Patents
Literature
41results about How to "Convenient identity verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
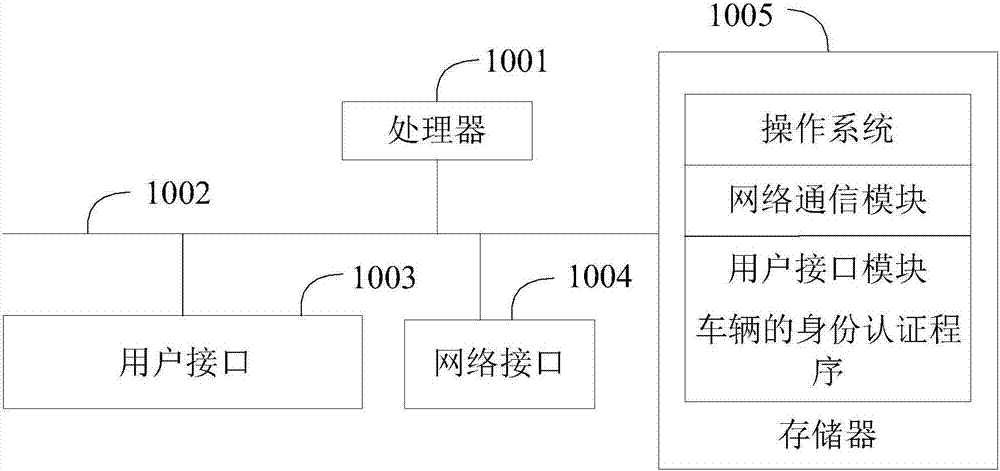
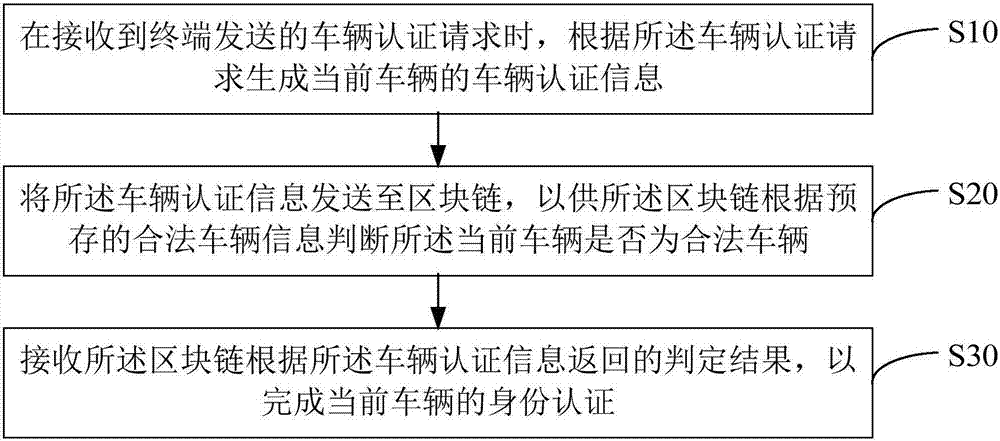
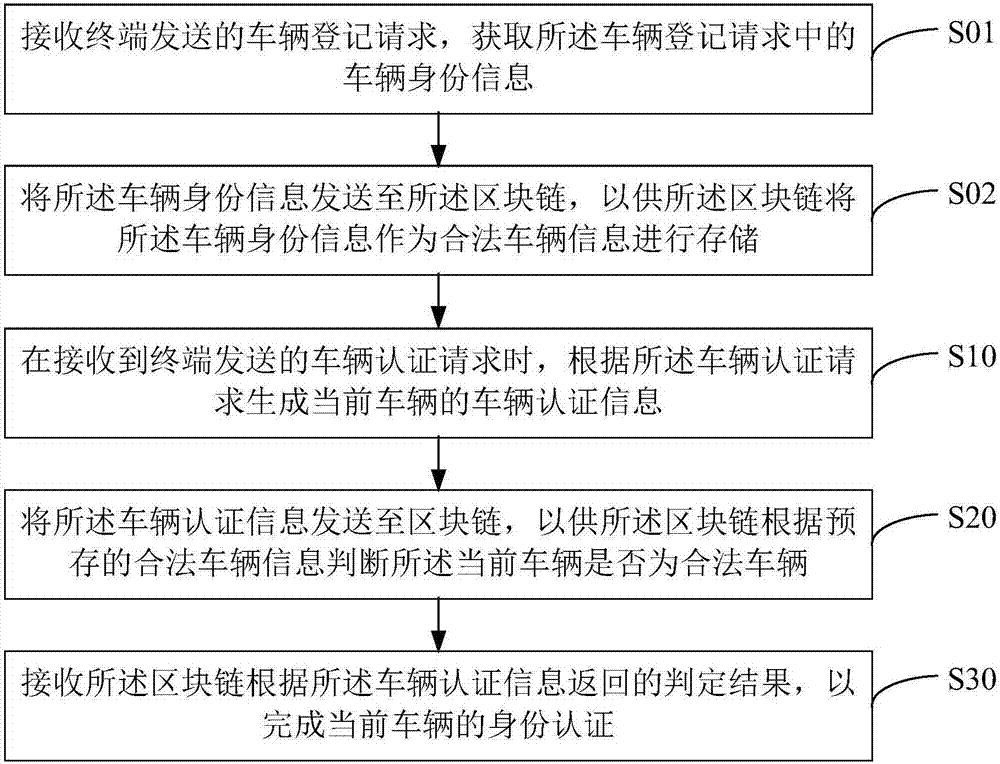
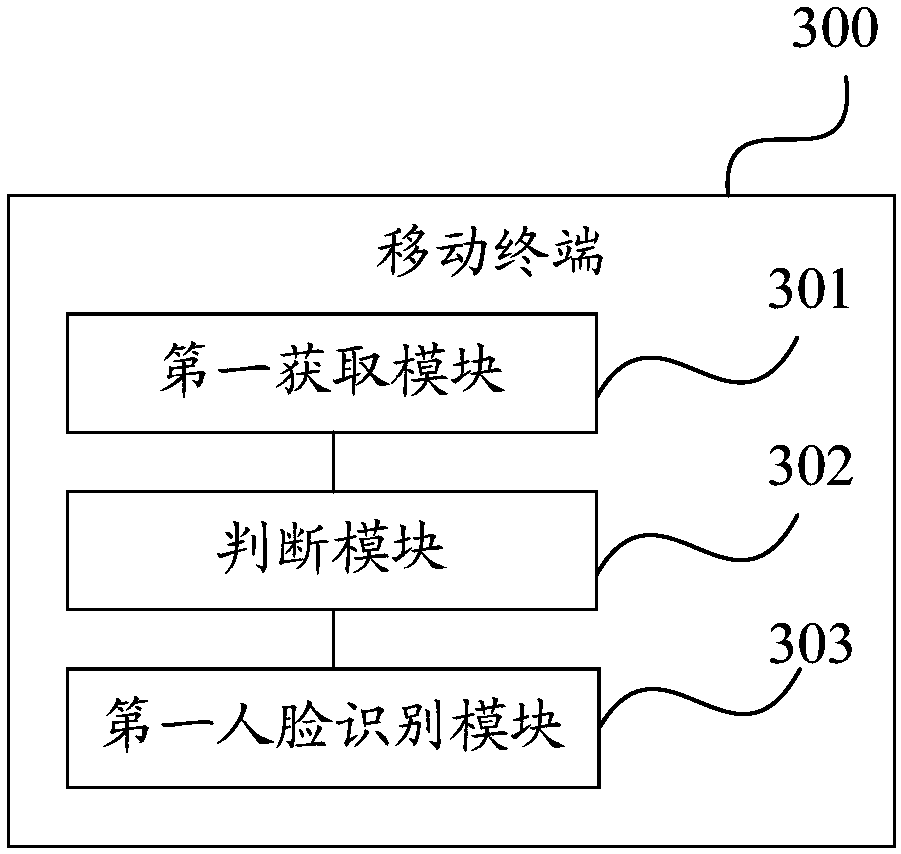
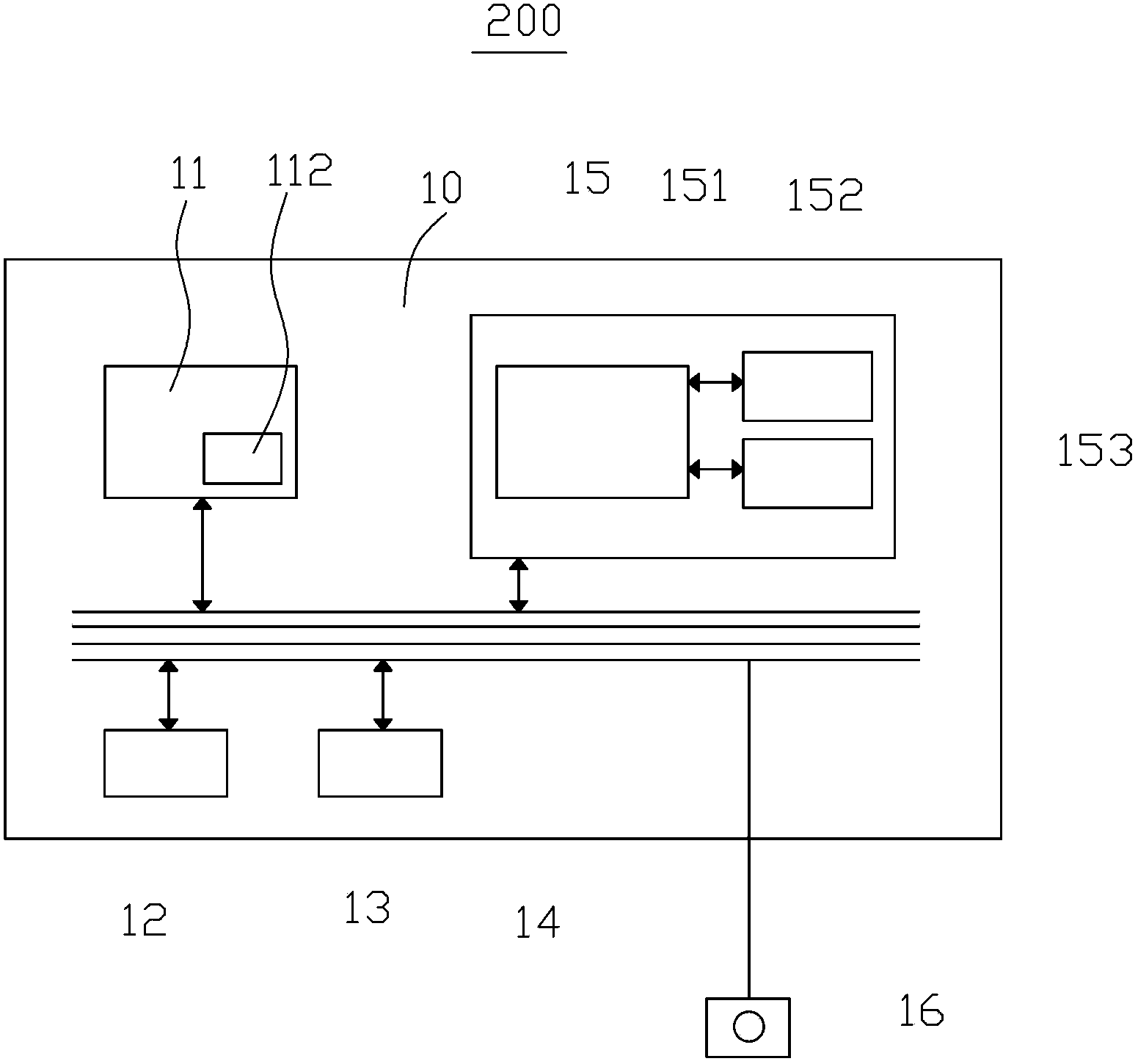
Vehicle identity authentication method and apparatus, and computer readable storage medium
InactiveCN107465673AAuthentication securityConvenient identity verificationRoad vehicles traffic controlTransmissionComputer terminalEmbedded system
The invention provides a vehicle identity authentication method and apparatus, and a computer readable storage medium. The vehicle identity authentication method comprises the following steps: when a vehicle authentication request sent by a terminal is received, generating vehicle authentication information of a current vehicle according to the vehicle authentication request; sending the vehicle authentication information to a block chain, so that the block chain judges whether the current vehicle is a legal vehicle according to pre-stored legal vehicle information; and receiving a judgment result returned by the block chain according to the vehicle authentication information so as to accomplish the identity authentication of the current vehicle. By adoption of the manner, the identity authentication of the vehicle can be accomplished securely and conveniently, the vehicle identity authentication precision is improved, the information sent by illegal vehicle is not received, thereby improving the anti-interference ability of the communication between the vehicles in the system, and the technical problem that the communication between the vehicles in the CACC is interfered easily is solved.
Owner:SHENZHEN ECHIEV AUTONOMOUS DRIVING TECH CO LTD
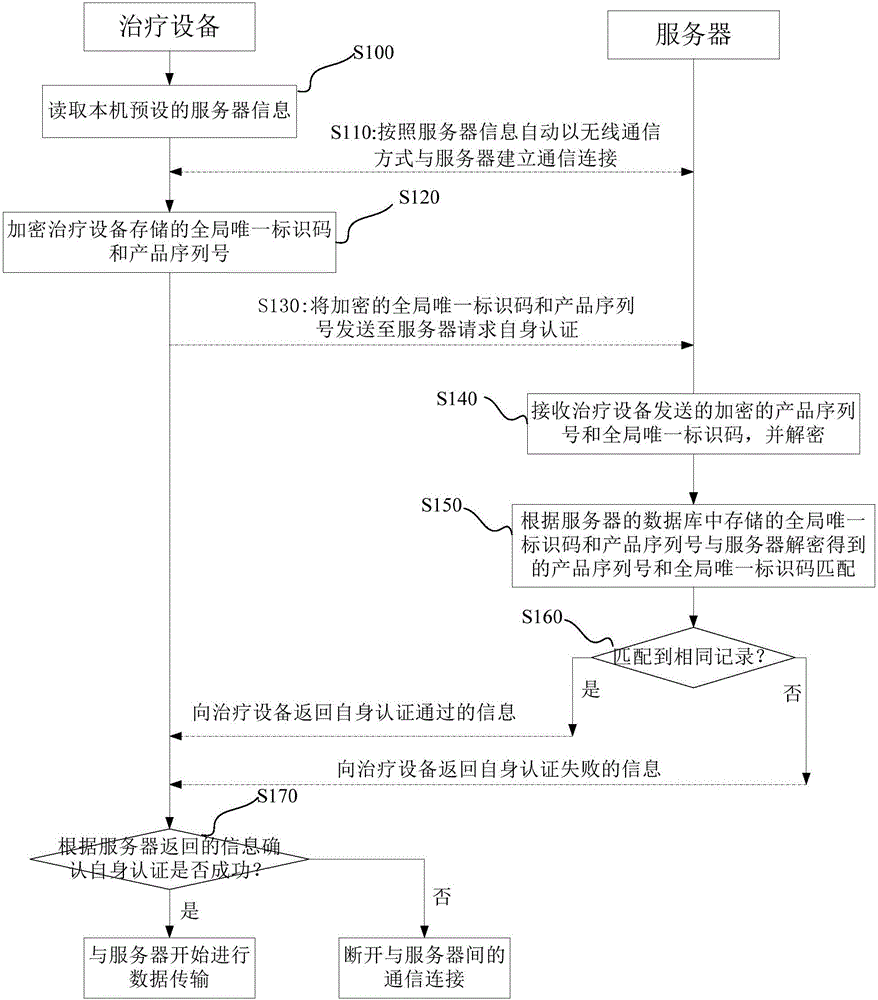
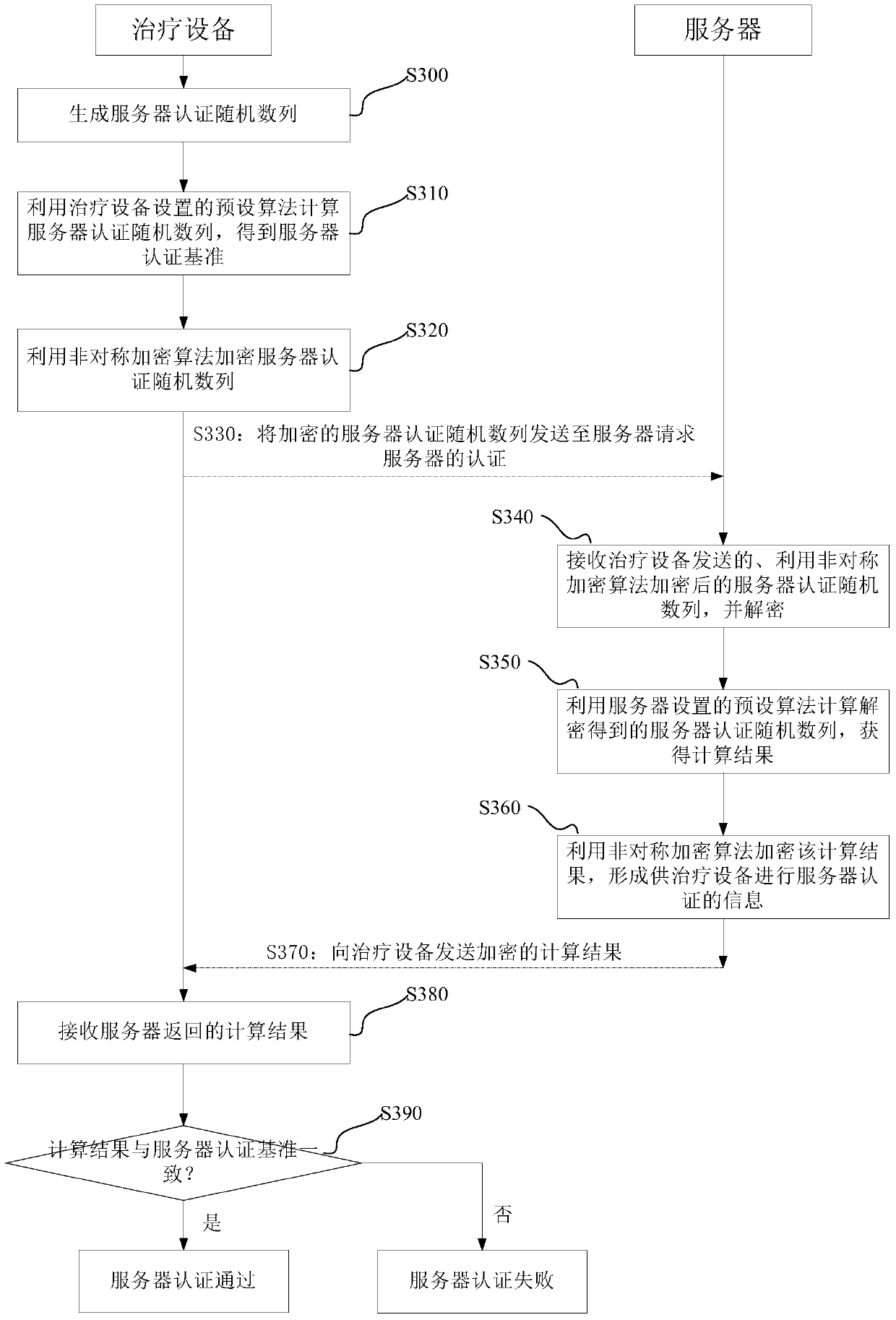
Authentication method, authentication device, authentication system and treatment equipment
ActiveCN105871857AAvoid same-identity situationsPrevent peepingTransmissionData transmissionAuthentication system
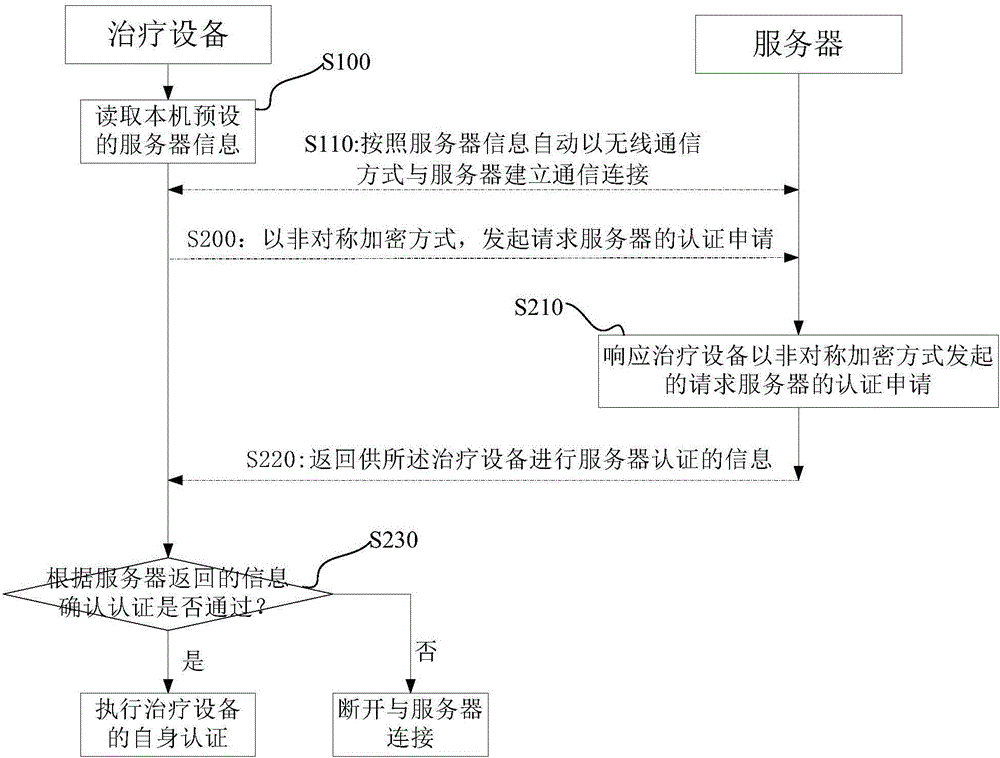
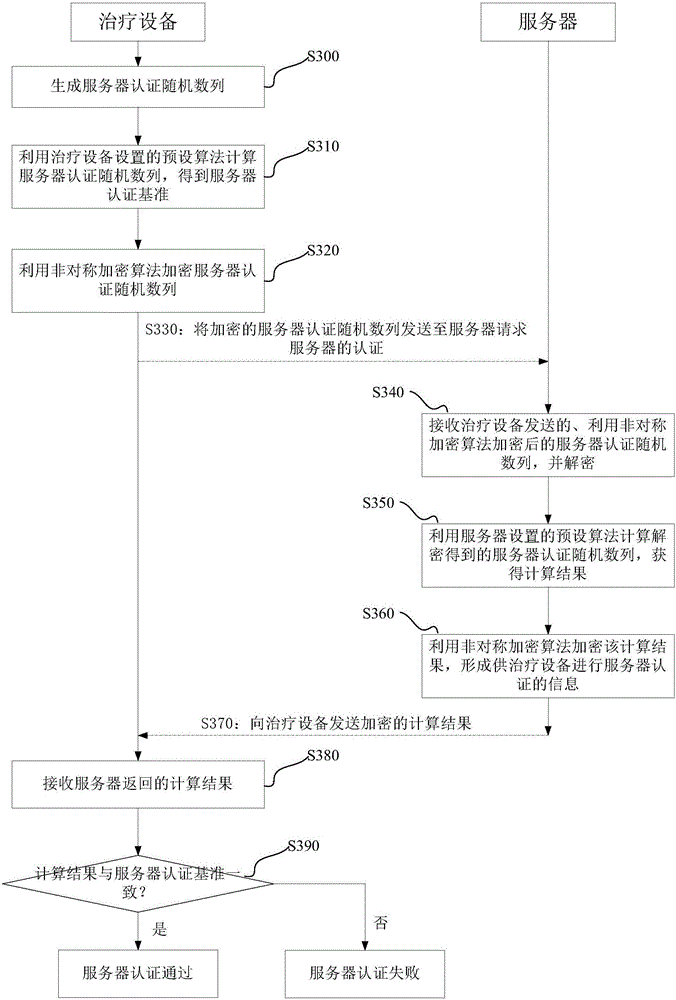
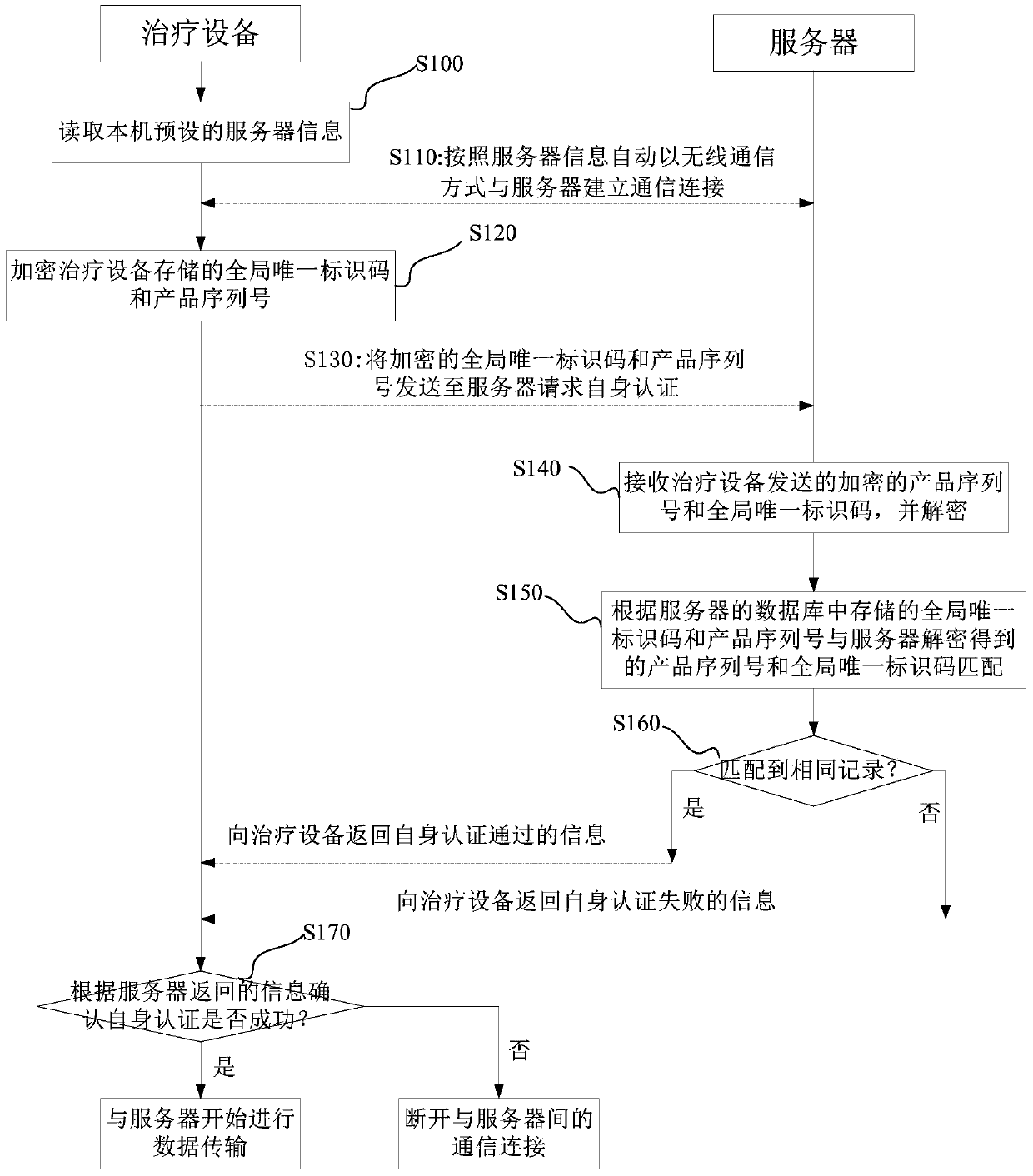
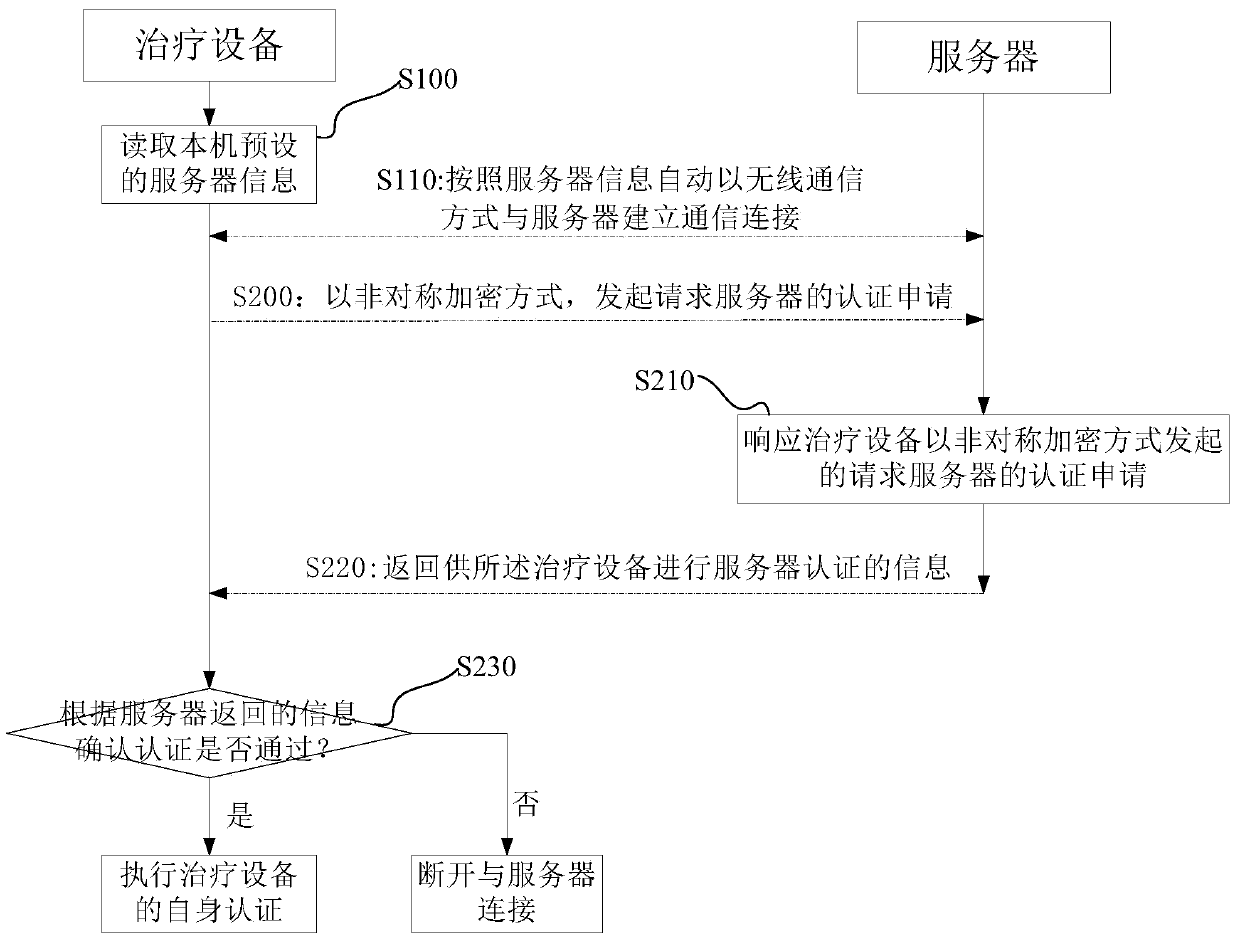
The invention discloses an authentication method, an authentication device, an authentication system and treatment equipment. The authentication method comprises the steps of reading server information which is preset by a local machine, automatically establishing communication connection according to the server information in a wireless communication manner; and initiating self authentication by the treatment equipment, wherein self authentication comprises reading a global unique identification code and a product serial number which are pre-stored by the local machine; encrypting the global unique identification code and the product serial number which are stored in the treatment equipment, and