Internet of things security authentication method, system and terminal based on national secret algorithm
A technology of Internet of Things terminal and national secret algorithm, applied in the field of system and terminal, Internet of Things security authentication method based on national secret algorithm, can solve the problems of long time-consuming encryption and decryption, poor algorithm implementation efficiency, insecurity, etc., to ensure data security The effect of safety, safety enhancement, and reliability assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] Embodiment 1, the present disclosure provides a security authentication method for the Internet of Things based on a national secret algorithm;
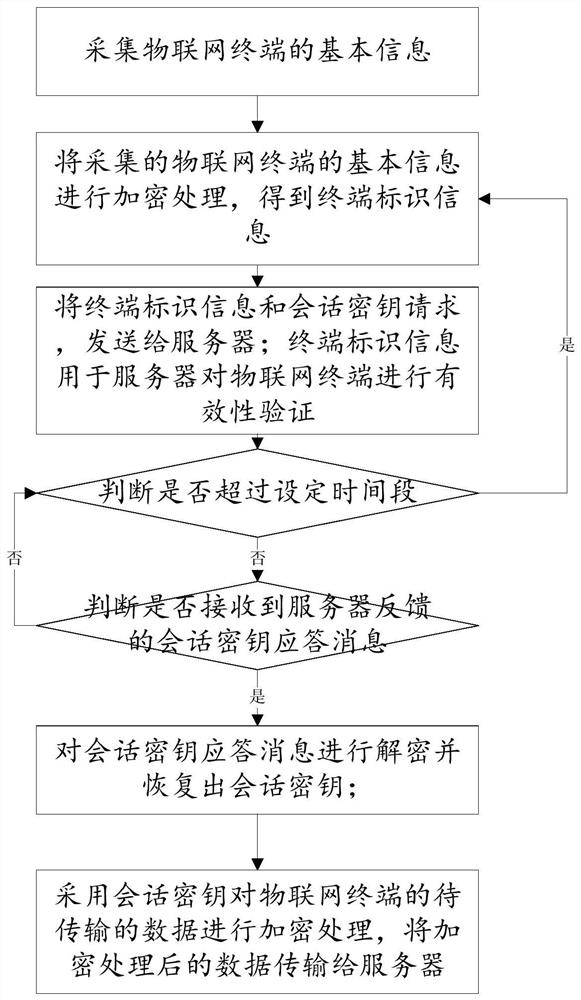
[0053] Such as figure 1 As shown, the security authentication method of the Internet of Things based on the national secret algorithm is applied to the terminal of the Internet of Things, including:
[0054] Sa1: Collect basic information of IoT terminals;
[0055] Sa2: terminal identification information preparation step: encrypt the collected basic information of the IoT terminal to obtain the terminal identification information;
[0056] Sa3: Send the terminal identification information and session key request to the server; the terminal identification information is used by the server to verify the validity of the IoT terminal;
[0057] Sa4: timeout judging step: judging whether the set time period is exceeded, if so, return to the terminal identification information preparation step; if not overtime, continue judging wh...
Embodiment 2
[0127] Embodiment 2, the present disclosure also provides a security authentication method for the Internet of Things based on a national secret algorithm;
[0128] The IoT security authentication method based on the national secret algorithm is applied to the server, including:
[0129] Sb1: Obtain the terminal identification information and session key request sent by the terminal;
[0130] Sb2: Perform terminal validity verification according to the terminal identification information sent by the terminal;
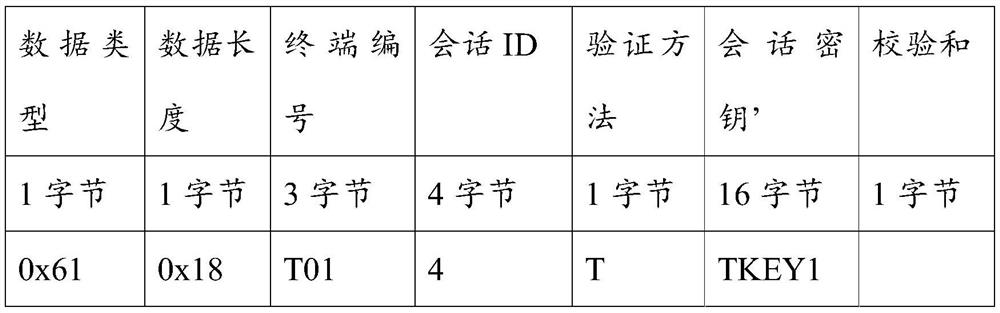
[0131] Sb3: Encrypt the session key request of the terminal whose validity has been verified, and obtain a session key response message;
[0132] Sb4: Feed back the session key response message to the terminal.
[0133] As one or more embodiments, in Sb2, terminal validity verification is performed according to the terminal identification information sent by the terminal; the specific steps include:
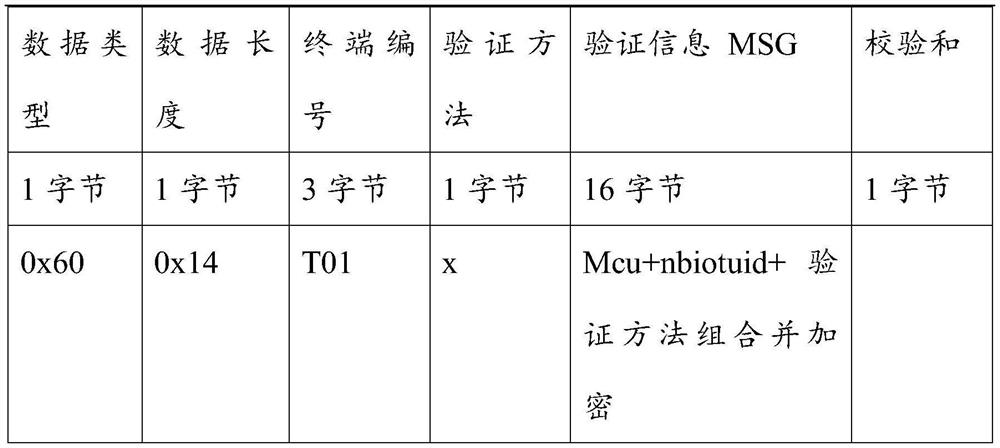
[0134] After the server receives the data packet sent by the termi...
Embodiment 3
[0155] Embodiment 3, the present disclosure also provides an Internet of Things security authentication terminal based on a national secret algorithm;
[0156] IoT security authentication terminal based on national secret algorithm, including:
[0157] The collection module is configured to: collect basic information of the Internet of Things terminal;
[0158] The terminal identification information preparation module is configured to: encrypt the collected basic information of the IoT terminal to obtain the terminal identification information;
[0159] The validity verification module is configured to: send the terminal identification information and the session key request to the server; the terminal identification information is used by the server to verify the validity of the IoT terminal;
[0160] The overtime judging module is configured to: judge whether the set time period is exceeded, and if so, return to the terminal identification information preparation step; if ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com