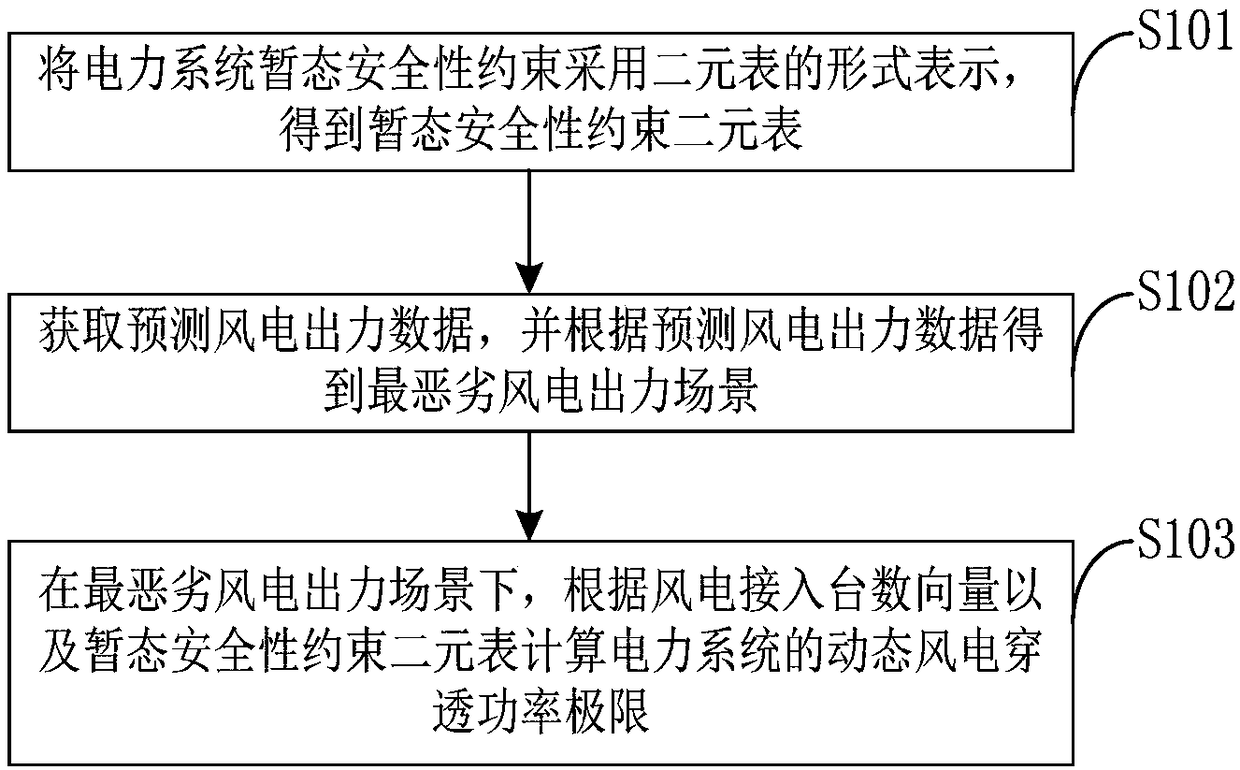
[0060] figure 1 A flow chart of a method for calculating a dynamic wind power breakthrough power limit provided by an embodiment of the present invention is shown.
[0061] Such as figure 1 As shown, a method for calculating a dynamic wind power breakthrough power limit provided by this embodiment includes the following steps:
[0062] Step S101, expressing the transient security constraints of the power system in the form of a binary table to obtain a binary table of transient security constraints, wherein the binary table includes thresholds and time limits;
[0063] The binary table of transient security constraints is a unified expression form of power system transient security constraints. First, the power system transient security is divided into transient voltage security, transient power angle security and transient frequency security, and the transient voltage (frequency) security is further divided into transient voltage (frequency) Stability and acceptability of ...
Embodiment 2
[0096] Figure 4 A schematic diagram of a system for calculating a dynamic wind power breakthrough power limit provided by an embodiment of the present invention is shown.
