Controlling access to data
A technology of data and data identification, applied in digital data protection, data exchange network, electronic digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
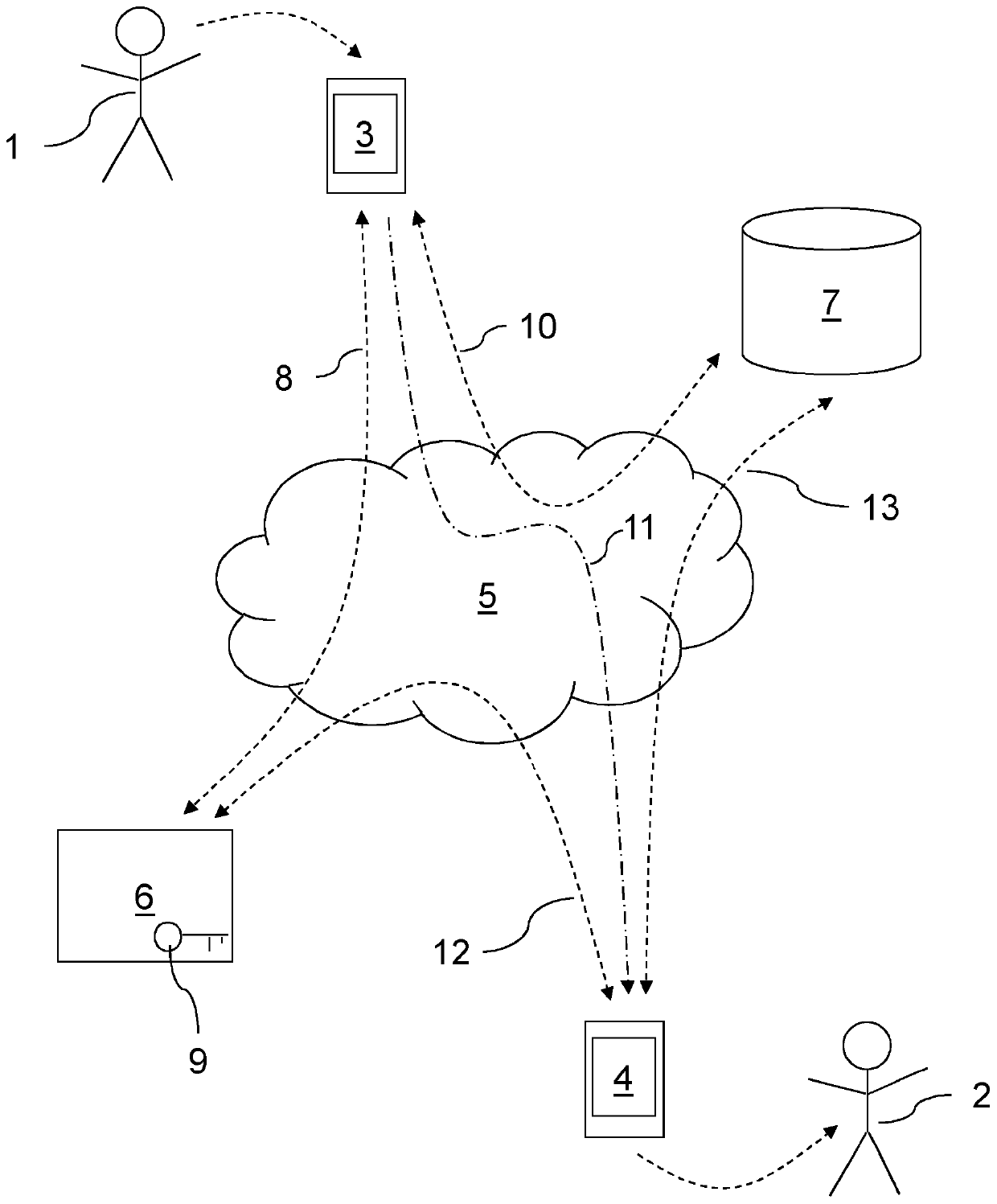
[0160] figure 1 A first human user 1 and a second human user 2 are shown. A first user 1 uses a first communication device 3 and a second user 2 uses a second communication device 4 . These devices 3 , 4 are communicatively linked via the Internet 5 . They can be mobile phones, laptops, personal computers or any other electronic communication devices.
[0161] The key server 6 and feature server 7 are also connected to the Internet 5 . Access to these servers 6, 7 may be restricted to authorized users.
[0162] In a specific example of use, a first user 1 is sending a confidential email to a second user 2 . The first user 1 enters an email into the first communication device 3 and identifies one or more intended recipients, thereby defining an access control list (ACL) of the names of those users who will be allowed to decrypt the email. In this example, the ACL only contains the second user2.
[0163] Subsequently, the first communication device 3 initiates a secure com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com