Malware opcode analysis method based on convolutional neural network
A convolutional neural network and malware technology, applied in the field of malware detection, can solve problems such as low classification success rate, insufficient accuracy, and incomplete extraction of opcode sequences, so as to reduce overfitting problems and achieve good evaluation Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
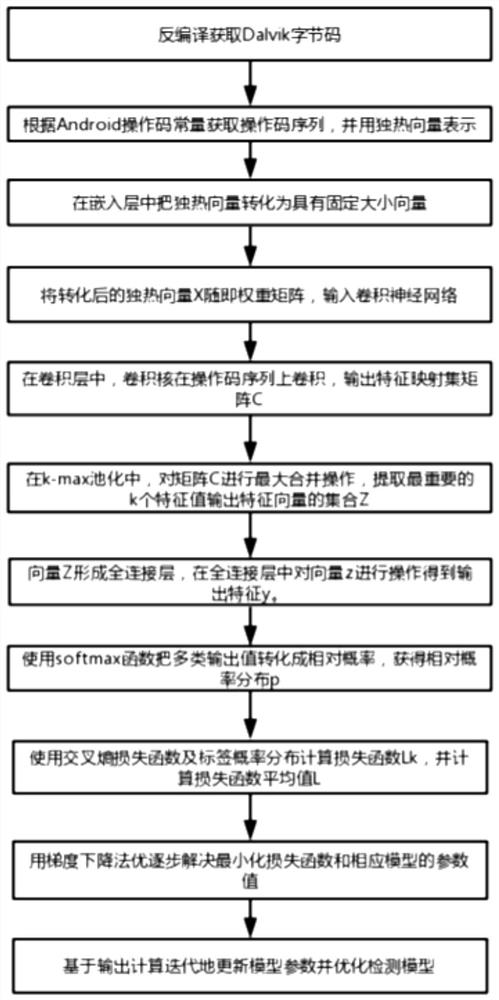
[0029] Such as figure 1 As shown, the present invention discloses a method for analyzing malware opcodes based on convolutional neural networks, comprising the following steps:
[0030] S1. Obtain a training sample; the training sample is an execution program of a known type of software, and the type includes benign and malicious;
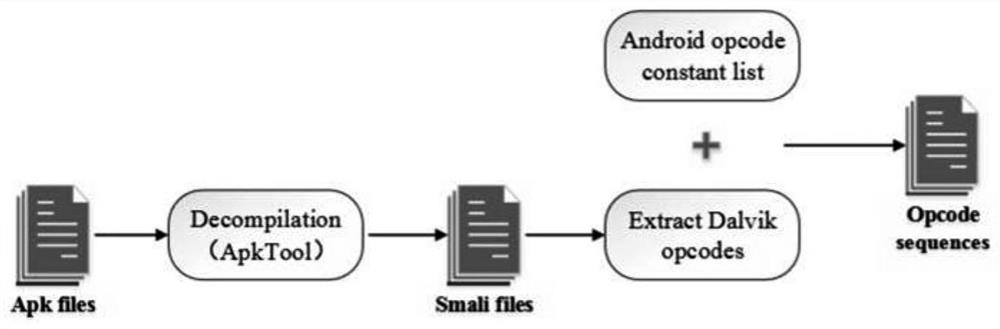
[0031] S2. Use apktool to decompile the training sample, obtain the smali file of the training sample, and obtain the Dalvik bytecode from the smali file, and discard the operand; the apk preprocessing process is as follows figure 2 shown.
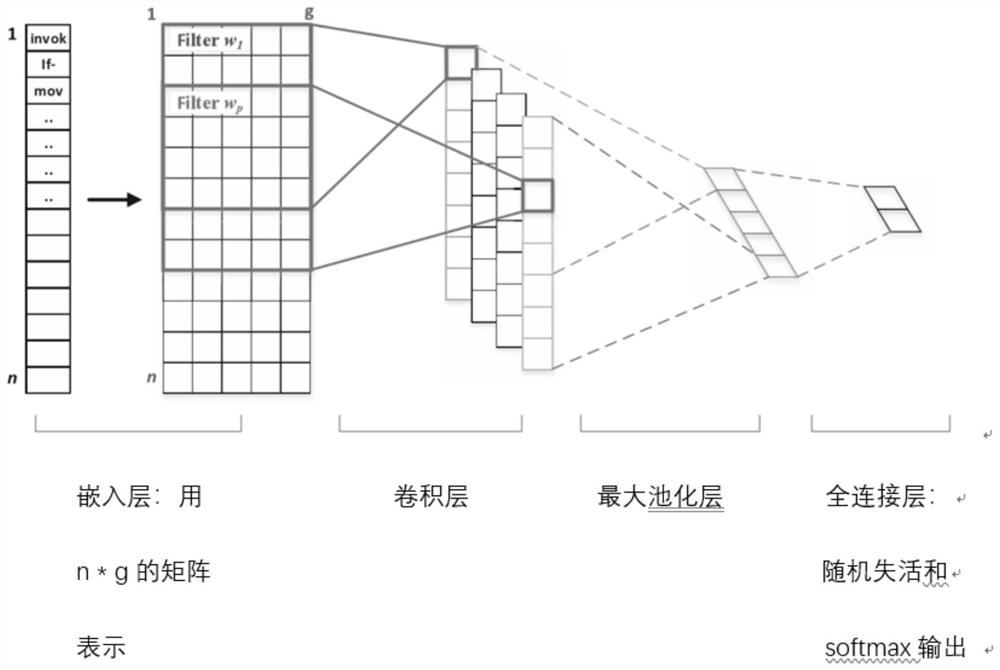
[0032] S3. Obtain the opcode sequence file according to the Android opcode constant list, the opcode sequence vector is represented by X={X1, X2, ..., Xn}, where n is the opcode length of the apk, and n * o (o= 256) One-hot vector representation;
[0033] S4. In t...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap