Security policy matching method and device, network equipment and storage medium
A security policy and matching method technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of security policy not taking effect, security policy matching speed is slow, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
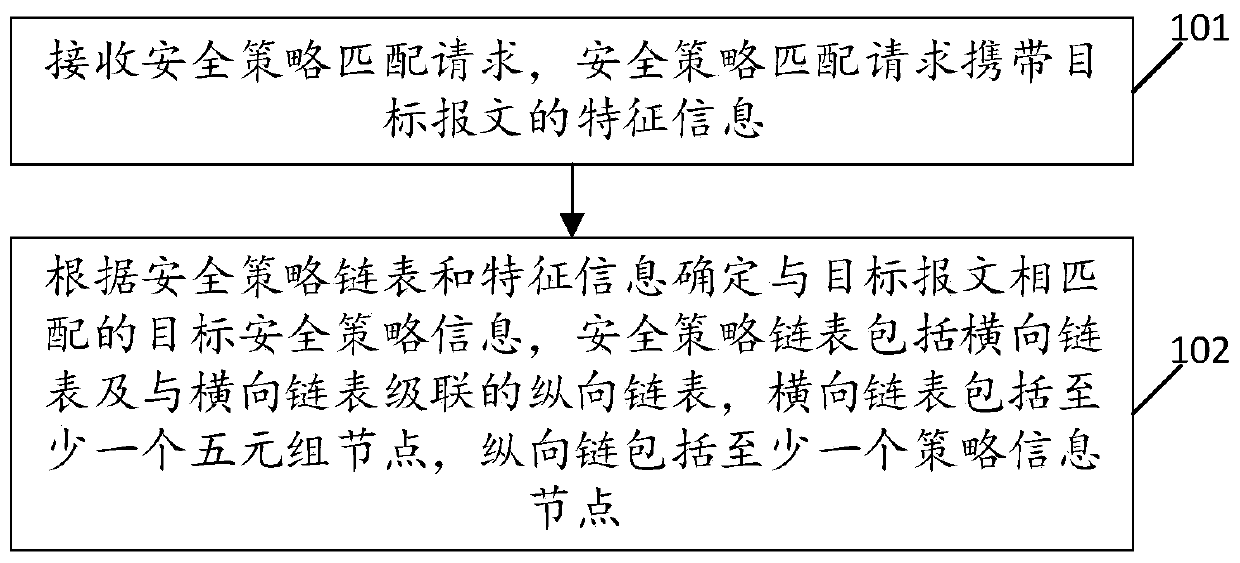
[0059] see figure 1 , figure 1 It is a schematic flowchart of a security policy matching method disclosed in the embodiment of this application. Such as figure 1 As shown, the method includes the steps of:
[0060] 101. Receive a security policy matching request, where the security policy matching request carries characteristic information of the target packet;
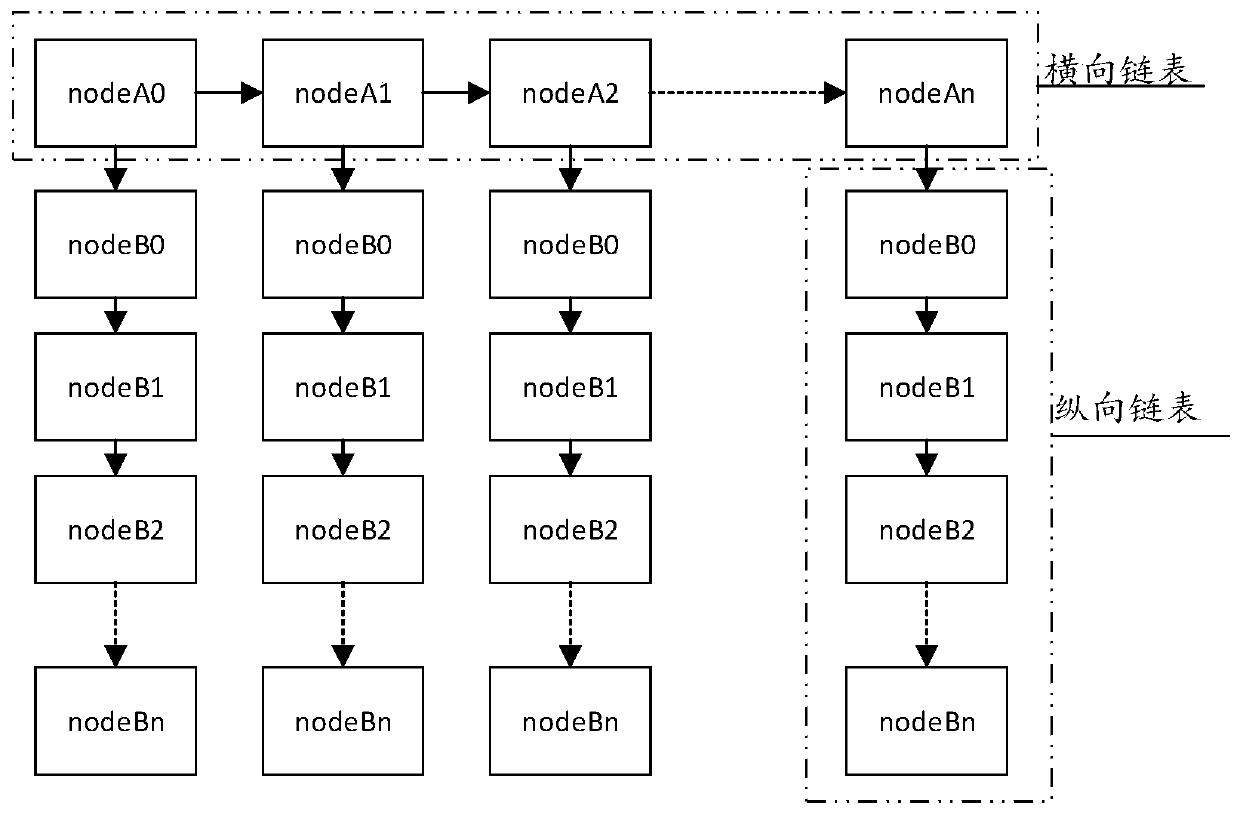
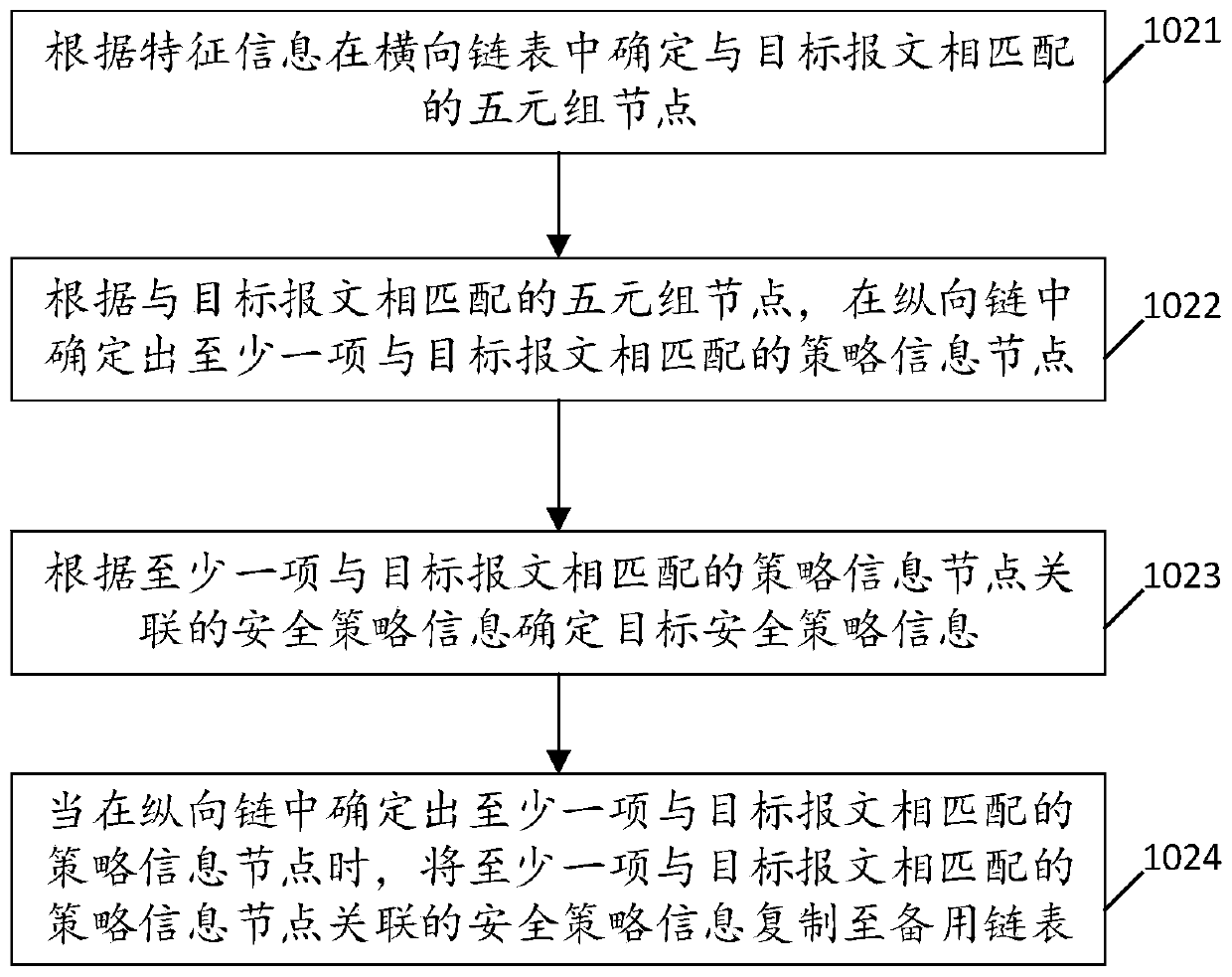
[0061] 102. Determine the target security policy information matching the target message according to the security policy linked list and feature information, the security policy linked list includes a horizontal linked list and a vertical linked list cascaded with the horizontal linked list, the horizontal linked list includes at least one quintuple node, and the vertical linked list Contains at least one policy information node.
[0062] In some optional implementation manners, the feature information includes source IP information of the target packet, source port information of the target packet, destination I...
Embodiment 2
[0089] see Figure 4 , Figure 4 It is a schematic flowchart of a security policy matching method disclosed in the embodiment of this application. Such as Figure 4 As shown, the method includes the steps of:
[0090] 201. Obtain a security policy configuration file, where the security policy configuration file includes at least one piece of quintuple configuration information and at least one piece of security policy configuration information associated with the quintuple configuration information;
[0091] 202. Construct a security policy linked list according to at least one quintuple configuration information and security policy configuration information;
[0092] 203. Receive a security policy matching request, where the security policy matching request carries characteristic information of the target packet;
[0093] 204. Determine the target security policy information matching the target message according to the security policy list and feature information. The sec...
Embodiment 3
[0105] see Image 6 , Image 6 It is a schematic structural diagram of a security policy matching device disclosed in the embodiment of this application. Such as Image 6 As shown, the device includes:
[0106] The receiving module 301 is configured to receive a security policy matching request, where the security policy matching request carries characteristic information of the target packet;
[0107] A determining module 302, configured to determine target security policy information matching the target message according to the security policy linked list and feature information, the security policy linked list includes a horizontal linked list and a vertical linked list cascaded with the horizontal linked list, and the horizontal linked list includes at least one quintuple node, the vertical chain includes at least one policy information node.
[0108] In some optional implementation manners, the feature information includes source IP information of the target packet, s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com