Proxy revocation-based key strategy attribute base encryption method
An attribute-based encryption and attribute-based technology, applied in key distribution, can solve the problems of large ciphertext space, update key and ciphertext, etc., and achieve the effect of improving revocation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
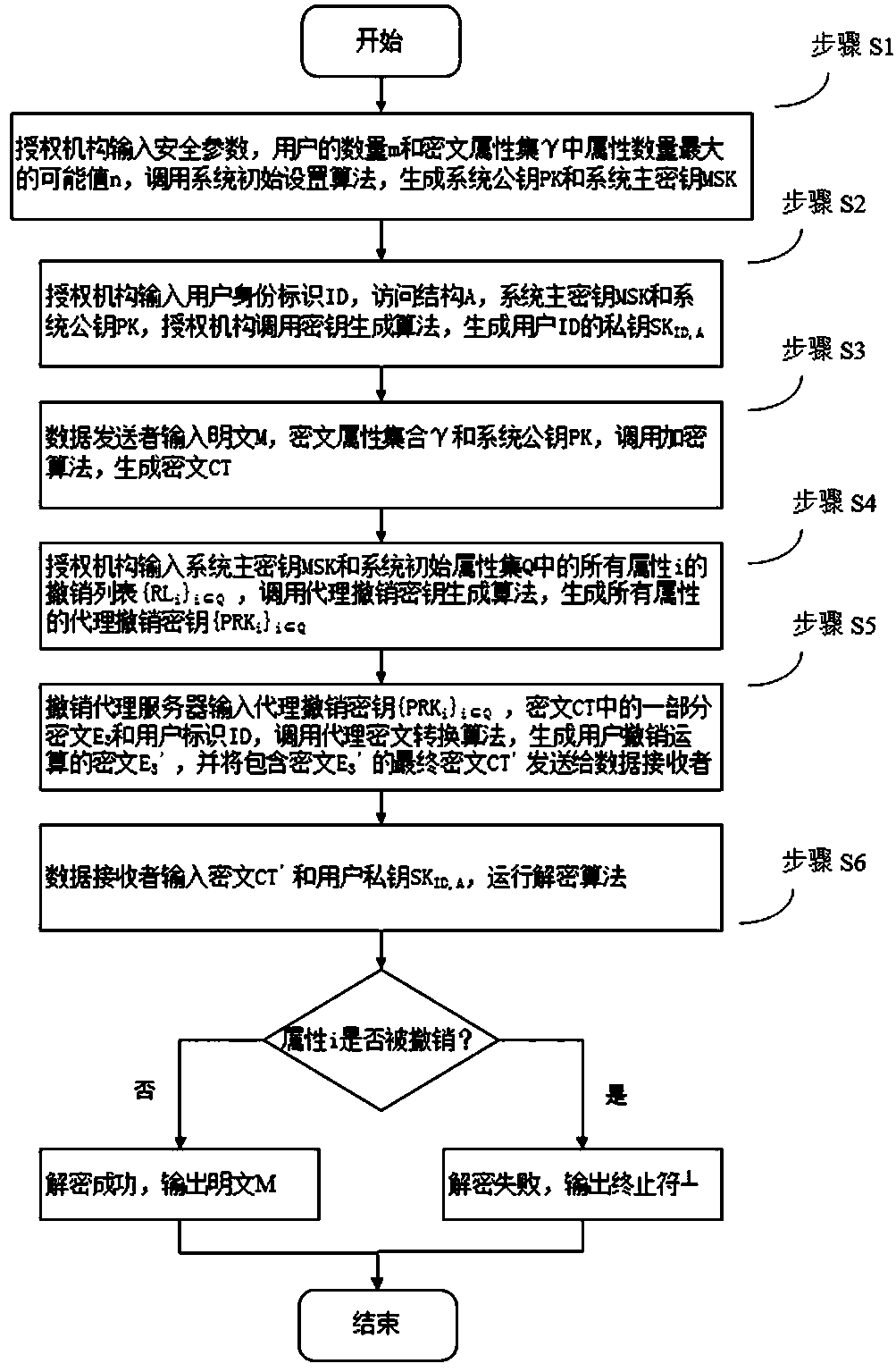
[0059] based on the following figure 1 and figure 2 , specifically explain the preferred embodiment of the present invention.
