Method, devices and system for user identity authentication
A user identity authentication and identity authentication technology, applied in the field of user identity authentication, can solve problems such as inability to complete user identity authentication, cost consumption, and easy loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
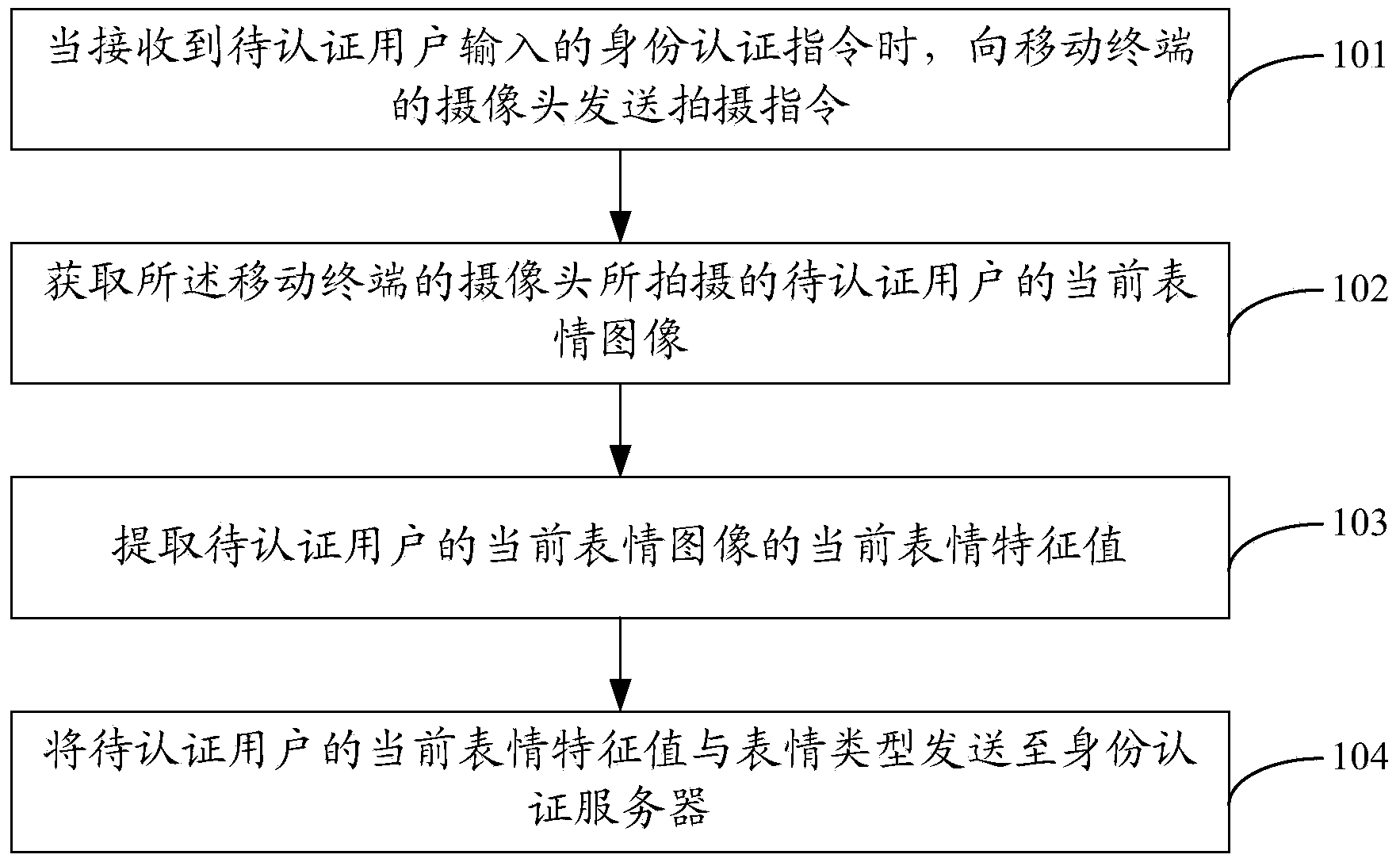
[0113] figure 1 It is a flow chart of Embodiment 1 of a user identity authentication method of the present invention, which is applied to a mobile terminal. Embodiment 1 mainly prepares for user identity authentication. The method includes:
[0114] Step 101: When receiving an identity authentication instruction input by a user to be authenticated, send a shooting instruction to the camera of the mobile terminal.
[0115] When the user to be authenticated logs into the bank client terminal on the mobile terminal or the client terminal of the shopping website to make payment for shopping, in order to protect the property safety of the user, it is necessary to perform identity authentication on the user to be authenticated. The user to be authenticated clicks an identity authentication button provided on the client interface of the mobile terminal, etc., to send an identity authentication instruction.