transmitting the encrypted global unique identification code and the product serial number to a server for requesting self authentication; confirming a self authentication result according to information which returns from the server; if self authentication passes, starting data transmission with the server; and if self authentication fails, disconnecting communication connection with the server. The authentication method, the authentication device, the authentication system and the treatment equipment reduce operation difficulty and complexity in identity authentication.
Owner:BMC MEDICAL
Face recognition method and electronic equipment
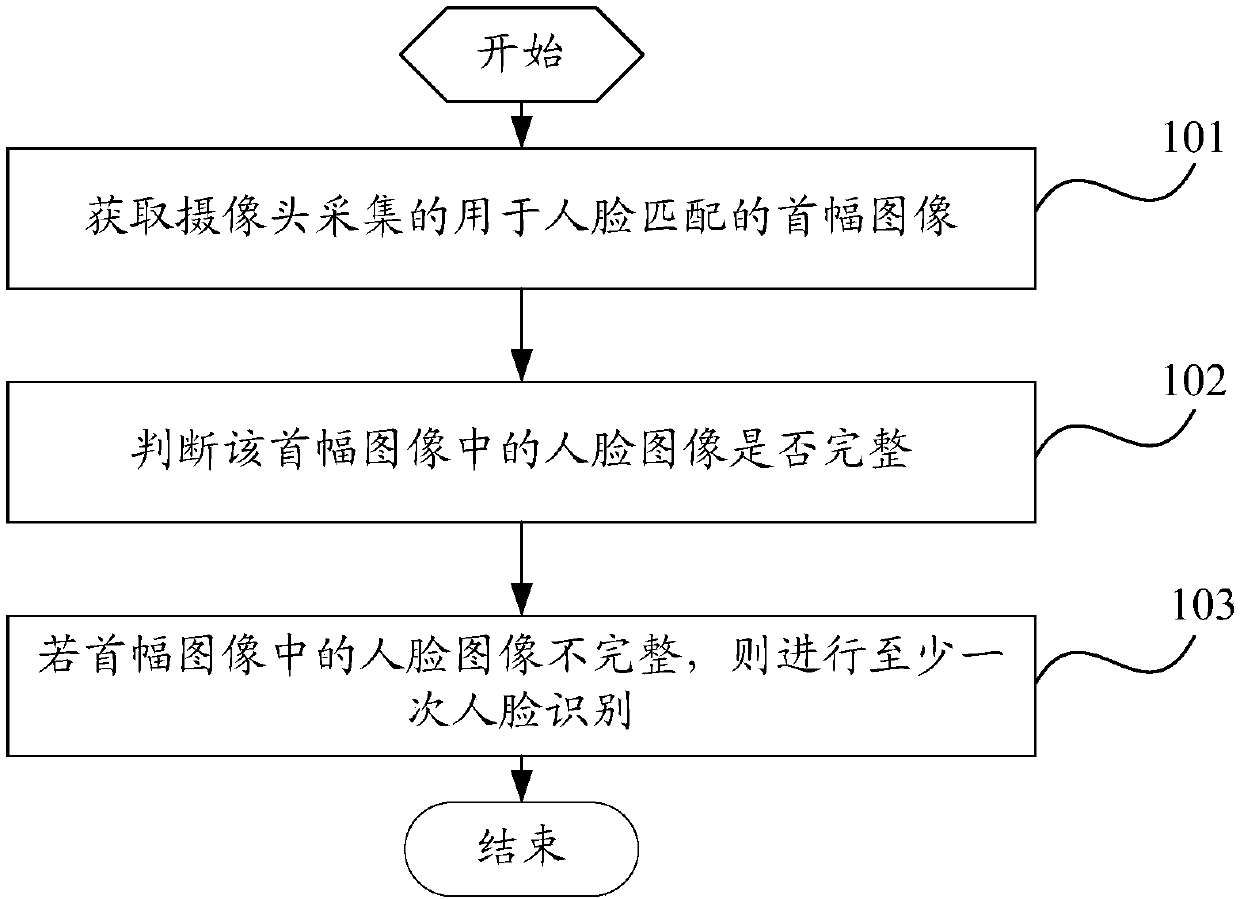
InactiveCN107679514AReduce the number of operationsImprove user experienceCharacter and pattern recognitionPattern recognitionElectric equipment
The invention provides a face recognition method and electronic equipment. The face recognition method comprises the steps that a first image collected by a camera and used for face matching is acquired; whether a face image in the first image is complete is judged; and if the face image in the first image is not complete, face recognition is performed at least once. According to the technical scheme, when it is detected that the face image is not complete, face recognition is automatically performed at least once, that is, after the risk that face matching failure is caused by incompletenessof the image for face matching is detected, an image is collected automatically and continuously for next face recognition. In this way, the number of times of operation by a user for triggering facerecognition during face recognition is reduced, convenience is brought to identity authentication, and the usage experience of the user is improved.
Owner:VIVO MOBILE COMM CO LTD
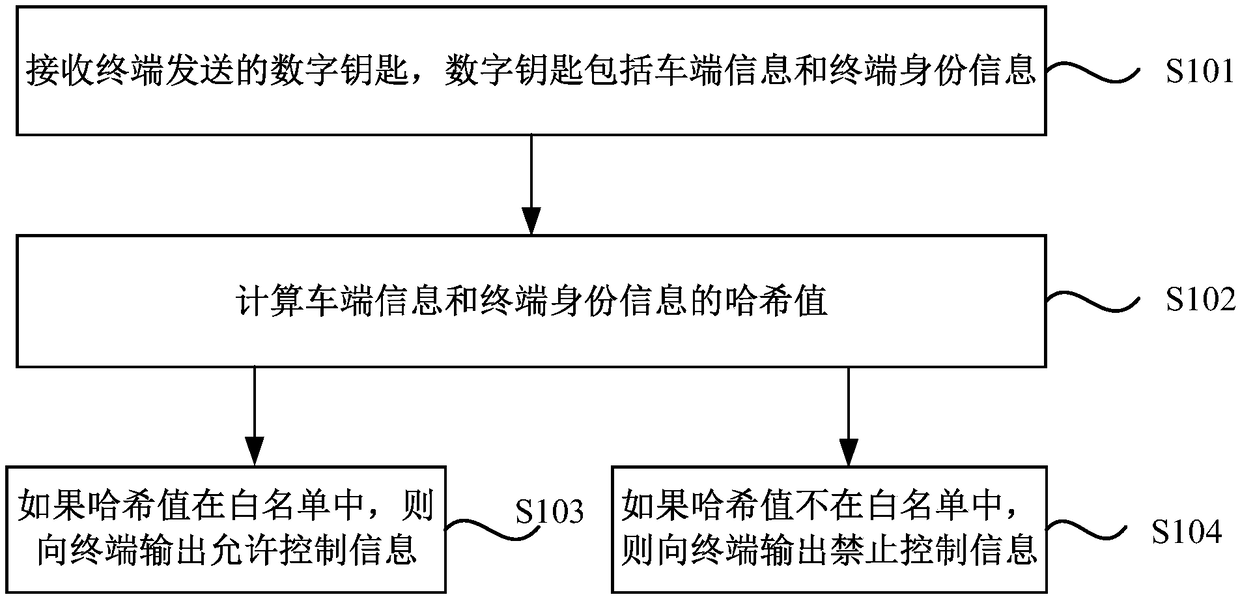
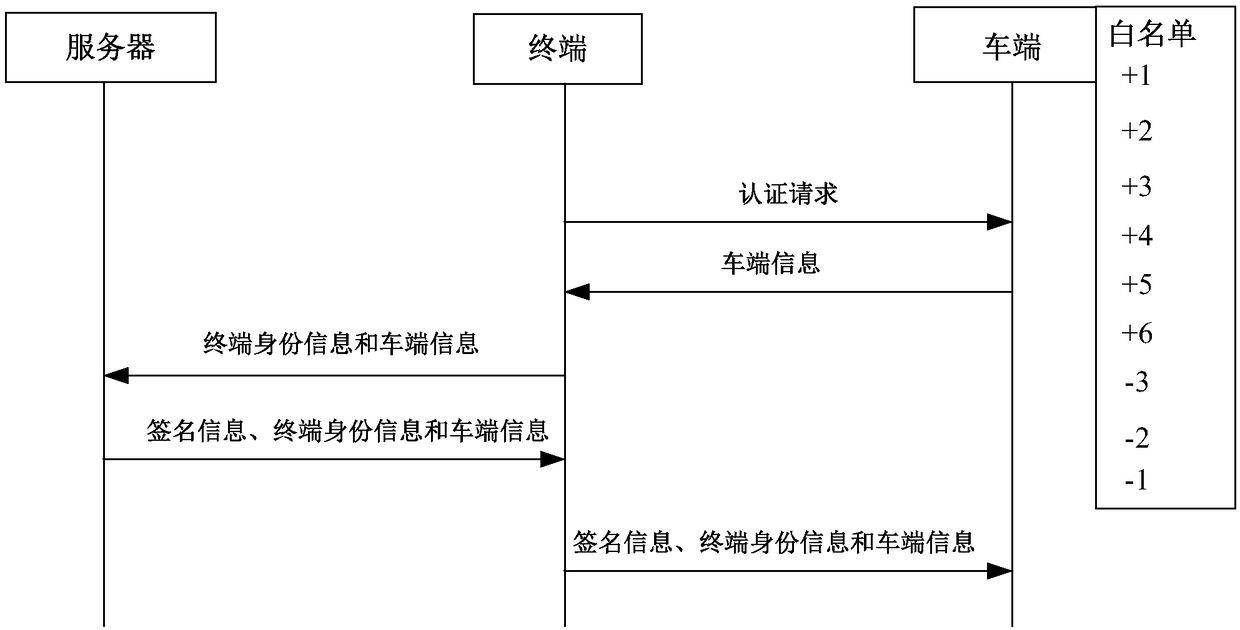
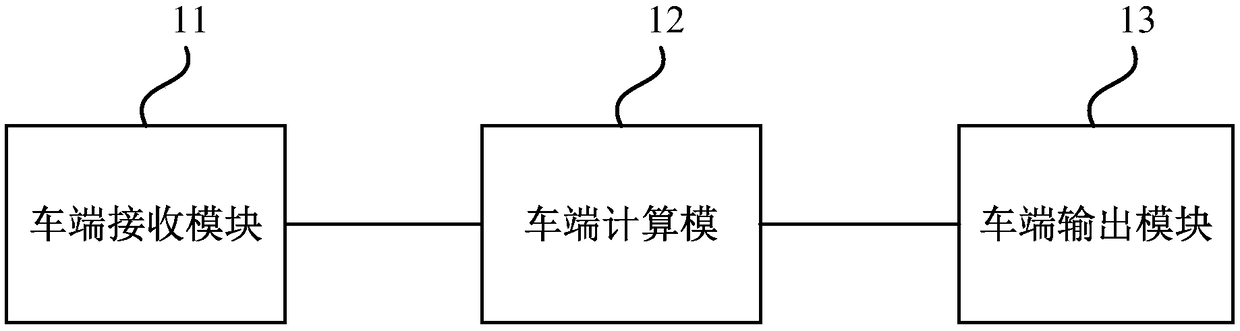
Identity authentication method and device and medium
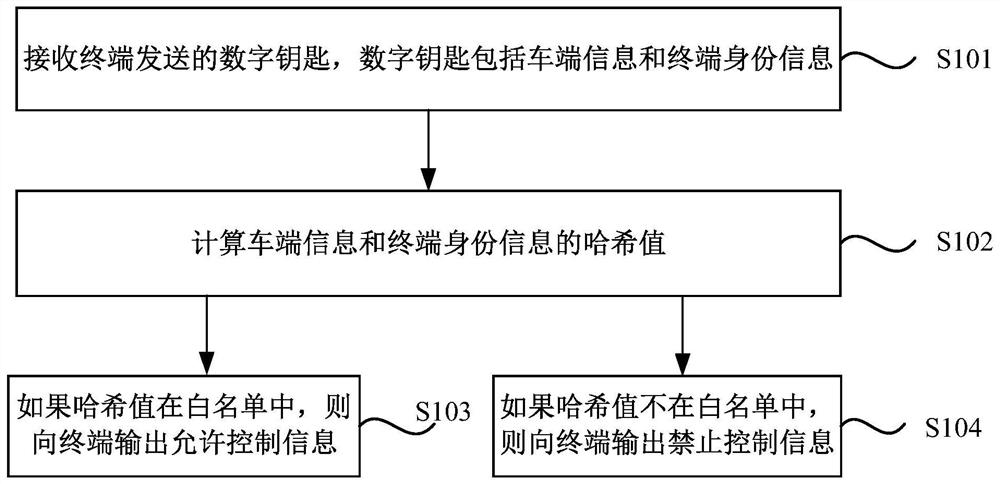
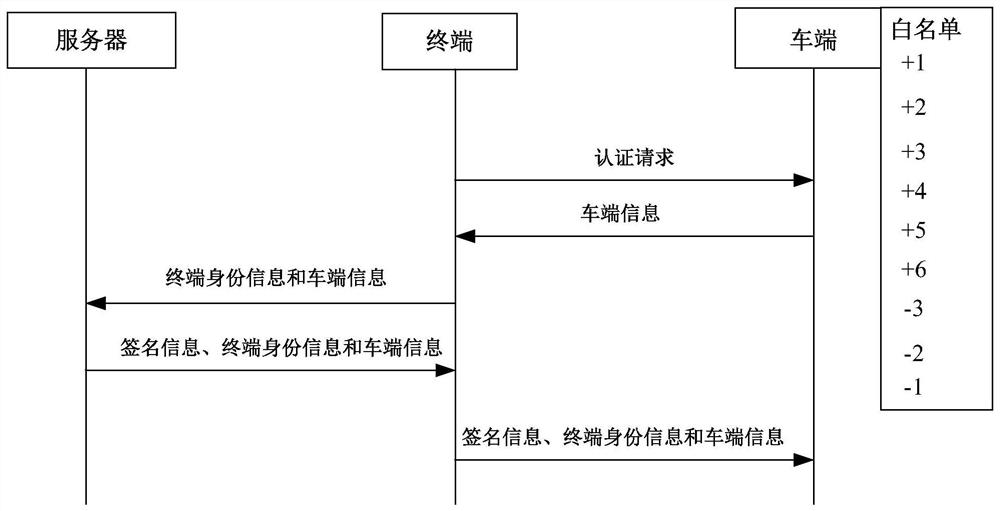
ActiveCN109361718AConvenient identity verificationPrevent leakageUser identity/authority verificationInformation technology support systemComputer terminalAuthentication
The embodiment of the invention discloses an identity authentication method and device and a medium. The method is applied to a vehicle of a system composed of a server, a terminal and the vehicle, and comprises the following steps: receiving a digital key sent by the terminal, wherein the digital key comprises vehicle end information and terminal identity information; calculating harsh values ofthe vehicle end information and the terminal identity information; and if the harsh value is in a white list, outputting allowable control information. The problem that the identity authentication method in the prior art is relatively low in security is solved, and a technical effect of effectively protecting user information is achieved.
Owner:上海银基信息安全技术股份有限公司
Method, devices and system for user identity authentication
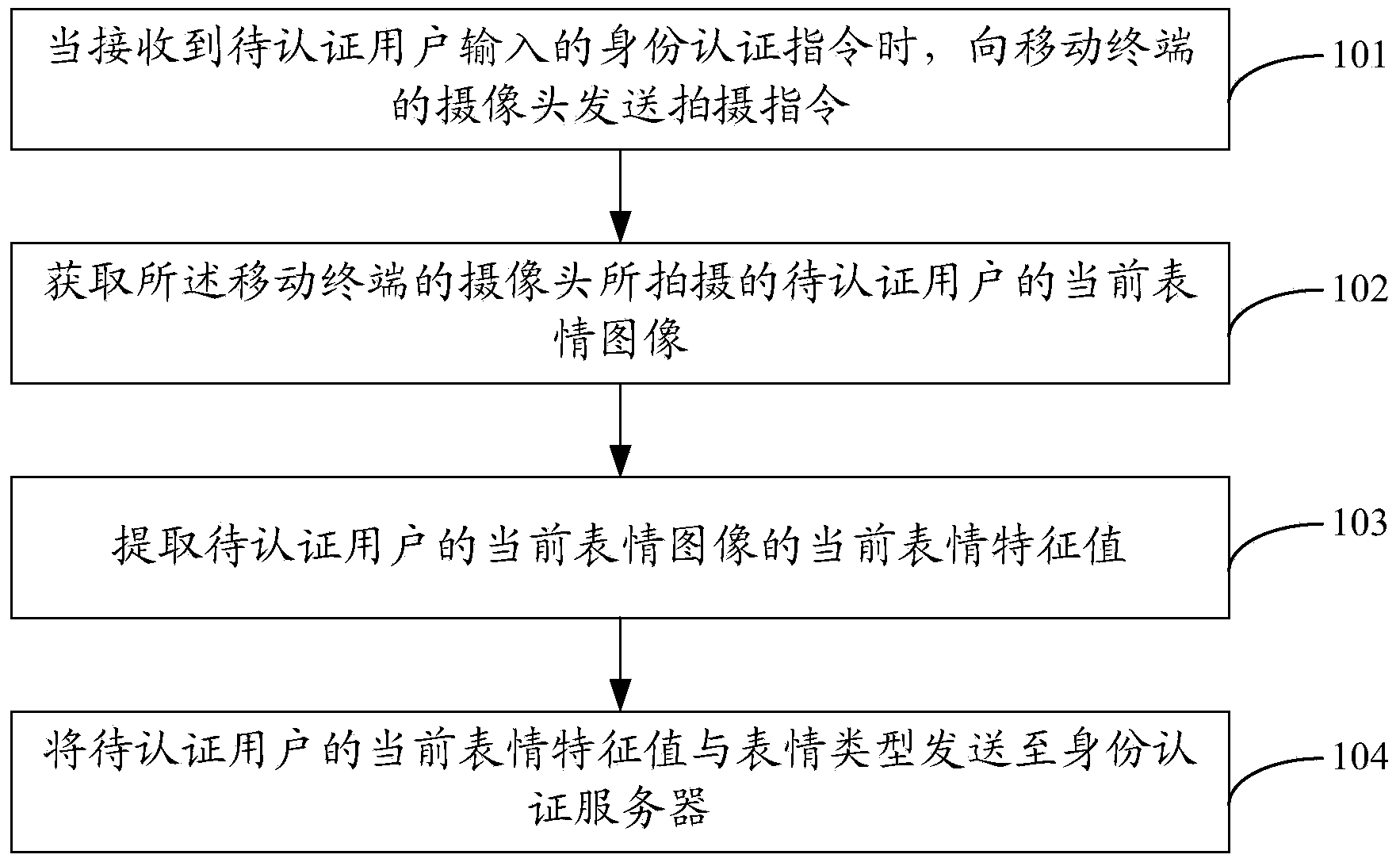
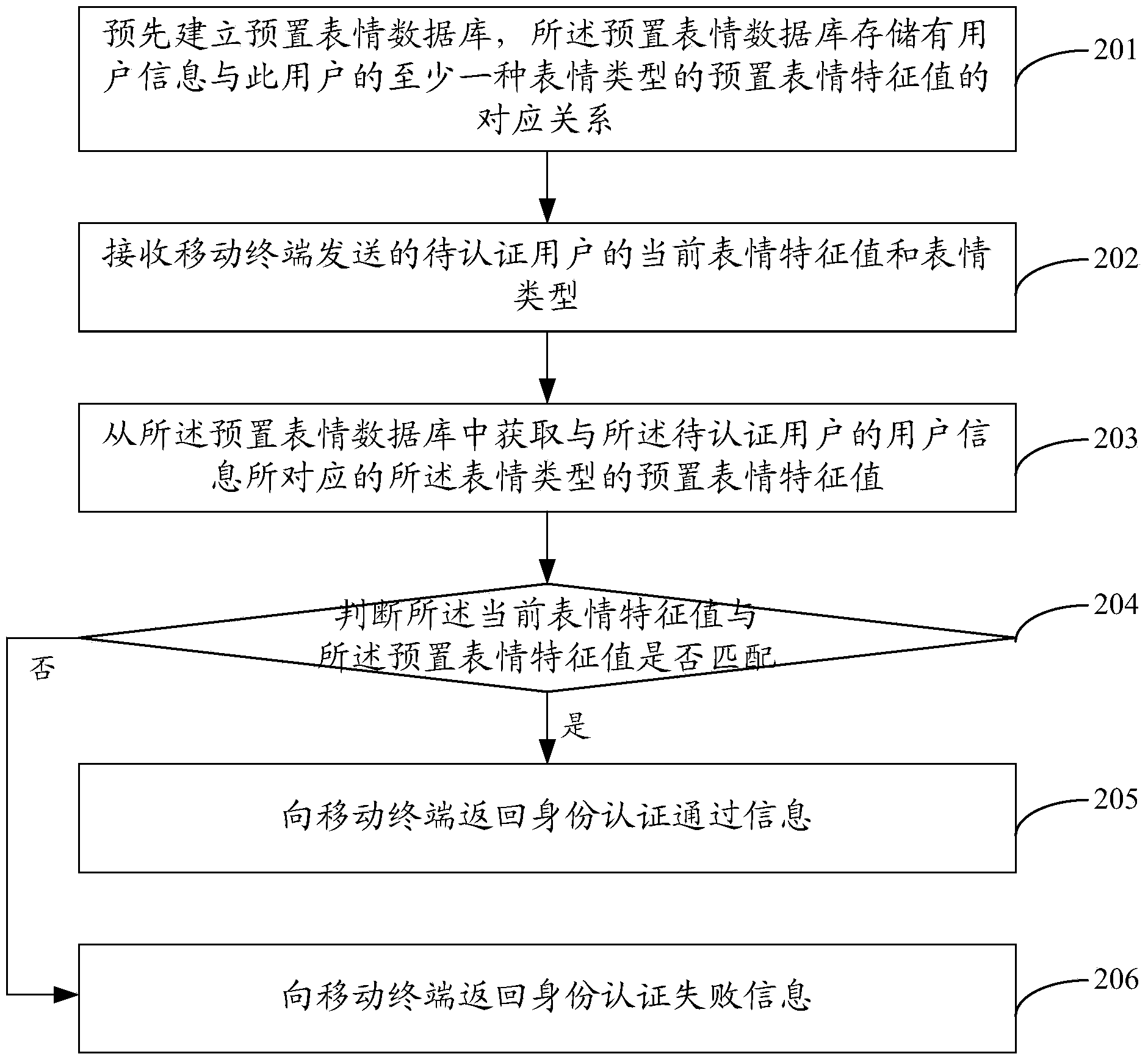
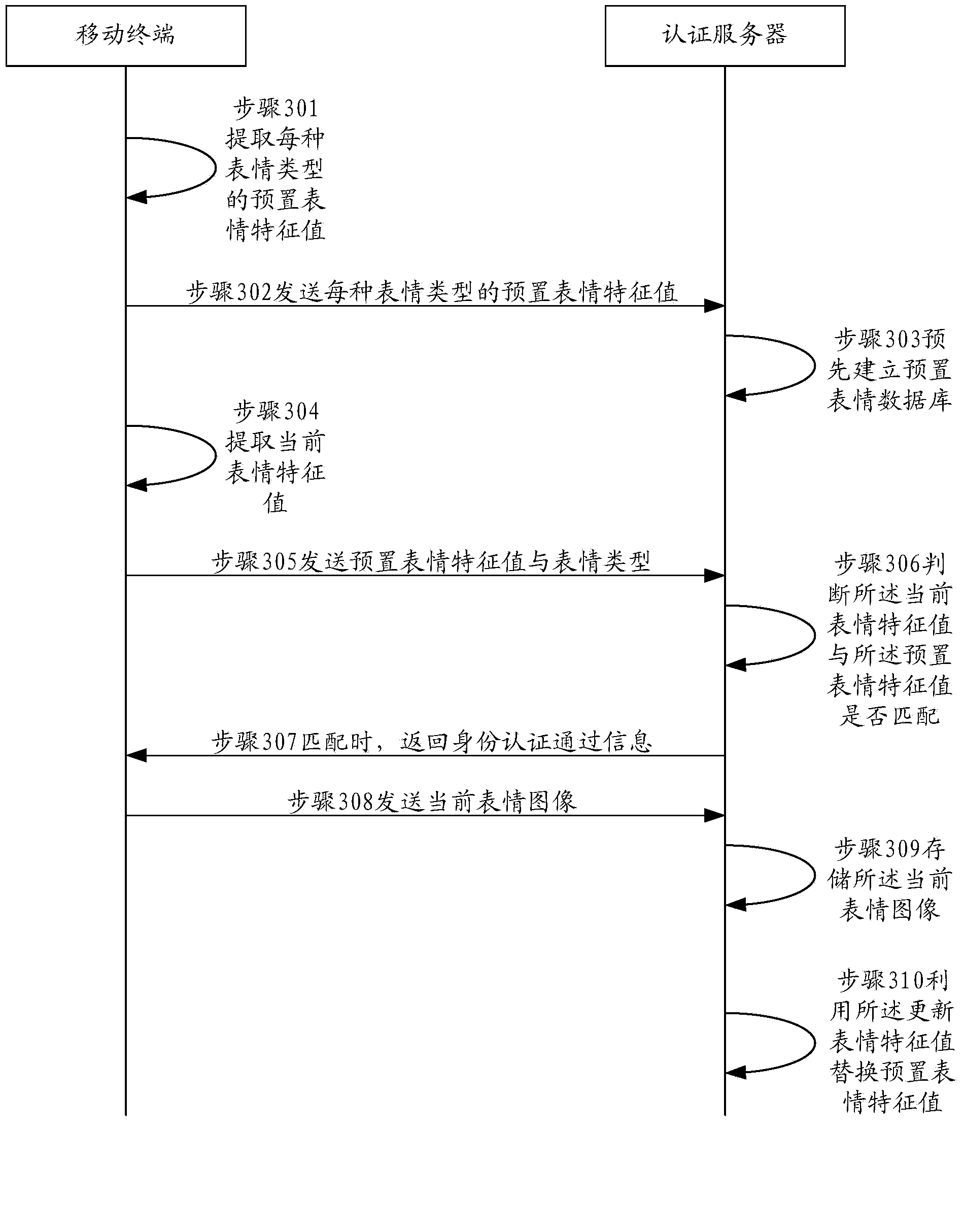
InactiveCN104270253AConvenient identity verificationEasy to implementUser identity/authority verificationSecurity arrangementPasswordAuthentication server
The invention provides a method, devices and a system for user identity authentication. A mobile terminal obtains a current expression image, taken by a camera of the mobile terminal, of a user to be authenticated, a current expression feature value of the current expression image of the user to be authenticated is extracted, and the current expression feature value and the expression type of the user to be authenticated are sent to an identity authentication server. The identity authentication server receives the current expression feature value and the expression type of the user to be authenticated, obtains a preset expression feature value of the expression type corresponding to user information of the user to be authenticated from a preset expression database and judges whether the current expression feature value is matched with the preset expression feature value, and if yes, identity authentication passing information is returned. By the adoption of the method for achieving user identity authentication by obtaining the current expression image of the user to be authenticated, no extra equipment such as a dynamic password card needs to be carried, user identity authentication is achieved conveniently and rapidly, no extra cost consumption is generated, and safety is high.
Owner:CHINA CONSTRUCTION BANK
Automatic walking equipment, code resetting method thereof and automatic walking system
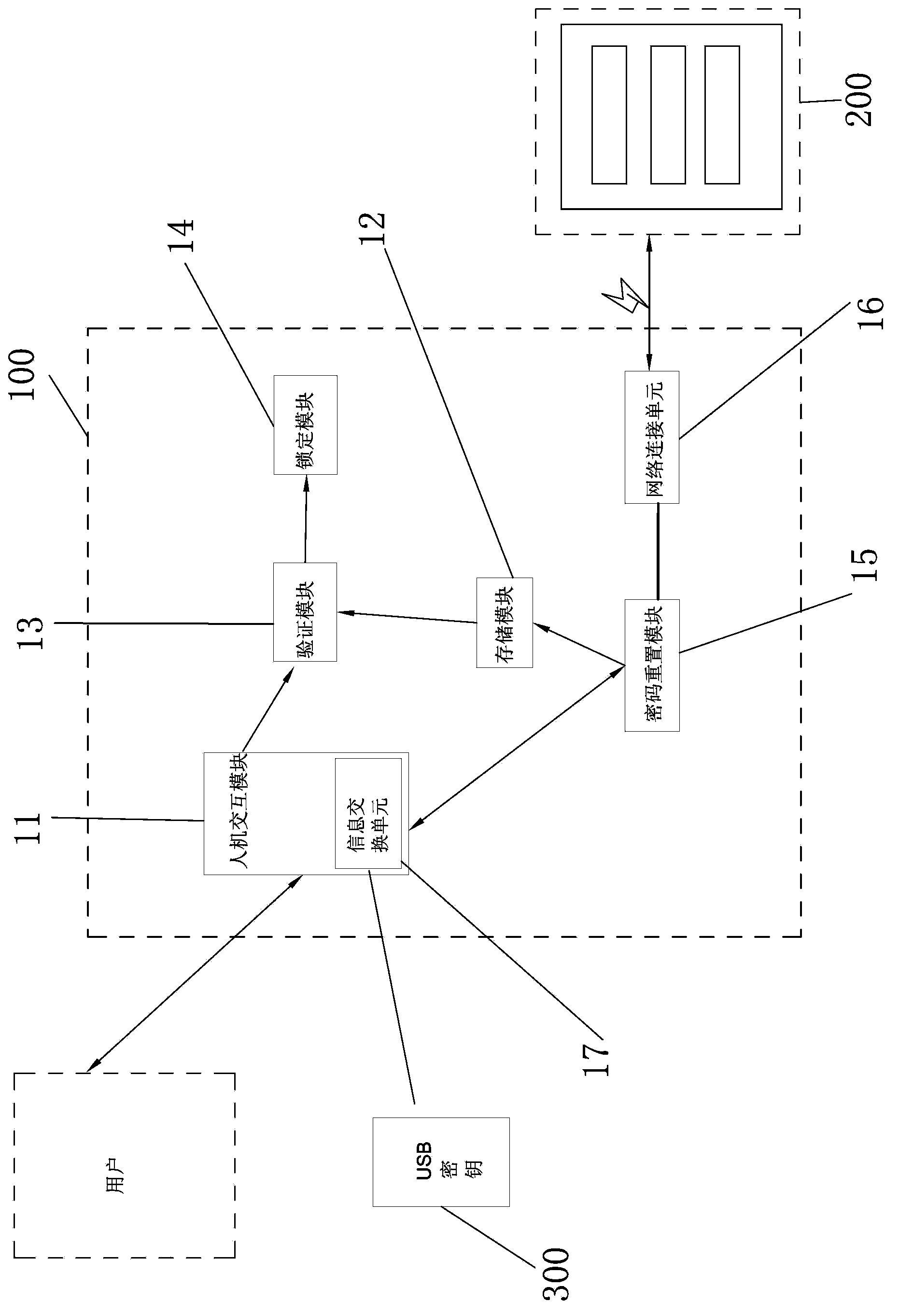
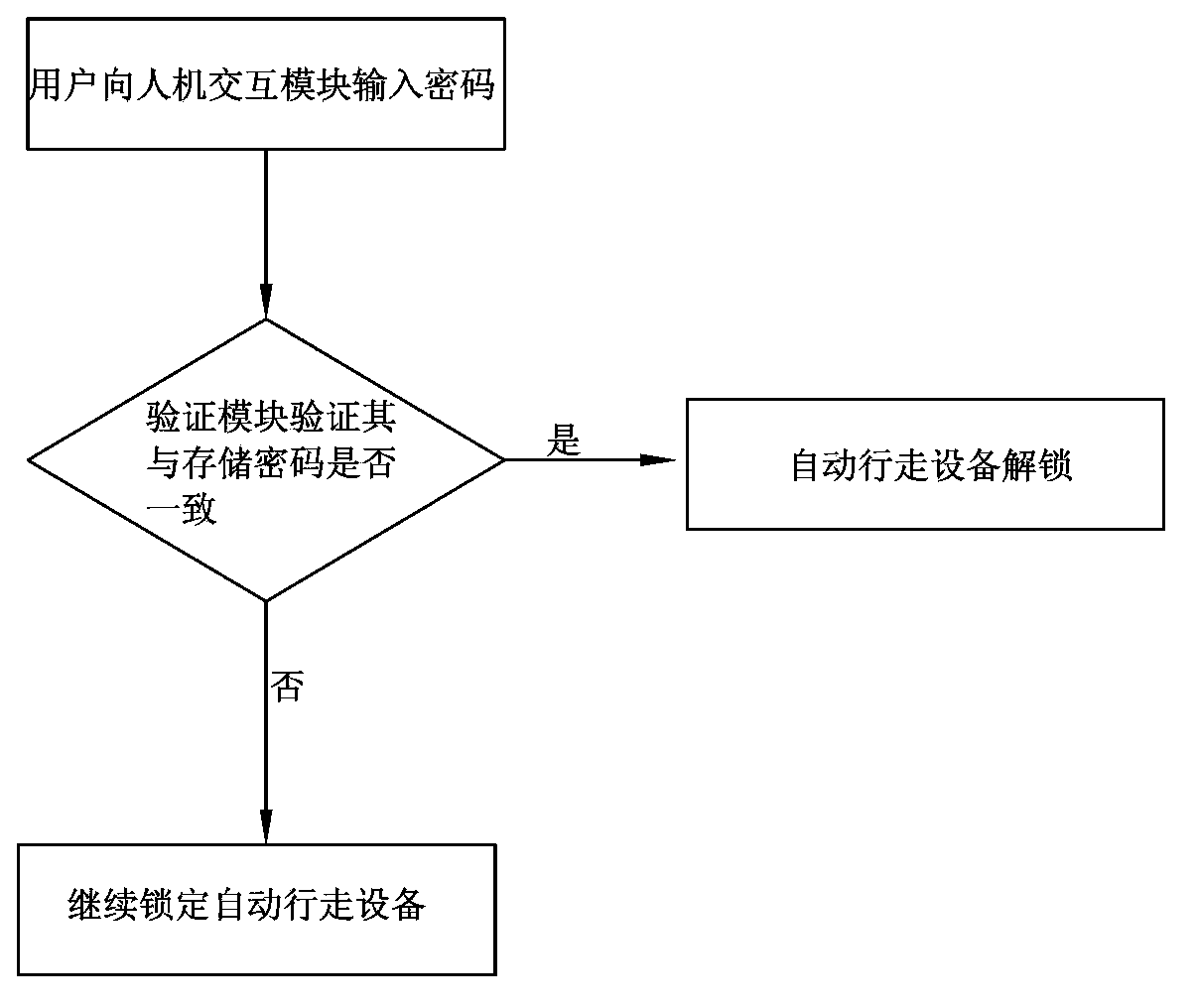
InactiveCN103473497AUnrestricted working hoursEasy and fast handlingDigital data authenticationNetwork connectionComputer module
Automatic walking equipment comprises a code protection device; the code protection device comprises a man-machine interaction module, a storage module, a verification module and a locking module; the code protection device also comprises a code resetting module; the code resetting module is connected with the storage module and comprises a network connection unit capable of being connected to a terminal service website; the code resetting module sends a code resetting request and identify verifying information to the terminal service website by the network connection unit and resets the code in the storage module to the original code after receiving the confirmation information fed from the terminal service website. When a user forgets the code, the code resetting can be started by the code resetting module, and the code of the automatic walking equipment can be restored to the original code, so the locking of the automatic walking equipment can be relieved.
Owner:POSITEC POWER TOOLS (SUZHOU) CO LTD
Digital certificate issuing method, verification method and system
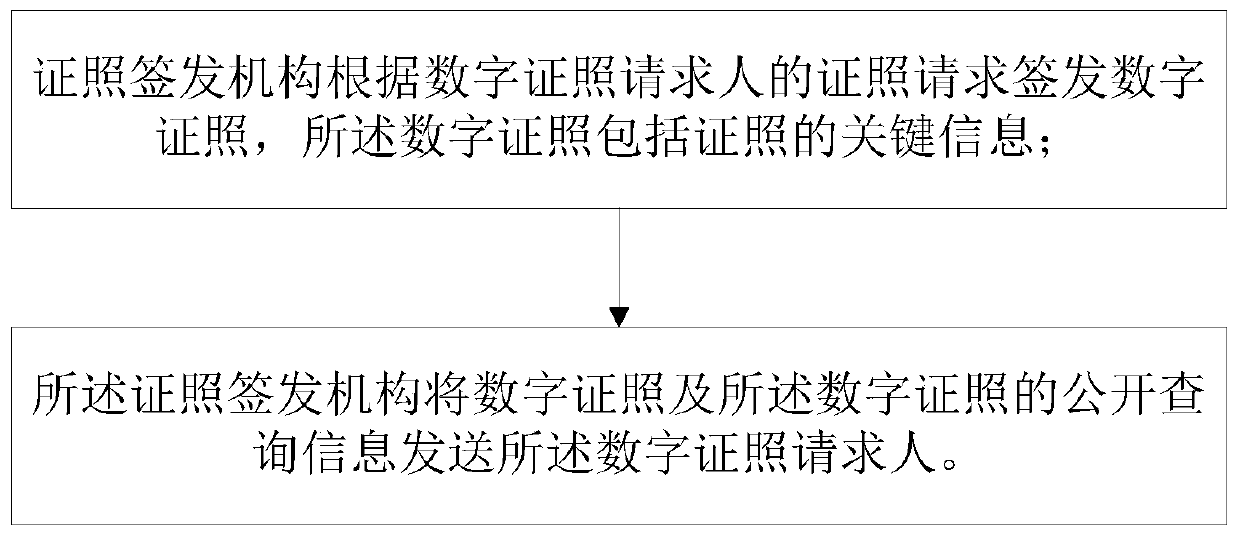
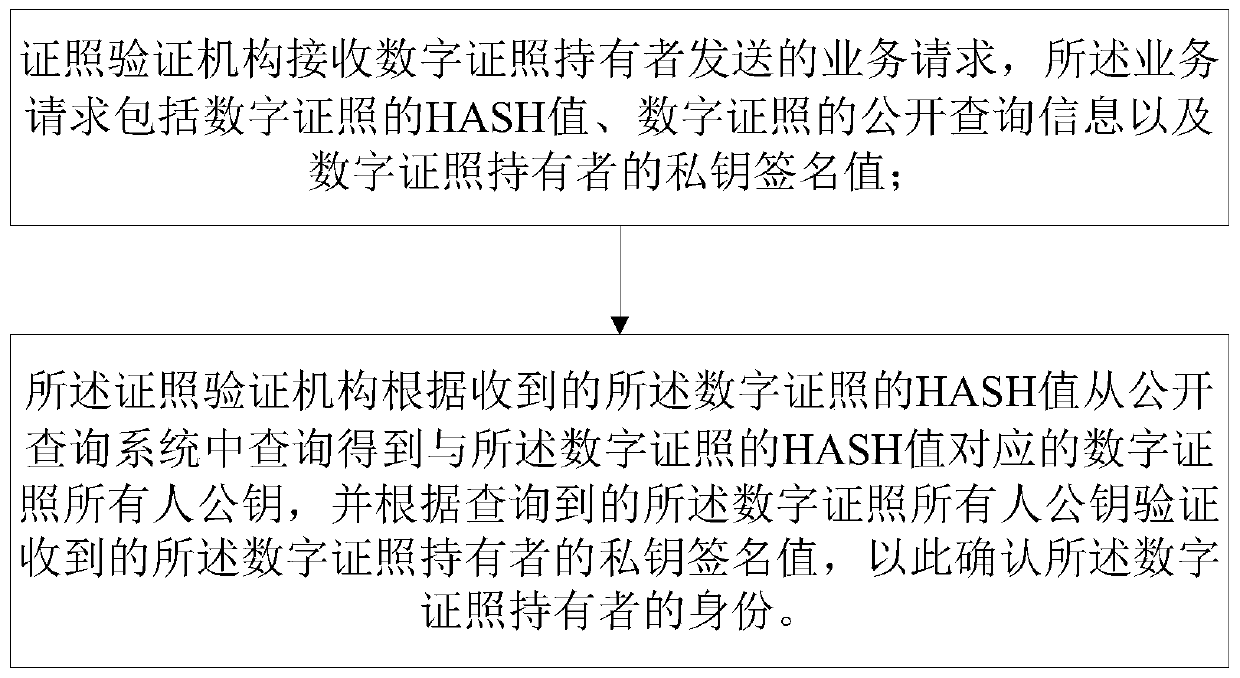
InactiveCN110119598AEnsure consistencyPrevent leakageProgram/content distribution protectionValidation methodsNon-interactive zero-knowledge proof
The invention relates to a digital certificate issuing method, a verification method and a system thereof. The digital certificate issuing method comprises the following steps that a certificate issuing mechanism issues a digital certificate according to a certificate request of a digital certificate requester, and the digital certificate comprises key information of the certificate; and the certificate issuing mechanism sends the digital certificate and the public query information of the digital certificate to the digital certificate requester. The digital certificate public inquiry system has the advantages that the certificate issuing mechanism sends the HASH value of the digital certificate, the public inquiry information of the digital certificate and the public key of the digital certificate requester to the public inquiry system, and due to the fact that the HASH of the data is encrypted in a one-way irreversible mode, the accuracy of information can be marked, and the information cannot be exposed. Digital certificate verification is based on a non-interactive zero-knowledge proof (NIZK) method, and it is guaranteed that sensitive information is not prone to being leaked.
