Method for safely using password in delegation mode
A password and security technology, applied in the field of password entrusted use, can solve problems such as inability to use and irreversible passwords, and achieve the effect of ensuring security and facilitating password management and use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
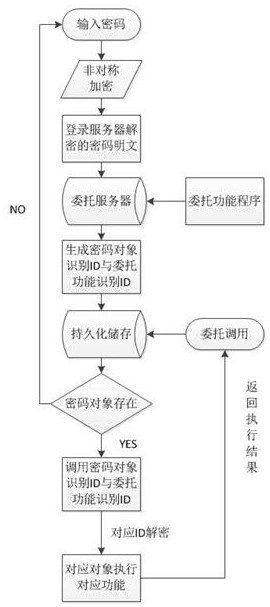
[0026] In one kind of embodiment of the present embodiment are delegated secure cryptographic methods, such as figure 1 As shown, including the following steps:
[0027] Step 1, a plurality of users to send encrypted password to the login server client, the password for the login server for different clients obtain a plurality of decrypted plain text passwords, login password for authentication plaintext;
[0028] Step 2, the login server to the plurality of passwords stored in plain text server commission, a server commission plaintext generation object identification ID unique passwords a password corresponding to the plaintext password for each of the current;
[0029] Step 3, adding a number of function programs to delegate trust server, the server generates a unique delegate delegate function delegate a function program ID identifying a current corresponding to a delegate for each function program;
[0030] Step 4, delegate the server returns a password object identification ...
Embodiment 2
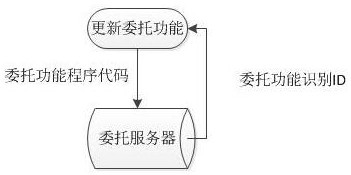
[0041] The present embodiment further optimization on the basis of the embodiment 1, such as figure 2As shown in the Step 2 and Step 3, the clear text password synchronization interact with the client by deploying a double function program in a single process or delegate server synchronous interaction with the clear text password delegate function program implemented by two servers delegate plaintext password safe storage and backup procedures and delegate functions.
[0042] Further, if only there is a delegate server, deploy a master trust in the process and a backup process server, to synchronize passwords in clear text to interact with the delegate functions of the program between the primary and the backup process through the process of load balancing.
[0043] Further, if the two servers trust exists, a delegate-based server deployment server, the deployment server and the other is standby server entrusted to constitute a HA cluster, the plain text password delegate function...
Embodiment 3
[0056] The present embodiment further optimized based on the above Example 1 or 2 on the proxy server is provided with a code that is loaded on an interface, the interface is loaded by loading the code plug implemented with the functions of the program delegate delegate function program to add a number of delegate server .
[0057] Further, the use of static or dynamically loaded loaded down with the insert delegate functions of the program loaded into the delegate server.
[0058] Dynamic loading:
[0059] Delegation is provided with HTTP server, and other dynamic RPC interfaces for dynamic loading plug, allowing the server password delegate delegate function provides a program interface code can be dynamically loaded, comply with the rules may be received through the interface code and the dynamic code is loaded into the server trust delegate functions among the collection procedures. Dynamic languages dynamically loaded widget
[0060] Received parameter is dynamic interface ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com