An enterprise real-name authentication method and authentication server
A real-name authentication, enterprise technology, applied in the field of information security, can solve the problems of error-prone, high logistics or time cost, low efficiency, etc., to achieve the effect of improving user login experience, efficient and convenient online real-name authentication service
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
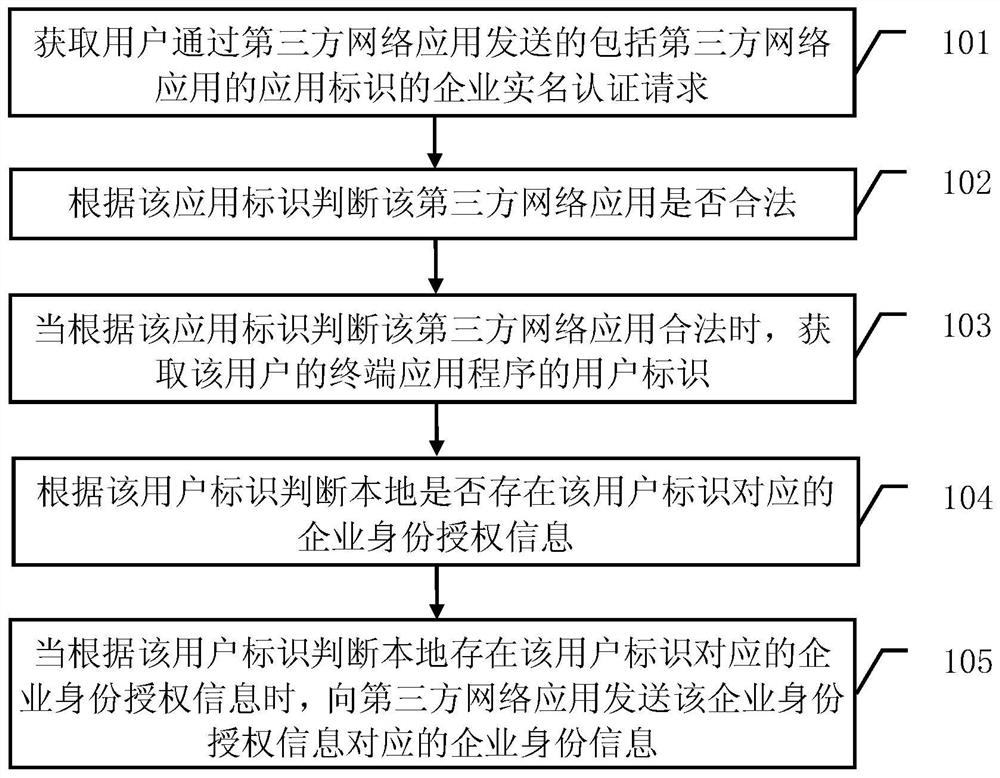
[0030] see figure 1 , the embodiment of the present invention provides an enterprise real-name authentication method, which can be applied to an authentication server independently deployed as an objective third party. Such as figure 1 As shown, the enterprise real-name authentication method described in the embodiment of the present invention includes:
[0031] Step 101, obtain the enterprise real-name authentication request sent by the user through the third-party network application, and the enterprise real-name authentication request includes the application identification of the third-party network application;
[0032] Step 102, judging whether the third-party network application is legal according to the application identifier;
[0033] Step 103, when judging that the third-party network application is legal according to the application identifier, obtain the user identifier of the user's terminal application program;
[0034] Step 104, according to the user identifi...
no. 2 example
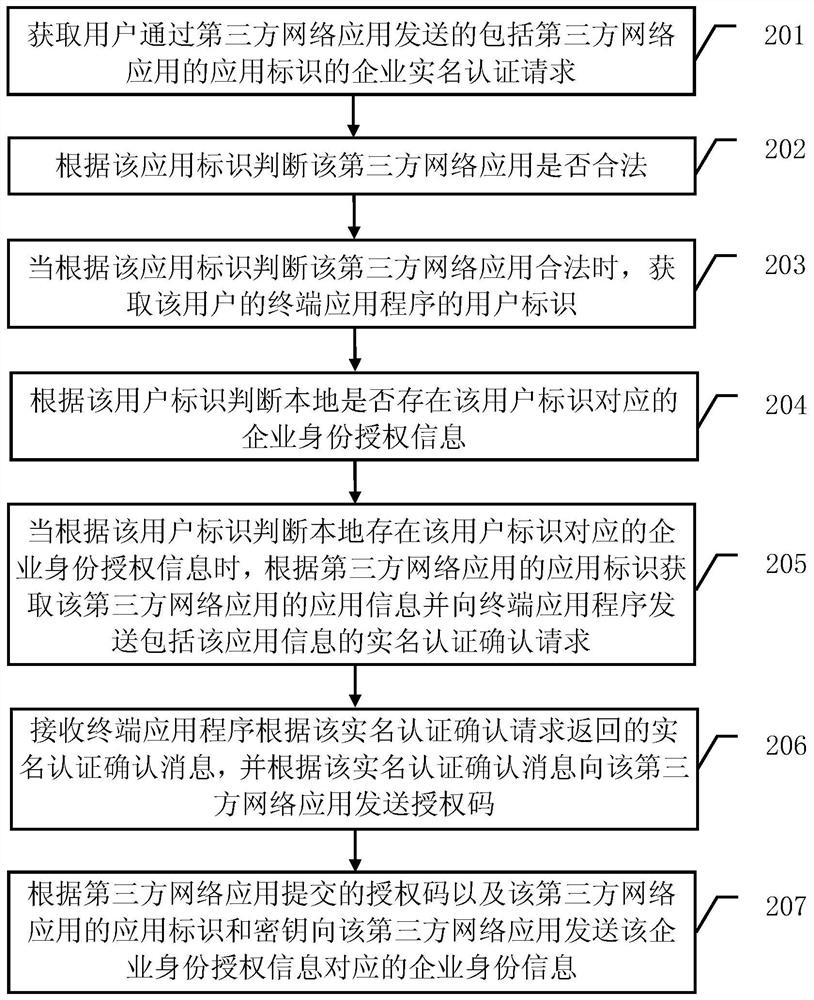
[0040] see figure 2 , the embodiment of the present invention provides a specific implementation of an enterprise real-name authentication method. Such as figure 2As shown, the enterprise real-name authentication method described in the embodiment of the present invention includes:
[0041] Step 201, obtain the enterprise real-name authentication request sent by the user through the third-party network application, and the enterprise real-name authentication request includes the application identification of the third-party network application;
[0042] Step 202, judging whether the third-party network application is legal according to the application identifier;
[0043] Step 203, when judging that the third-party network application is legal according to the application identifier, obtain the user identifier of the user's terminal application program;
[0044] Step 204, according to the user identification, it is judged whether the enterprise identity authorization info...
no. 3 example
[0107] see Figure 6 , the embodiment of the present invention provides an authentication server, which can be independently deployed as an objective third party and applied to the scenario of providing real-name authentication services for enterprises to log in to third-party network applications. Such as Figure 6 As shown, the authentication server in the embodiment of the present invention includes:
[0108] The first acquiring module 601 is configured to acquire the enterprise real-name authentication request sent by the user through the third-party network application, wherein the enterprise real-name authentication request includes the application identification of the third-party network application;
[0109] The first judging module 602 is configured to judge whether the third-party network application is legal according to the application identifier;
[0110] The second acquiring module 603 is configured to acquire the user identifier of the user's terminal applica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com