DNS hijacking defense method and apparatus
A target and domain name technology, applied in the Internet field, can solve problems such as affecting the normal operation of Internet business, achieve the effect of safe use and avoid being hijacked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
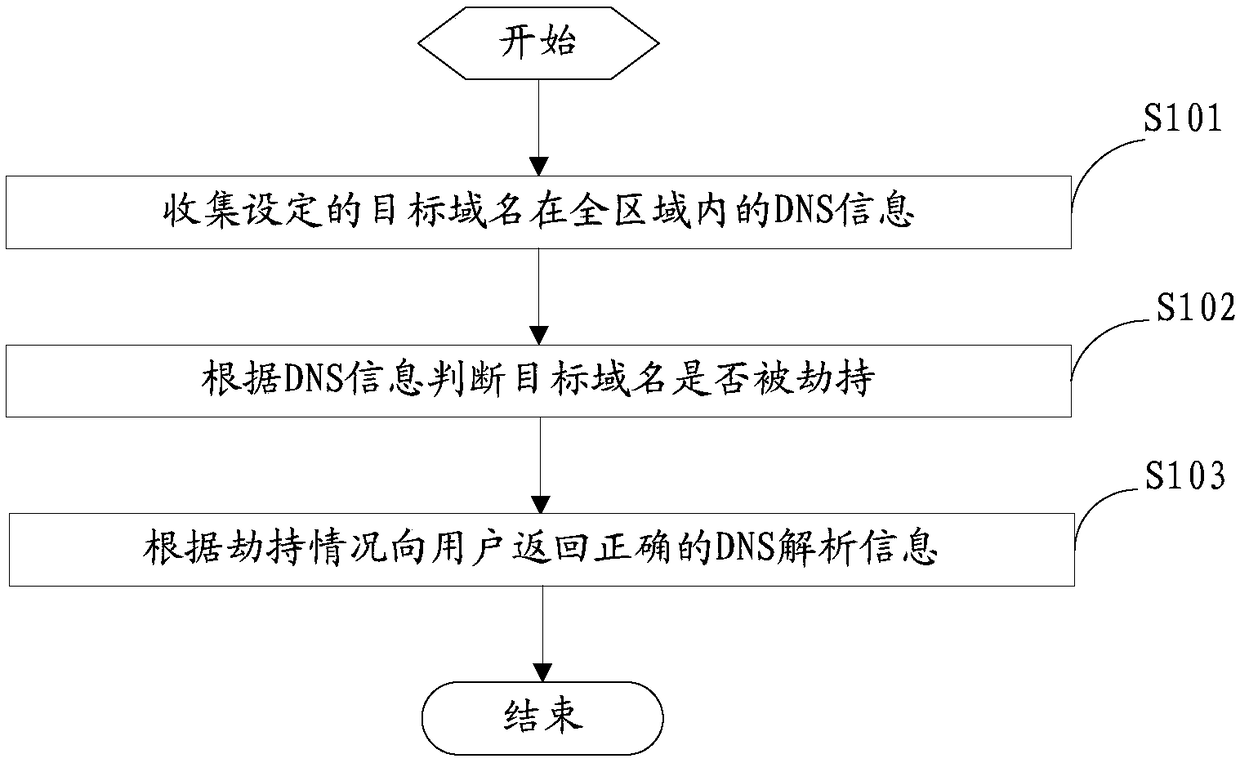
[0037] figure 1 It is a flowchart of steps of a DNS hijacking defense method provided by an embodiment of the present invention.
[0038] refer to figure 1 As shown, the DNS hijacking defense method provided in this embodiment is applied to the DNS system to prevent DNS hijacking. The defense method includes the following steps:
[0039] S101: Collect DNS information of the set target domain name in the whole region.
[0040] This embodiment is aimed at the hijacking defense of the domain name within the predetermined range, and the domain name within the predetermined range is the target domain name here. Since the method in this embodiment is applied to the DNS system, the whole area here refers to the network area served by the corresponding DNS system. The DNS information refers to the IP address corresponding to the corresponding domain name.
[0041] S102: Determine whether the target domain name has been hijacked according to the DNS information.
[0042] After col...
Embodiment 2
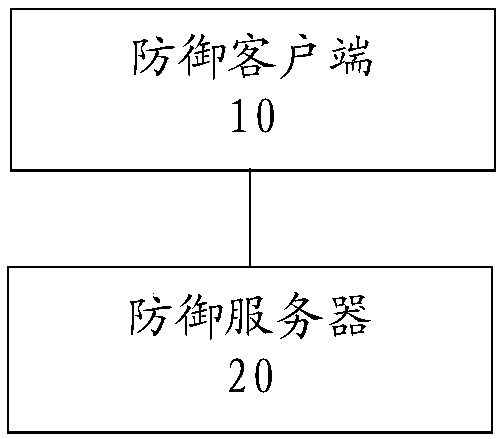
[0052] figure 2 It is a structural block diagram of a DNS hijacking defense device provided by an embodiment of the present invention.
[0053] refer to figure 2 As shown, the DNS hijacking defense device provided in this embodiment is applied to the DNS system to prevent DNS hijacking, and the defense device includes a defense client 10 and a defense server.
[0054] The defense client is used to collect the DNS information of the set target domain name in the whole area, and send the collected DNS information to the defense server.
[0055] This embodiment is aimed at the hijacking defense of the domain name within the predetermined range, and the domain name within the predetermined range is the target domain name here. Since the method in this embodiment is applied to the DNS system, the whole area here refers to the network area served by the corresponding DNS system. The DNS information refers to the IP address corresponding to the corresponding domain name.
[0056]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com