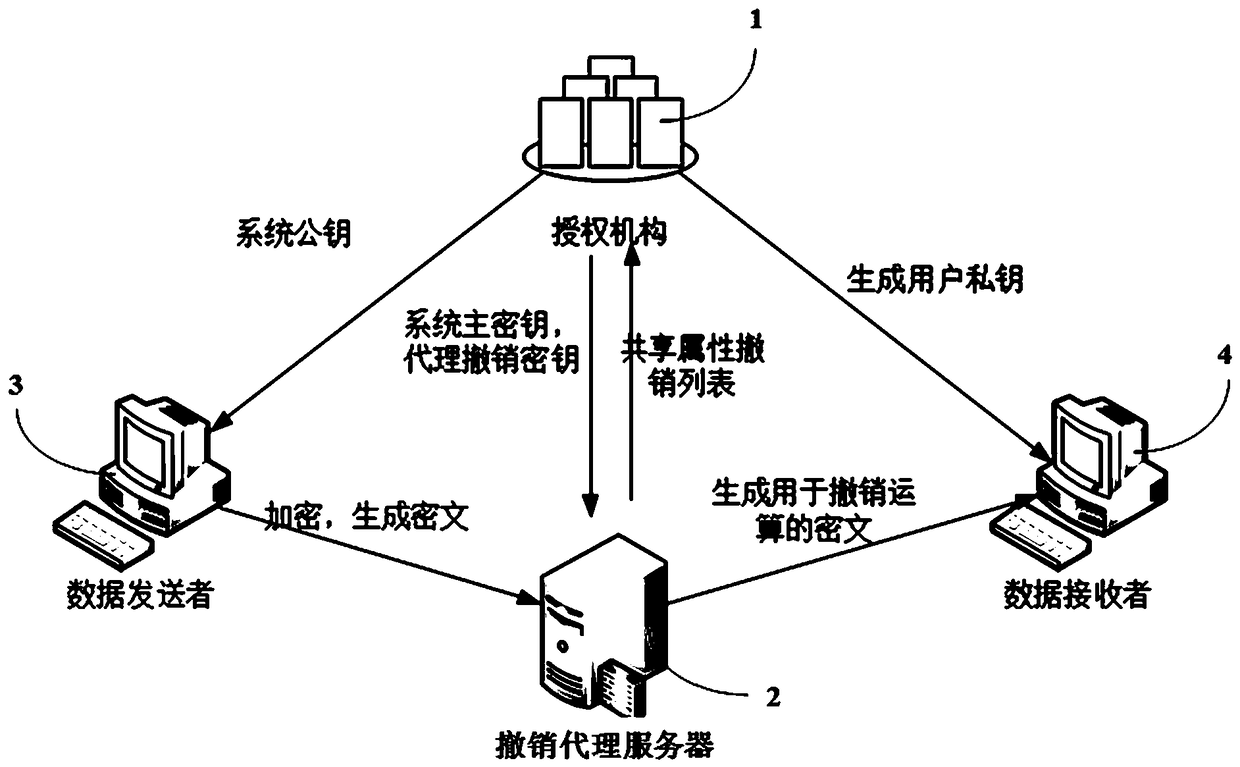
[0060] Aiming at the existing problems of indirect revocation, the present invention introduces the revocation list of all attributes held by the third-party authorization organization, and binds the user revocation list information of any number of attributes in the ciphertext, and the data receiver needs to The encrypted ciphertext is decrypted, enabling fine-grained agent-based instant attribute revocation.
[0061] Such as figure 1 As shown, the present invention provides a key policy attribute-based encryption method based on agent revocation, comprising the following steps:
[0062] Step S1, the authority inputs the security parameters, the number of users m and the possible value n of the largest number of attributes in the ciphertext attribute set, calls the system initial setting algorithm, and generates the system public key PK and syste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com