Broadcast authentication method for wireless network with limited node resource
A wireless network and resource-constrained technology, which is applied in the field of broadcast authentication of wireless networks, can solve the problems of unable to revoke the authentication ability of captured nodes in time, difficulty in fully satisfying node resources, and network scale limitations, so as to reduce broadcast authentication overhead and improve The effect of revoking efficiency and improving authentication efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] According to a preferred embodiment of the present invention, its specific method is as follows:
[0048] 1) Protocol initialization;
[0049] 1.1) Before network deployment, BServer constructs μTinst according to BNode's FP;
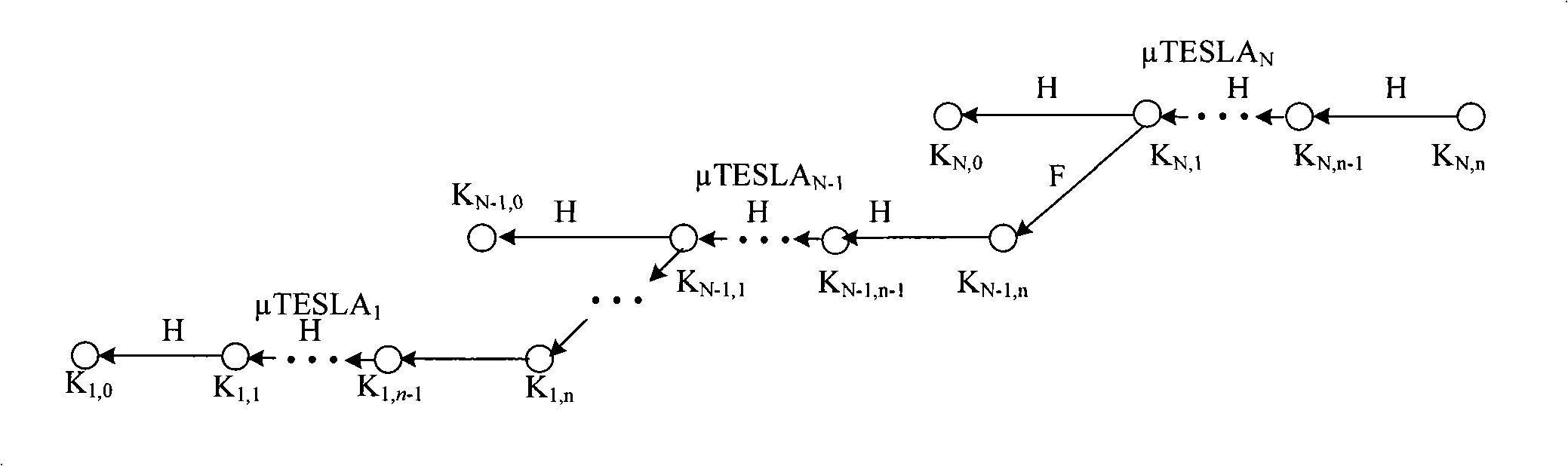
