Method and device for realizing docker network penetration through two-layer protocol stack in cloud computing environment
A technology of network protocol stack and cloud computing environment, which is applied in the field of realizing docker network penetration of two-layer protocol stack, which can solve the problems of memory time consumption and reduce CPU usage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
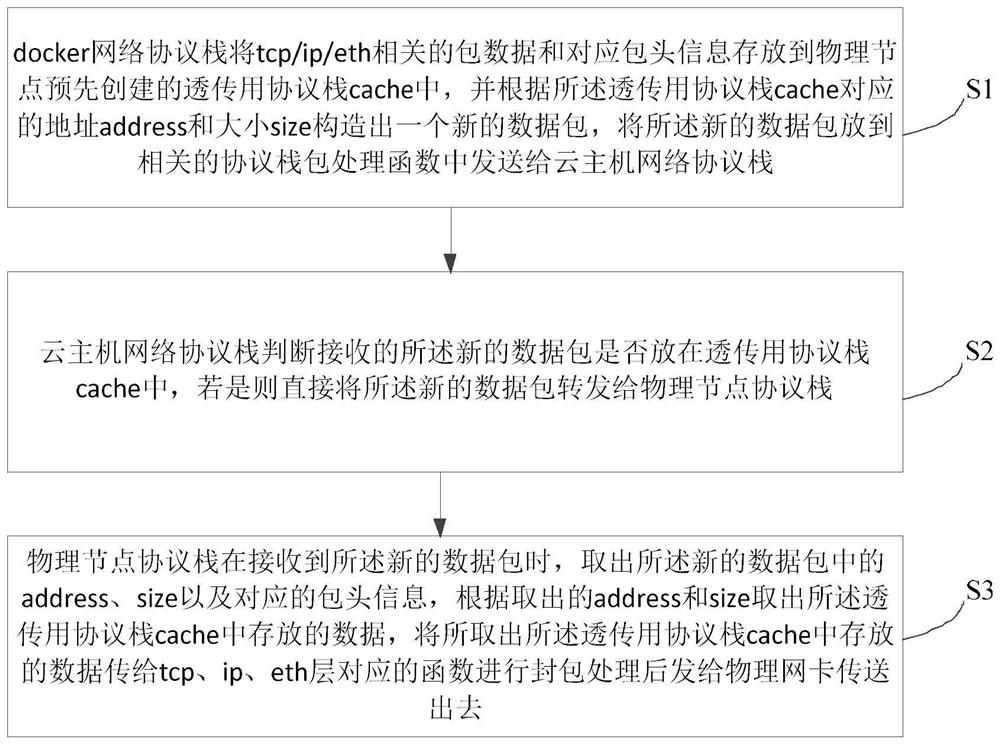
[0035] figure 1 It shows a schematic flow diagram of a method for implementing a docker network to penetrate a two-layer protocol stack in a cloud computing environment provided by an embodiment of the present invention, as shown in figure 1 As shown, the method for realizing docker network penetration through the two-layer protocol stack under the cloud computing environment of this embodiment includes:
[0036]S1. The docker network protocol stack stores tcp (transmission control protocol) / ip (interconnection protocol between networks) / eth (ethernet) related packet data and corresponding packet header information to the pre-created transparent transmission protocol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com