Method and device for device identity authentication in machine-to-machine environment
A technology of device identity and machine environment, applied in the field of information security, to achieve good application prospects, ensure anti-attack, and improve the effect of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
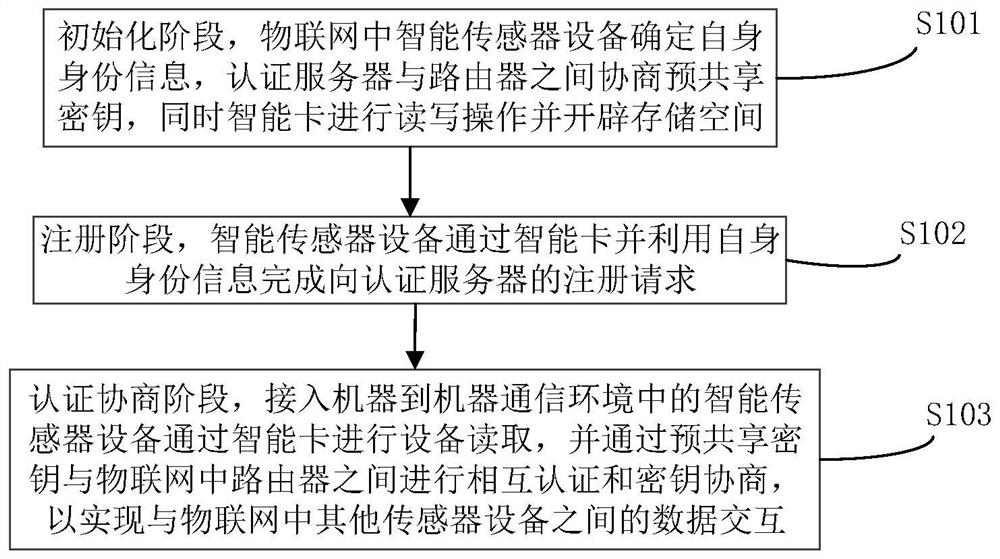
[0028] For the situation that traditional identity authentication and key agreement protocols are not suitable for the Internet of Things environment, and traditional encryption methods and protocols are subject to specific constraints in the environment of the perception layer, the embodiments of the present invention, see figure 1 As shown, a method for device identity authentication in a machine-to-machine environment is provided, including the following content:
[0029] S101) In the initialization stage, the smart sensor device in the Internet of Things determines its own identity information, the authentication server and the router negotiate a pre-shared key, and at the same time, the smart card performs read an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com