Owner:北京思源理想控股集团有限公司
Data security management method applied to operation and maintenance auditing system
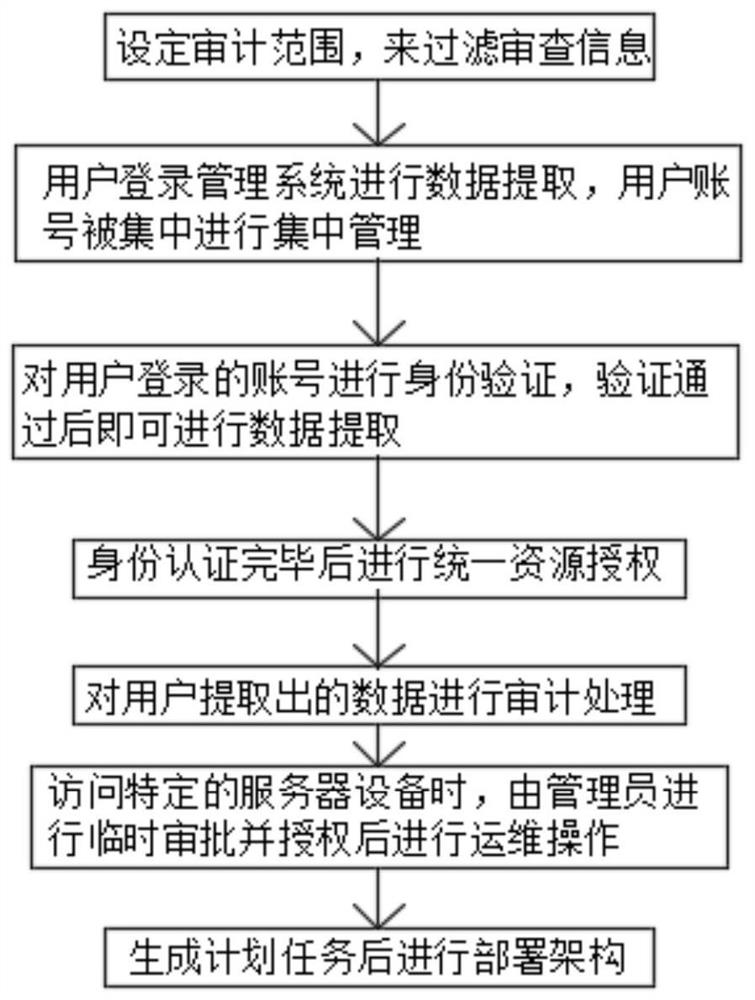
InactiveCN111914234AImprove securityEasy maintenanceDigital data protectionDigital data authenticationData ingestionUser authentication
The invention discloses a data security management method applied to an operation and maintenance auditing system, which comprises the following steps of: 1, setting an auditing range to filter auditing information; 2, a user logs in the management system for data extraction, and user accounts are centrally managed; 3, identity verification is made on an account logged in by the user, and data isextracted after verification passes; 4, after identity authentication is completed, unified resource authorization is carried out, resources needed by the user are extracted from unified resources, and centralized access control is carried out; 5, the data extracted by the user is audited 6, when the specific server equipment is accessed, an administrator carries out temporary approval and authorization and then carries out operation and maintenance operation; and 7, a planned task is generated and then an architecture is deployed. According to the invention, the security of a user authentication link is improved, operation and maintenance personnel can maintain resources conveniently, repeated work is reduced, and the operation and maintenance efficiency is improved.
Owner:安徽长泰科技有限公司
Method of locking/unlocking computer screen based on NFC terminal
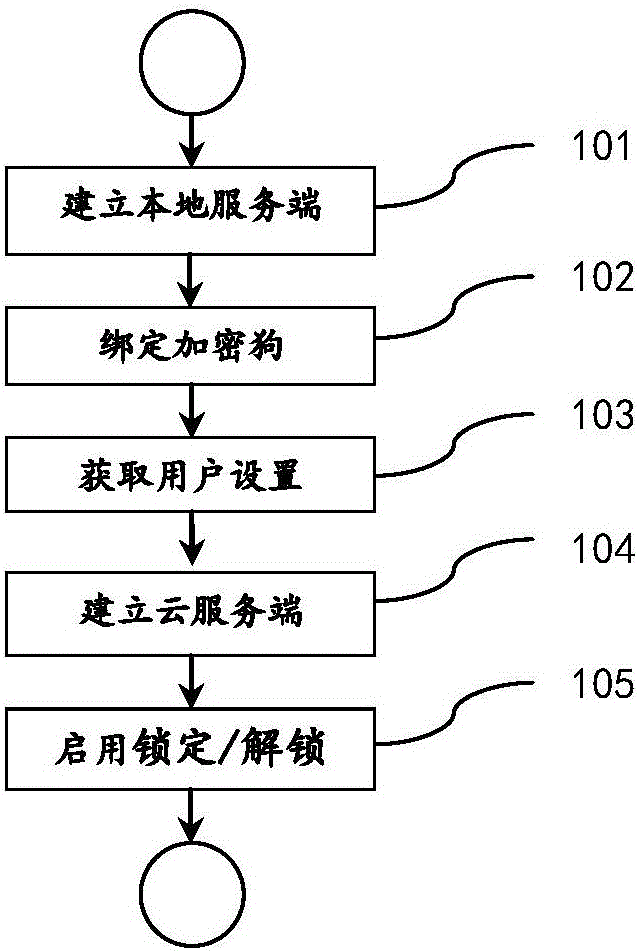
InactiveCN105959277AEasy to operateConvenient identity verificationDigital data authenticationTransmissionUser needsComputer terminal
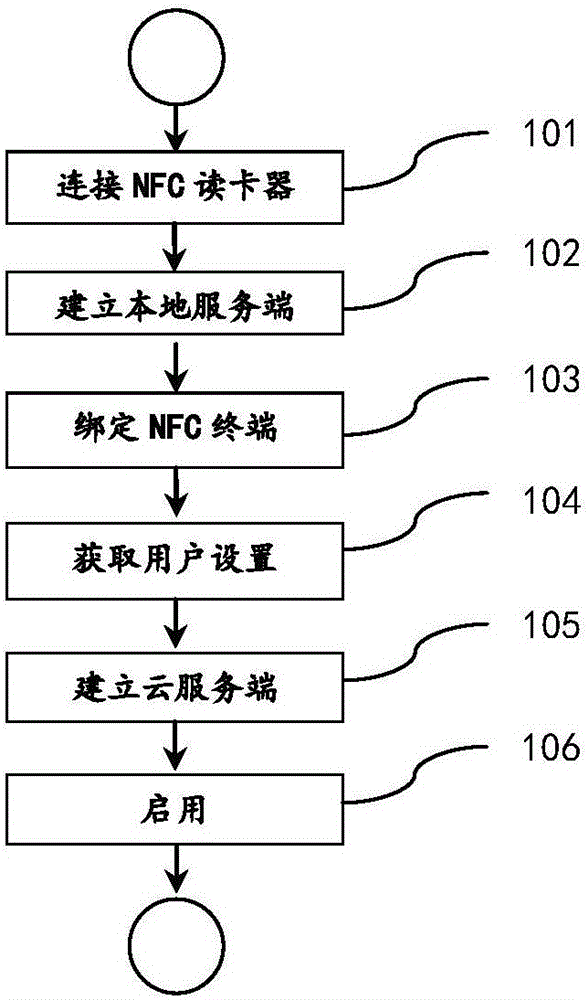
The invention discloses a method of locking / unlocking computer screen based on NFC terminal, comprising the following steps: 101) connecting an NFC reader; 102) setting up a local server; 103) binding an NFC terminal; 104) accessing information configured by a user; 105) establishing a cloud server; and 106) initiating the locking / unlocking of screen. According to the invention, the method has following advantages: 1) NFC terminal used as a key to locking / unlocking a PC screen; when it is used to unlock, all a user needs to do is put the NFC terminal close to a computer NFC recognizer; with it, the screen becomes unlocked. 2) extra layers of security protection to make up loopholes facing computer safety and convenient operations; 3) availability of emergency mode for more secure, more convenient identity identification and computer unlocking; 4) using an active protection mode for the system, and based on used scenes, the protection is set to be automatic, hidden in a bottom layer seldom felt by the user, so that protection becomes silent.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
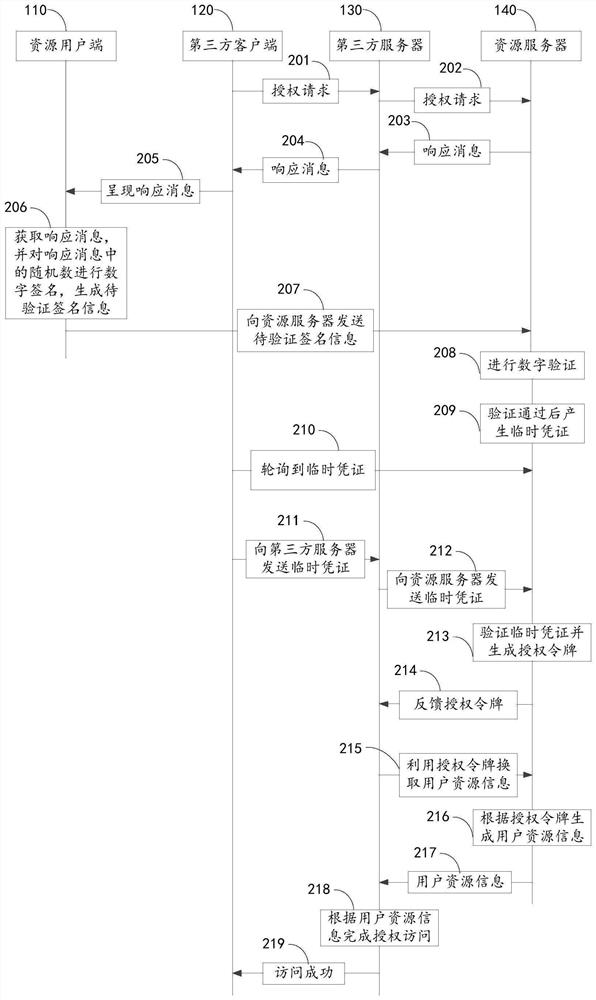
Authorization authentication method, resource server, resource client, device and medium
PendingCN112861089AConvenient identity verificationPrevent leakageDigital data authenticationThird partyInternet privacy
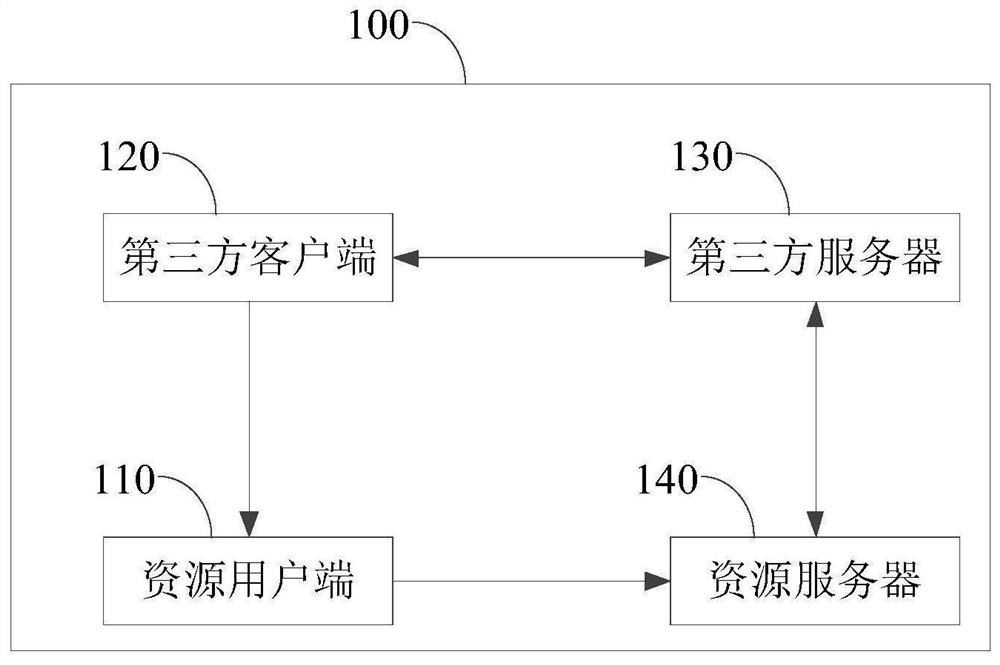
The embodiment of the invention provides an authorization authentication method, a resource server, a resource user side, equipment and a medium. The method comprises the steps: obtaining to-be-verified signature information sent by the resource user side and identification information of an authorization request, wherein the authorization request is used for a third-party server to apply for accessing protected user resource information in the resource server; carrying out the signature authentication on the signature information to be verified, an authentication result is generated, wherein the authentication result is used for representing whether the identity of the resource user side is legal or not; and when the identity of the resource user side is legal, executing an authentication process that the resource server authorizes the user resource information to the third-party server. According to the method, identity authentication is carried out on the resource user side in the authorization authentication process based on the digital certificate, the safety of user identity authentication can be enhanced, and the safety of user information opening is further ensured.
Owner:北京数字医信科技有限公司
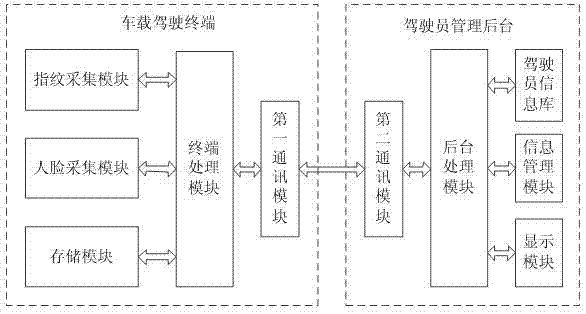
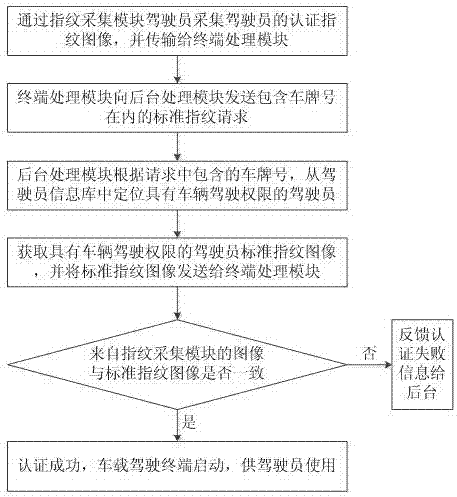
Fingerprint identification-based driver identity authentication system and method
InactiveCN107301374AImplement identity authenticationConvenient identity verificationData processing applicationsTransmissionInformation repositoryComputer terminal
The invention discloses a fingerprint identification-based driver identity authentication system and method. The system comprises a vehicle-mounted driving terminal and a driver management background, wherein the vehicle-mounted driving terminal comprises a fingerprint collection module and a terminal processing module; the driver management background comprises a background processing module and a driver information library; the fingerprint collection module is connected with the terminal processing module; the terminal processing module is connected with the background processing module through network communication; and the background processing module is connected with the driver information library. According to the fingerprint identification-based driver identity authentication system and method provided by the invention, an authentication fingerprint image of a driver is collected and the collected image is compared with a standard fingerprint image provided by the driver management background to realize driver identity authentication, so that comprehensive management of a transportation company is facilitated, identity authentication of drivers before vehicle driving is facilitated, and the working efficiency of the drivers is improved.
Owner:CHENGDU YIMENG HENGXIN TECH
Identity authentication system and reimbursement equipment
ActiveCN107948132ARealize electronic processingAchieving processing powerFinanceTransmissionInternet privacyAuthentication system
The invention discloses an identity authentication system and reimbursement equipment. The identity authentication system comprises a processor, and a biological feature acquisition assembly and a behavior feature acquisition assembly connected with the processor, wherein the biological feature acquisition assembly is used for acquiring biological feature information of a user; the behavior feature acquisition assembly is used for acquiring behavior feature information of the user; and the processor is used for acquiring feature information of the user by utilizing at least one of the biological feature acquisition assembly and the behavior feature acquisition assembly, and authenticating identity of the user by using the feature information of the user. The identity authentication systemcan realize the effect of implementing identity authentication by using different features of the user.
Owner:YGSOFT INC
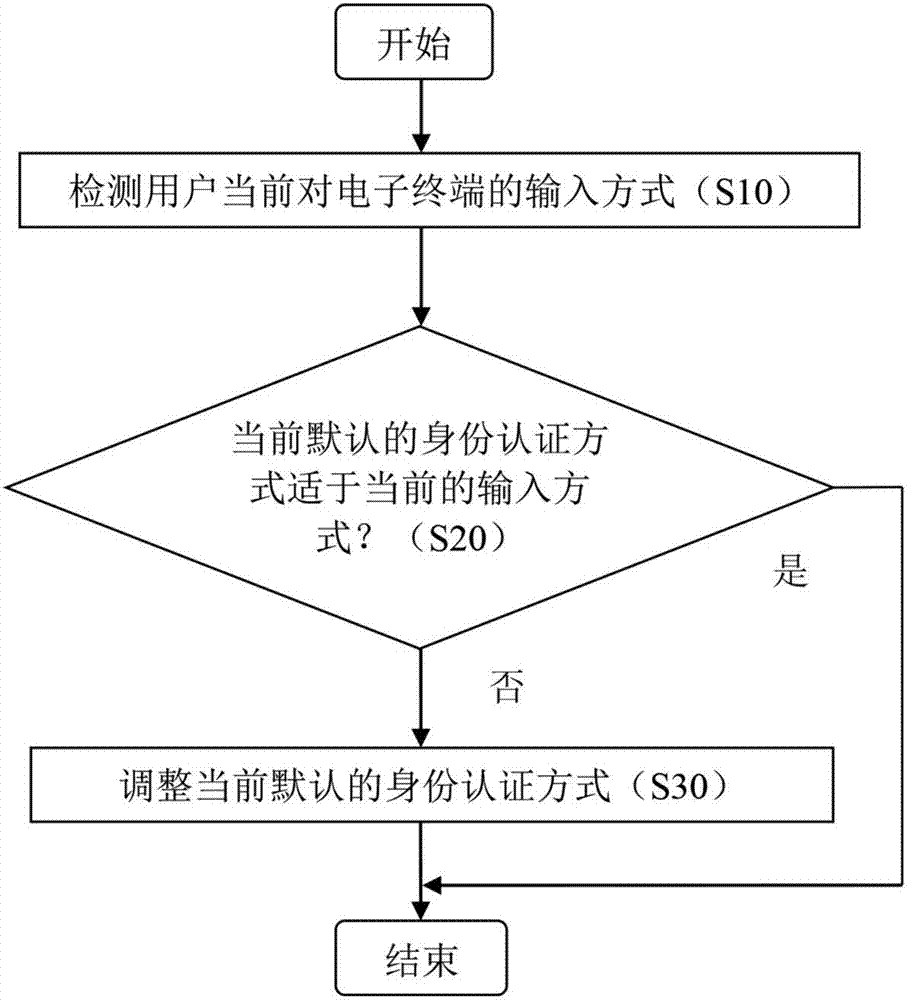
Method and apparatus for adjusting identity authentication mode
InactiveCN107194218AConvenient identity verificationDigital data authenticationInput/output processes for data processingAuthentication
A method and an apparatus for adjusting an identity authentication mode are provided. The method comprises: (A) detecting a current input mode to the electronic terminal performed by a user; (B) determining whether a first identity authentication mode as the current default identity authentication mode is applicable to the current input mode; and (C) when it is determined that the first identity authentication mode as the current default identity authentication mode is not applicable to the current input mode, adjusting the current default identity authentication mode. According to the method and the apparatus, identity authentication for the user can be facilitated.
Owner:SAMSUNG GUANGZHOU MOBILE R&D CENT +1
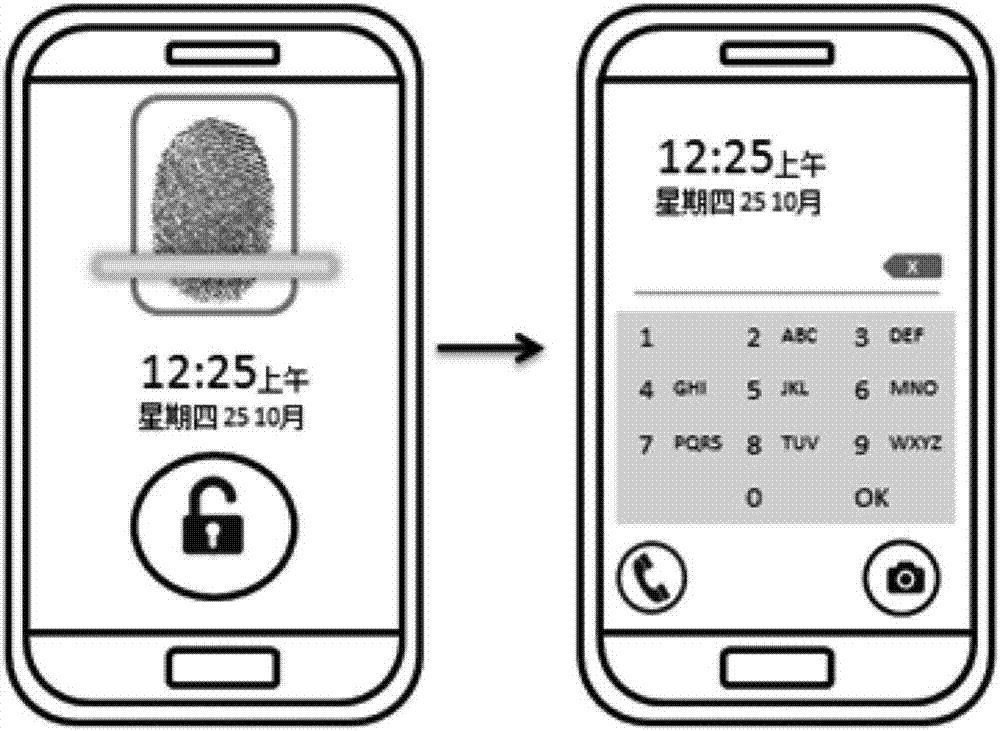
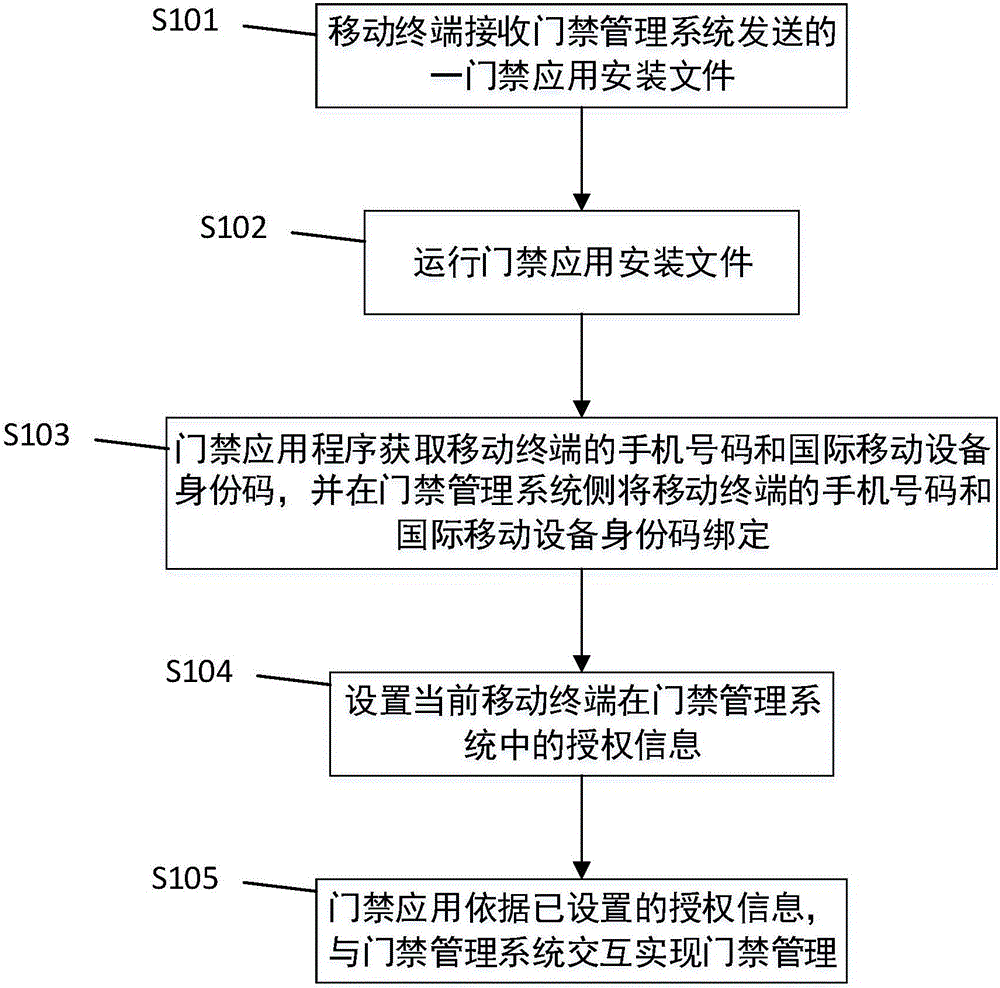
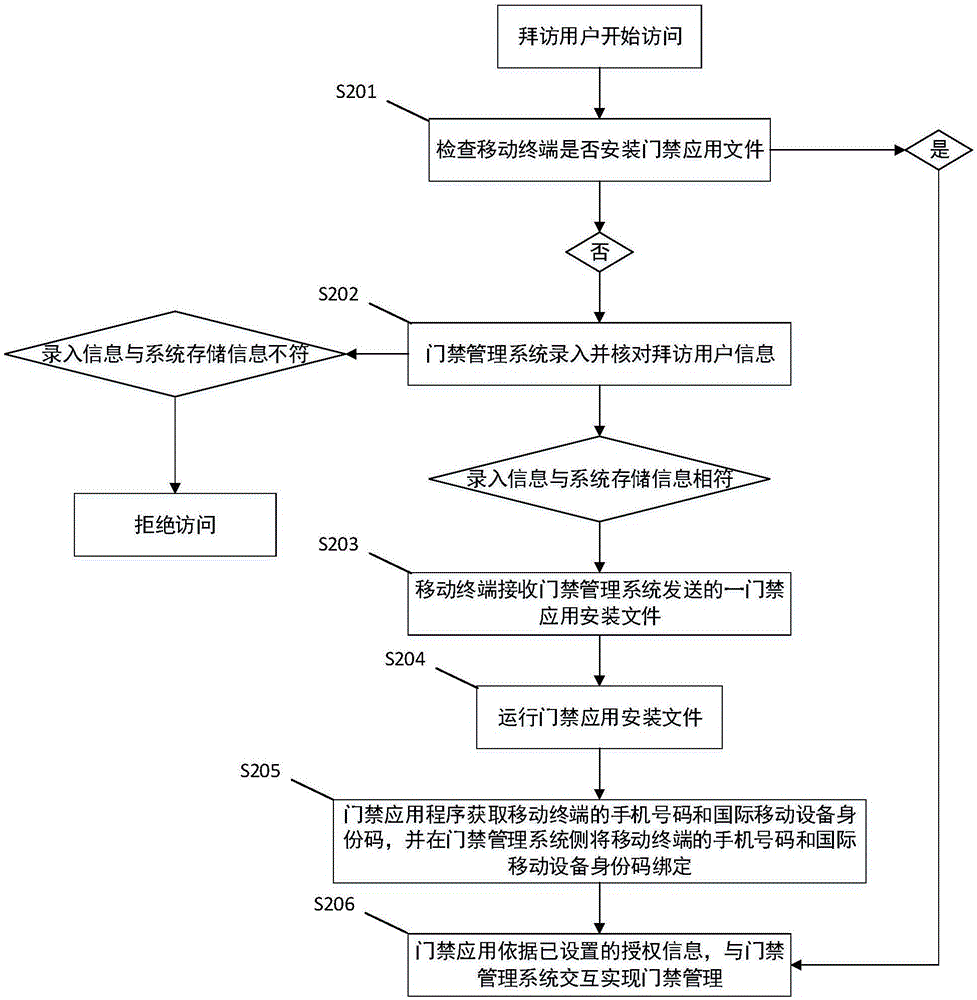
Mobile terminal-based access control management information processing method and device
InactiveCN106652136AQuick managementManagement management fastIndividual entry/exit registersInformation processingMobile device
The invention discloses a mobile terminal-based access control management information processing method and device aiming at solving the technical problem of a complicated access control management program in the prior art. The mobile terminal-based access control information processing method comprises the following steps: a mobile terminal receives a first access control application installation file transmitted by an access control management system, wherein the access control application installation file is generated according to visitor information of the mobile terminal; the access control application installation file obtains a mobile phone number of the mobile terminal and an international mobile equipment identity code of the mobile terminal after running, and carries out binding of the mobile phone number of the mobile terminal and the international mobile equipment identity code of the mobile terminal on the side of the access control management system; an authorization message of the current mobile terminal in the access control management system is set; and the access control application interacts with the access control management system according to the set authorization message for achieving access control management.
