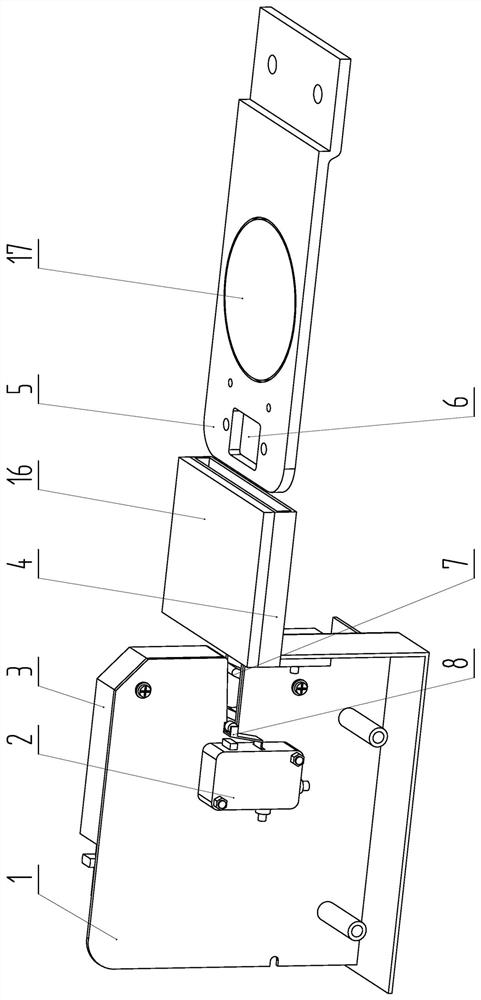
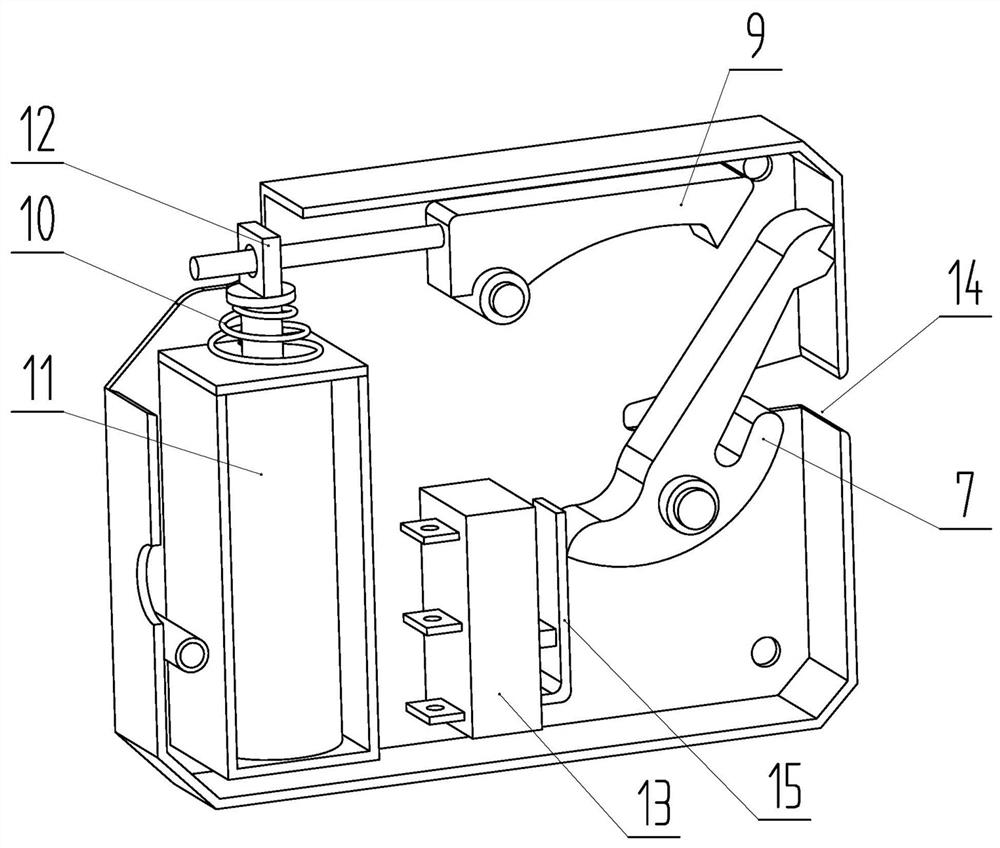
Shared equipment lock control device and control method of the device
A technology for sharing equipment and control methods, which is applied in the direction of locking portable objects, lock applications, coin-operated equipment with instrument control, etc., and can solve problems such as the transportation of accompanying beds
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] A control method comprising the following steps:
[0036] 1) When the IC card fixed on the lock tongue passes through the card reader, the card reader reads the identification information in the IC card and feeds back the read information to the controller;
[0037] 2) After receiving the identity information read in step 1), the controller compares it with the identity information stored in the controller, and sends a locking signal to the locking device after the comparison is successful;
[0038] 3) After the locking device receives the locking signal in step 2), if both the primary microswitch and the secondary microswitch are in the triggered state, the locking action will be performed to lock the lock tongue.
[0039] In the step 2), after the controller receives the identity information read by the card reader in the step 1), if it is inconsistent with the identity information stored by the controller, the controller always feeds back the unlocking instruction to...
Embodiment 2
[0041] A control method comprising the following steps:
[0042] 1) After the lock tongue triggers the micro-switch once, the micro-switch sends the trigger signal to the controller, and the controller sends the control command to the card reader after receiving the trigger signal, and the card reader is activated;
[0043] 2) The card reader activated in step 1) reads the IC card on the inserted latch, and feeds back the identity information in the read IC card to the controller;
[0044] 3) After the card reader reads the identity information of the IC card, the identity information is fed back to the controller;
[0045] 4) After the controller receives the identity information read from the card reader, it compares it with the identity information stored by itself, and sends a locking signal to the locking device after the comparison is consistent;
[0046] 5) After the locking device receives the locking signal, if the secondary micro-switch is in the triggered state, it...
Embodiment 3
[0048]A control method, wherein in step 4), after the controller receives the identity information read from the card reader, it compares it with the identity information stored by itself, and sends an unlock instruction to the locking device after the comparison is inconsistent; The locking device executes the unlocking action after receiving the unlocking instruction from the controller. In the step 5), after the secondary micro switch is in the triggered state and lasts for 1 s, the locking device executes the locking action; if the identity information fed back by the controller is inconsistent with the card reader, the second step in the step 5) After the micro switch is in the activated state and lasts for 1s, the locking device performs the locking action but the controller marks its state as unlocked; the locking device performs the locking action but the controller marks its state as unlocked If the secondary micro switch is in the triggered state again, the controlle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com