A method based on probe technology to realize threat detection of IoT terminals
An Internet of Things terminal and threat detection technology, which is applied in the field of Internet of Things terminal threat detection based on probe technology, can solve the problems of difficult security threats, poor compatibility, and inability to differentiate, and achieve automatic discovery and management, and dynamic defense methods Effect
Active Publication Date: 2021-04-06
SICHUAN CHANGHONG ELECTRIC CO LTD
View PDF11 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0005] The asset device agent solution, which installs the agent program on the asset device, requires the asset device to have certain computing power, has problems such as poor compatibility, and difficulty in finding security threats when deployed separately, and this solution cannot be differentiated when the agent policy is issued
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment 1
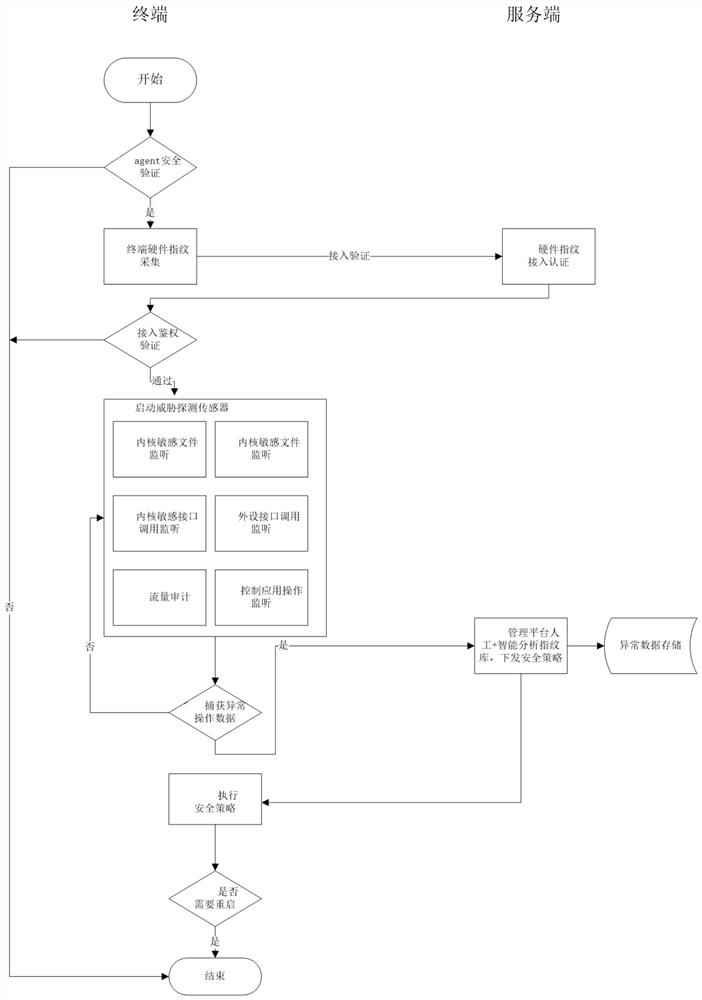
[0033] Such as figure 1 As shown, a method based on the probe technology to realize the threat detection of the Internet of Things terminal includes the following steps:
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a method for realizing threat detection of Internet of Things terminals based on probe technology, which includes firstly collecting and synthesizing terminal hardware fingerprints; then authenticating and accessing terminal hardware fingerprints; and then collecting terminal information, and by The management platform analyzes the terminal's own security issues, and finally the management platform issues a security warning, and the terminal executes the corresponding security policy. The method of the present invention can simultaneously solve the security problems of the device terminal itself, the security problem of the terminal cloud interaction, and the security problem of the cloud itself in the Internet of Things, and the present invention can support a variety of special protocols for the Internet of Things, and can realize automatic discovery and management of Internet of Things assets. And provide timely and dynamic defense methods.
Description
technical field [0001] The invention relates to the technical field of Internet of Things security, in particular to a method for realizing threat detection of Internet of Things terminals based on probe technology. Background technique [0002] The advent of the Internet of Things era is beyond doubt, and various types of Internet of Things smart terminals are emerging and widely used in various fields of people's work and life. According to a survey report released by Gartner, the number of IoT devices in the world was about 8.4 billion in 2017, and the number of IoT devices may exceed 20 billion by 2020. It can be seen that the future development space of the Internet of Things market is extremely huge. As the key infrastructure of the entire IoT system architecture, the IoT smart terminal is a key node connecting the real world and the digital world, so the importance of IoT terminal security is self-evident. [0003] At present, in the Internet of Things environment, ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L29/06H04L29/08
CPCH04L63/0876H04L63/20H04L63/10H04L63/1425H04L63/1416H04L67/12H04L67/56
Inventor 何斌肖建文有庆
Owner SICHUAN CHANGHONG ELECTRIC CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com