Owner:QIKU INTERNET TECH SHENZHEN CO LTD
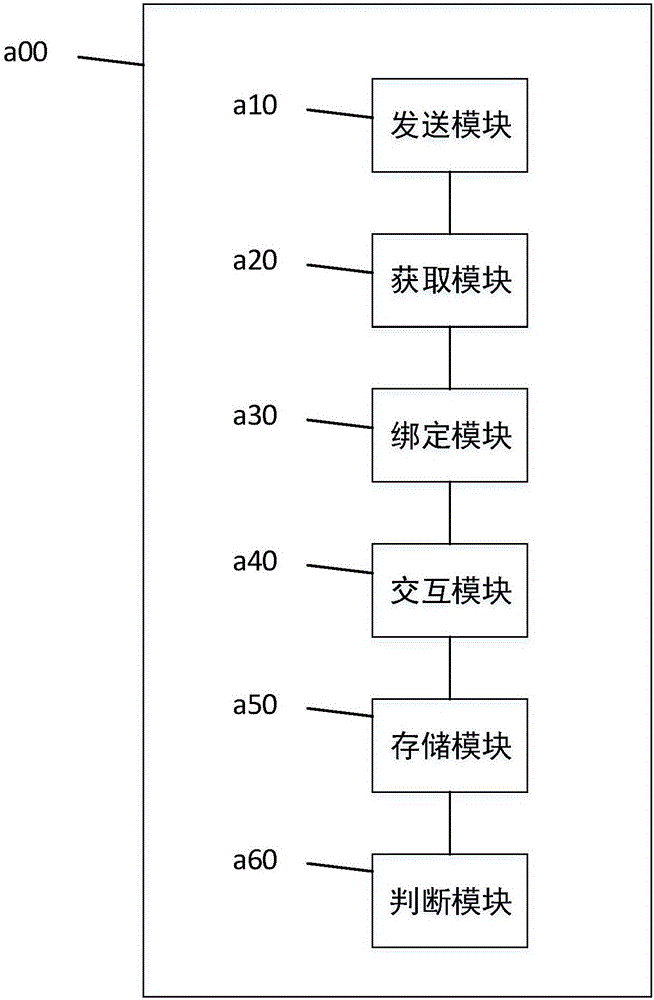
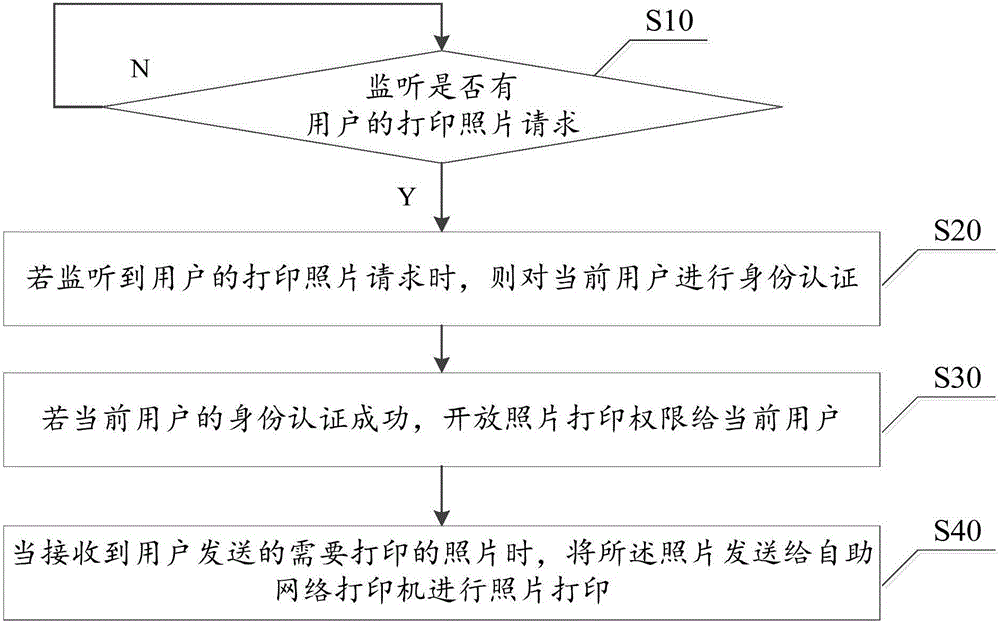
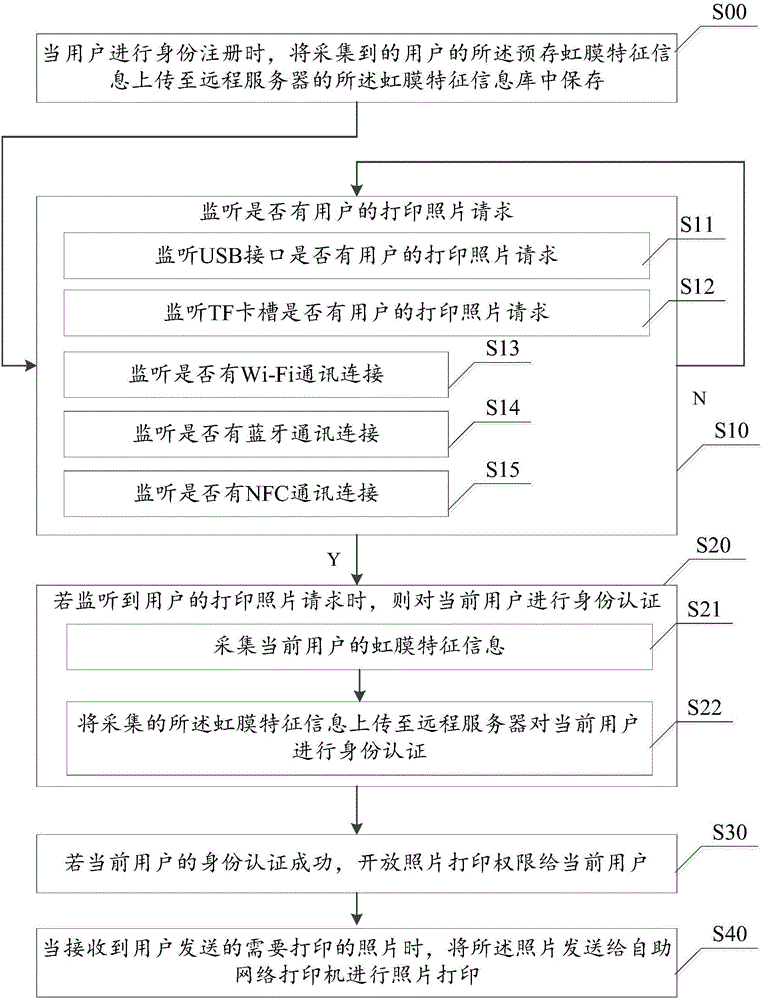
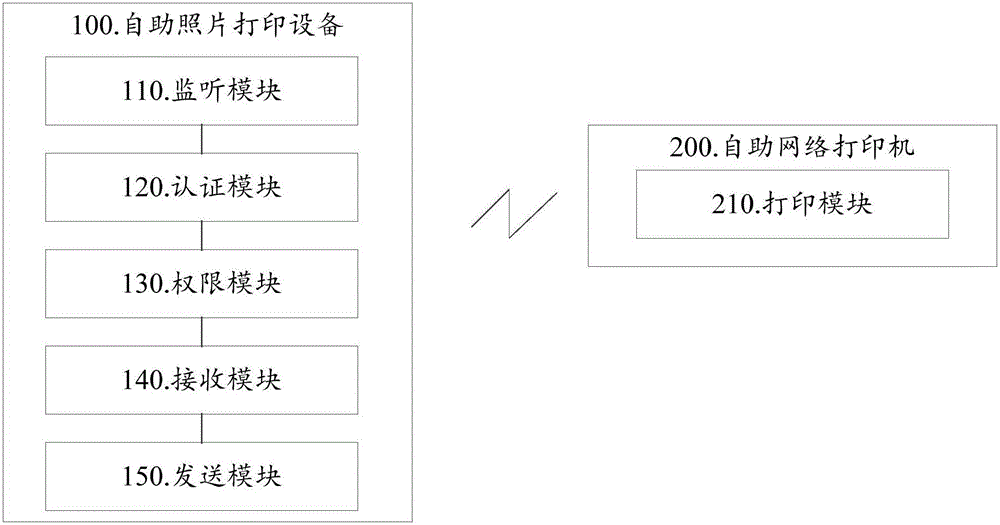
Self-service photograph printing method and system
InactiveCN106408784AConvenient printing feeGuarantee the safety of useDigital data authenticationApparatus for meter-controlled dispensingSelf-serviceCurrent user
The invention discloses a self-service photograph printing method and system. The method includes: a step S10, monitoring if a photograph printing request of a user exists or not, executing the step S10 if not; a step S20, performing identity authentication on a current user if the photograph printing request is monitored; a step S30, opening a photograph printing permission for the current user if the identity authentication of the current user is successful; a step S40, sending a photograph to a self-service network printer to print the photograph when the photograph needing to be printed sent by the user is received. Identity authentication is performed on a user through iris feature information, the printing permission is opened for the user only identity authentication is successful, it is ensured that not everyone can print photographs by using the self-service network printer, the use security of the user can be ensured, and merchant can conveniently find a corresponding user to perform settlement.
Owner:PHICOMM (SHANGHAI) CO LTD
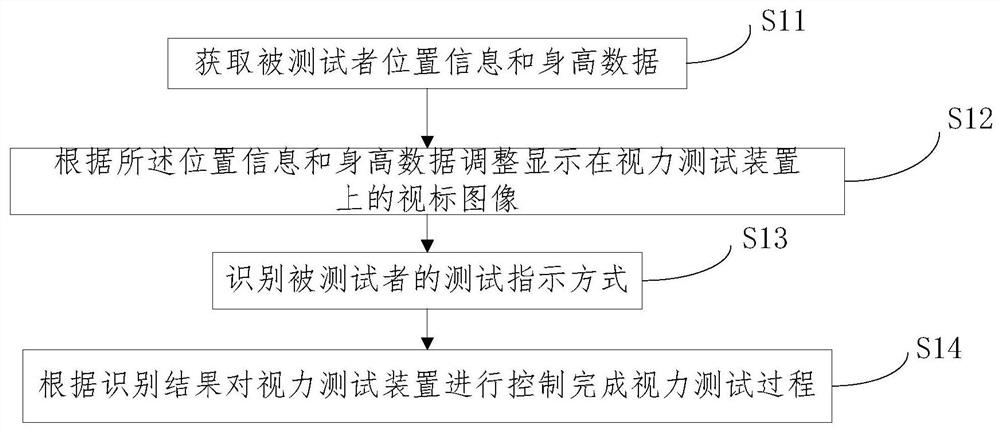
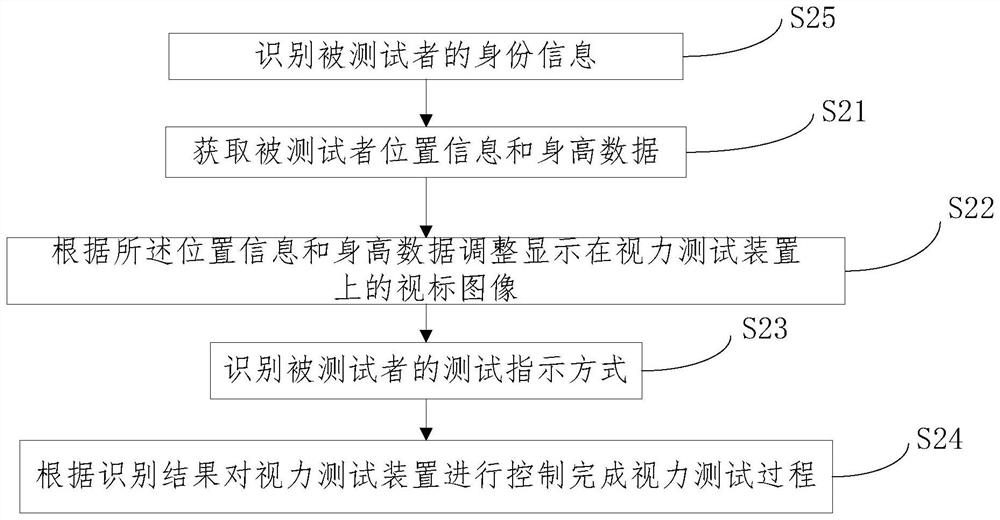
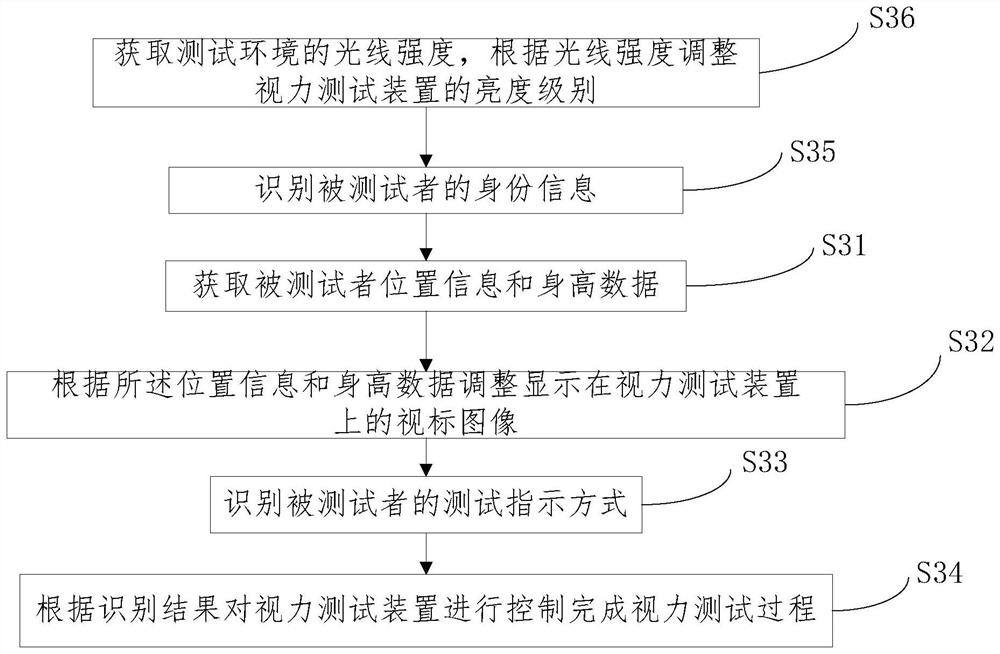
Intelligent vision testing method, device and system
PendingCN113143193AHigh degree of automationEasy to manageDigital data authenticationEye diagnosticsVision testingVisual acuity
The invention relates to the field of intelligent vision testing, in particular to an intelligent vision testing method, device and system, and the method comprises the steps: obtaining the position information and height data of a testee; adjusting a sighting mark image displayed on the vision testing device according to the position information and the height data; identifying a test indication mode of the testee; and controlling the vision testing device according to the identification result to complete the vision testing process. By means of the intelligent vision testing method, device and system, the whole vision testing process can be completed more intelligently.
Owner:张婧怡
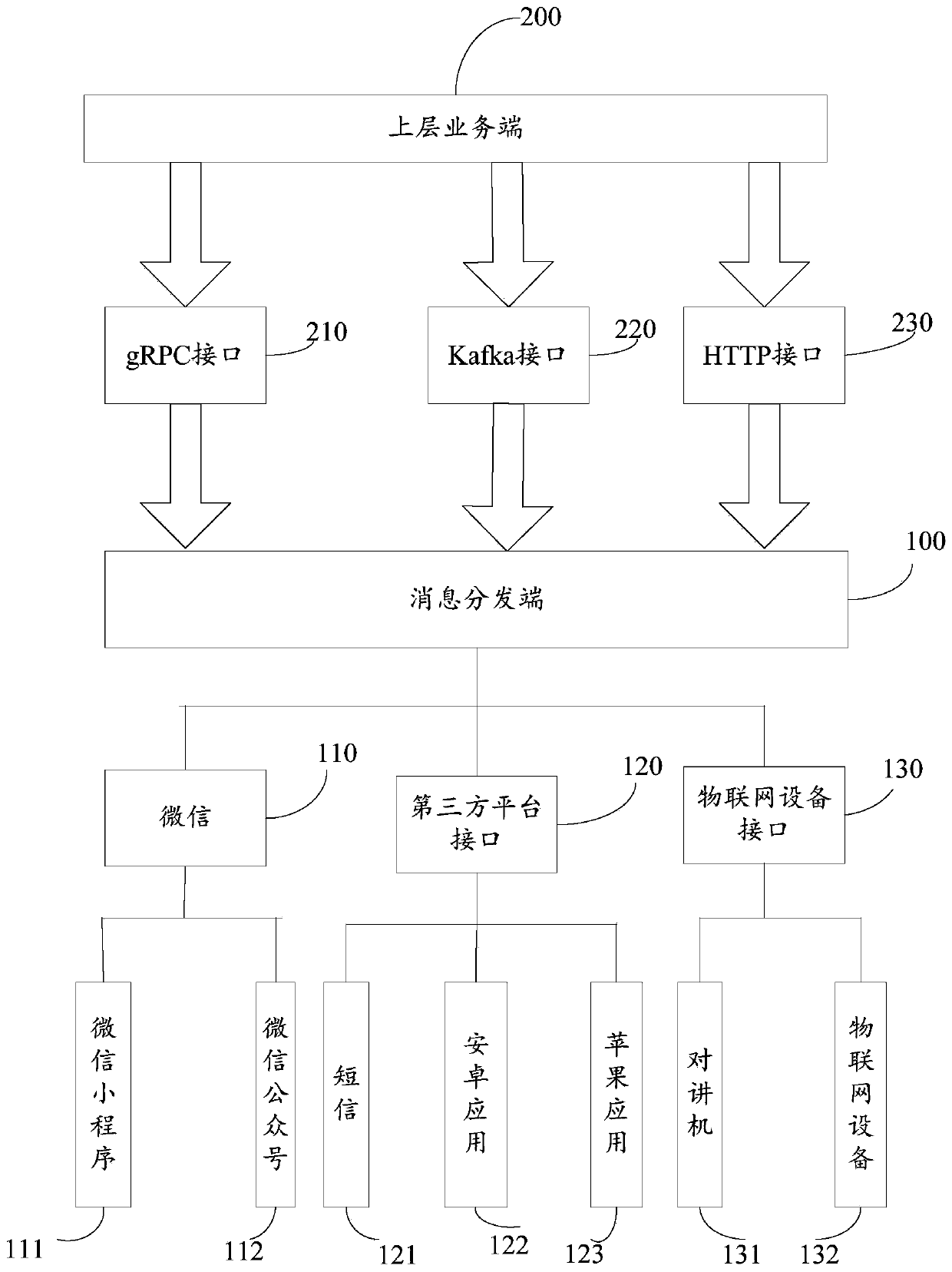
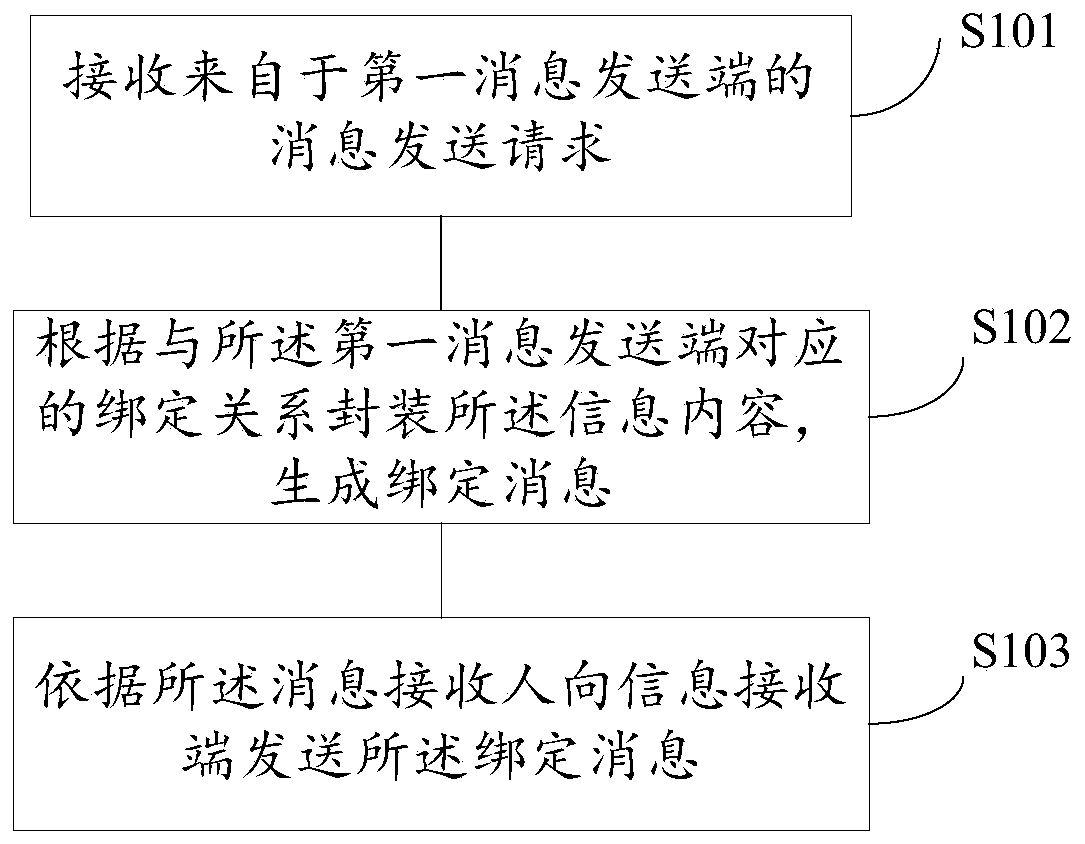
Message distribution method and device
PendingCN111400066AReduce workloadImplement message sendingInterprogram communicationDistribution methodEngineering
The embodiment of the invention provides a message distribution method and device, and the method comprises the steps: receiving a message sending request from a first message sending end, and enabling the message sending request to comprise message contents and a message receiver; packaging the message content according to a binding relationship corresponding to the first message sending end, andgenerating a binding message; and sending the binding message to a message receiving end according to the message receiver. According to the message distribution method provided by the embodiment ofthe invention, a plurality of applications with message sending requests can share one message pushing system, so the workload of developing the message pushing system is reduced.
