Applied authorization control method, device and electronic equipment
A technology of authorization control and application identification, which is applied in the field of communication and can solve problems such as complex processing methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
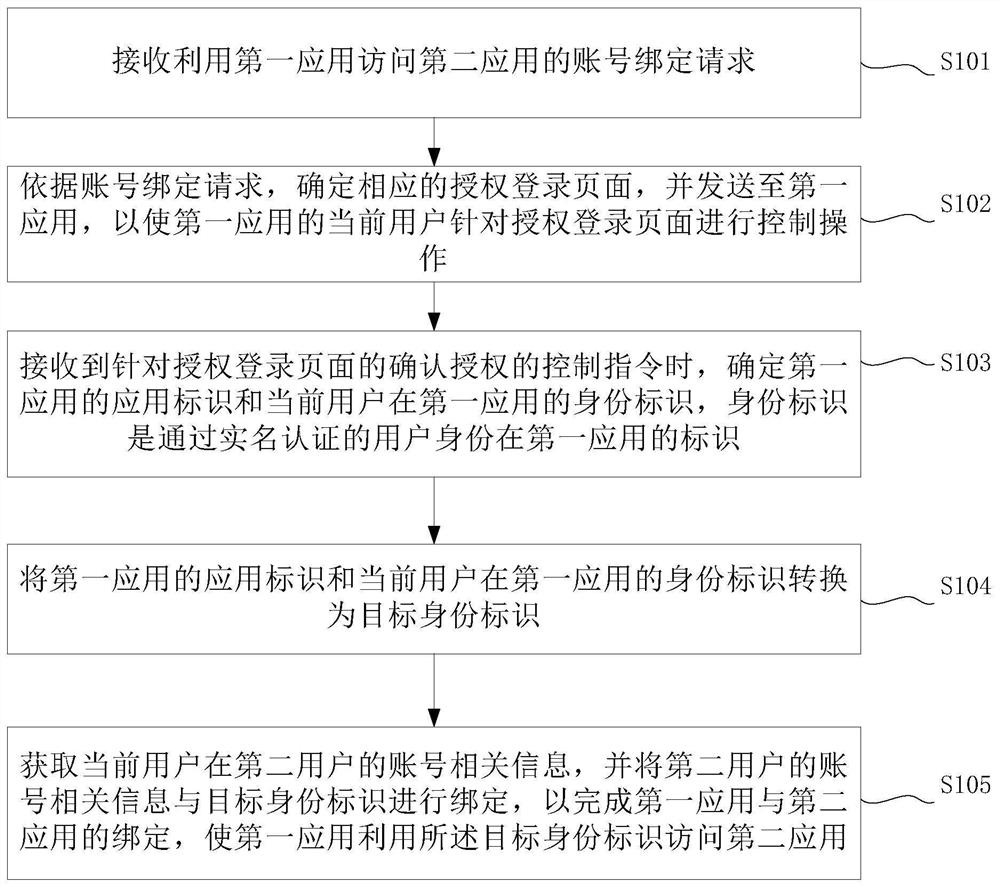
[0052] The embodiment of the present application provides an application authorization control method, such as figure 1 As shown, the method includes steps S101 to S105.
[0053] Step S101: Receive an account binding request for accessing a second application by using the first application.
[0054] In the embodiment of the present application, the identity authorization server receives the account binding request. Specifically, the account binding request may be directly sent by the first application to the identity authorization server, or may be sent by using a server corresponding to the first application. In practical application, the account binding request is generally sent by the server corresponding to the first application.
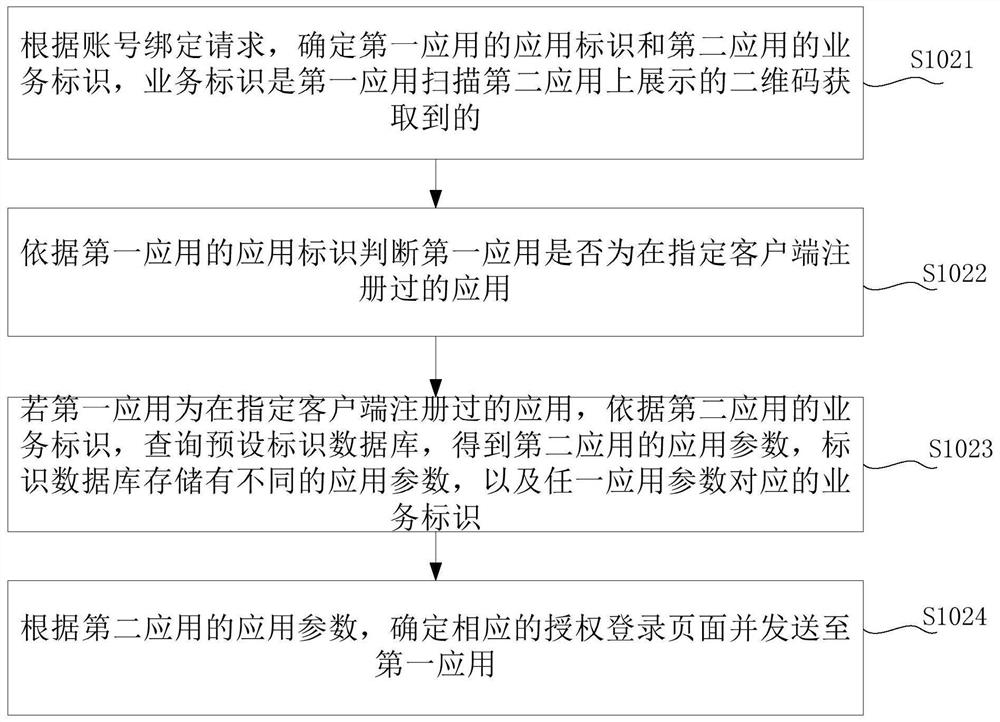
[0055] In this embodiment of the present application, the account binding request is used to determine the current application and the third-party application, that is, the current application is the first application, and the third-party appli...
Embodiment 2
[0089] The embodiment of the present application provides an application authorization control method, such as Image 6 As shown, the method includes: step S201, step S202 and step S203.
[0090] Step S201: Receive a target identity identifier of a first application, where the target identity identifier is an identifier for the first application to access the second application.
[0091] In this embodiment of the present application, the server corresponding to the second application receives the client identification of the first application, and the client identification of the first application is sent by the server corresponding to the first application. Specifically, the client identity of the first application is obtained by converting the identity authorization server according to the first identity of the first application in the first embodiment,
[0092] In practical application, the server corresponding to the first application generally sends the client identity i...
Embodiment 3
[0101] In order to further illustrate the authorization control method of the application provided by this application, such as Figure 7 As shown, the present application provides a system applying the application authorization control method provided by the present application. like Figure 7 As shown, the system includes a first application 100 , a first server 110 , a second application 200 , a second server 210 , a third application 300 and a third server 310 . Wherein, the first application and the second are both registered in the third application. The process of using the system is as follows:
[0102] (1) Start the second application, and click the preset control for the third application on the second application;
[0103] (2) the third application assigns the second parameter to the second application;
[0104] (3) The second application sends the second application parameter to the third server, so that the third server stores the second parameter and generate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com