Identity authentication method and device and medium
A technology for identity authentication and terminal identity, which is applied in user identity/authority verification, secure communication devices, digital transmission systems, etc., and can solve the problems of weak security of identity authentication methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
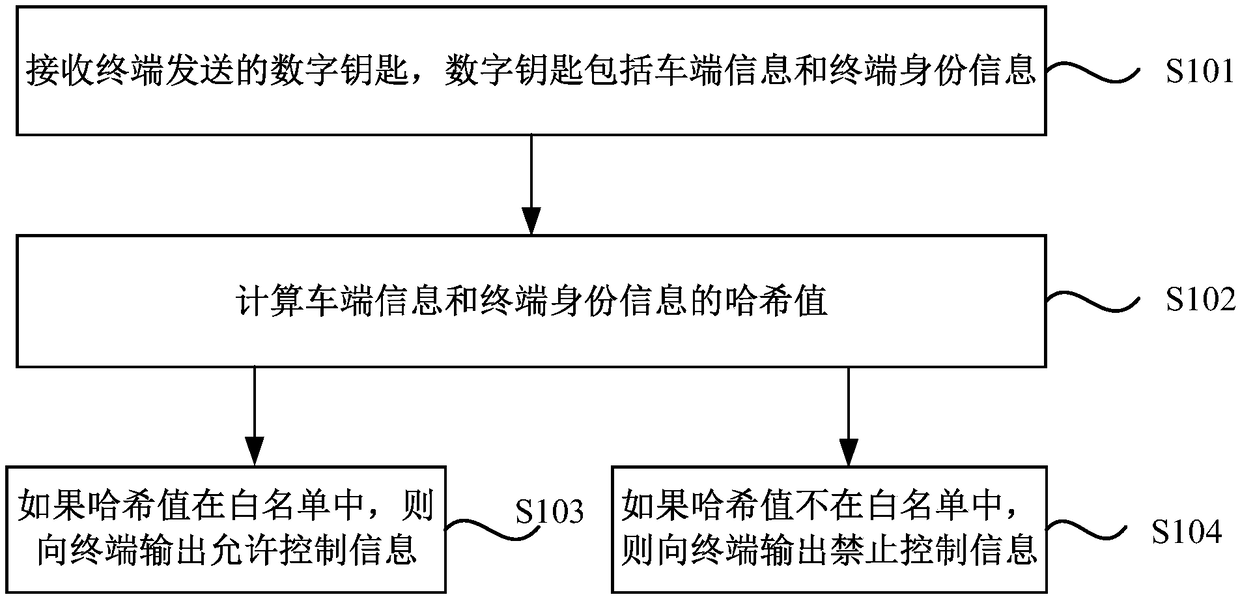
[0029] figure 1 It is a flow chart of the identity authentication method provided by Embodiment 1 of the present invention. The technical solution of this embodiment is applicable to the situation where the vehicle terminal verifies the identity of the terminal. The method can be executed by the identity authentication device provided in the embodiment of the present invention, and the device can be implemented in the form of software and / or hardware, and configured to be applied in a processor. The method specifically includes the following steps:
[0030] S101. Receive the digital key sent by the terminal, where the digital key includes vehicle information and terminal identity information.
[0031] If the terminal wants to control the vehicle through the digital key, it usually needs to send the digital key to the vehicle so that the vehicle can verify it. The digital key in this embodiment includes vehicle terminal information and terminal identity information, wherein ...
Embodiment 2
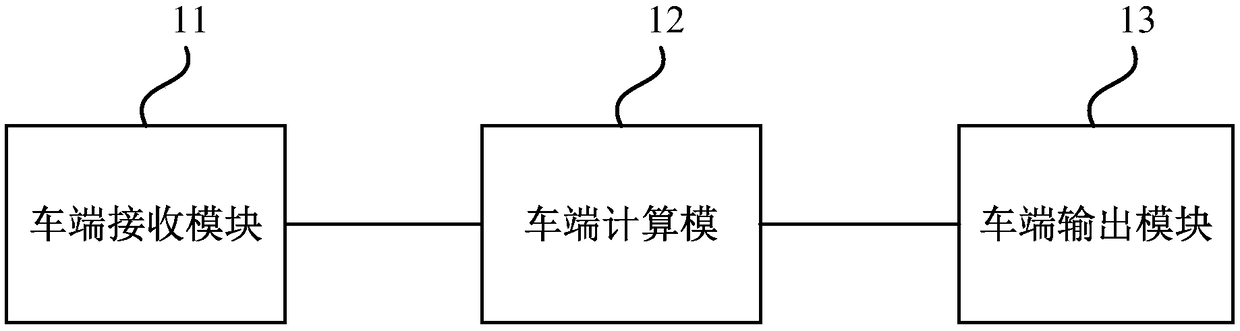
[0047] image 3 It is a structural block diagram of the identity authentication device provided by Embodiment 2 of the present invention. The device is used to execute the identity authentication method provided by any of the above embodiments, and the device may be implemented by software or hardware. The unit includes:
[0048] The car end receiving module 11 is used to receive the digital key, and the digital key includes car end information and terminal identity information;
[0049] Car end calculation module 12, for calculating the hash value of described car end information and terminal identity information;
[0050] The vehicle-side output module 13 is configured to output permission control information if the hash value is in the white list.