Owner:北京云迹科技股份有限公司
Intelligent terminal with encryption transaction function and transaction method
ActiveCN103455917AConvenient identity verificationFunction increaseUser identity/authority verificationPayment architecturePaymentCommunication interface
The invention relates to an intelligent terminal which comprises a main circuit board, a main processor, a main storage device and a data bus. The main processer, the main storage device and the data bus are arranged on the main circuit board, and the main processor and the main storage device are connected with the data bus. The intelligent terminal further comprises an encryption module arranged on the main circuit board, an encryption algorithm is built in the encryption module, the encryption module is provided with a communication interface, and the encryption module is connected to the data bus only through the communication interface. The encryption algorithm is built in the intelligent terminal and can be used for encryption processing in transaction, external U shield devices are not needed, and therefore the identity authentication and safety payment function can be conveniently achieved in digital TV set-top boxes or digital televisions with U shields difficult to use, and convenience and fastness are achieved. In addition, the invention further provides a transaction method.
Owner:TENCENT TECH (SHENZHEN) CO LTD
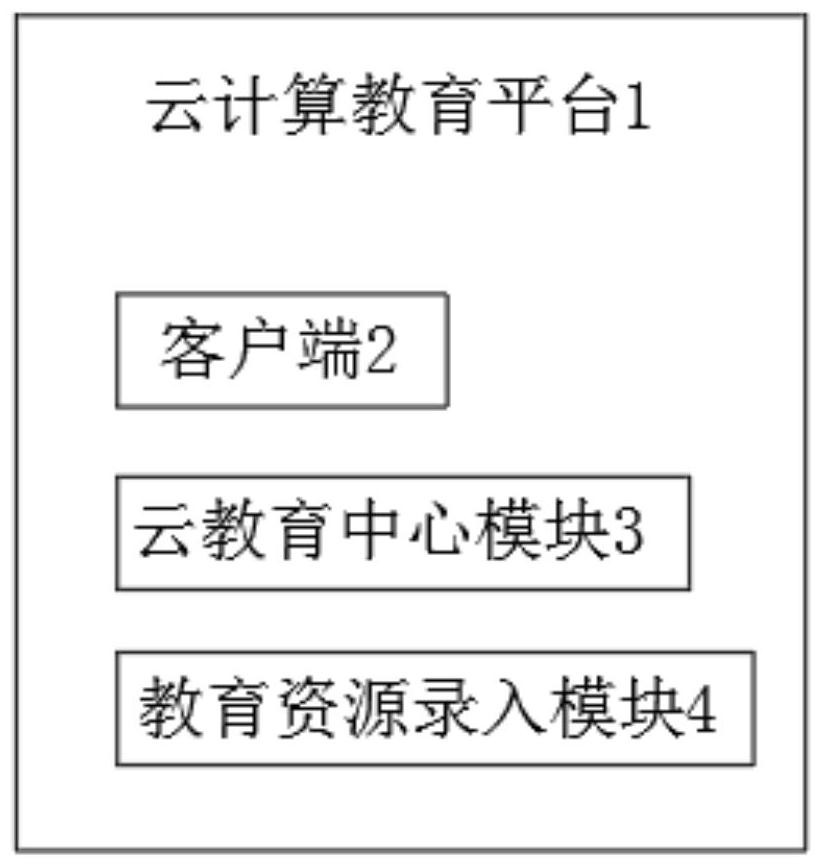
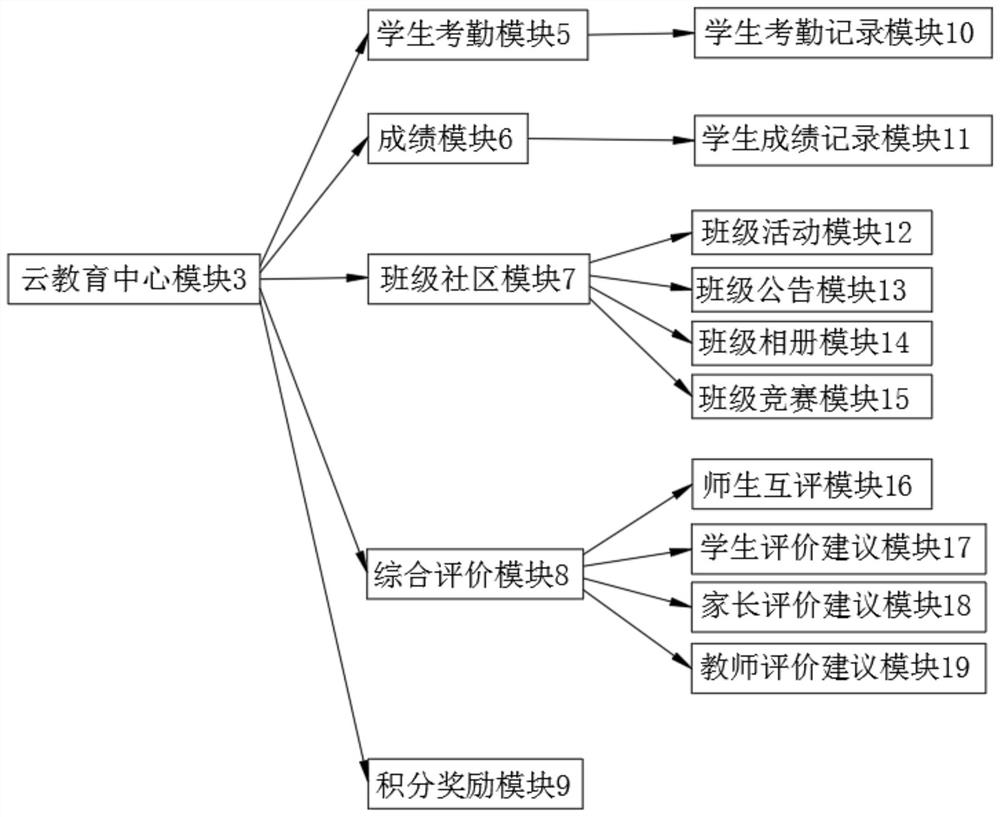
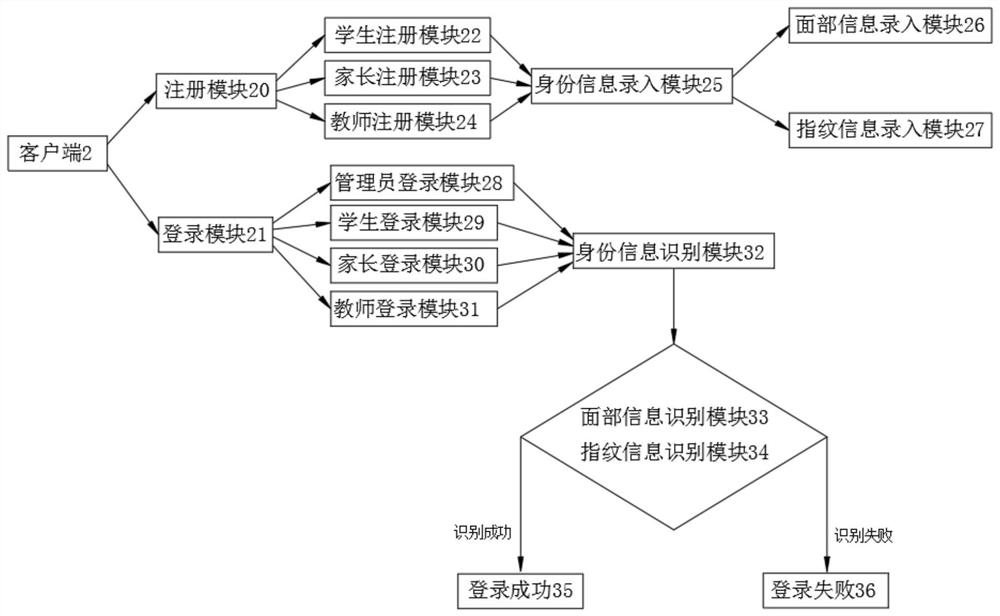
Cloud computing education platform based on big data
PendingCN113077365AEasy to summarize and integrateEasy to shareDiscounts/incentivesDigital data authenticationKnowledge managementCloud computing
The invention discloses a cloud computing education platform based on big data. The platform comprises a cloud computing education platform, a client and a cloud education center module, wherein the cloud computing education platform is provided with the client, the cloud education center module and an education resource input module, the digital library resource module is connected with the campus education resource input module to facilitate input of various education resources, and the classroom education teaching resource module is connected with the teacher education resource input module to facilitate induction and integration of teaching videos and notes of teachers in a classroom; extracurricular education resources are connected with the student education resource input module and the parent education resource input module, so education resources obtained by the students and the parents outside the class can be conveniently shared into the education platform, various education is transmitted to the education resource sharing module after being audited by the education resource auditing module, and teachers and students can conveniently share the resources inside and outside the class; and students can be more comprehensively educated.
Owner:甄彦辉
Identity authentication method, device and equipment and storage medium
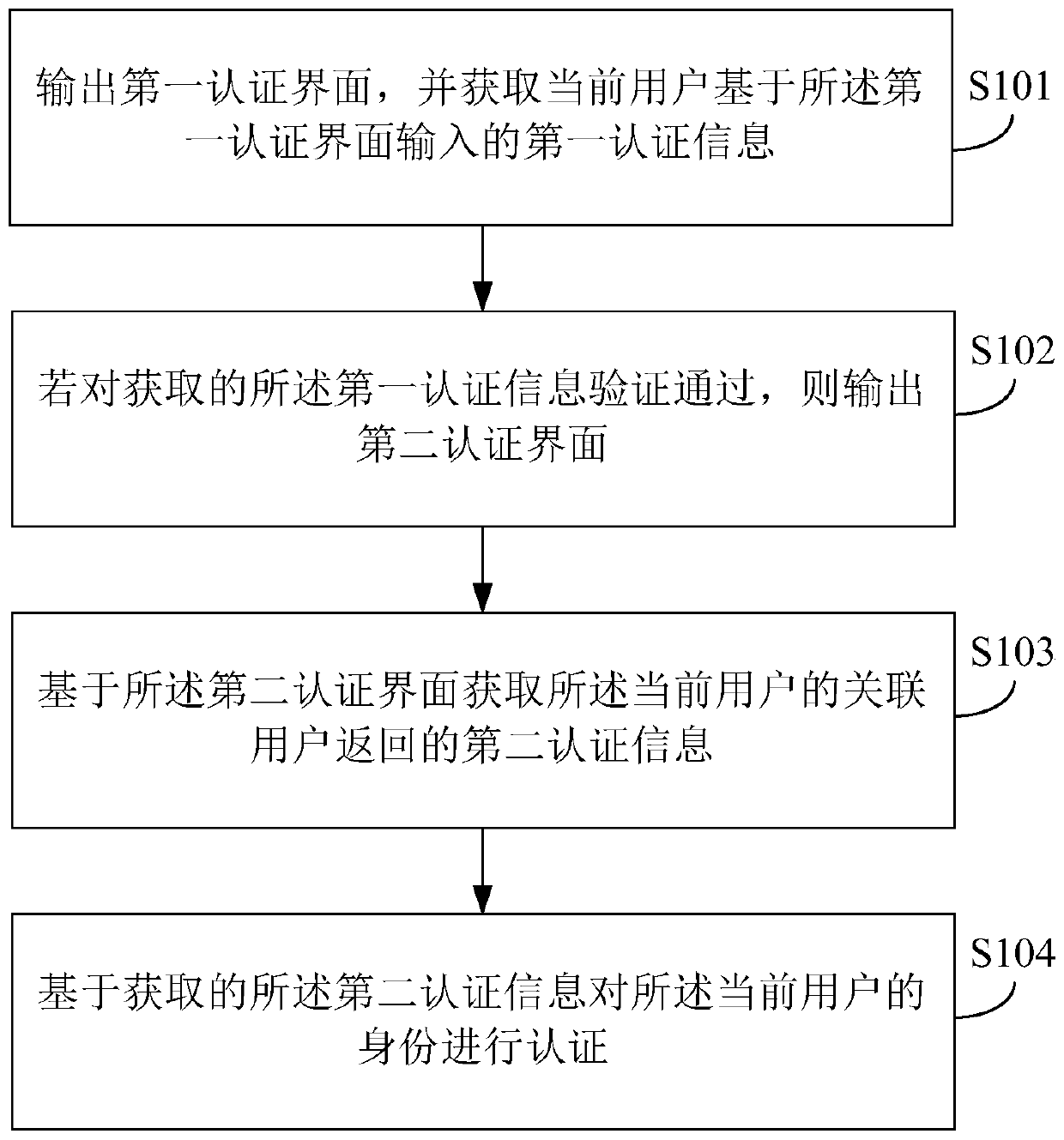
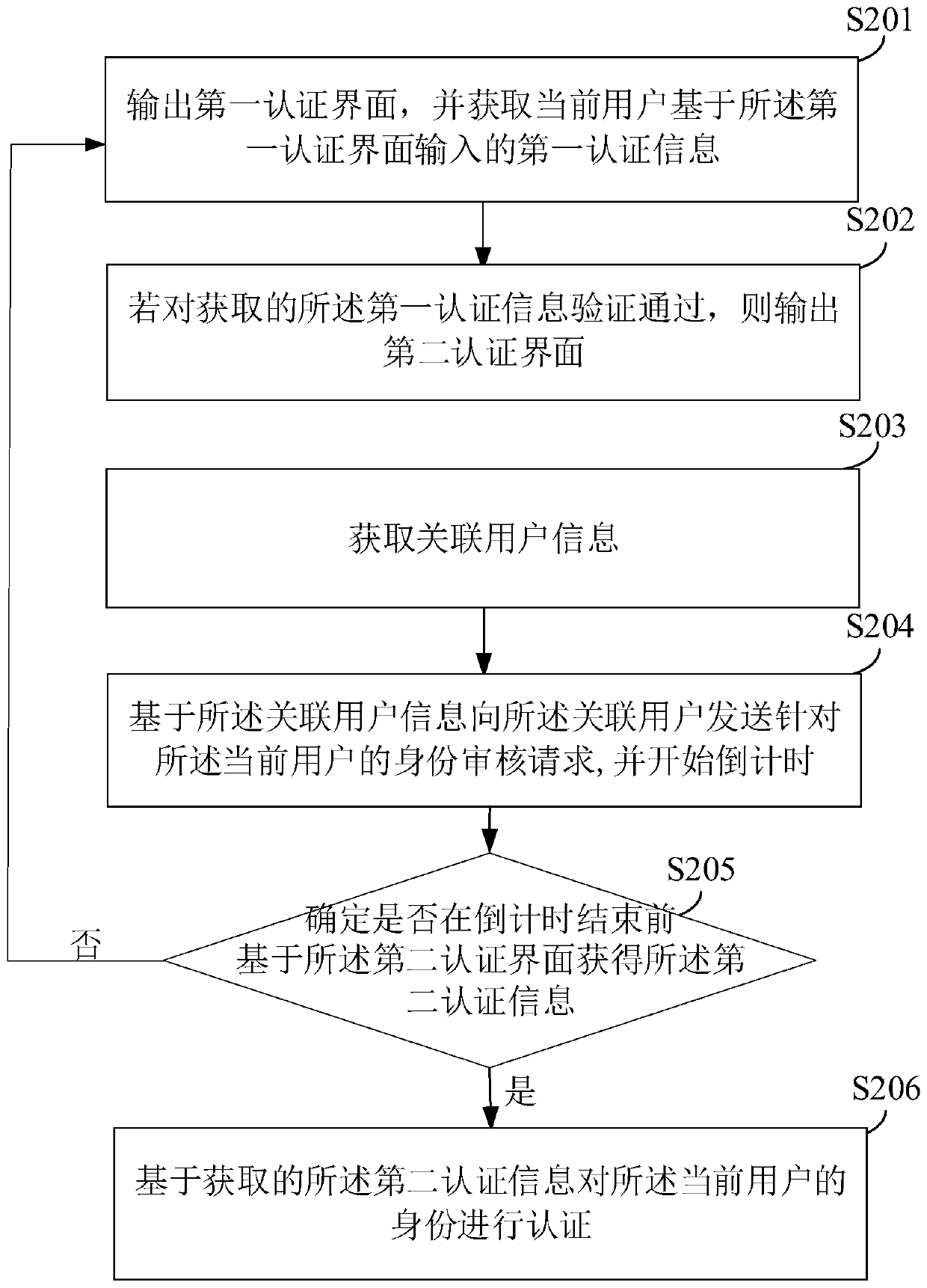
ActiveCN109829321AConvenient identity verificationFast authenticationDigital data protectionTerminal equipmentComputer terminal
The invention provides an identity authentication method and device, equipment and a storage medium, and the method comprises the steps: outputting a first authentication interface, and obtaining first authentication information input by a current user based on the first authentication interface; If the obtained first authentication information passes the verification, outputting a second authentication interface; Obtaining second authentication information returned by the associated user of the current user based on the second authentication interface; And authenticating the identity of the current user based on the obtained second authentication information. The identity of the current user can be authenticated based on the second authentication information returned by the associated user of the current user; The dependence of the identity authentication scheme on the associated terminal equipment can be reduced, and the identity authentication process of the user can still be completed when the user forgets to carry the terminal equipment or the terminal equipment fails and cannot receive the authentication information.