[0050] see figure 1 , the concrete steps of step 1.1) are as follows:
[0051] 1.1.1) BServer divides the life cycle of BNode into N with a length of T N time interval such that T N Just one μTinst can be run, and then according to the broadcast frequency and real-time requirements of BNode, Tinst N Divide into n smaller ones of length T n time interval;
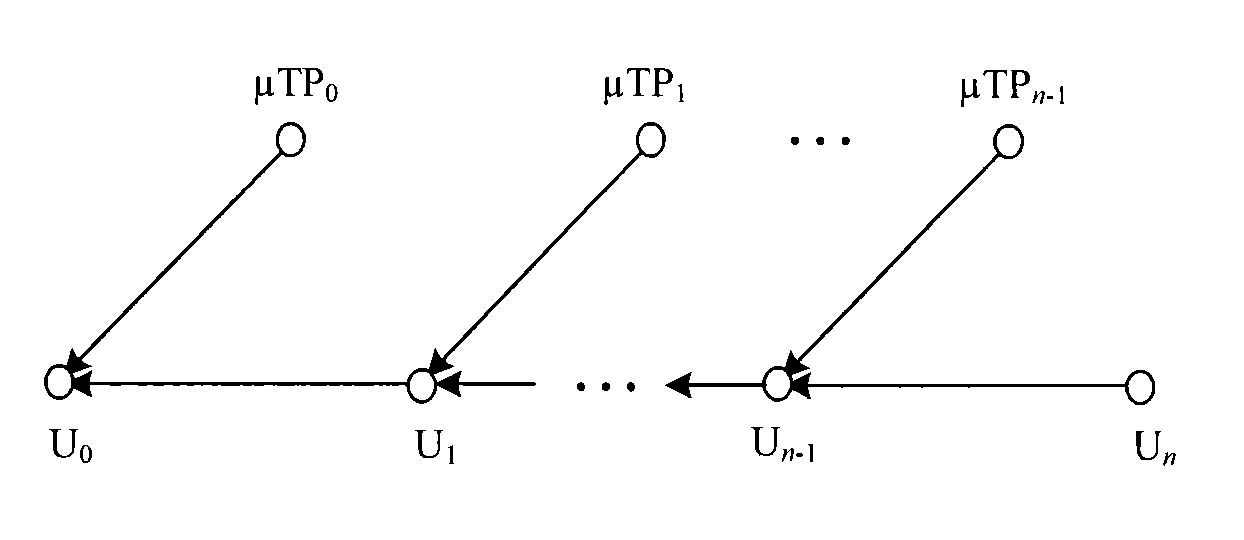
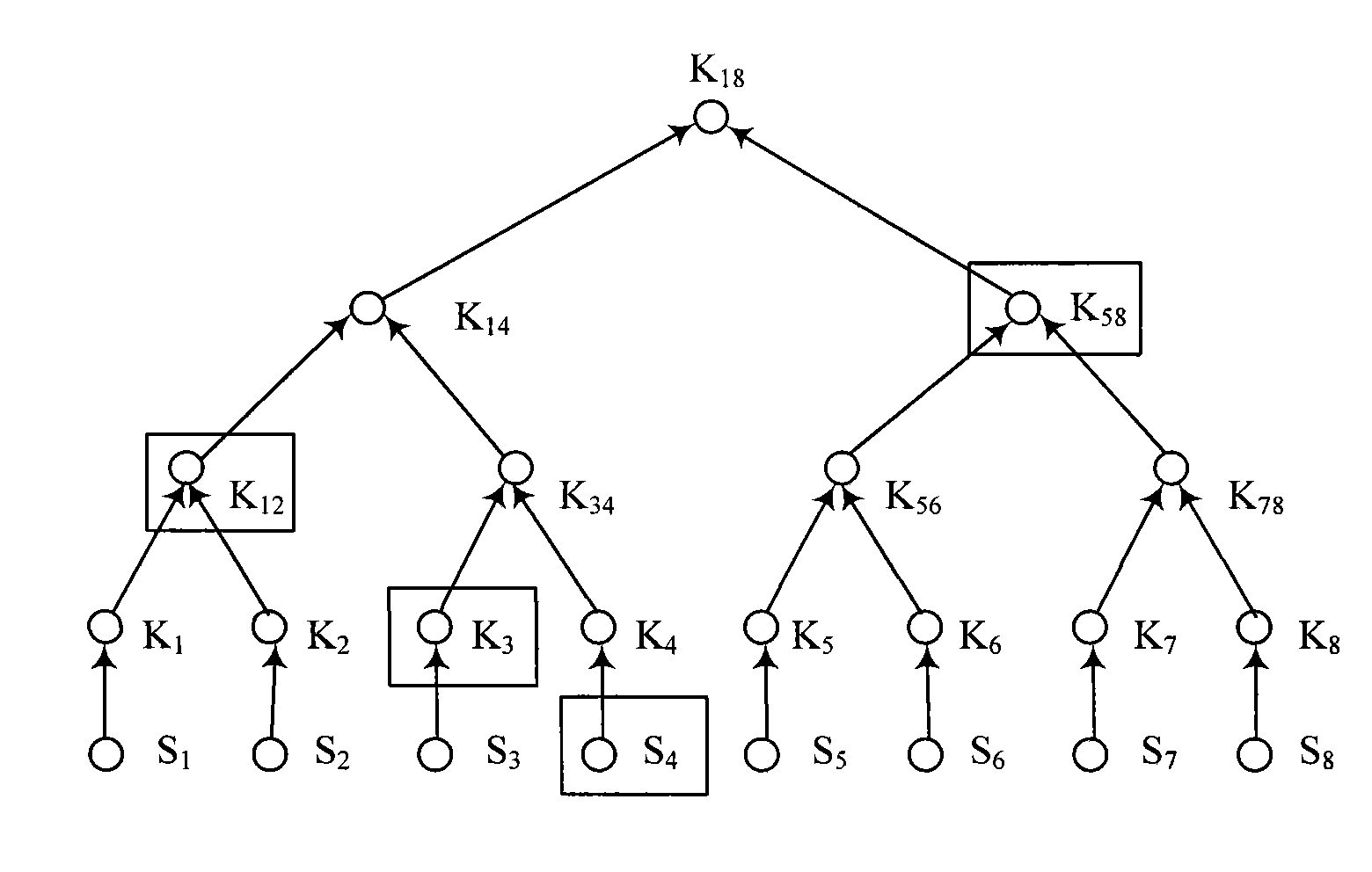
[0052] 1.1.2) According to N and n, BServer uses the pseudo-random function F to sequentially generate N keychains. The specific process is as follows: BServer randomly generates the initial key K of the Nth keychain N,n , using the hash function H, according to the equation K N,i =H(K N,i+1 ) to generate the remaining keys in the chain; then, use the second key of the previous key cha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com