Policy control method, equipment and system
A technology of policy control and policy billing control, which is applied in the communication field and can solve problems such as usage monitoring of instances that do not support usage monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 2
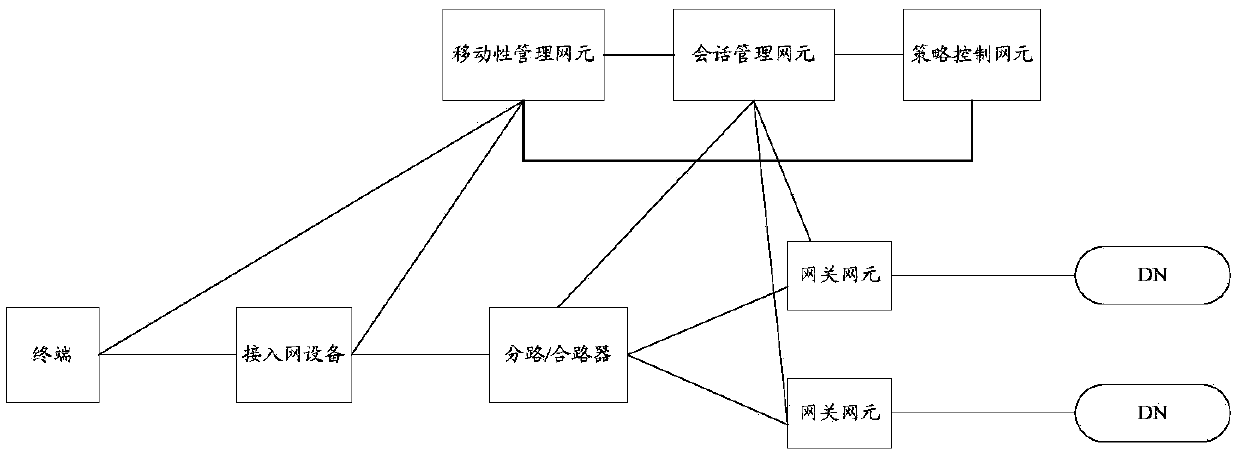
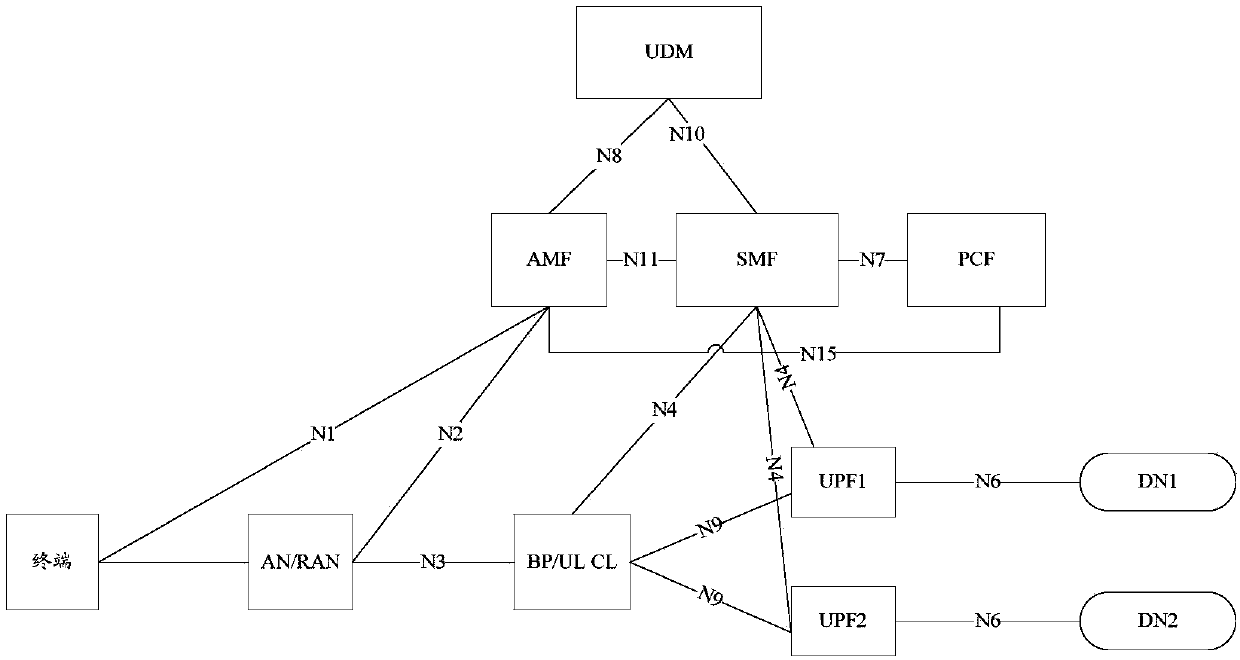
[0172] Wherein, PCC rule 1 includes monitoring key1, and PCC rule 2 includes monitoring key2. Neither PCC rule 1 nor PCC rule 2 sets an instruction to exclude the usage detected by the PCC rule from the session-level usage, that is, the PCF decides that the usage of PCC rule 1 and PCC rule 2 must be accumulated in the session-level usage monitoring. Usage monitoring information 1 is for application monitoring instance 1, including [monitoring key1, PCC rule indication, usage threshold threshold1]. Usage monitoring information 2 corresponds to application monitoring instance 2, including [monitoring key2, session level indication, usage threshold threshold2]. Wherein, the PCC rule indication may be a service data flow level indication, which is used to indicate that monitoring key1 corresponds to a service data flow level usage monitoring instance.
[0173] Wherein, the instruction to execute PCC rule 3 and PCC rule 4 on UPF2 may be the identifier of UPF1, and the instruction ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com