[0116] When the mobile terminal receives the identity authentication instru...
Embodiment 2
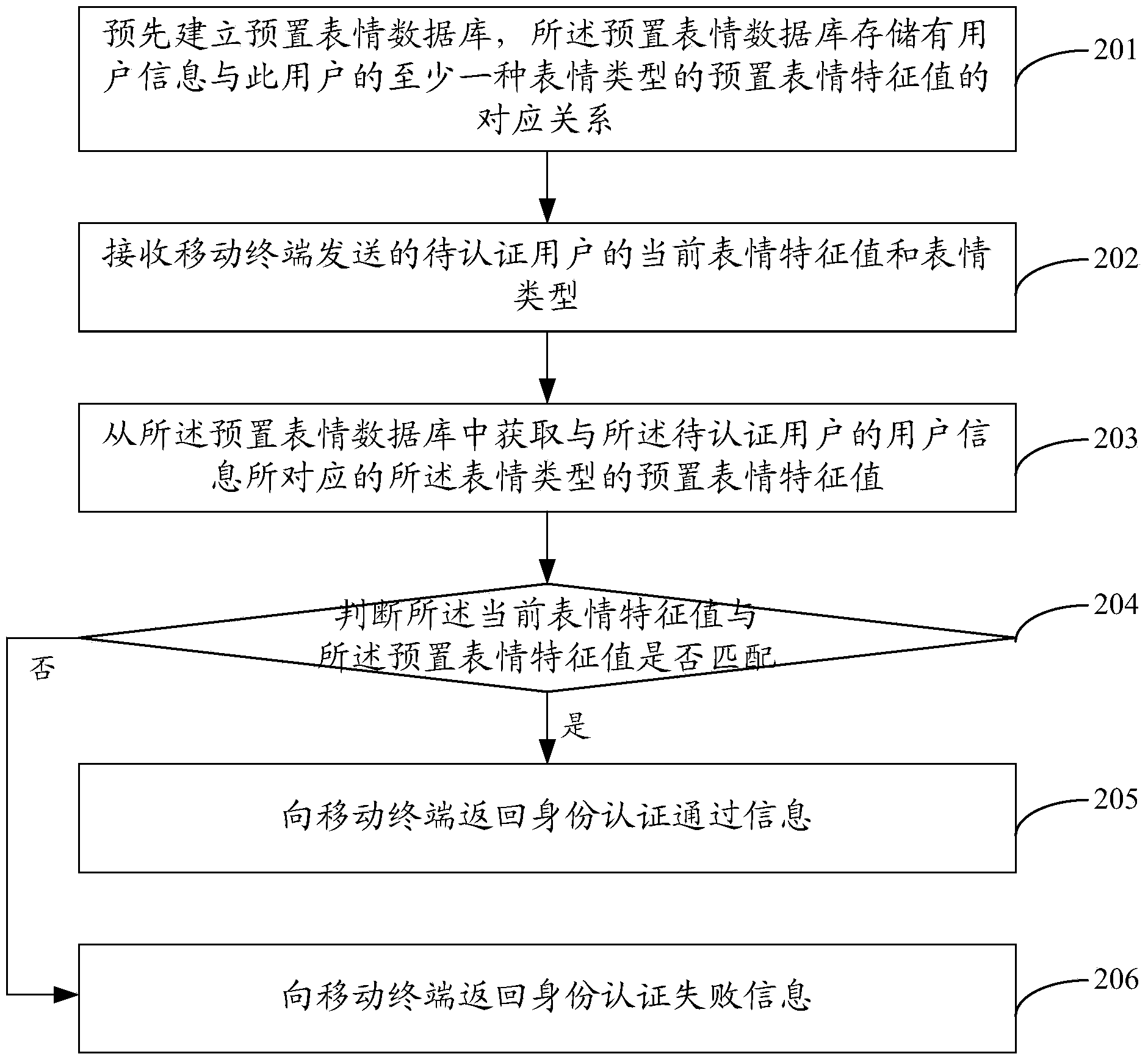
[0148] figure 2 It is a flow chart of Embodiment 2 of a user identity authentication method of the present invention, which is applied to an identity authentication server. Embodiment 2 mainly describes the execution process of user identity authentication. The method includes:
[0149] Step 201: Establish a preset expression database in advance, and the preset expression database stores the correspondence between user information and preset expression feature values of at least one type of expression of the user.
[0150] The identity authentication server pre-establishes a database of preset facial expressions, and the database of preset facial expressions stores correspondences between user information of multiple users and feature values of preset facial expressions. Wherein, the preset expression database may store preset expression feature values of various types of expressions for each user.
