A safety control method and system and related equipment
A security control and user technology, applied in the field of communication, can solve the problems of adverse effects on public security, inability to legally monitor signals, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
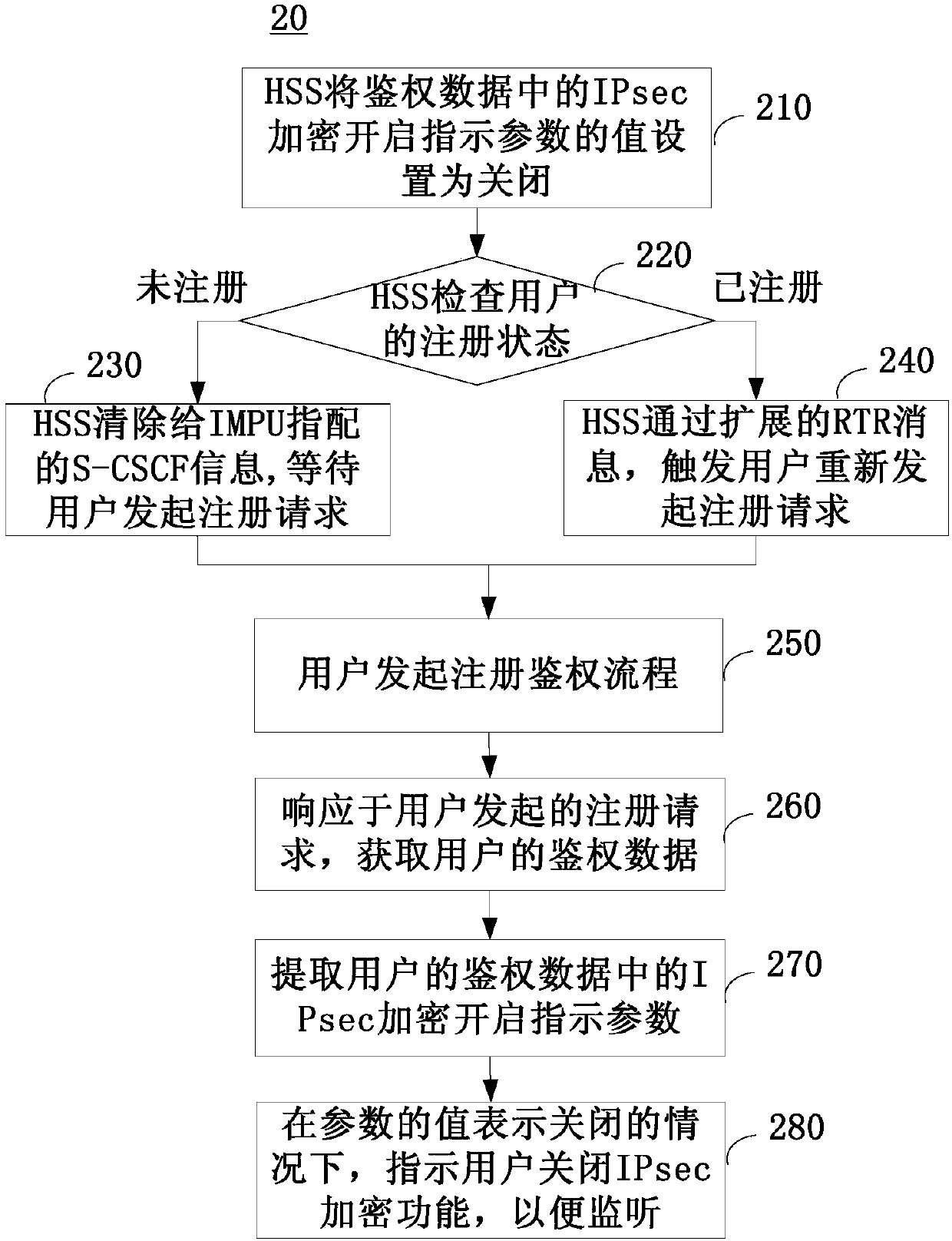
[0042] The following will clearly and completely describe the technical solutions in the embodiments of the present disclosure with reference to the drawings in the embodiments of the present disclosure.
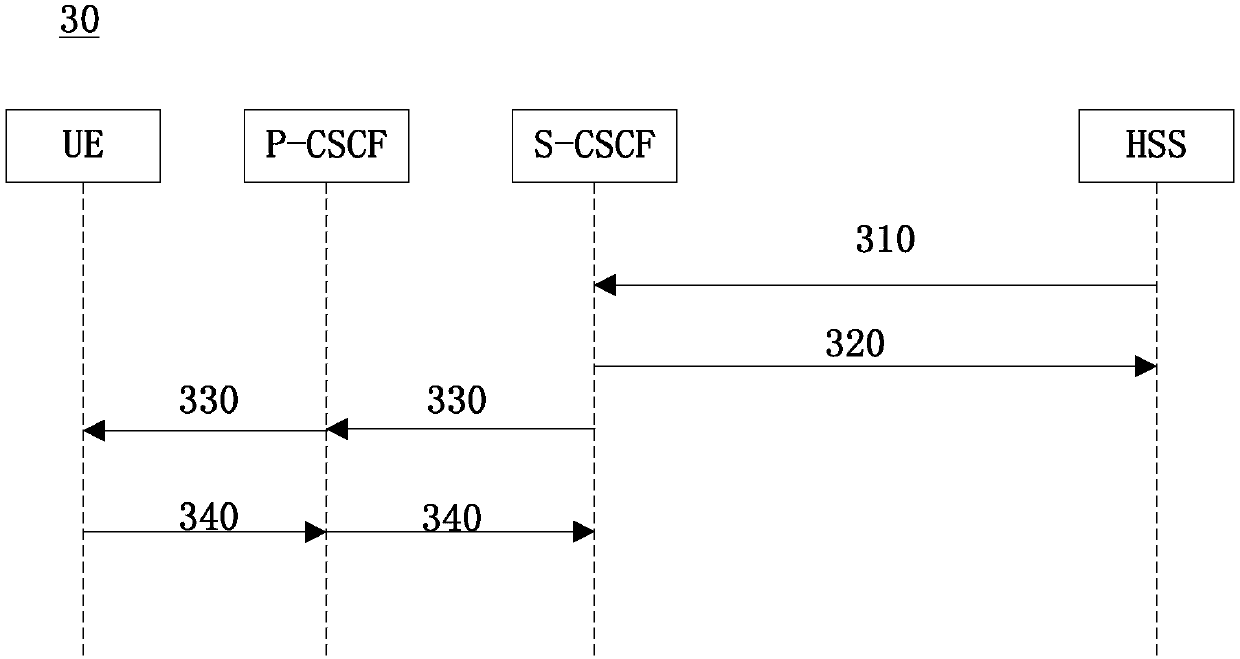
[0043] figure 1 It is a schematic flowchart of an embodiment of the security control method of the present disclosure. When the security control method in this embodiment is applied to an IMS system, the method may be executed by a Serving Call Session Control Function (S-CSCF, Serving CallSession Control Function).
[0044] Such as figure 1 As shown, the method 10 of this embodiment includes:
[0045] Step 110, in response to the registration request initiated by the user, obtain the user's authentication data, for example, obtain the user's authentication data from a Home Subscriber Server (HSS, Home Subscriber Server).
[0046] Step 120, extracting the IPsec encryption enable indication parameter in the user's authentication data.
[0047] Wherein, the value of the IP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com