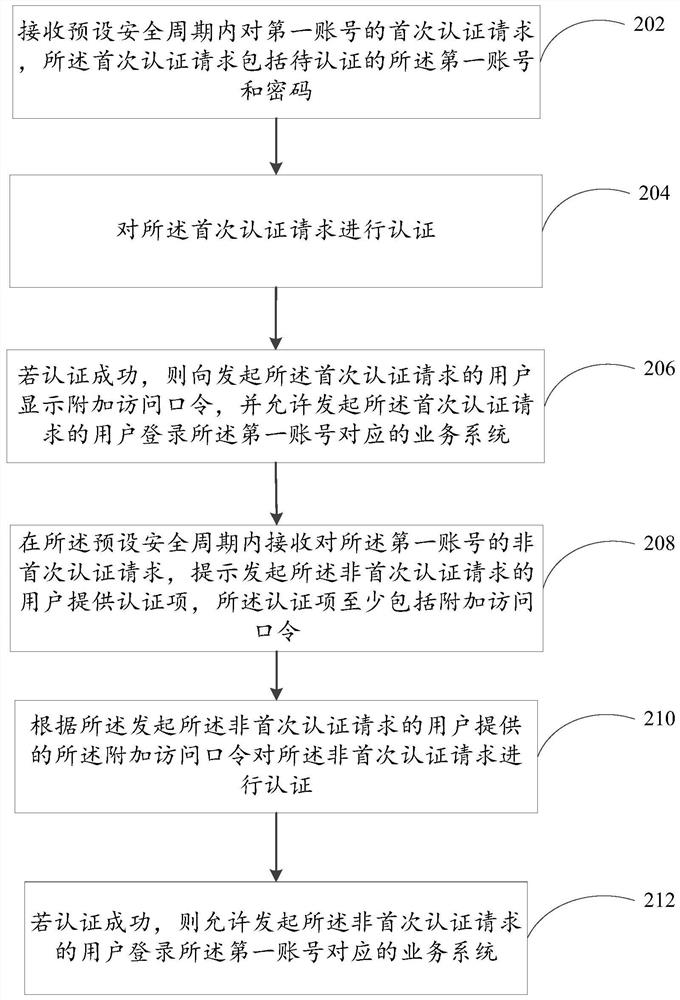
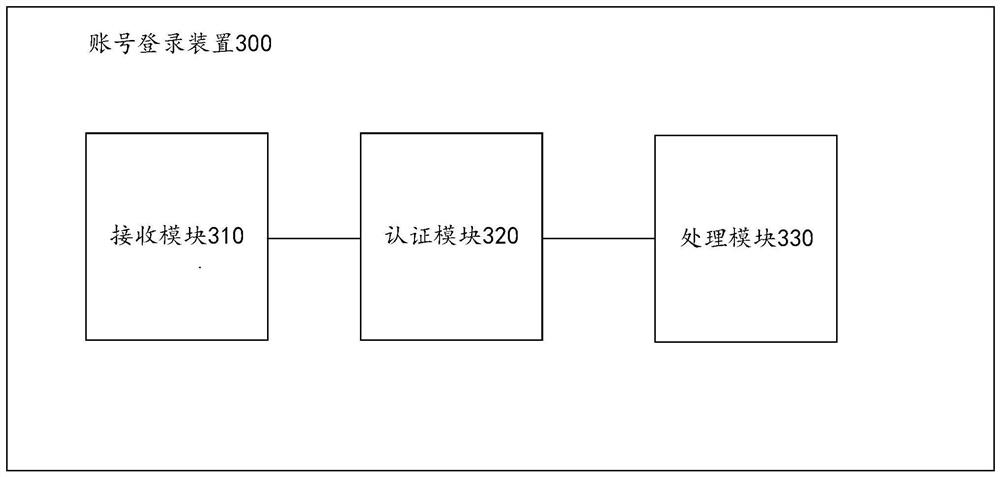
Account login method, device, computing device and storage medium
A technology of account login and account, which is applied in the information field, can solve problems such as unrestricted and inability to discover account authentication in time, and achieve the effect of reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] In the following description, numerous specific details are set forth in order to provide a thorough understanding of the specification. However, this specification can be implemented in many other ways different from those described here, and those skilled in the art can make similar extensions without violating the connotation of this specification, so this specification is not limited by the specific implementations disclosed below.
[0072] In this article, "first", "second", etc. are only used to distinguish each other, not to indicate the degree of importance and order, or the prerequisite for mutual existence.
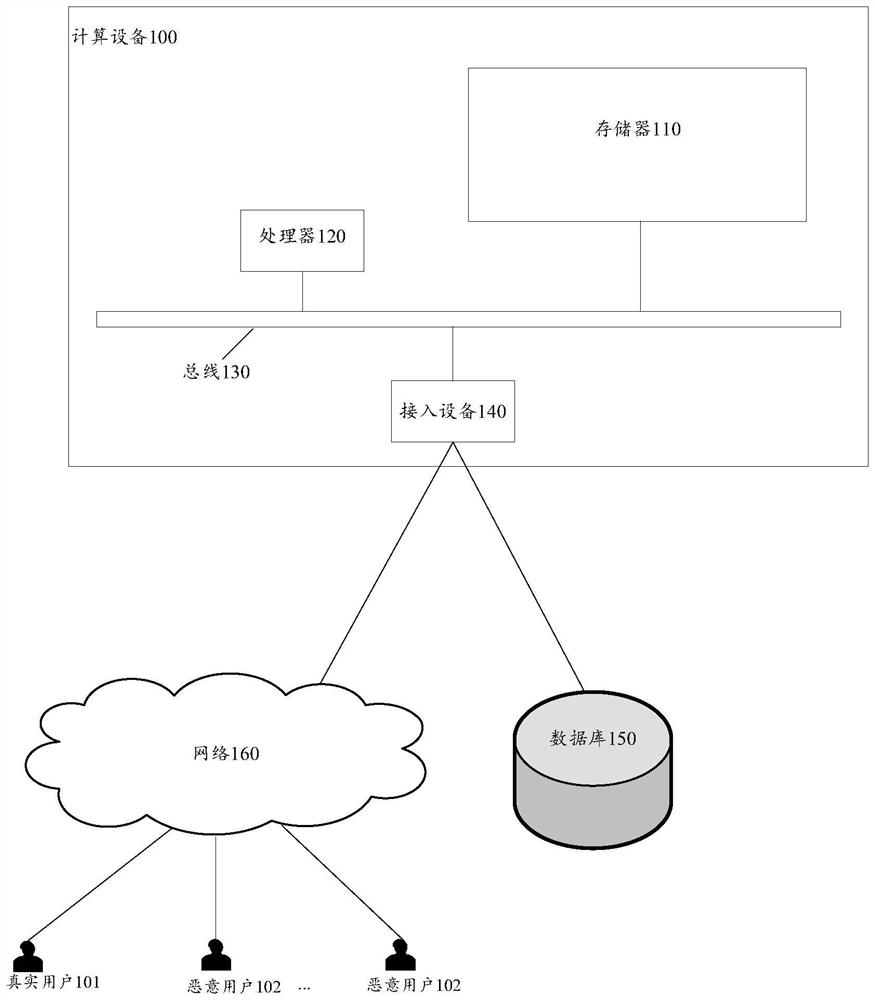
[0073] figure 1 is a structural block diagram illustrating a computing device 100 according to an embodiment of the present specification. Components of the computing device 100 include, but are not limited to, a memory 110 and a processor 120 . The processor 120 is connected to the memory 110 through the bus 130, and the database 150 is used to save th...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap