High-fidelity H.264/AVC video three-coefficient reversible steganography method
A high-fidelity, high-efficiency technology, applied in digital video signal modification, electrical components, image communication, etc., can solve the problem of algorithm embedding efficiency reduction, achieve good visual quality, high embedding efficiency, and ensure reversibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
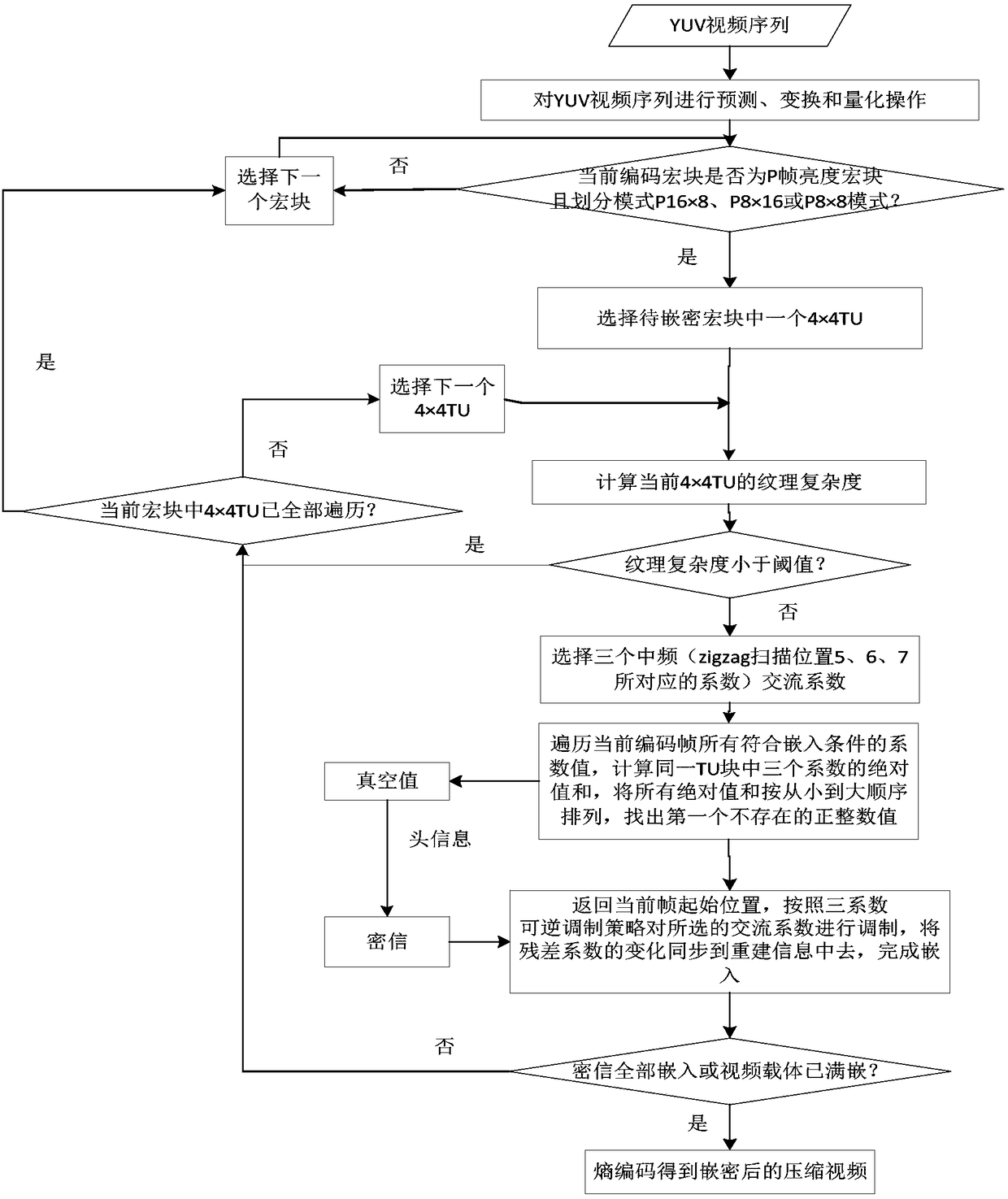
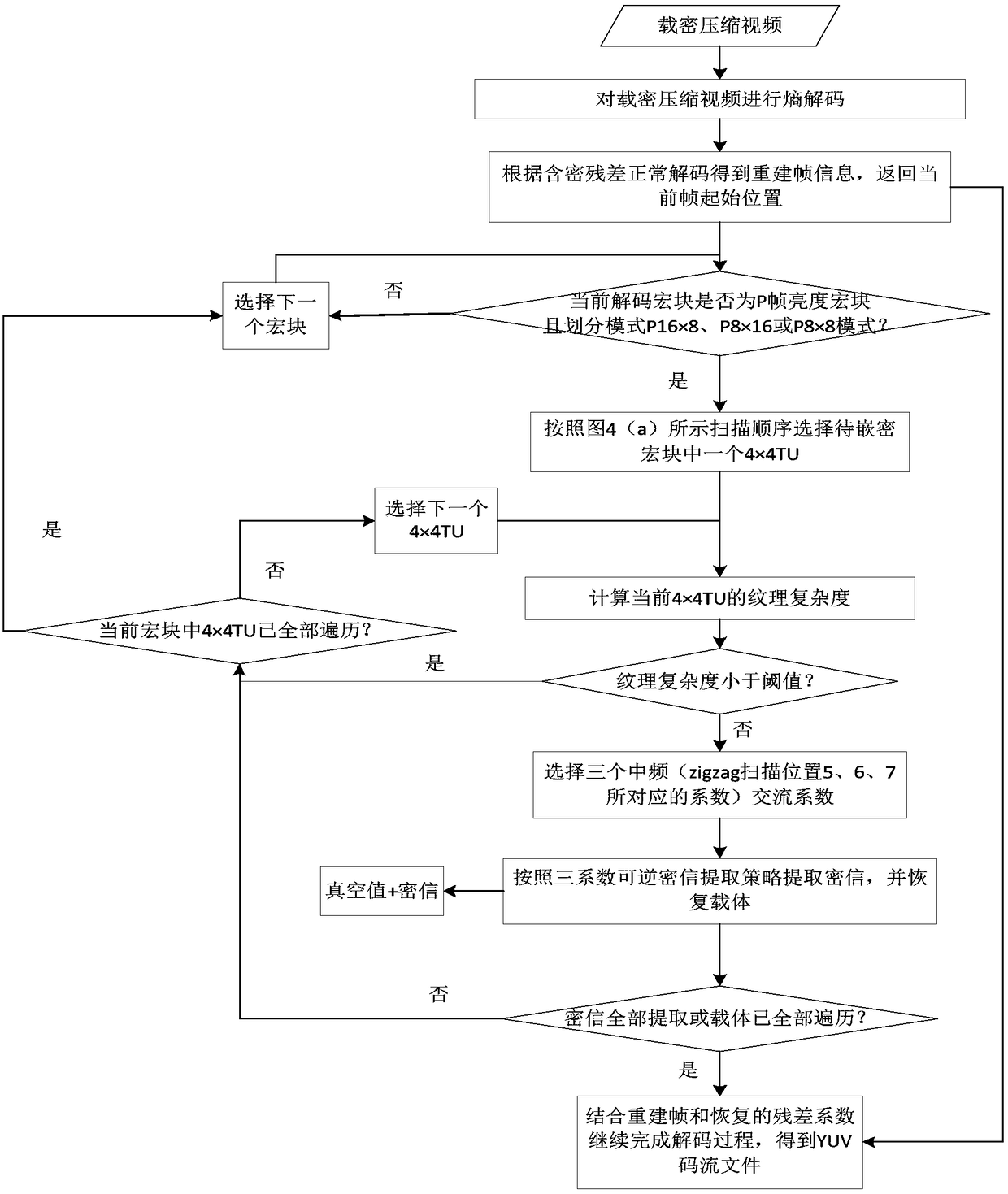
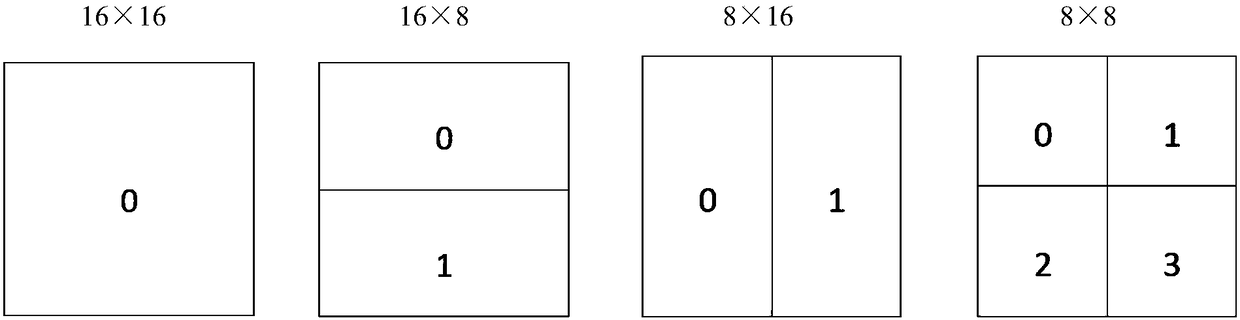
[0052] A high-fidelity three-coefficient reversible steganography method for H.264 / AVC video, including two parts: an embedding method and an extraction method. The flow chart of the embedding method is as follows: figure 1 As shown, the embedding process is mainly divided into six steps, including obtaining quantized residual DCT coefficients and macroblock prediction modes, selecting macroblocks to be embedded that meet the embedding requirements, determining the final 4×4TU sub-blocks for embedding, traversing the current Encode the frame to obtain the "vacuum value", modulate the carrier according to the "vacuum value" and the secret message content, and synchronize the change of the residual to the reconstructed macroblock of the macroblock, and entropy coding to obtain the compressed video after embedding. The flow chart of the extraction method is as follows figure 2 As shown, the extraction process is mainly divided into six steps, including entropy decoding to obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com