A method of virtual identity verification
A virtual identity and identity information technology, applied in the information field, can solve problems such as user identity confirmation, identity matching, and difficulty in ensuring the authenticity of information, and achieve the effect of improving confirmation efficiency and solving cyber violence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
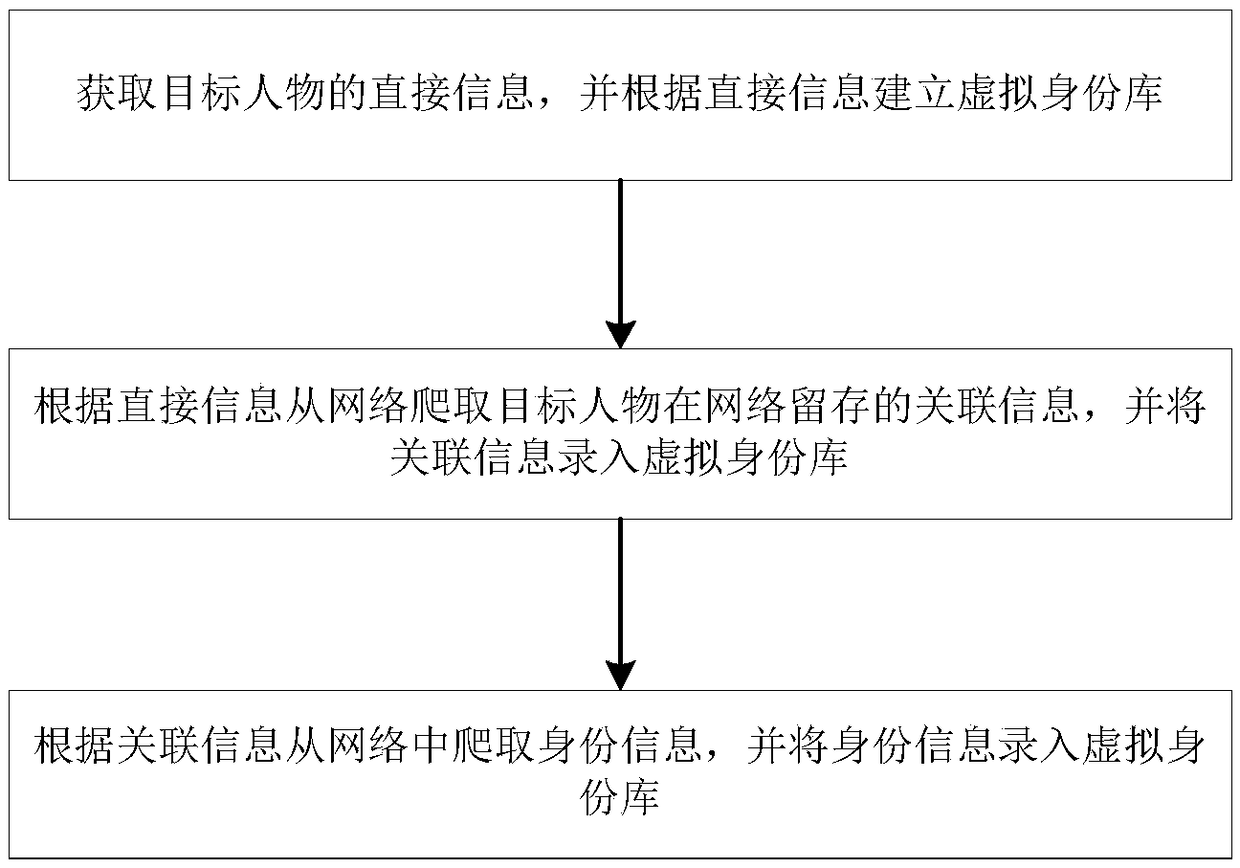
[0022] like figure 1 As shown, this embodiment discloses a method for virtual identity verification, which is characterized in that it includes the following steps:
[0023] S01: Obtain the direct information of the target person, and establish a virtual identity database based on the direct information;
[0024] S02: Crawl the related information of the target person from the network according to the direct information, and enter the related information into the virtual identity database;
[0025] S03: Crawl the identity information from the network according to the associated information, and enter the identity information into the virtual identity database.
[0026] The virtual identity library includes at least the following information of the target person: name, phone number, QQ number, WeChat ID, work unit, bank card, graduate school and grade major.
[0027] The direct information includes at least name, phone number, QQ number or WeChat ID.
[0028] The channels fo...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap