Joint training method and device for business models
A business model and training method technology, applied in the computer field, can solve problems such as inability to fully share data and data islands
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The schemes provided herein will be described below with reference to the drawings. The following describes the technical terms embodiment according to the present embodiment description.
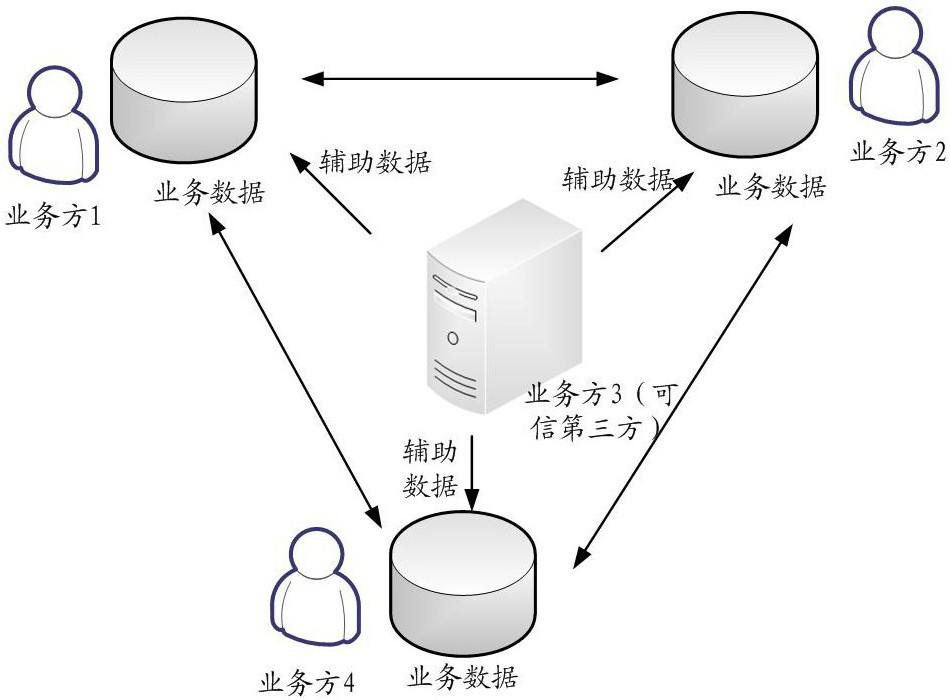
[0041] Multi-party Secure Computing (Secure Muti-Party Computation, MPC) is a secure algorithms to protect data privacy. Secure Computing enables multi-party participation in multiple data calculated collaborate calculated without leakage own data.
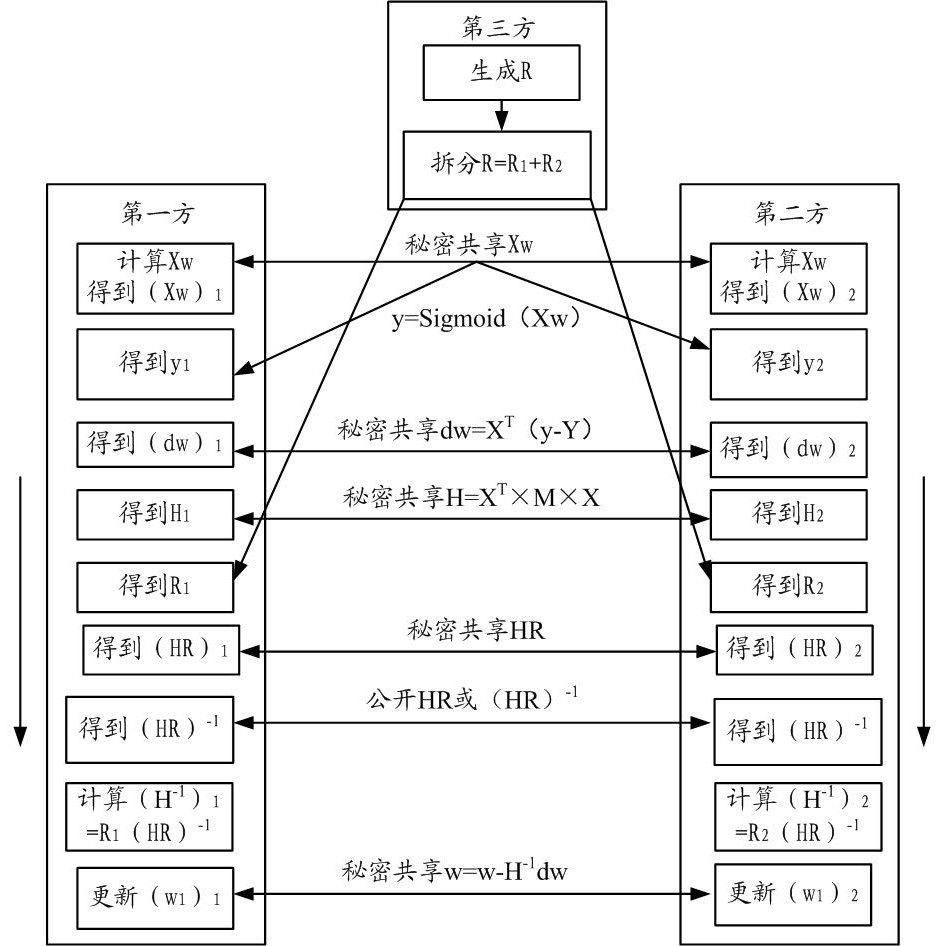
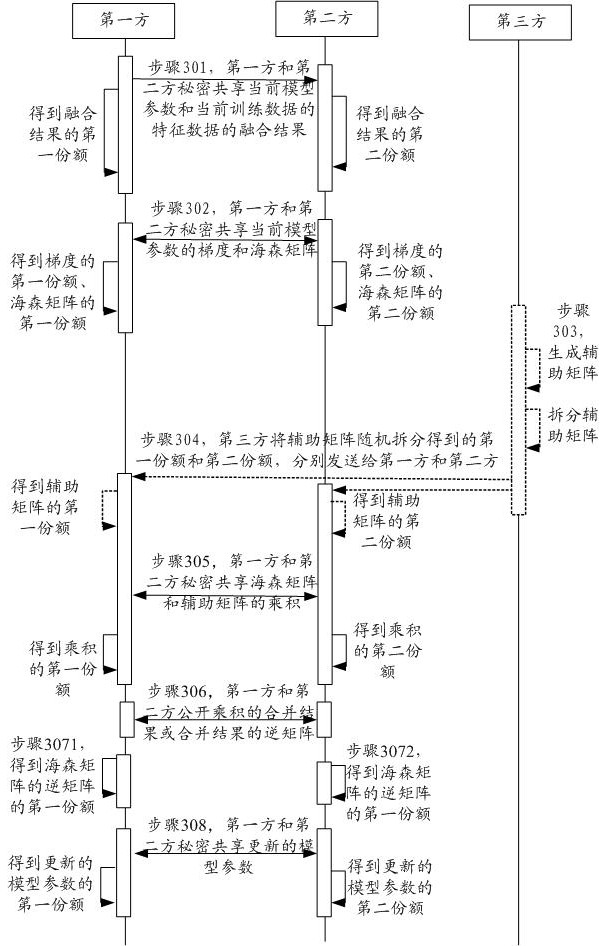
[0042] Secret Sharing (Secret Sharing, SS) is a secure algorithms to protect data privacy. A plurality of data side may be made without leaking own data, using the secret sharing method for collaborative computing, to obtain secret information. Each data share may obtain a copy of the confidential information. Single party can not recover the data secret information. Only the parties have a number of data integration in order to restore the share secret information. For example, the data held by the data x square P1 1 The data side P2 holds ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com