[0097] Such as Figure 4 As shown, a dynamic wind power breakthrough power limit calculation system provided in this embodiment includes a binary table generation module 10, an acquisition module 20, and a calculation module 30;
[0098]The binary table generation module 10 is used to express the transient security constraints of the power system in the form of a binary table to obtain a binary table of transient security constraints, wherein the binary table includes a threshold and a time limit;
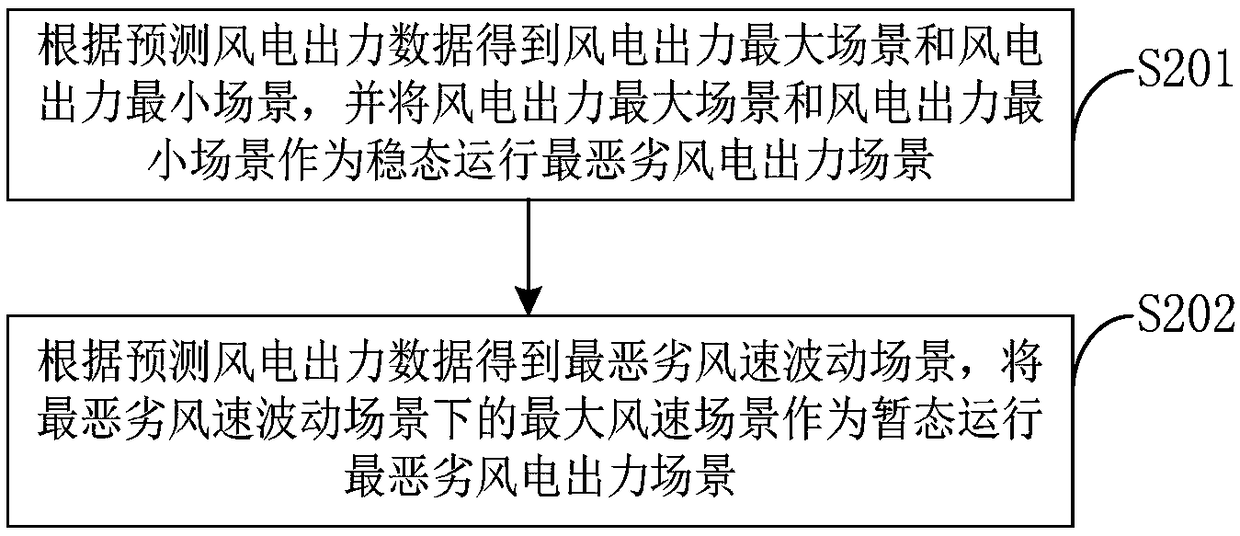
[0099] An acquisition module 20, configured to acquire predicted wind power output data, and obtain the worst wind power output scenario according to the predicted wind power output data;
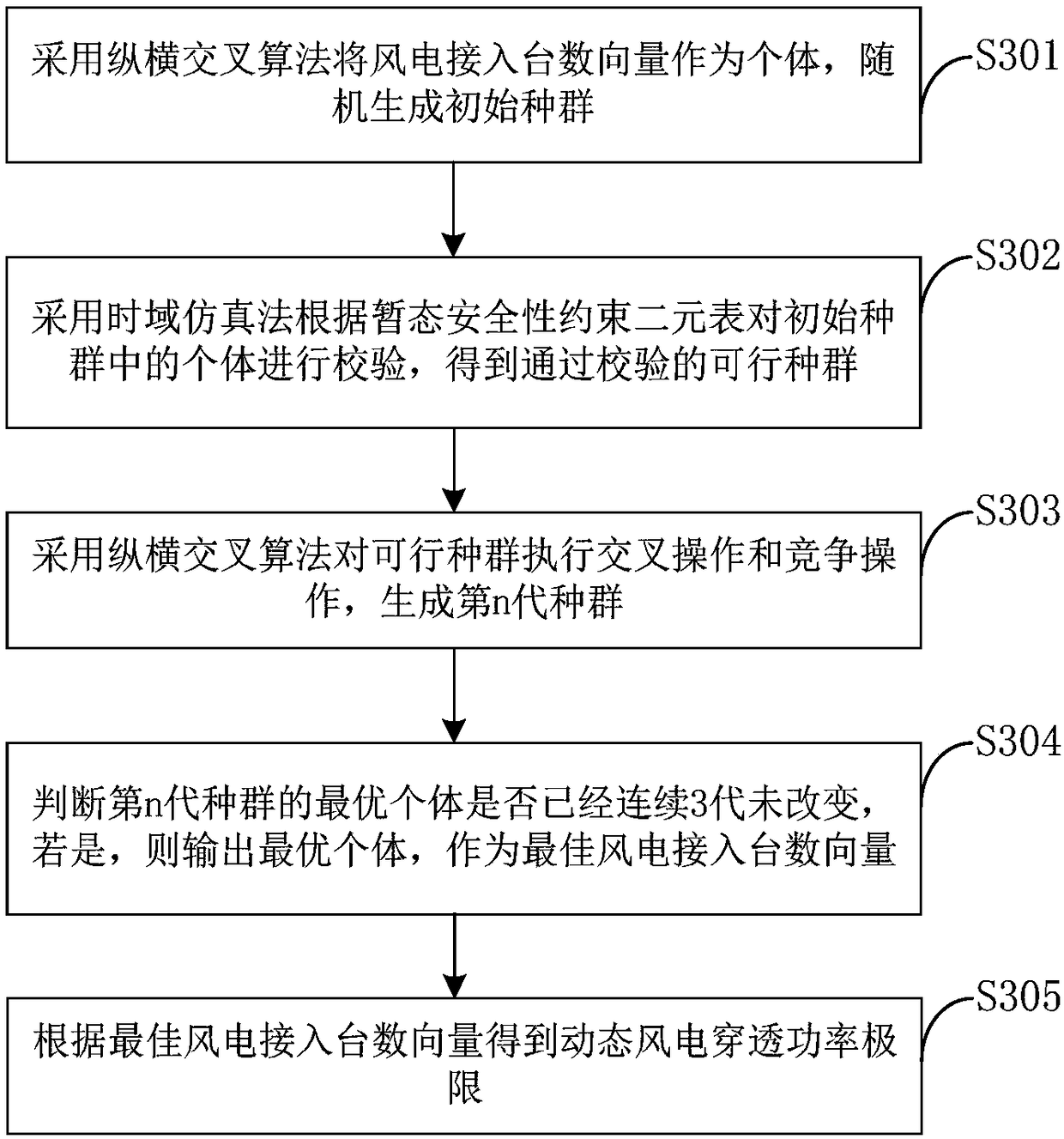
[0100] The calculation module 30 is used to calculate the dynamic wind power penetration power limit of the power system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com