Owner:北京三快云计算有限公司 +1
Method for locking/ unlocking computer screen on the basis of softdog
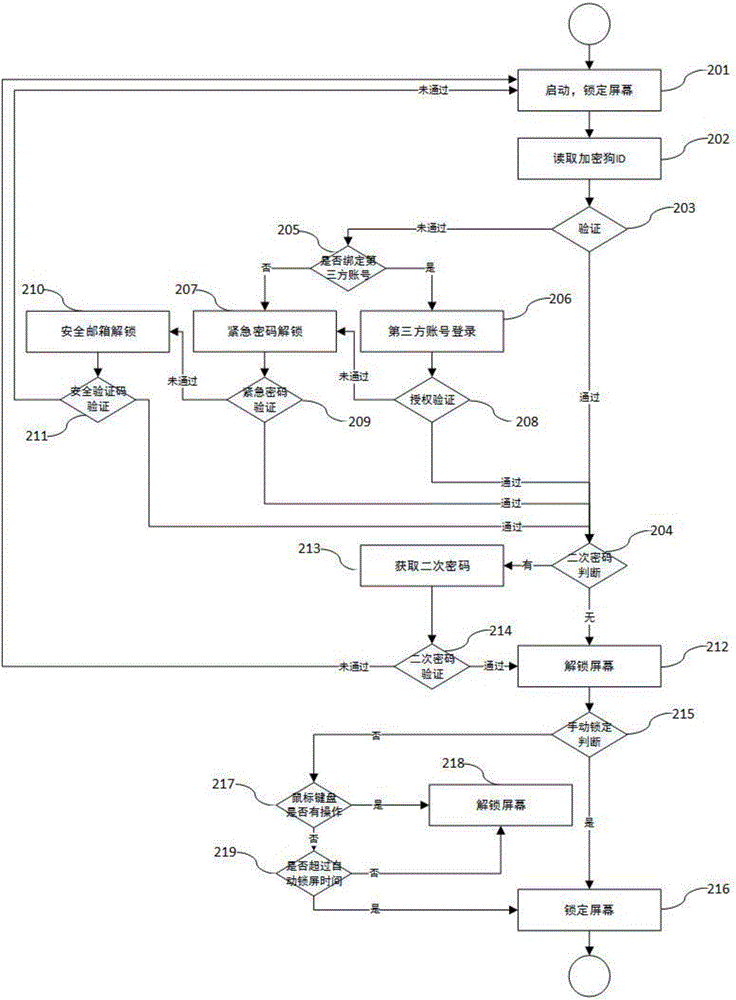
InactiveCN105975841AFilling gaps in security defensesEasy to operateDigital data authenticationPasswordProtected mode
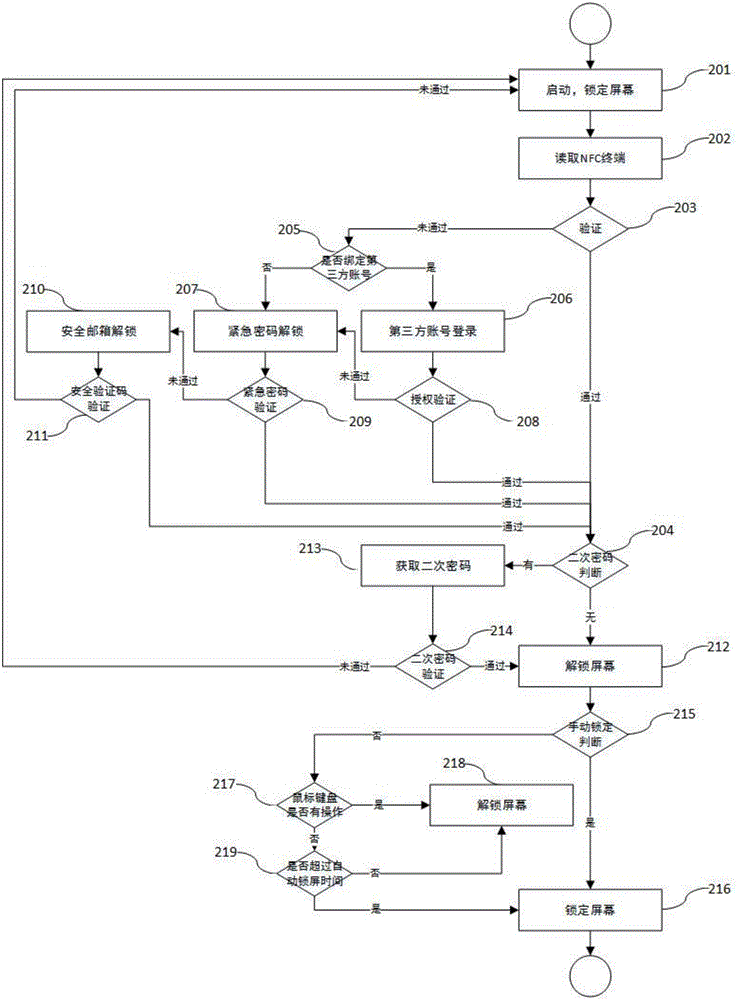
The invention discloses a method for locking / unlocking a computer screen based on a dongle, comprising the following steps: 101: establishing a local server; 102: binding the dongle; 103: acquiring user settings; 104: establishing a cloud server; 105: Enable screen lock / unlock. The beneficial effects of the present invention are as follows: the dongle is used as a key to lock / unlock the screen of the personal computer; multi-layer security protection layers are added, and the operation is convenient; an emergency mode is provided for safer and more convenient identity authentication and unlocking of the computer; emergency password / safety is set Mailbox, which is convenient for unlocking the computer safely in special emergency situations such as lost or stolen dongles; adopts the active protection mode of the system, and sets the protection to automatic according to the usage scenario, hiding it at the bottom layer that the user cannot perceive. To protect the silent.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
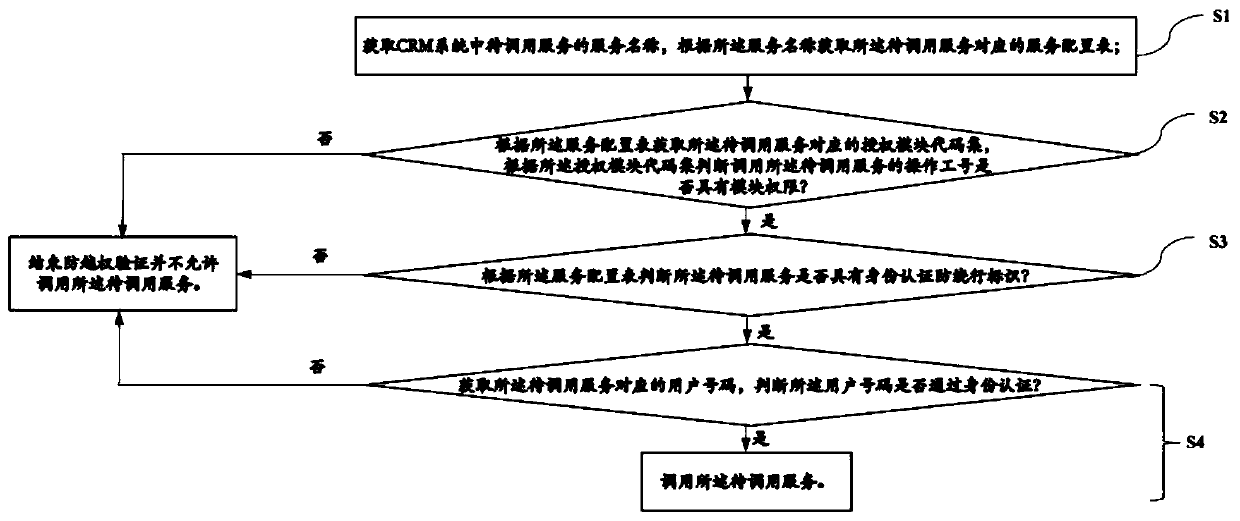
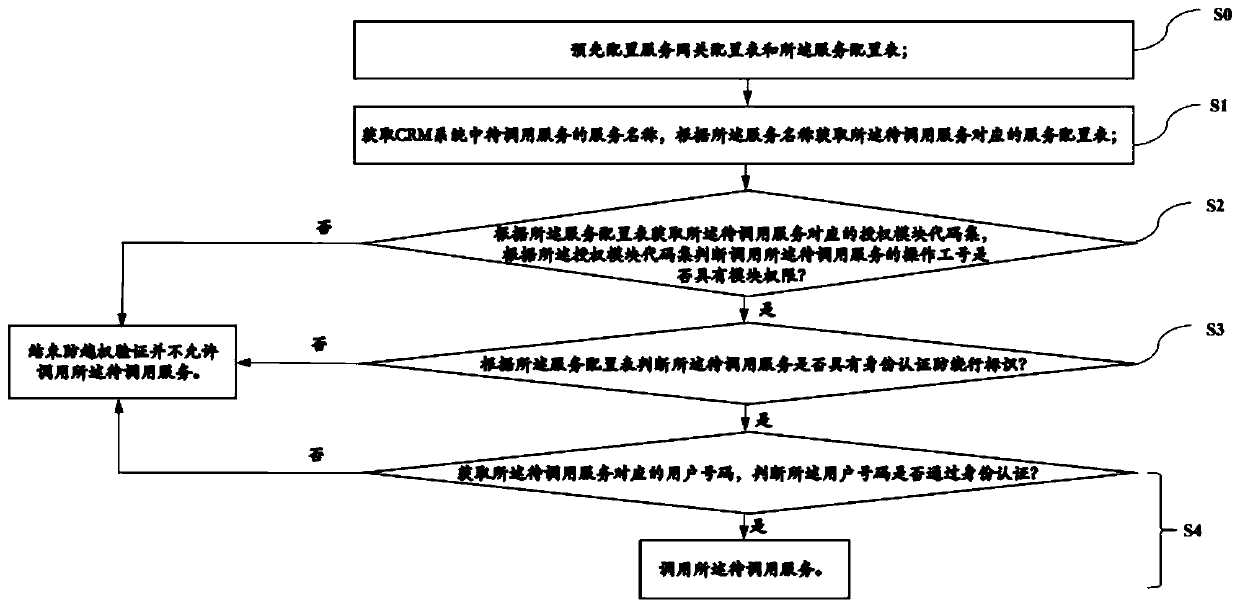
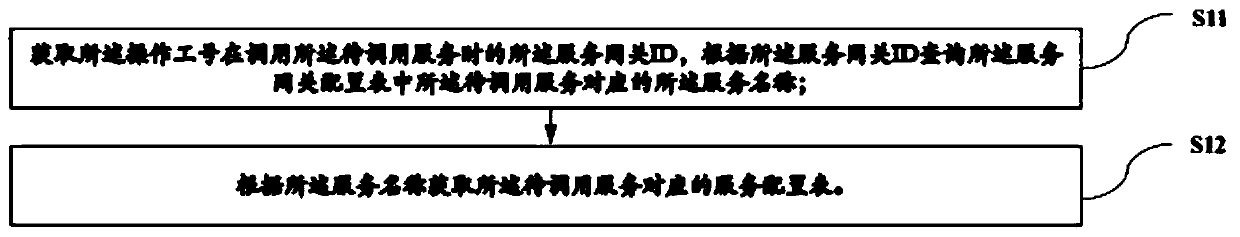
CRM system anti-unauthorized implementation method and device and storage medium
ActiveCN111526143AAvoid illegal callsAvoid doing business illegallyData switching networksAuthorizationEngineering
The invention relates to a CRM system anti-unauthorized implementation method and device and a storage medium, and the method comprises the steps: obtaining a service name of a to-be-called service ina CRM system, and obtaining a service configuration table corresponding to the to-be-called service according to the service name; obtaining an authorization module code set corresponding to the to-be-called service according to the service configuration table, and judging whether the operation job number has the module permission or not according to the authorization module code set; if so, judging whether the to-be-called service has an identity authentication anti-detour identifier or not according to the service configuration table: if so, obtaining a user number corresponding to the to-be-called service, and judging whether the user number passes the identity authentication or not: if so, calling the to-be-called service, and if not, not allowing to call the to-be-called service. According to the invention, double security reinforcement is carried out on the CRM system, services without functional module permission are prevented from being illegally called, illegal business handling by bypassing customer identity authentication is avoided, unauthorized and illegal access is prevented, and the security of the CRM system is greatly improved.
Owner:北京思特奇信息技术股份有限公司
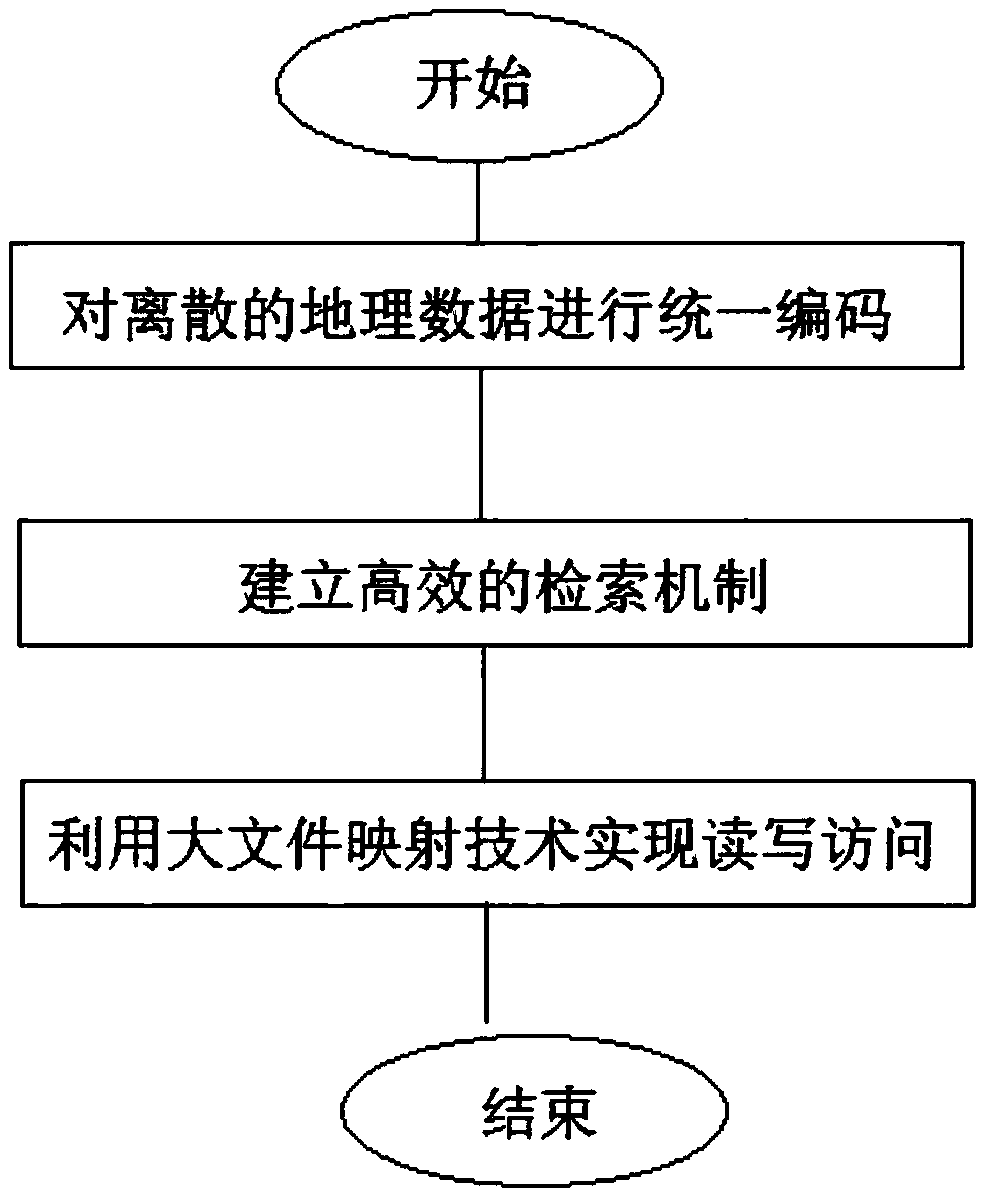
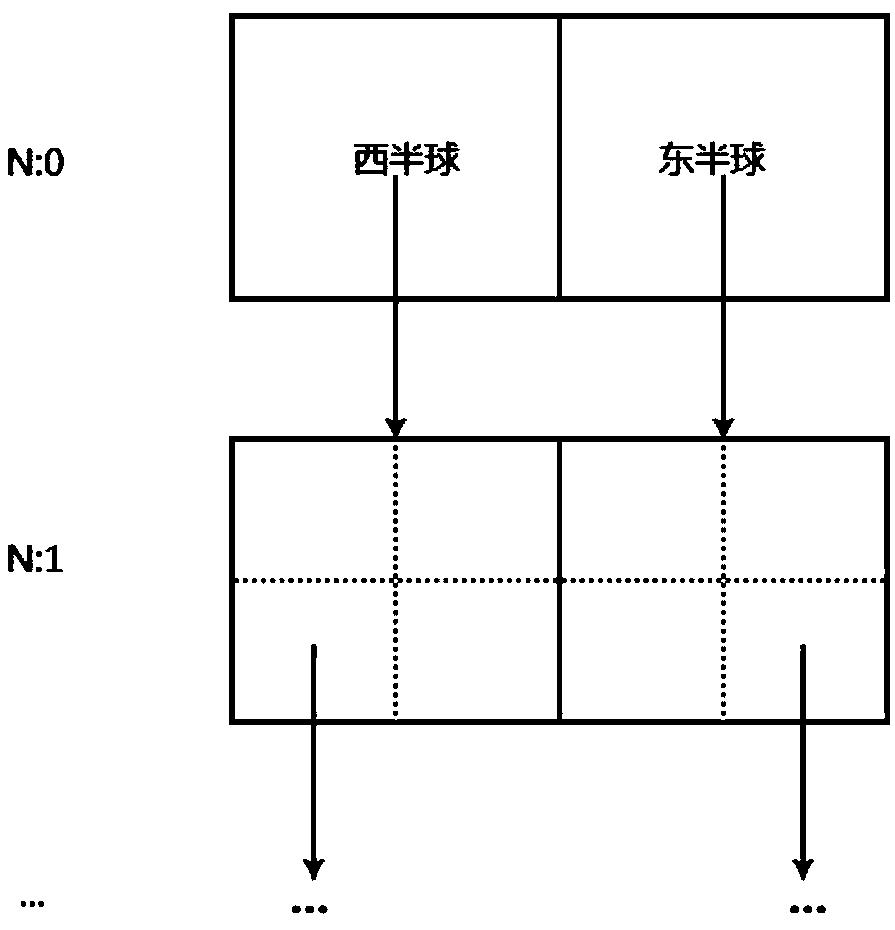
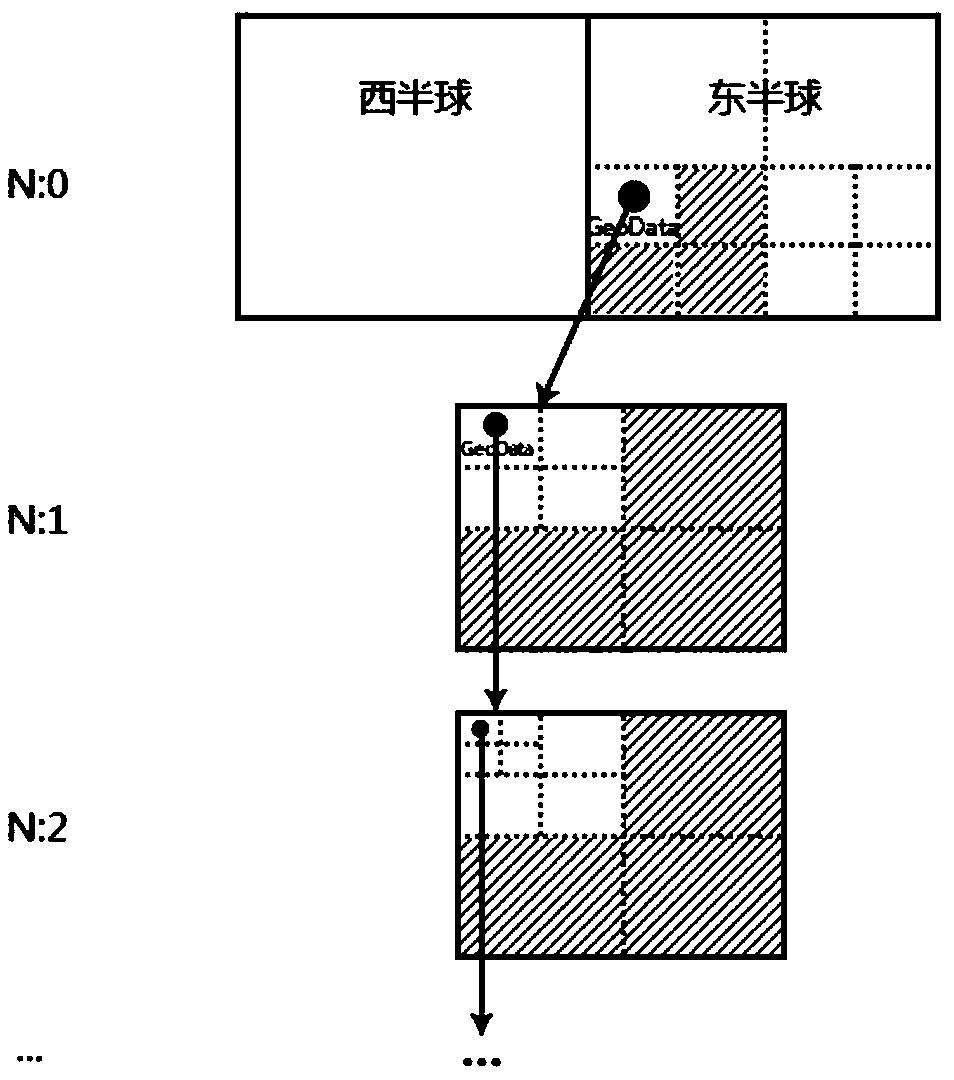
Discrete geographic data archiving management method
ActiveCN109325086AConvenient identity verificationSolve traversalFile access structuresGeographical information databasesMapping techniquesSmall data
The invention discloses a discrete geographic data archiving management method, comprising the following steps of: 1 uniformly encoding the discrete small data or files; 2 designing an efficient retrieval tree based on unified coding, which is convenient for quick query; 3 utilizing a large file memory mapping technology to realize fast read and write access. The method of the invention effectively realizes the efficient access and storage control of the discrete small data or files.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Authentication methods, devices, systems and therapeutic devices
ActiveCN105871857BAvoid same-identity situationsPrevent peepingTransmissionTherapeutic DevicesData transmission
The invention discloses an authentication method, an authentication device, an authentication system and treatment equipment. The authentication method comprises the steps of reading server information which is preset by a local machine, automatically establishing communication connection according to the server information in a wireless communication manner; and initiating self authentication by the treatment equipment, wherein self authentication comprises reading a global unique identification code and a product serial number which are pre-stored by the local machine; encrypting the global unique identification code and the product serial number which are stored in the treatment equipment, and transmitting the encrypted global unique identification code and the product serial number to a server for requesting self authentication; confirming a self authentication result according to information which returns from the server; if self authentication passes, starting data transmission with the server; and if self authentication fails, disconnecting communication connection with the server. The authentication method, the authentication device, the authentication system and the treatment equipment reduce operation difficulty and complexity in identity authentication.
Owner:BMC MEDICAL
An identity authentication system and reimbursement device
ActiveCN107948132BConvenient identity verificationReduce the possibility of theftFinanceSecuring communicationInternet privacyEngineering
The application discloses an identity authentication system and reimbursement equipment. Wherein, the identity authentication system includes a processor, a biological feature collection component connected to the processor, and a behavioral feature collection component; wherein, the biological feature collection component is used to collect user biometric information; the behavioral feature collection component Used to collect the user’s behavior characteristic information; the processor is used to use at least one of the biological characteristic collection component and the behavior characteristic collection component to obtain the user’s characteristic information, and use the user’s characteristic information to verify the user’s identity verify. The above solution can realize identity authentication by using different characteristics of users.
Owner:YGSOFT INC
Identity authentication system based on block chain technology
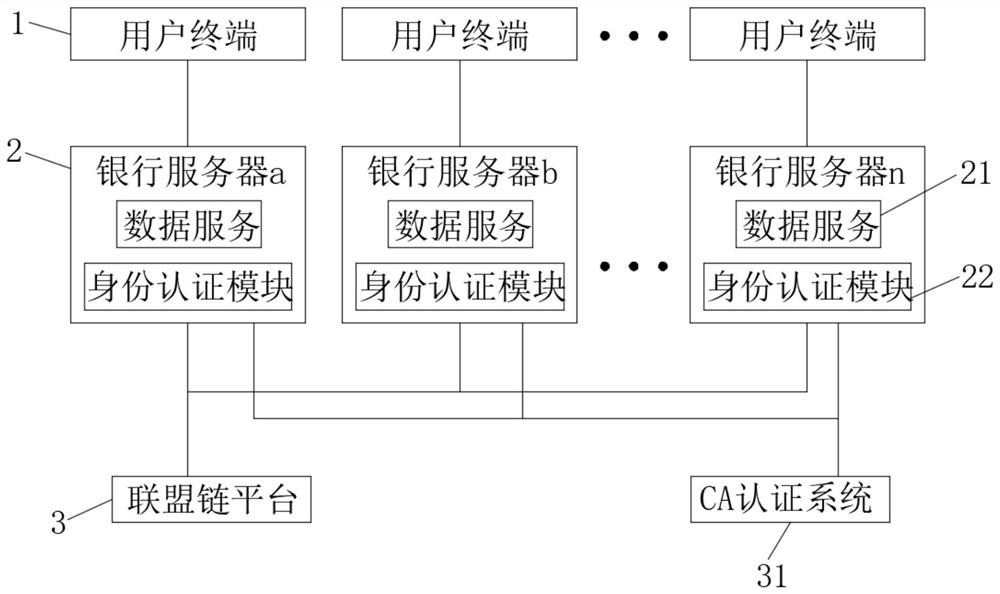
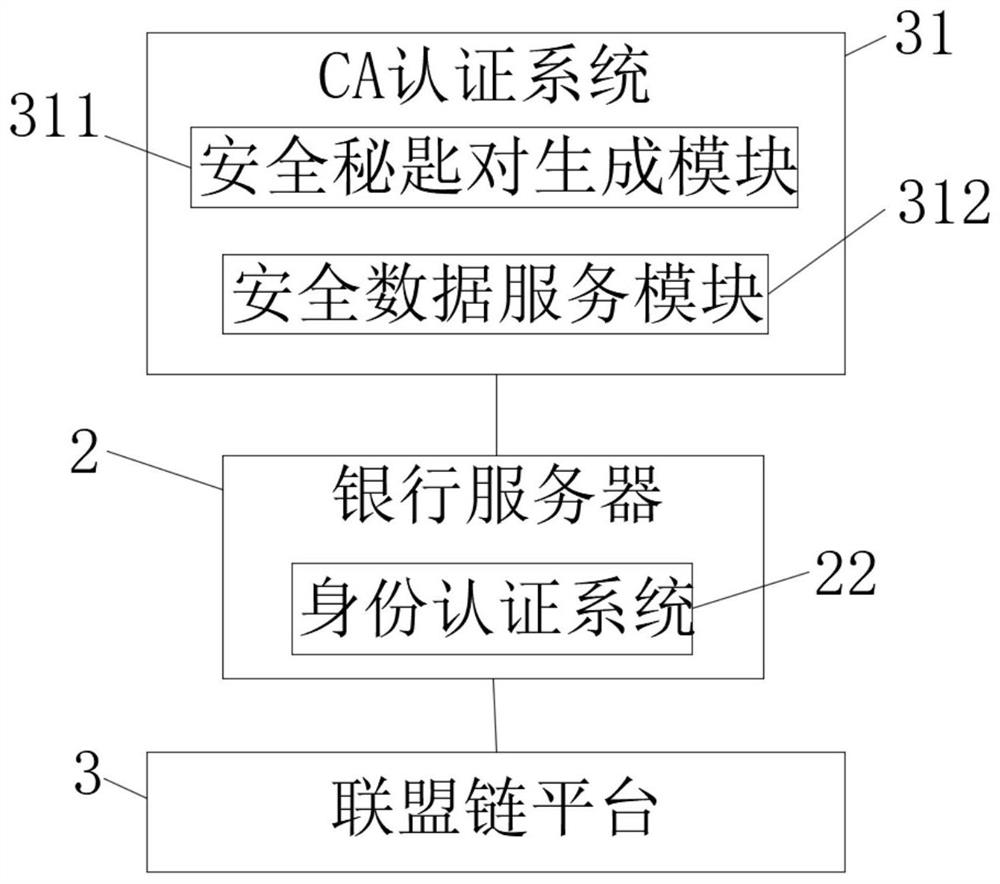
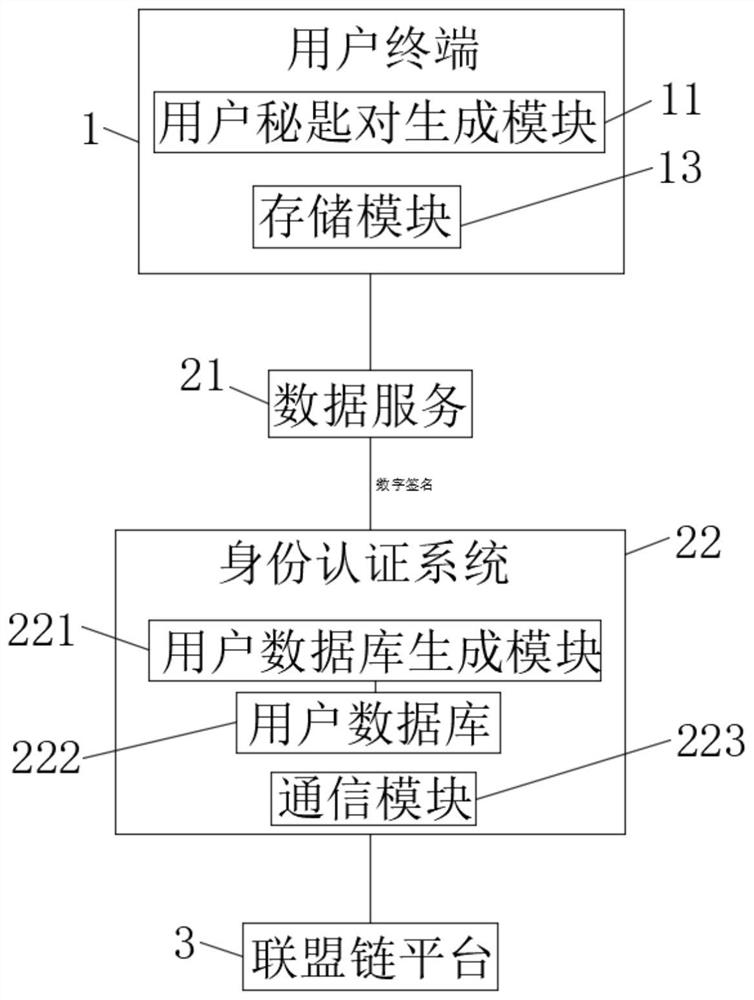
PendingCN113141256AImprove securityConvenient identity verificationKey distribution for secure communicationUser identity/authority verificationBanking industryInternet privacy
The invention discloses an identity authentication system based on a block chain technology, and belongs to the field of identity authentication. The identity authentication system based on the block chain technology comprises a user terminal, an alliance chain platform, a CA authentication module and a plurality of bank servers. The user terminal is used for generating a user secret key and storing the user secret key and a digital certificate; and the bank server is used for collecting related data such as personal information and secret keys of users according to banking business, and performing digital signature on the secret keys of the users to form digital certificates. According to the invention, when a user needs to handle services in different banking institutions, identity authentication can be carried out in a plurality of different banks by using the digital certificate without filling personal information again, and meanwhile, the system supports binding of a plurality of login modes and the digital certificate of the user, so that the identity authentication of the user is facilitated; and the business handling efficiency of the user and the security of private information secrecy are improved.
