Activation method, mobile terminal and server for virtual key configuration information
A technology of virtual keys and configuration information, applied in the field of vehicles, can solve problems such as illegal calls, reduce the security of unlocking operations, and reduce the reliability of tokens, and achieve the effect of improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
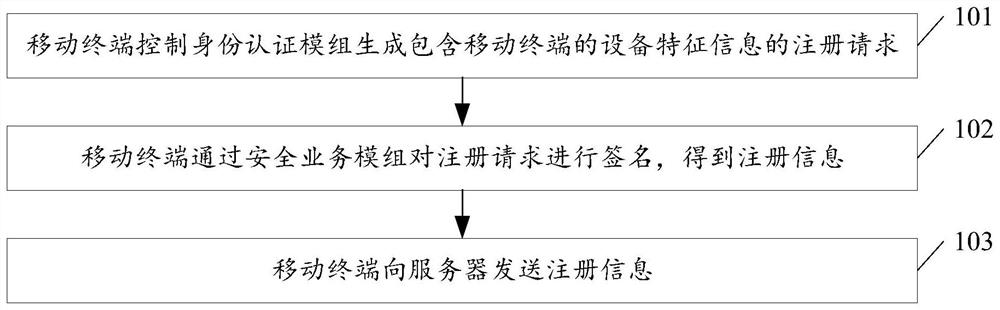
[0060] see figure 1 , figure 1 It is a schematic flowchart of a method for activating virtual key configuration information disclosed in an embodiment of the present invention. Such as figure 1 As shown, the activation method of the virtual key configuration information may include the following steps:
[0061] 101. The mobile terminal controls the identity authentication module to generate a registration request including device characteristic information of the mobile terminal.
[0062] In the embodiment of the present invention, the terminal device may be a smart phone, a smart bracelet or other devices. The identity authentication module may be a module in the trusted zone (Trusted Zone) of the operating system of the mobile terminal, such as the Internet Finance Authentication Alliance (Internet Finance Authentication Alliance, IFAA) mobile terminal trusted application (TrustedApplication, TA). The mobile terminal can control the virtual key application module to call...
Embodiment 2
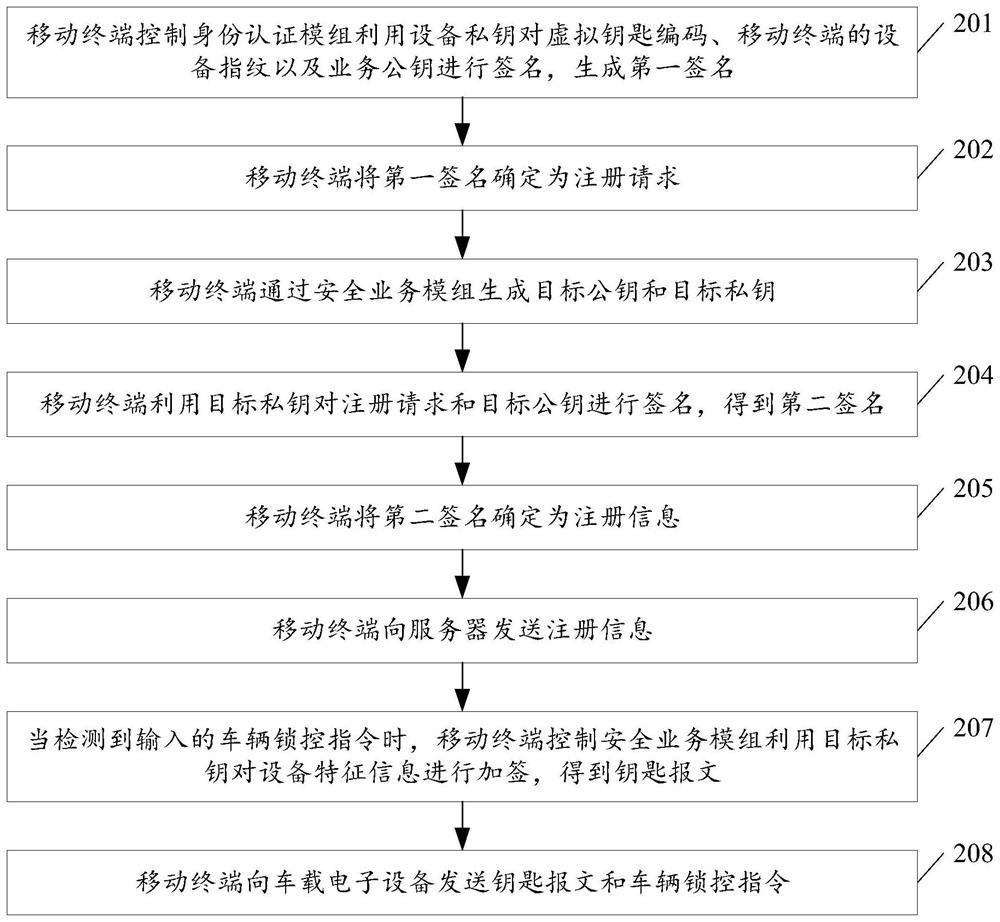
[0072] see figure 2 , figure 2 It is a schematic flowchart of another method for activating virtual key configuration information disclosed in the embodiment of the present invention. Compared with Embodiment 1, this embodiment of the present invention explains in more detail how registration requests and registration information are generated, and adds a process in which the mobile terminal controls the unlocking of the vehicle, which can ensure the accuracy of the configuration information for activating the virtual key, and can also Improving the accuracy of verification of registration information can in turn improve the safety of operations performed on vehicles. Such as figure 2 As shown, the activation method of the virtual key configuration information may include the following steps:
[0073] 201. The mobile terminal controls the identity authentication module to use the device private key to sign the virtual key code, the device fingerprint of the mobile termin...
Embodiment 3
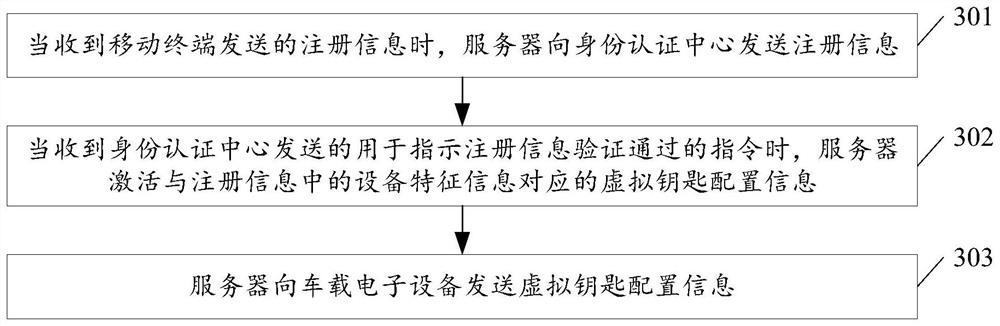
[0089] see image 3 , image 3 It is a schematic flowchart of another method for activating virtual key configuration information disclosed in the embodiment of the present invention. Such as image 3 As shown, the activation method of the virtual key configuration information may include the following steps:
[0090] 301. When receiving the registration information sent by the mobile terminal, the server sends the registration information to the identity authentication center, and the registration information is used for the identity authentication center to verify the registration information.
[0091] In the embodiment of the present invention, the server may be a Bluetooth authentication server, etc., and the registration information sent by the mobile terminal may include the device feature information of the mobile terminal, the first signature generated according to the device feature information (ie, the registration request), and the target public key. , the device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com