[0051] Among them, the car-side information includes car-side identity information and random numbers, and the digital key is the master digital key or the shared digital key.
[0052] The calculation module at the vehicle e...
Embodiment 3
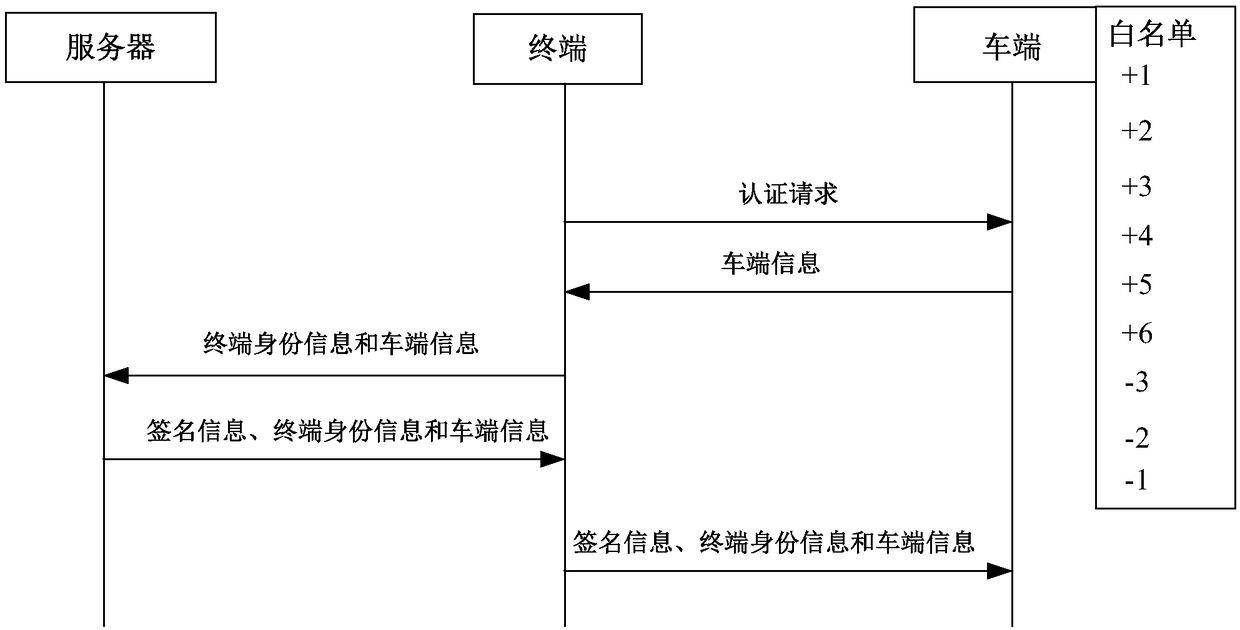
[0058] Figure 4 It is a flow chart of the identity authentication method provided by Embodiment 3 of the present invention. The technical solution of this embodiment is applicable to the situation that the vehicle terminal verifies the identity of the terminal, and is applied to the terminal of the vehicle-machine system composed of the server, the terminal and the vehicle. The method can be executed by the identity authentication device provided in the embodiment of the present invention, and the device can be implemented in the form of software and / or hardware, and configured to be applied in a processor. The method specifically includes the following steps:
[0059] S201. Send a digital key to the vehicle terminal, where the digital key includes vehicle terminal information and terminal identity information.
[0060] If the terminal wants to control the vehicle through the digital key, it usually needs to send the digital key to the vehicle so that the vehicle can verify...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com