CRM system anti-unauthorized implementation method and device and storage medium
A CRM system and implementation method technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problem of no service execution authority for job numbers, and achieve the purpose of avoiding illegal business transactions, preventing unauthorized access, and improving security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
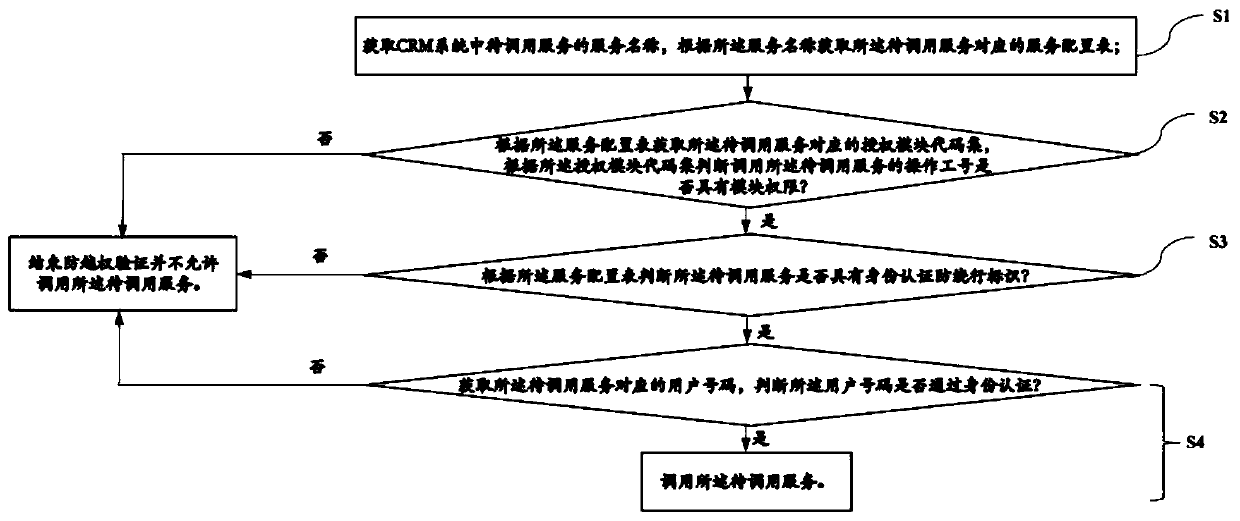
[0075] Embodiment one, as figure 1 As shown, a method for realizing the anti-overreach of a CRM system includes the following steps:
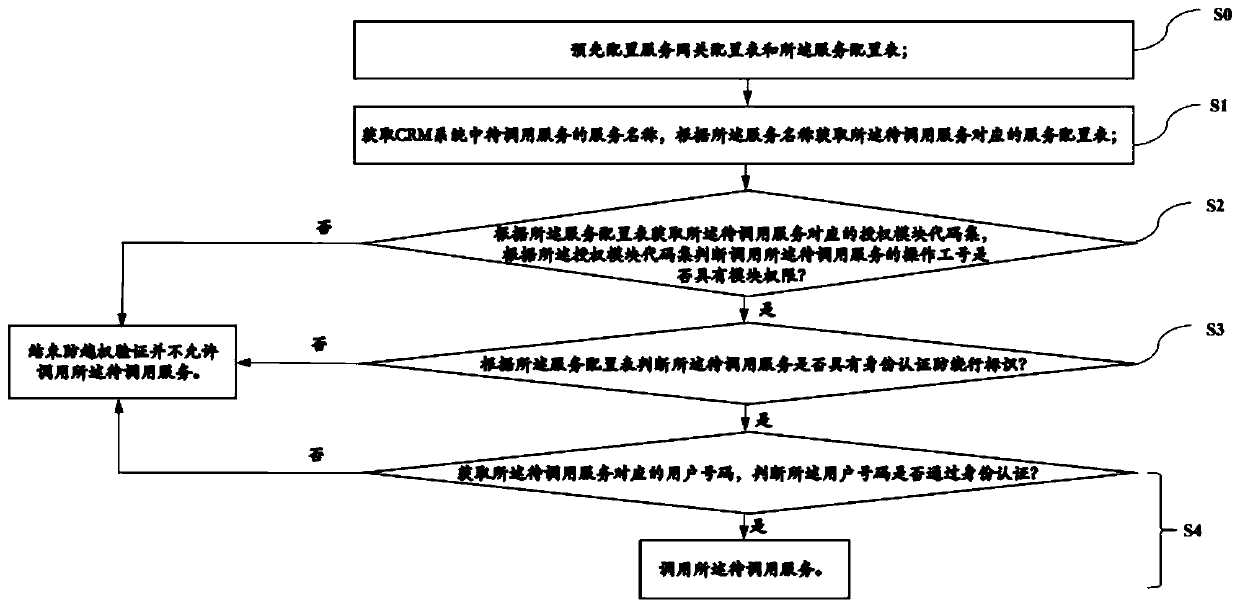
[0076] S1: Obtain the service name of the service to be called in the CRM system, and obtain the service configuration table corresponding to the service to be called according to the service name;
[0077] S2: Obtain the authorization module code set corresponding to the service to be called according to the service configuration table, and judge whether the operator number calling the service to be called has module authority according to the authorization module code set, and if so, execute S3, If not, then end the authorization verification and do not allow calling the service to be called;
[0078] S3: According to the service configuration table, it is judged whether the service to be called has an identity authentication and anti-circumvention flag, if yes, execute S4, if not, end the verification of preventing unauthorized access and n...
Embodiment 2
[0112] Embodiment two, such as Figure 6 As shown, a CRM system anti-overreach implementation device includes a data acquisition module, a first judgment module, a second judgment module, a third judgment module and a service call module;
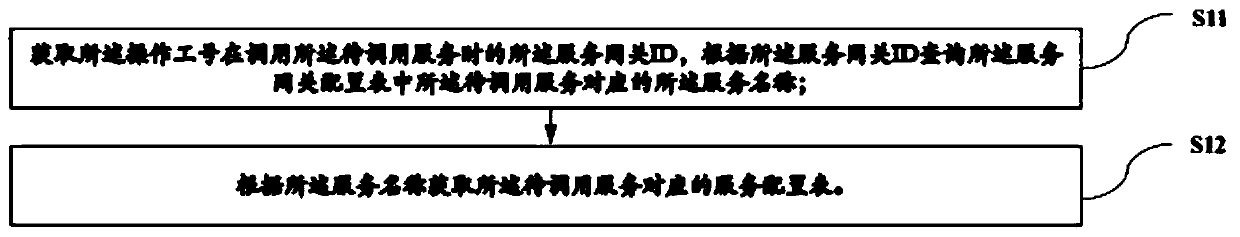
[0113] The data obtaining module is used to obtain the service name of the service to be called in the CRM system, obtain the service configuration table corresponding to the service to be called according to the service name; and is also used to obtain the service configuration table to be called according to the service configuration table Authorization module code set corresponding to the service;
[0114] The first judging module is used to judge whether the operator number calling the service to be called has module authority according to the authorization module code set;
[0115] The second judging module is used to judge whether the service to be called has an identity authentication anti-bypass identification according to the serv...
Embodiment 3
[0142] Embodiment 3. Based on Embodiment 1 and Embodiment 2, this embodiment also discloses a CRM system anti-overreach implementation device, including a processor, a memory, and a device stored in the memory and capable of running on the processor. A computer program that, when run, implements the figure 1 The specific steps from S1 to S4 are shown.
[0143] Through the computer program stored in the memory and run on the processor, the anti-overreach of the CRM system of the present invention is realized, and the problem of over-authorization in the prior art that the employee number has no service execution authority and the service call fails to pass the user identity authentication is solved. The double security reinforcement of the CRM system prevents services without functional module authority from being illegally invoked, avoids bypassing customer identity authentication for illegal business transactions, prevents unauthorized access, and greatly improves the securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com