IP address analysis method and device for network attack and storage medium
A network attack and IP address technology, applied in the Internet field, can solve problems such as low computing speed, high computing cost, and large amount of computing, and achieve the effect of reducing computing time, reducing computing time, and reducing the number of clustered IPs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
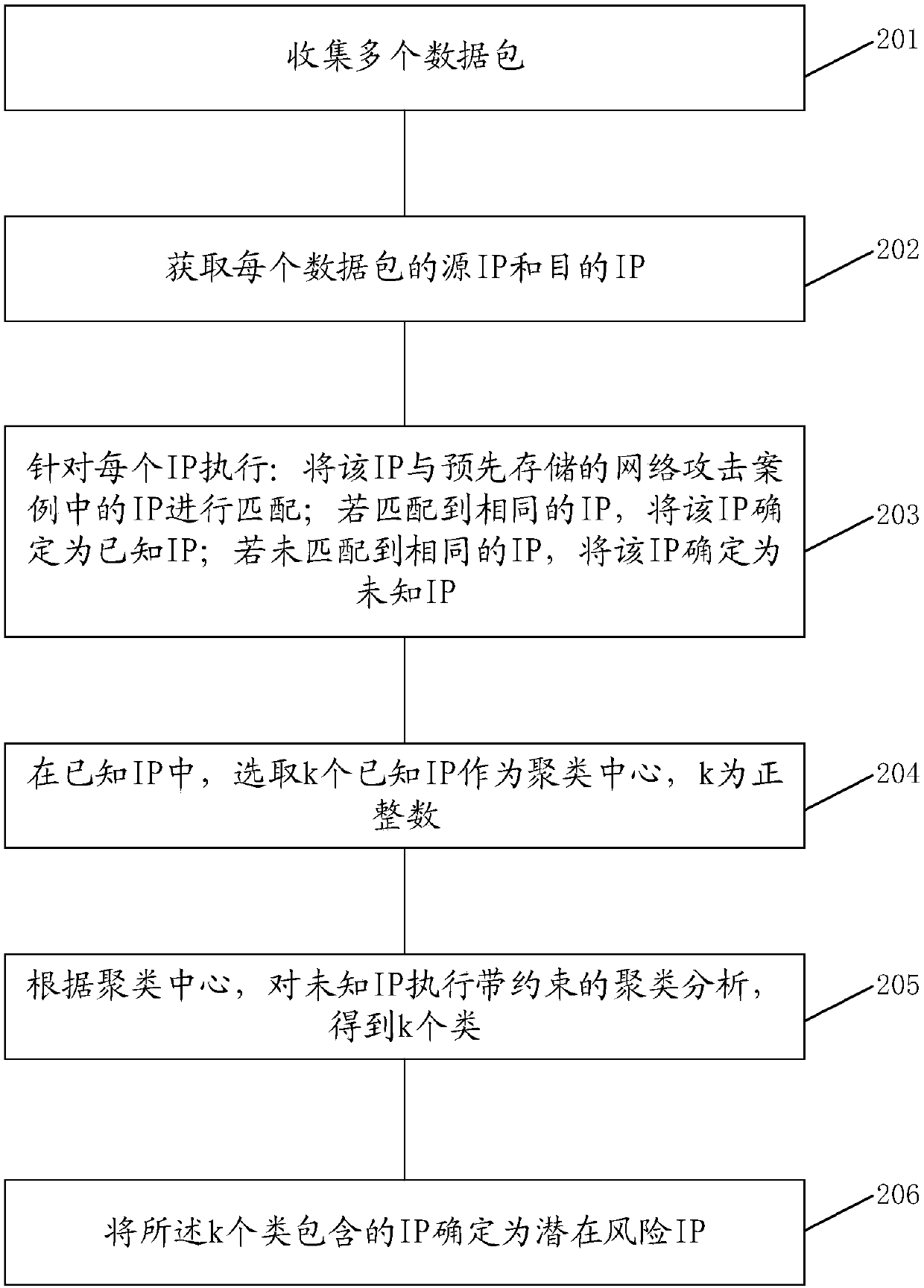
[0027] In order to cluster IPs more effectively and prepare for preventing network attacks, the embodiments of the present application provide an IP address analysis method, device and storage medium for network attacks. In order to better understand the solutions provided by the embodiments of this application, some nouns in the embodiments of this application are explained below:
