DNS hijacking detection method and device
A detection method and DNS service technology, applied in the field of network security, can solve problems such as high labor cost, low efficiency, and inconsistency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
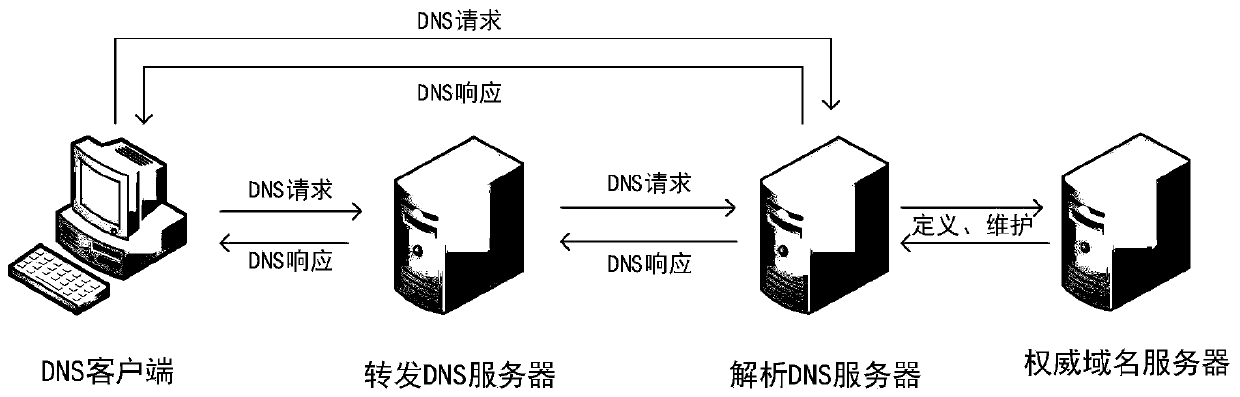
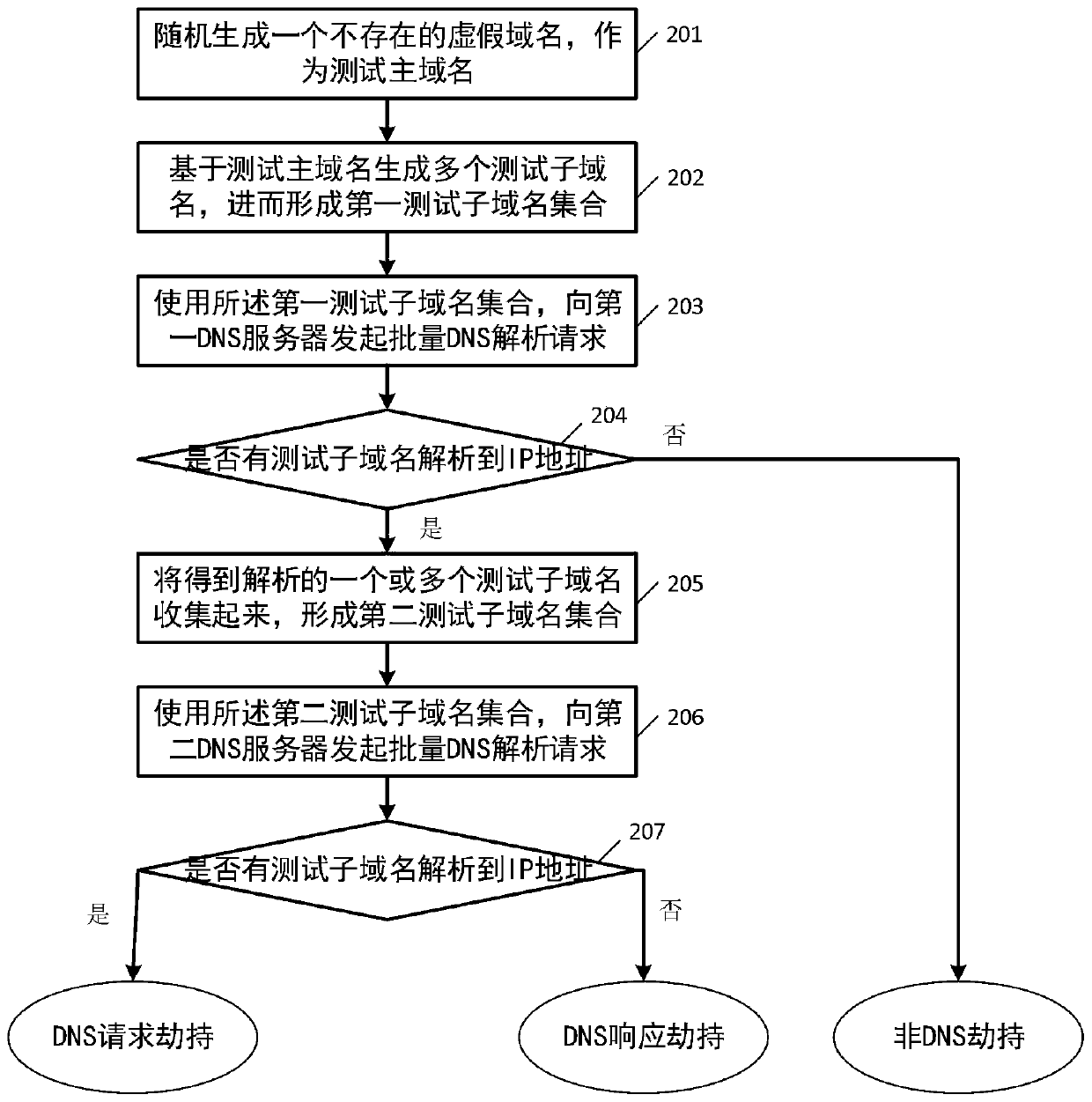
[0051] The embodiment of the present invention provides a DNS hijacking detection method, which is mainly aimed at the DNS hijacking of DNS packet modification type occurring in the network. Before the introduction of the detection method, the detection principle and detection idea of the detection method of the present invention will be introduced. Wherein, the detection method provided by the present invention is mainly based on the following detection principles:
[0052] During the entire process of DNS message transmission, if a DNS message is modified in a certain link, a false DNS resolution record will be obtained; for example, if the DNS request is to resolve the IP address of a domain name, a False IP address. The real DNS request process and the hijacked DNS request process are different in many aspects, the most important difference lies in the processing of fake domain names and fake DNS servers. If we request a domain name that does not exist, a normal non-hi...
Embodiment 2
[0099] On the basis of the DNS hijacking detection method provided in the above-mentioned embodiment 1, the present invention also provides a DNS hijacking detection device that can be used to implement the above method, such as Figure 7 Shown is a schematic diagram of the device architecture of the embodiment of the present invention. The device for detecting DNS hijacking in this embodiment includes one or more processors 21 and memory 22 . in, Figure 7 A processor 21 is taken as an example.
[0100] The processor 21 and the memory 22 may be connected via a bus or in other ways, Figure 7 Take connection via bus as an example.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com