Owner:深圳华数云计算技术有限公司
Identity authentication method and device, computer equipment, storage medium and program product
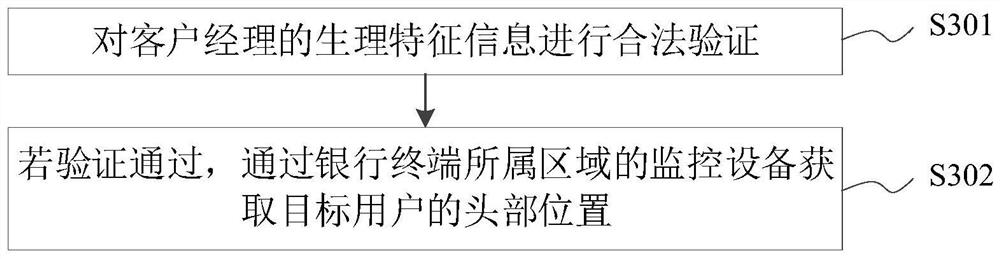
PendingCN114792001AImprove accuracyFacilitate identity authentication and business processingDigital data authenticationComputer equipmentEngineering
The invention relates to the technical field of information security, in particular to an identity authentication method and device, computer equipment, a storage medium and a program product. The method comprises the following steps: in response to an identity authentication request of a target user input in a bank terminal by a customer manager, obtaining a head position of the target user; the target user represents a user whose height is not matched with the installation position of the camera in the bank terminal; determining a target acquisition position according to the head position of the target user; according to the target collection position, controlling a camera to adjust a collection pose, and collecting a face image of the target user through the adjusted camera; the face of the target user is located at the central position of the view of the adjusted camera; and authenticating the identity of the target user based on the face image of the target user. By adopting the method, users with unconventional heights can conveniently carry out identity authentication and business handling.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Identity authentication method and system based on body shapes and movements
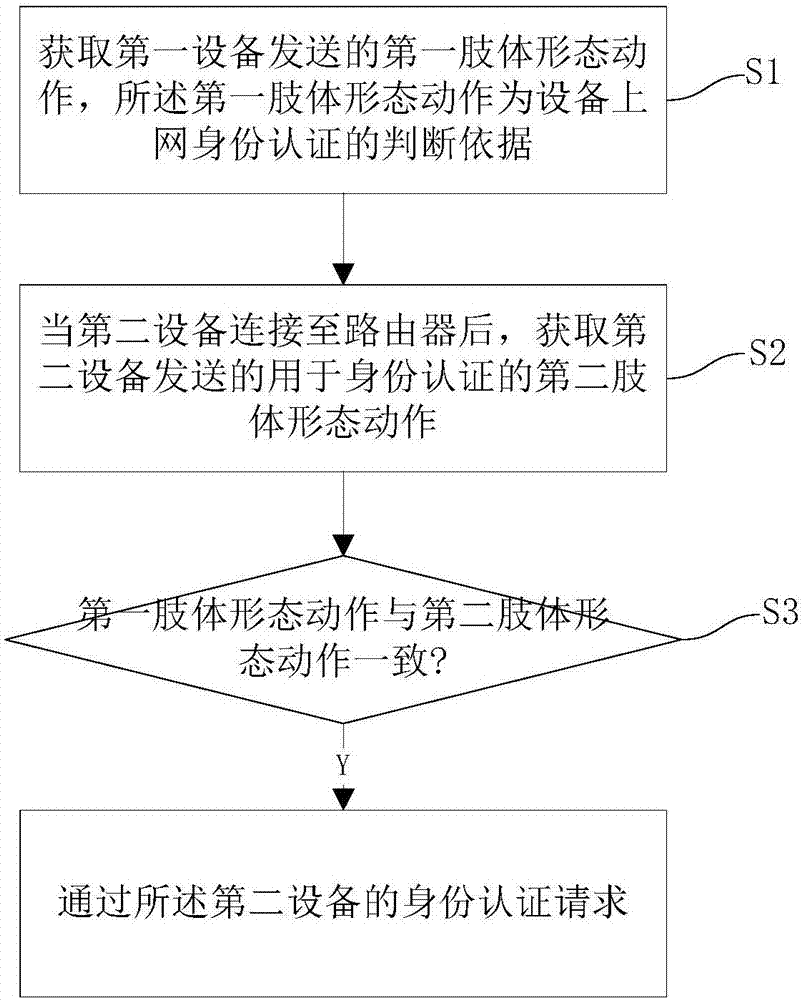
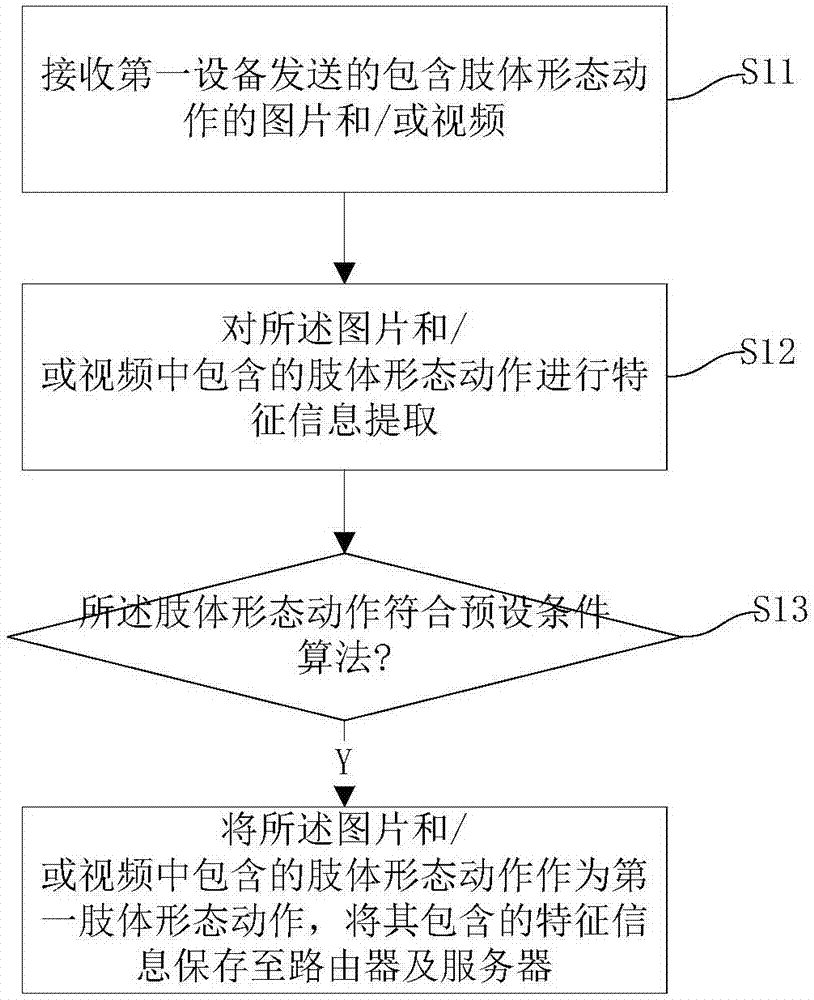
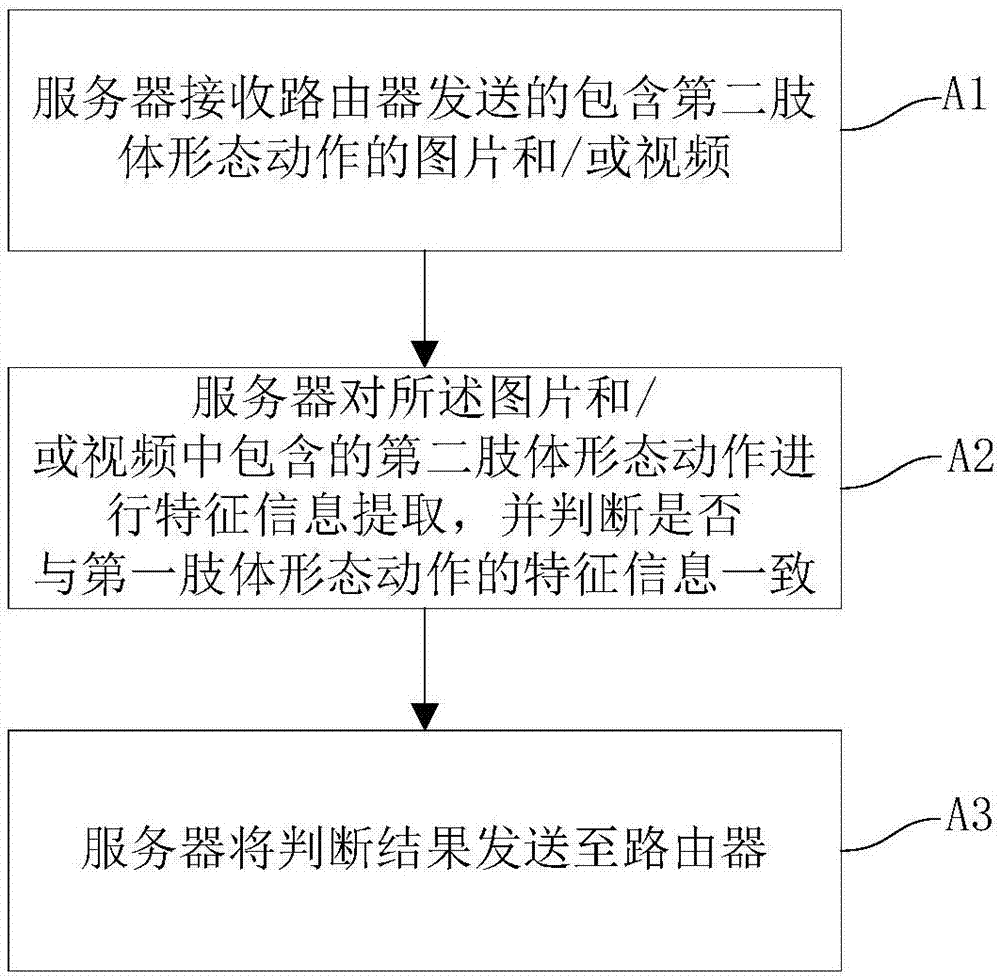
InactiveCN107995209AAuthentication IntelligenceConvenient identity verificationCharacter and pattern recognitionTransmissionBody shapePropagation effect
The invention discloses an identity authentication method and system based on body shapes and movements. The method comprises the following steps: S1, acquiring first body shapes and movements sent byfirst equipment, wherein the first body shapes and movements serve as a judgment basis for identity authentication for network access of equipment; S2, after second equipment is connected to a router, acquiring second body shapes and movements sent by the second equipment and used for the identity authentication; and S3, judging whether the first body shapes and movements are identical to the second body shapes and movements or not, and approving an identity authentication request of the second equipment if the first body shapes and movements are identical to the second body shapes and movements. The method and system provided by the embodiment of the invention has the advantages that the body shapes and movements are identified for the identity authentication, so that the identity authentication is more intelligent and convenient, and better propagation effects and more fun are achieved.
Owner:台州市吉吉知识产权运营有限公司
Identity authentication method, device and medium
ActiveCN109361718BConvenient identity verificationPrevent leakageUser identity/authority verificationInformation technology support systemInternet privacyEngineering
The embodiments of the present invention disclose an identity authentication method, device and medium. The method is applied to a vehicle in a system composed of a server, a terminal and a vehicle, including: receiving a digital key sent by the terminal, where the digital key includes vehicle terminal information and terminal identity information; calculate the hash value of the vehicle terminal information and the terminal identity information; if the hash value is in the white list, output the permission control information. The problem that the security of the identity authentication method in the prior art is relatively weak is solved, and the technical effect of effectively protecting user information is achieved.
Owner:上海银基信息安全技术股份有限公司
Identity authentication method and system based on block chain
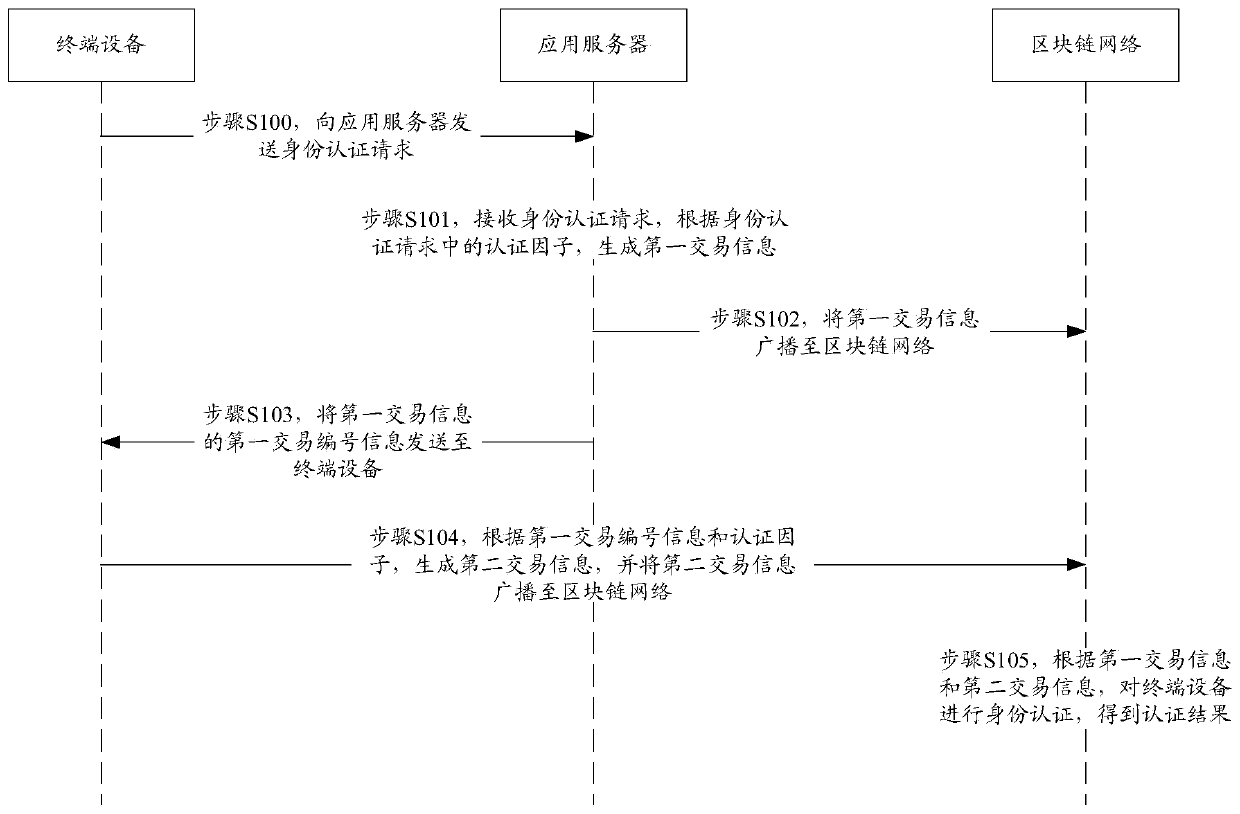
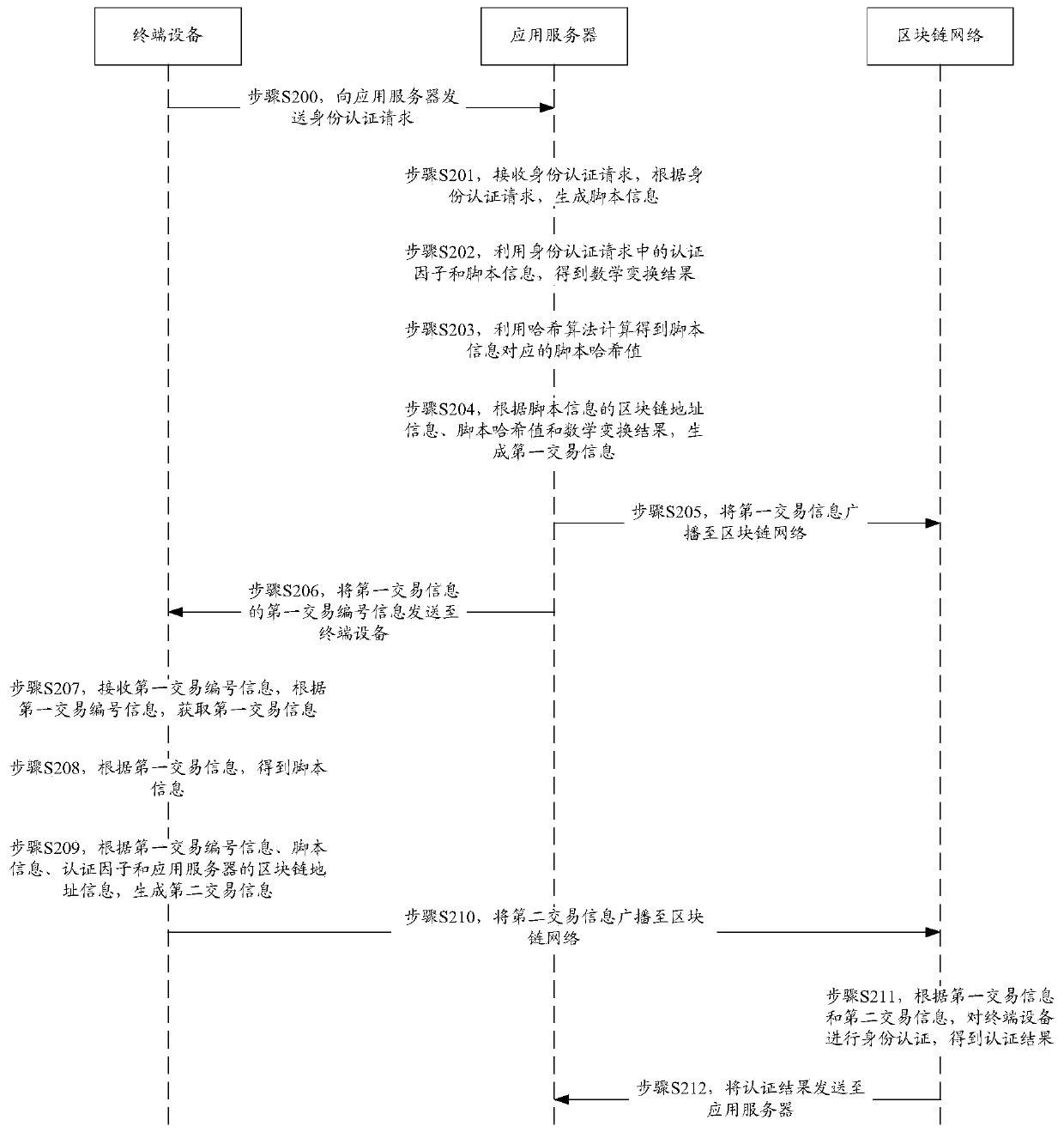
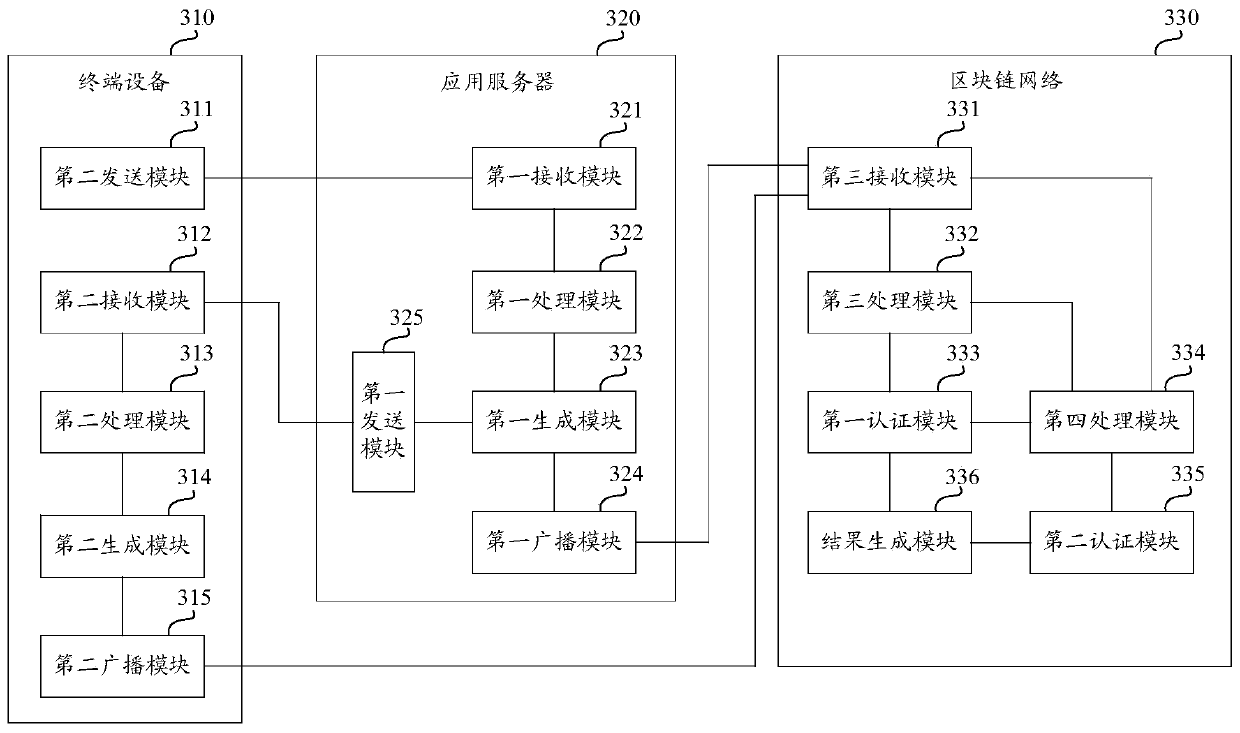
ActiveCN106534160BAuthentication securityConvenient identity verificationTransmissionApplication serverTerminal equipment
The invention discloses an identity authentication method and system based on a block chain. The method includes the steps of a terminal device sending an identity authentication request including an authentication factor to an application server, an application server receiving the identity authentication request and generating first transaction information according to the authentication factor in the identity authentication request, the application server broadcasting the first transaction information to a block chain network, the application server sending the first transaction number information of the first transaction information to the terminal device, the terminal device receiving the first transaction number information, generating second transaction information according to the first transaction number information and the authentication factor and broadcasting the second transaction information to the block chain network, and the block chain network conducting identity authentication for the terminal device according to the first transaction information and the second transaction information to obtain the authentication result. According to the technical scheme of the invention, identity authentication for a terminal device can be safety and conveniently carried out through a block chain network.
Owner:JIANGSU PAYEGIS TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com