A method, payment terminal and system for securely importing payment terminal keys
A payment terminal and key technology, applied in the field of information security, can solve problems such as potential security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
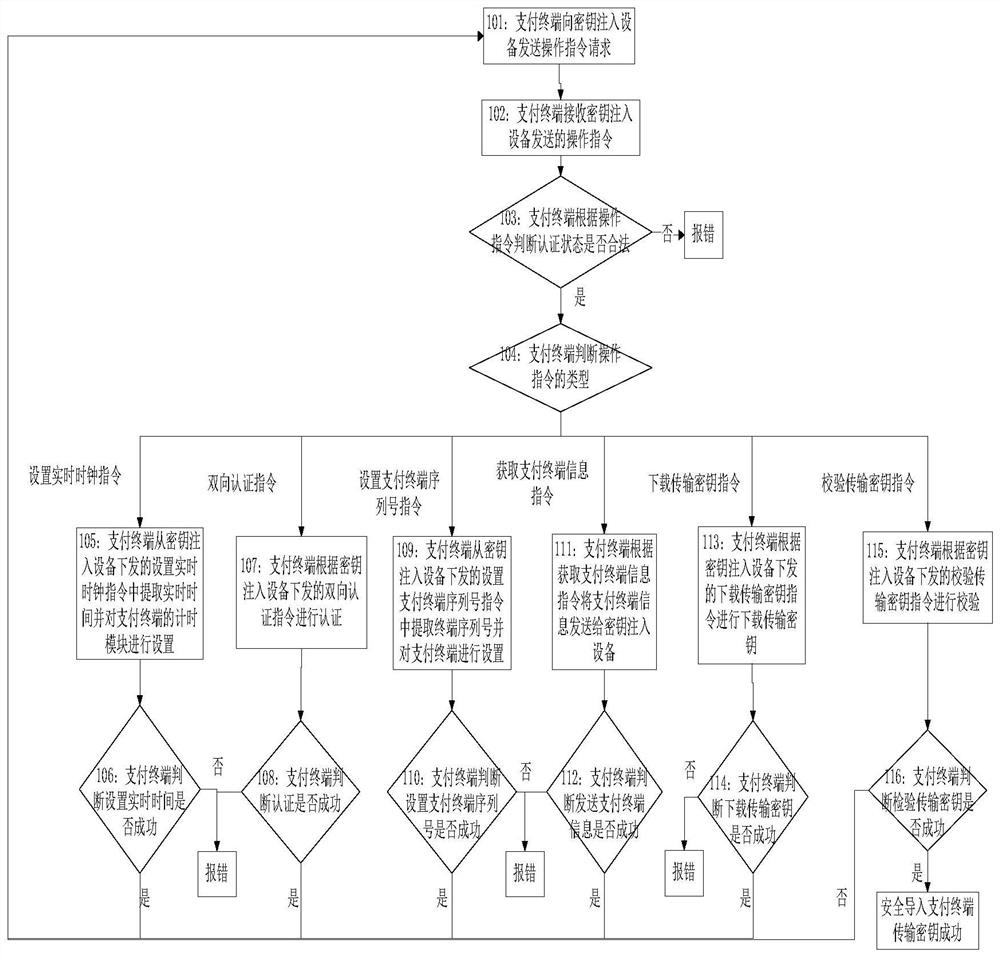
[0113] Embodiment 1 of the present invention provides a method for securely importing payment terminal keys, such as figure 1 shown, including:
[0114] Step 101: the payment terminal sends an operation instruction request to the key injection device;
[0115] Step 102: the payment terminal receives the operation instruction sent by the key injection device;
[0116] Specifically, the operation instructions include an instruction for setting a real-time clock, an instruction for two-way authentication, an instruction for obtaining payment terminal information, an instruction for setting a serial number of a payment terminal, an instruction for downloading and transmitting a key, and an instruction for verifying a transmission key;
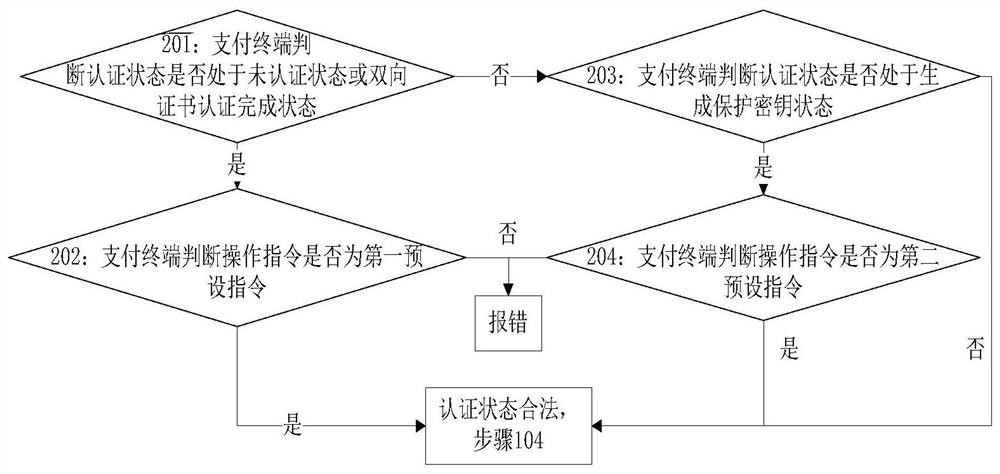
[0117] Step 103: The payment terminal judges whether the authentication status is legal according to the operation instruction, if yes, execute step 104, otherwise report an error;
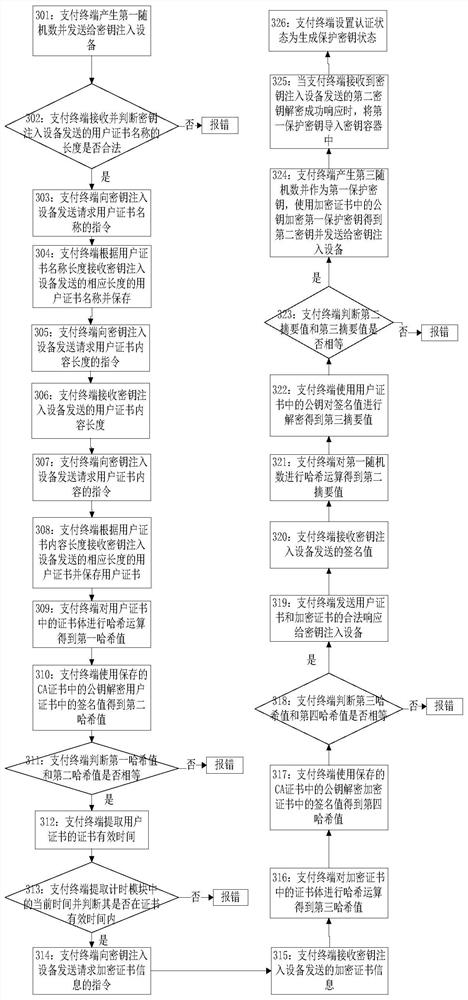
[0118] In this embodiment, the implementation process of step 1...
Embodiment 2
[0272] Embodiment 2 of the present invention provides a method for securely importing payment terminal keys, such as Figure 9 shown, including:
[0273] Step 901: the payment terminal sends an operation instruction request to the key injection device;
[0274] Step 902: The key injection device receives the operation instruction request sent by the payment terminal, and sends the operation instruction to the payment terminal;
[0275] Specifically, the operation instructions include an instruction for setting a real-time clock, an instruction for two-way authentication, an instruction for obtaining payment terminal information, an instruction for setting a serial number of a payment terminal, an instruction for downloading and transmitting a key, and an instruction for verifying a transmission key;
[0276] Step 903: The payment terminal receives the operation instruction sent by the key injection device, and judges whether the authentication status is legal according to the...
Embodiment 3
[0447] Embodiment 3 of the present invention provides a payment terminal for securely importing payment terminal keys, such as Figure 18 shown, including:
[0448] The first sending module 11 is configured to send an operation instruction request to the key injection device;
[0449] The first receiving module 12 is configured to receive the operation instruction sent by the key injection device;
[0450] The first judging module 13 is used to judge whether the authentication state is legal according to the operation instruction received by the first receiving module 12, if it is legal, then trigger the second judging module 14, otherwise trigger the first error reporting module 15;
[0451] The second judging module 14 is used to judge the type of the operation instruction received by the first receiving module 12, such as triggering the first generation sending module 16 for a two-way authentication instruction, triggering the second sending module 20 for downloading and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com