Method for identifying suspicious attack codes based on sandbox dynamic behaviors
A sandbox and behavioral technology, applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., can solve problems such as the inability to detect unknown virus intrusions, and achieve the effect of improving sensitivity and reducing harm.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] With reference to accompanying drawing, further illustrate the present invention:
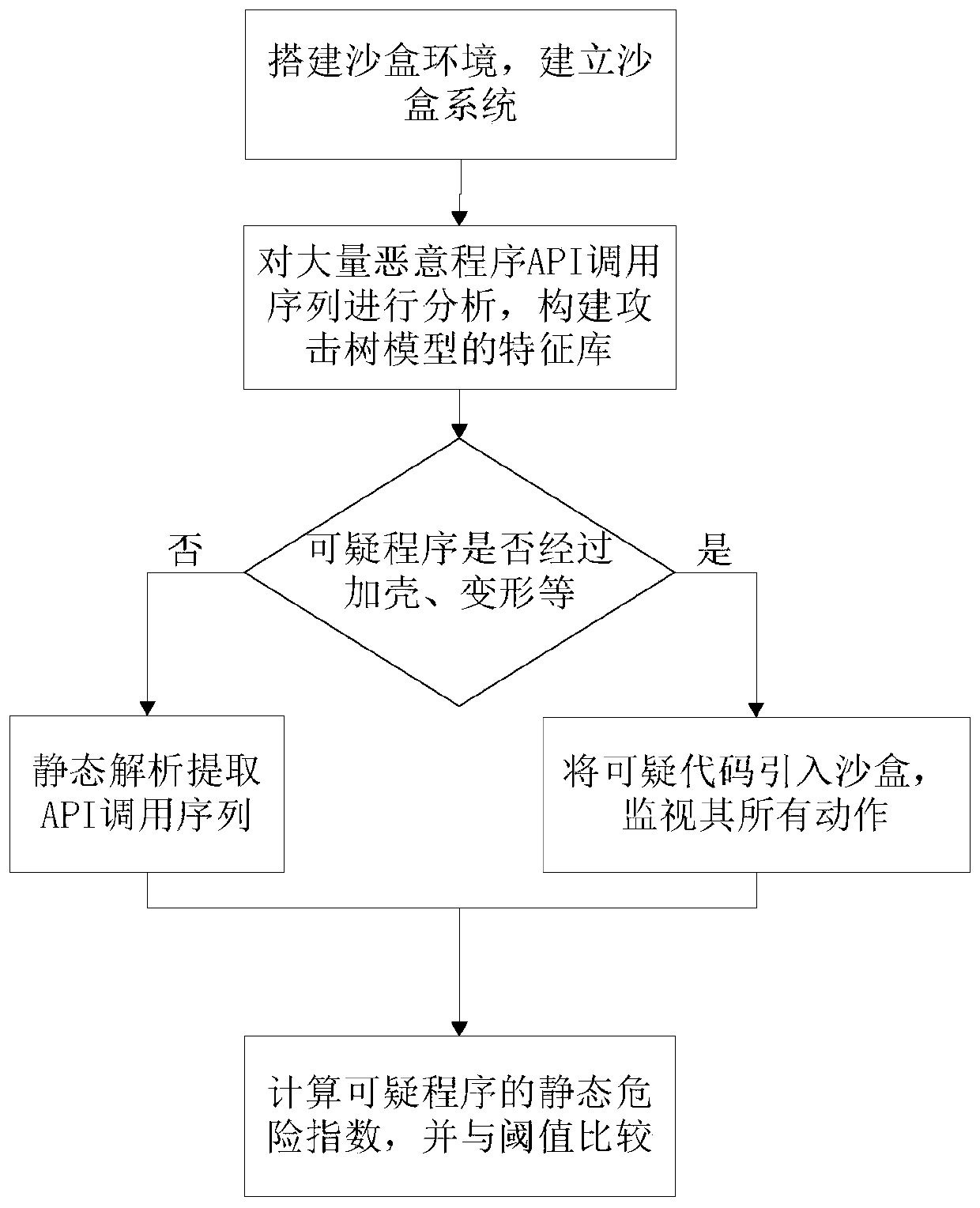
[0021] A method for identifying suspicious attack code based on sandbox dynamic behavior, comprising the following steps:
[0022] 1) Establish a sandbox. The sandbox system includes a sandbox system, a behavior acquisition system, a behavior analysis system, and a system interface.
[0023] 2) The construction of the attack tree model, analyzing a large number of malicious code behaviors, and constructing the feature library of the attack tree model according to the most commonly used API sequences of malicious code.
[0024] 3) Determine whether the PE file of the suspicious program has been packed, deformed, etc. If so, it can be introduced into the sandbox, and if not, the PE file can be statically analyzed to extract the API call sequence.
[0025] 4) Introduce codes with packing and deformed suspicious attack behaviors into the sandbox, simulate the execution of applications and s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com