A proxy firewall protection method and system for smart contracts
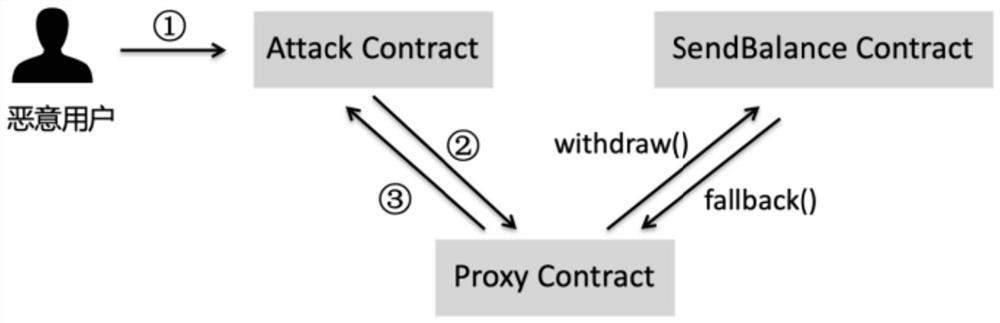
A smart contract and firewall technology, applied in transmission systems, digital transmission systems, data processing applications, etc., can solve problems such as inability to guarantee testability, inability to know, and inability to protect smart contracts, achieving efficient and timely access control, The effect of ensuring transaction security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0045]See Figure 1-3 。
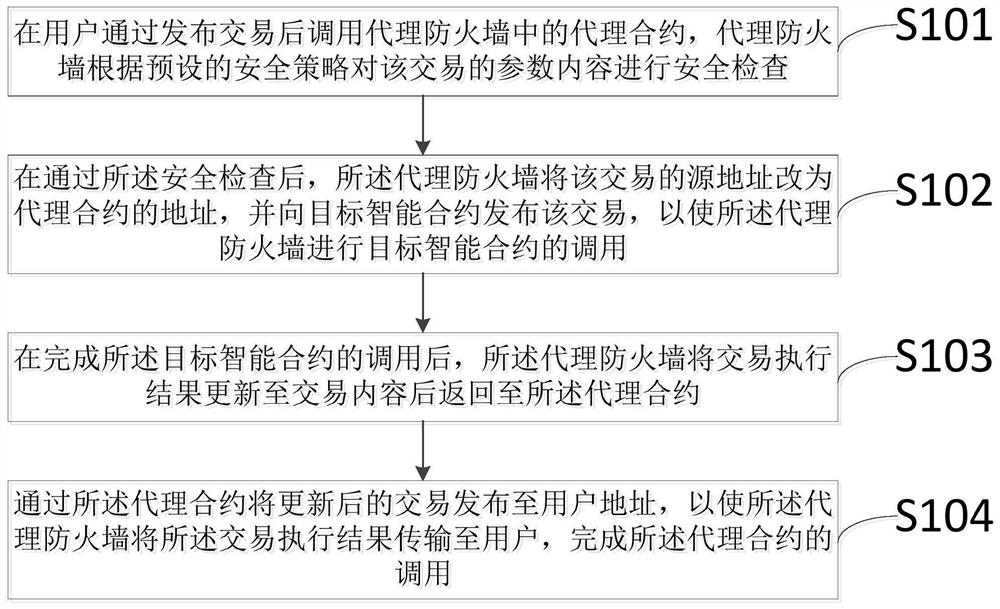
[0046] as Figure 1 As shown, the present embodiment provides a proxy firewall protection method for smart contracts, comprising at least the following steps:
[0047] S101. After the user publishes the transaction, the proxy contract in the proxy firewall is invoked, and the proxy firewall performs security checks the parameter content of the transaction according to the preset security policy;
[0048] Specifically, for step S101, the user publishes a transaction to invoke the proxy firewall contract, the proxy firewall checks the parameter content of the transaction according to the security policy, such as whether the sender address is in the blacklist of the protection policy library.
[0049] It should be noted that transactions are a data structure of the blockchain that mainly contains the following main fields: Type: type of transaction, ContractCreation (creating a contract) or MessageCall (calling a contract or transferring a transfer); Nonce: Th...
no. 2 example
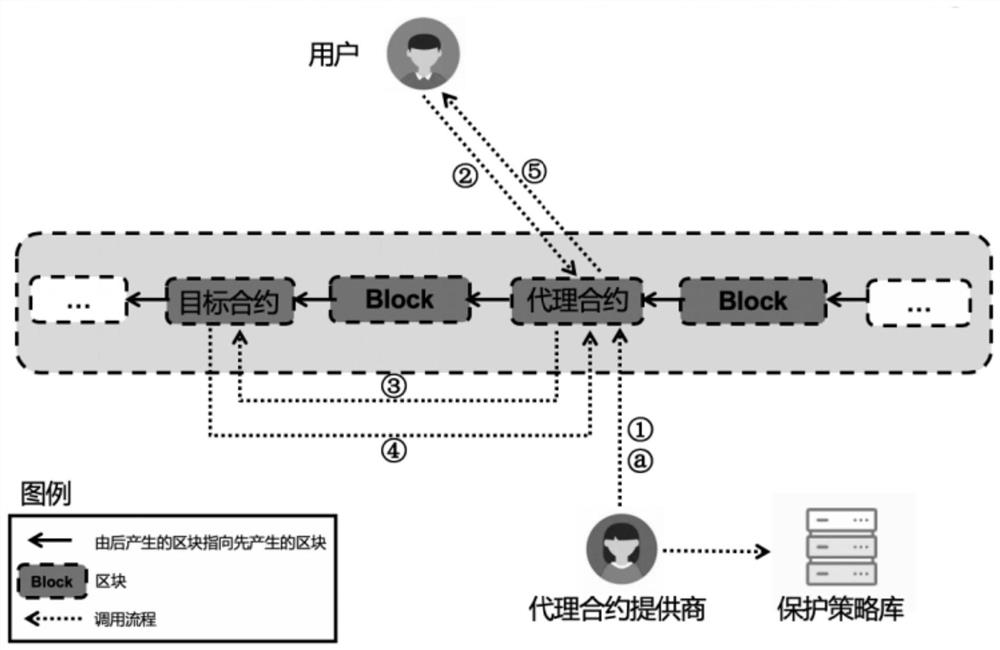
[0073] See Figure 4-5 。
[0074] as Figure 4 As shown in this embodiment, the present embodiment provides a proxy firewall protection system for smart contracts, comprising:
[0075] Transaction release module 100, for invoking the proxy contract in the proxy firewall after the user publishes the transaction, the proxy firewall performs security checks on the parameter content of the transaction according to the preset security policy;
[0076] Specifically, for the transaction publishing module 100, the user publishes a transaction to call the proxy firewall contract, the proxy firewall checks the parameter content of the transaction according to the security policy, such as whether the sender address is in the blacklist of the protection policy library.
[0077] Smart contract calling module 200, for passing the security check, the proxy firewall will change the source address of the transaction to the address of the proxy contract, and publish the transaction to the target smar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com