A method for generating vehicle network simulation data set based on intrusion attack
An in-vehicle network and simulation data technology, applied in the field of automotive information security, can solve problems such as the inability to deal with the attack category of in-vehicle network information security threats, the method of generating variable attack data with less consideration of attacks, the limited security protection capability and the scope of application, etc. Achieve the effect of enriching the data source of vehicle network intrusion detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be described in further detail below in conjunction with the embodiments given in the accompanying drawings.
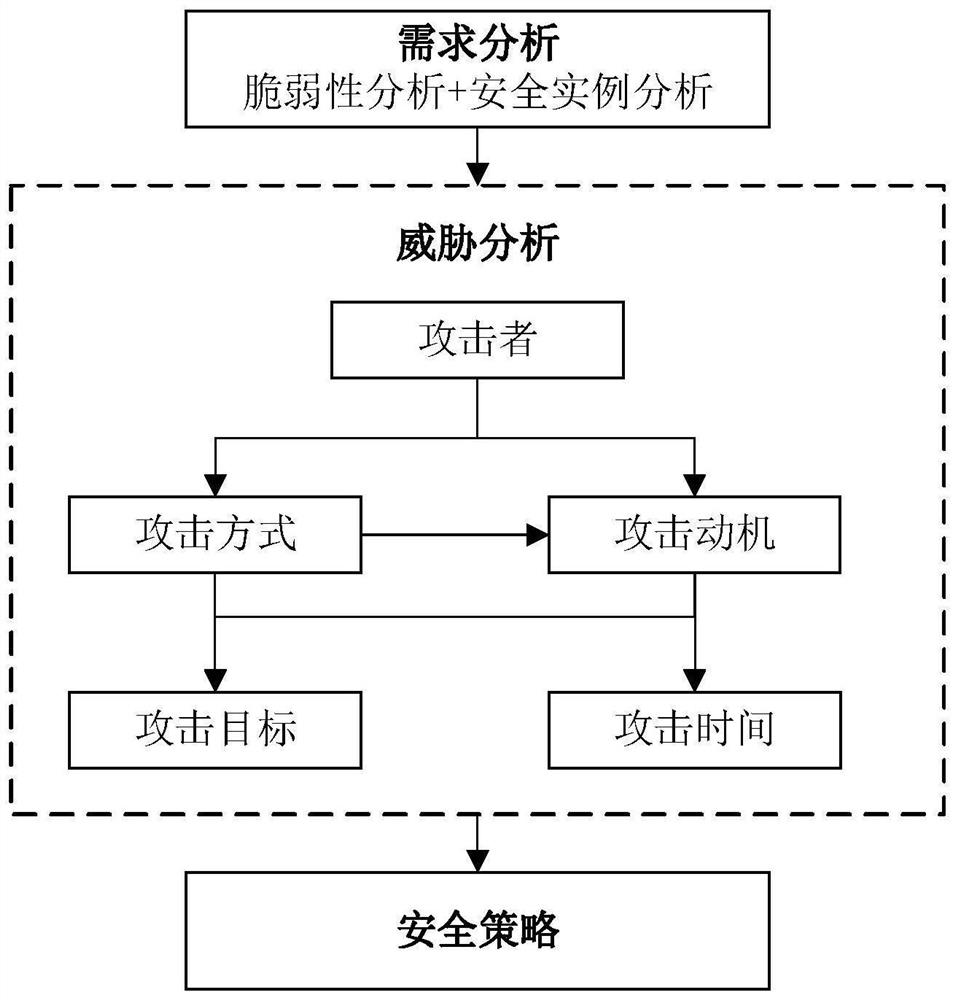
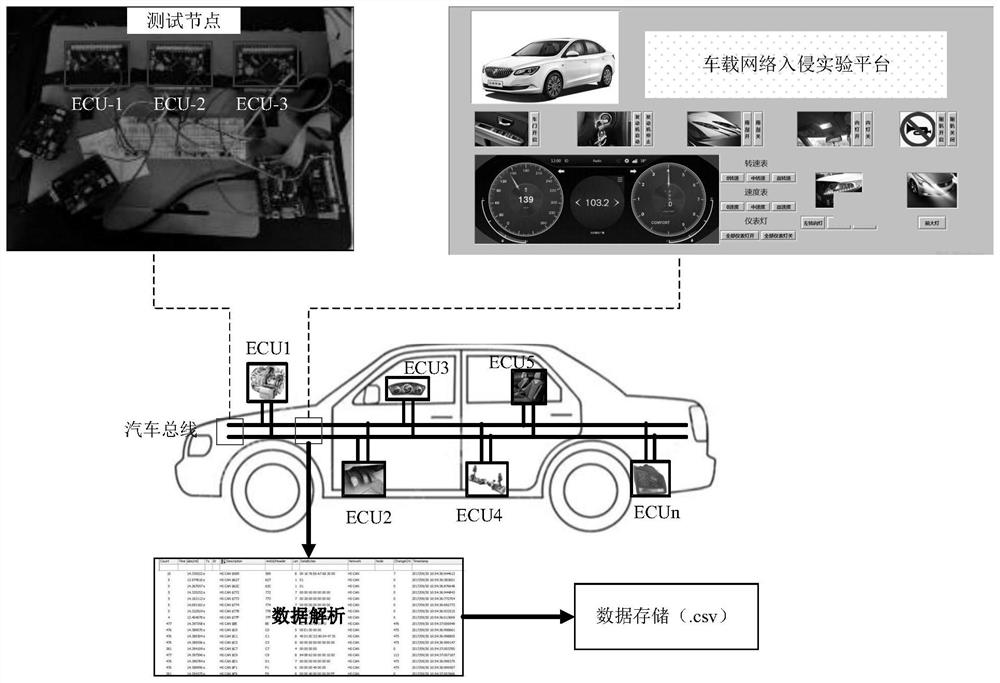
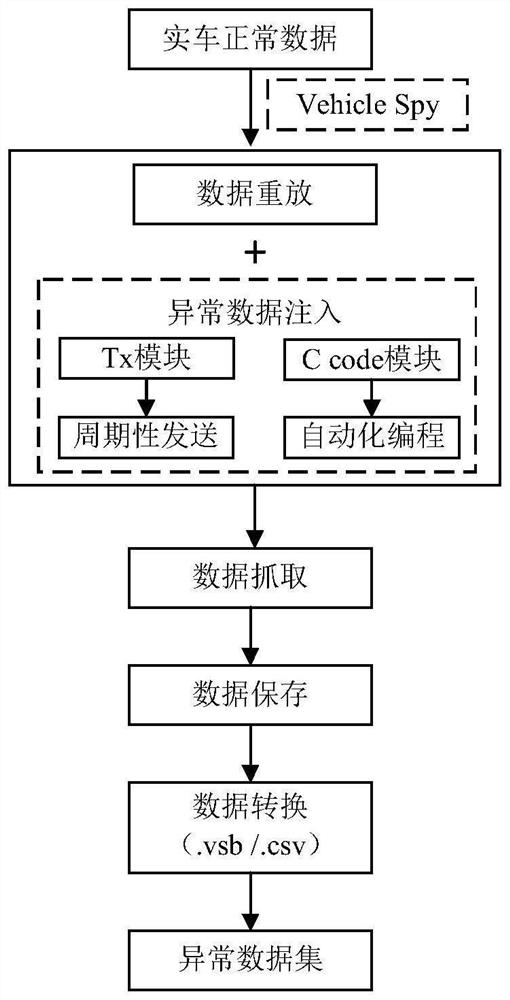
[0031] refer to Figures 1 to 4B As shown, a method for generating a vehicle-mounted network simulation data set based on an intrusion attack in this embodiment. Firstly, the information security vulnerability analysis of the vehicle network is carried out. According to the existing typical vehicle information security attack cases, the influencing factors of the vehicle network information security are analyzed, and the vehicle information security threat analysis framework is established from the perspective of the attacker. Then analyze the possible attack links under different attack methods and attack paths of the vehicle network, consider different attack methods and their characteristics, and use different attack test tools, software programming control and database programming processing methods to build a variety of attack me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com