[0151] When the identity authentication server establishes the preset e...
Embodiment 3
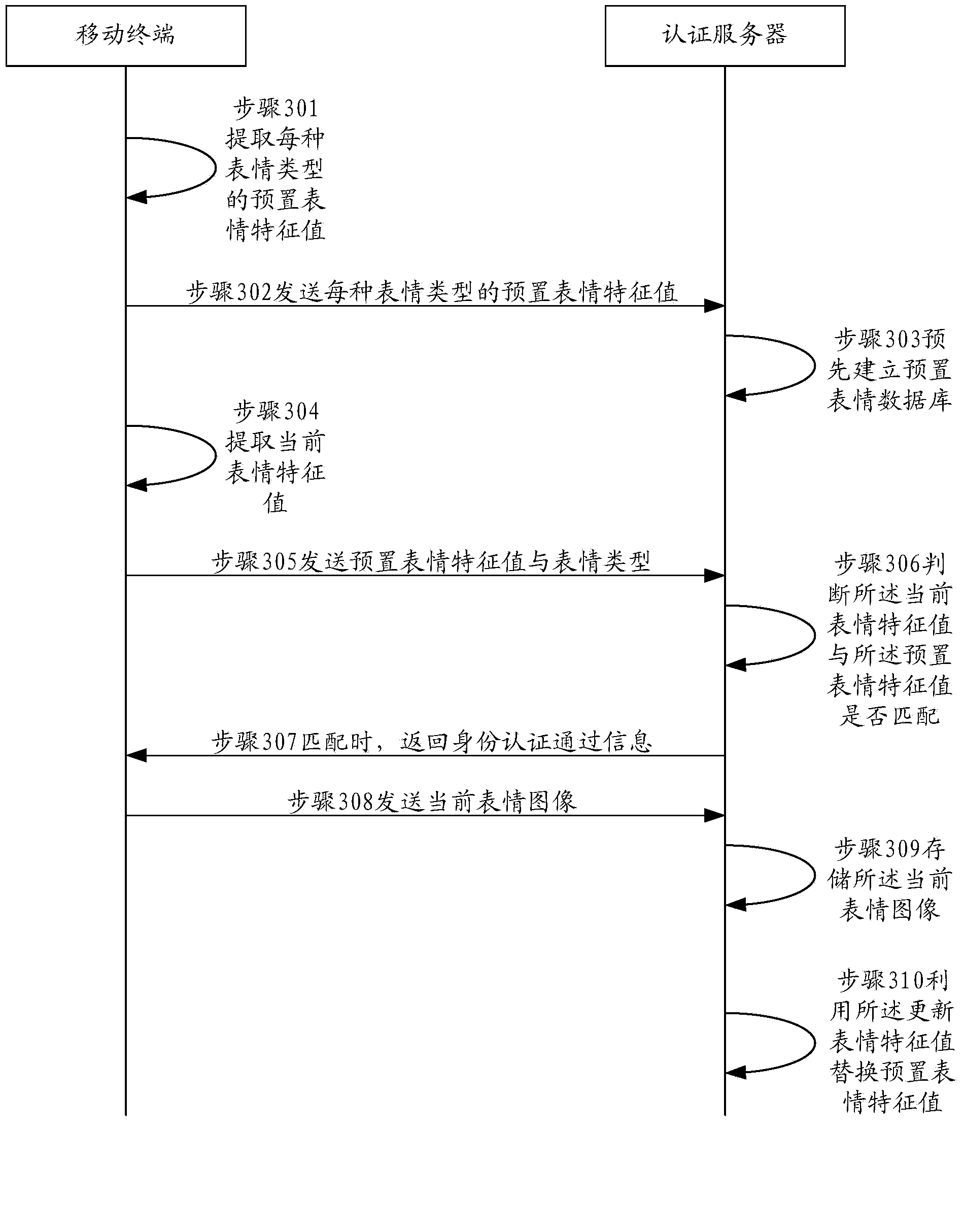
[0192] image 3 It is a sequence diagram of Embodiment 3 of a user identity authentication method of the present invention, which is applied to a user identity authentication system. Embodiment 3 describes the entire process of user identity authentication, and the method includes:
[0193] Step 301: The mobile terminal sends a shooting instruction to the camera of the mobile terminal, acquires preset facial expression images of at least one type of facial expressions of the user captured by the camera of the mobile terminal, and extracts preset expressions in the preset facial expression images of each facial expression type of the user. Expression feature value.
[0194] Step 302: The mobile terminal sends the preset emoticon feature value of each emoticon type to the authentication server.
[0195] Step 303: The authentication server uses the preset expression feature values of each type of expression of the user to pre-establish a preset expression database.
[0196] S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com