Method for borrowing device, terminal device and server
A technology for terminal equipment and servers, applied in the fields of instruments, data processing applications, computing, etc., can solve the problems of complex equipment management process, low borrowing efficiency, occupation of staff, etc., to simplify equipment management process, improve borrowing efficiency, save money The effect of registration time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, various implementation modes of the present invention will be described in detail below in conjunction with the accompanying drawings. However, those of ordinary skill in the art can understand that, in each implementation manner of the present invention, many technical details are provided for readers to better understand the present application. However, even without these technical details and various changes and modifications based on the following implementation modes, the technical solution claimed in this application can also be realized.
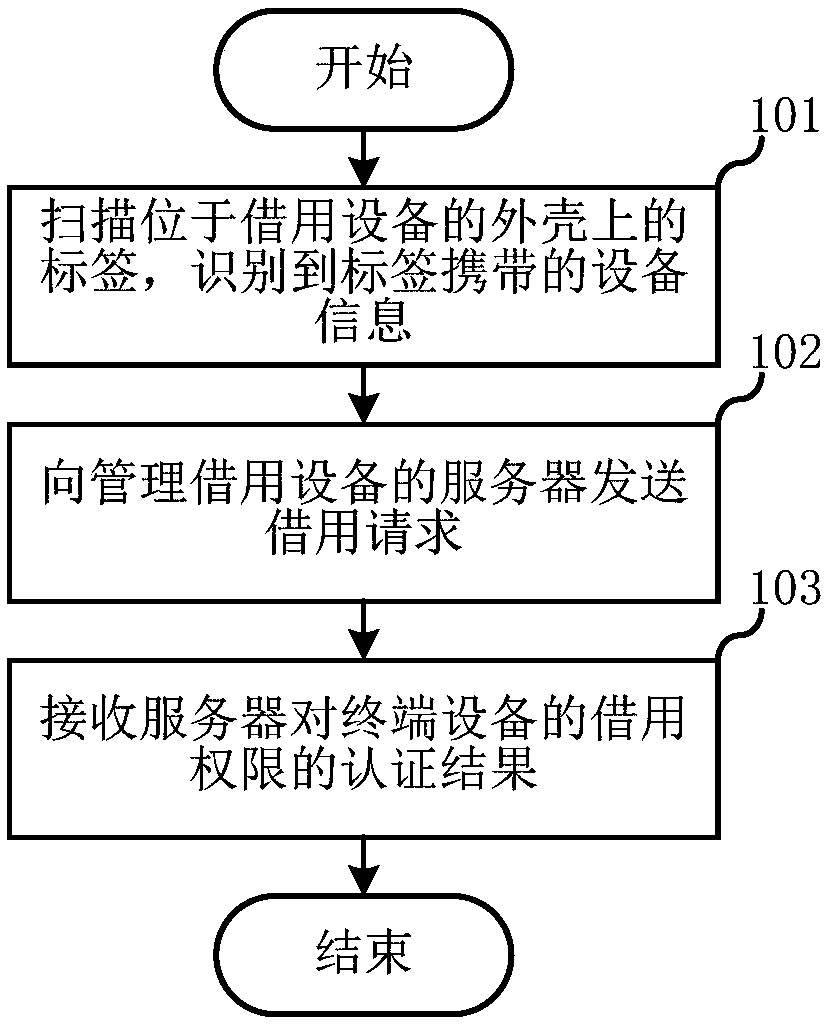
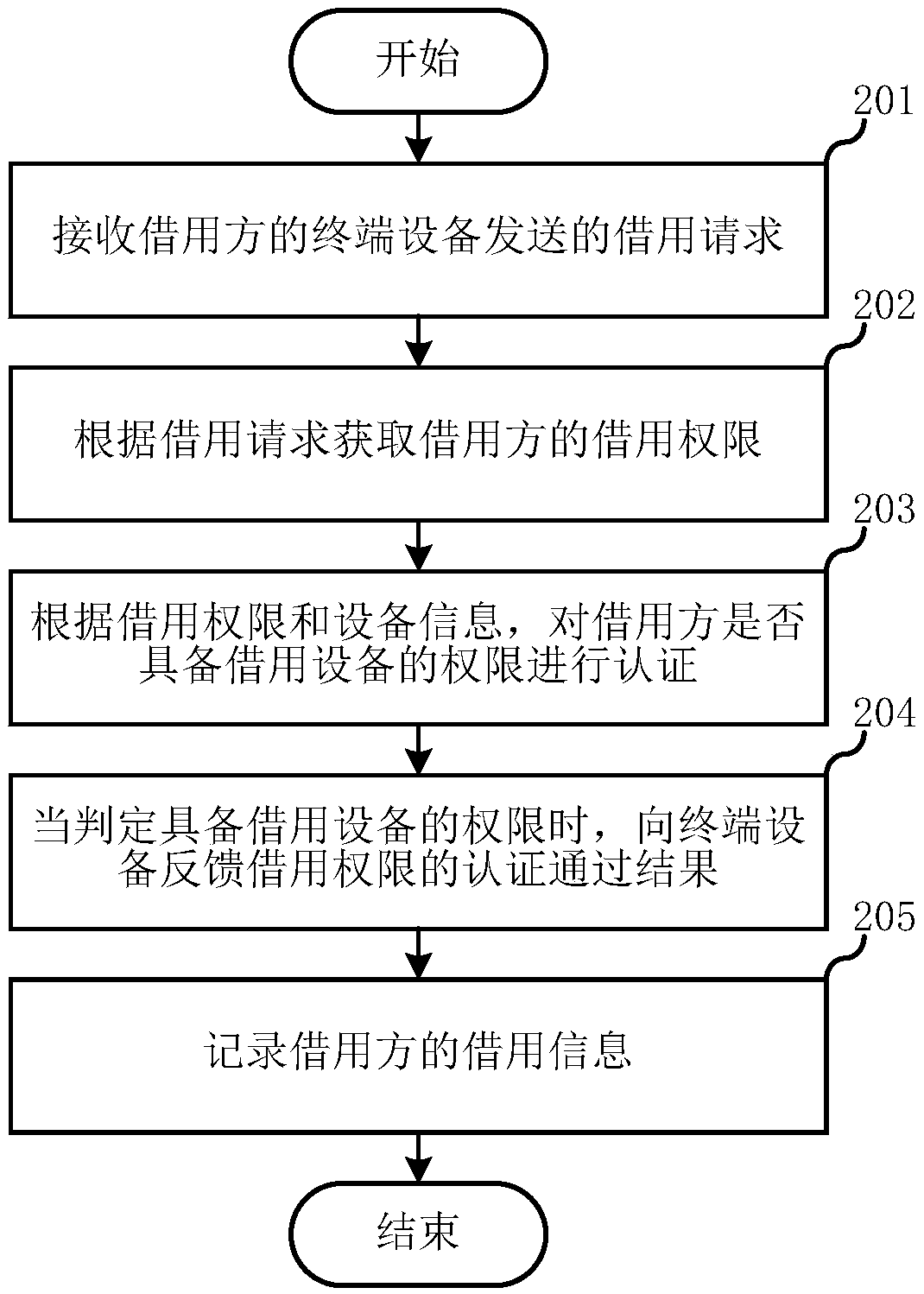
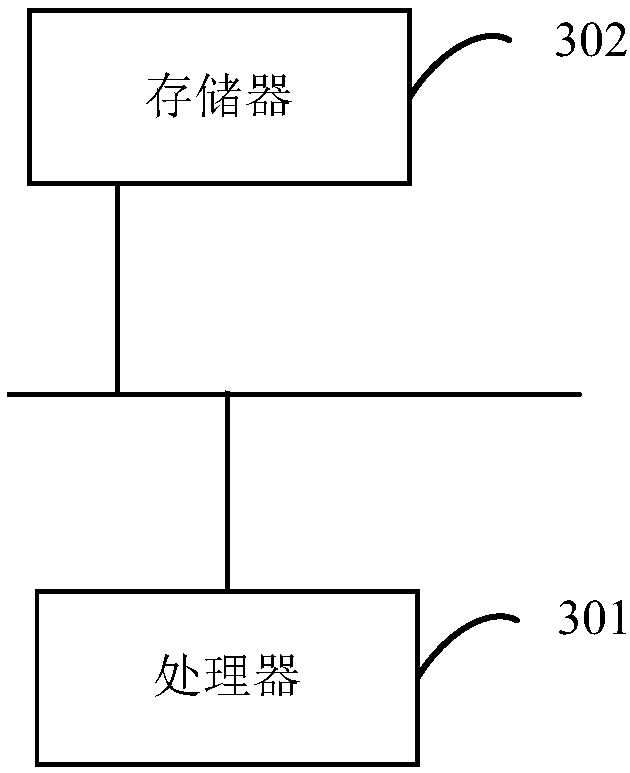
[0021] A first embodiment of the present invention relates to a borrowing method of a device. Applied to terminal equipment, in this embodiment, by using the label set on the shell of the borrowing device, it can play a role in reminding the borrower to pass the authority authentication when borrowing, and b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com