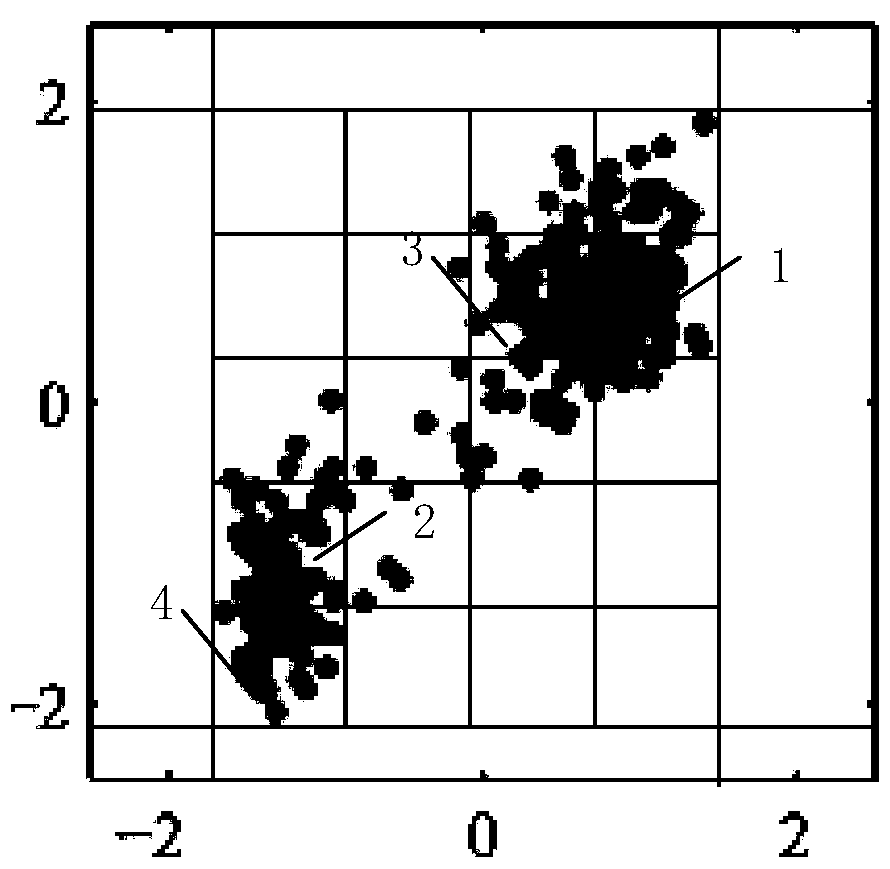
[0028] Clustering method with constraints: also known as conditional system clustering method, this method is based on the idea of system clustering, in the clustering process, clustering is carried out according to the conditions of clustering between classes, and those who do not meet the conditions are not allowed to gather together, specifically, Those who do not meet the criteria will not be placed in either category.
[0029] Next, the principle of the scheme provided by the embodiment of the present application is described:
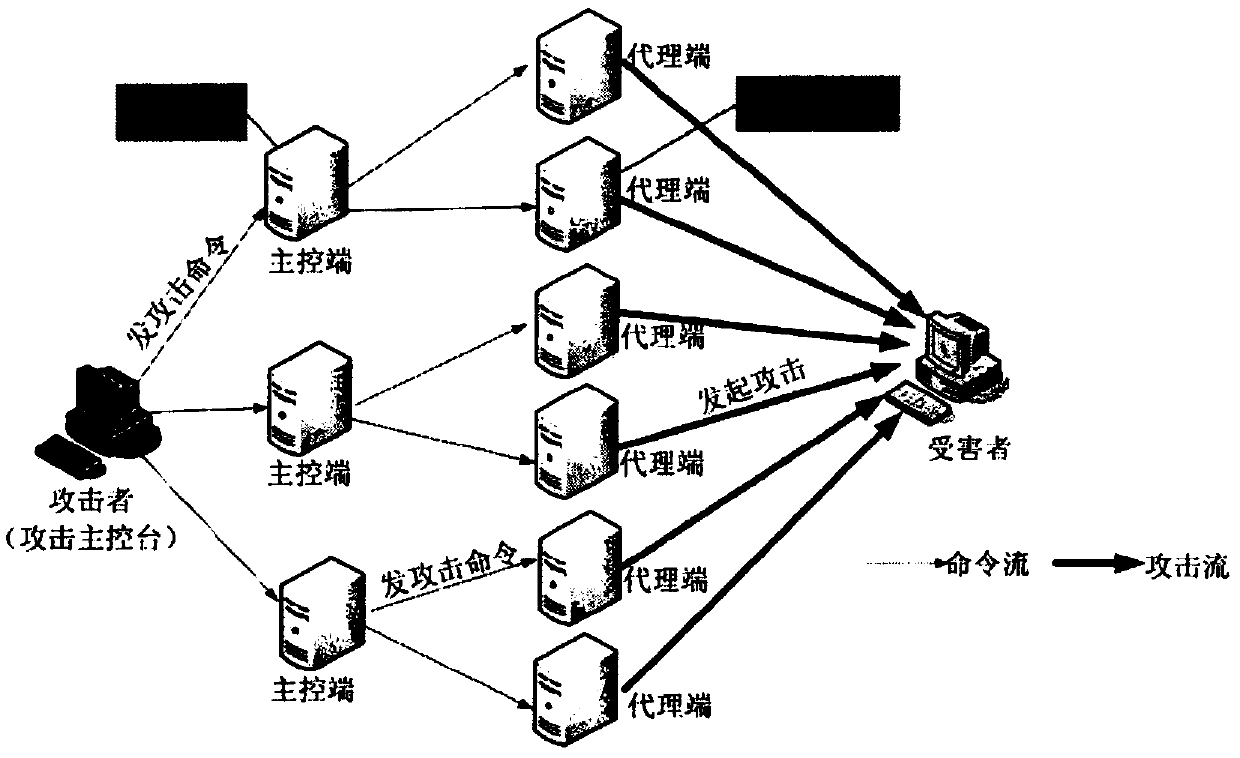
[0030] DDos attackers will use hundreds of thousands of agent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com