Unified security login authentication method and device for operating system and service application
An operating system and business application technology, applied in the field of information security identity authentication, can solve the problems of inconsistency, virtual account and business application access user authentication discrete, etc., to achieve the effect of password-free high-strength identity authentication, sharing and consistency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
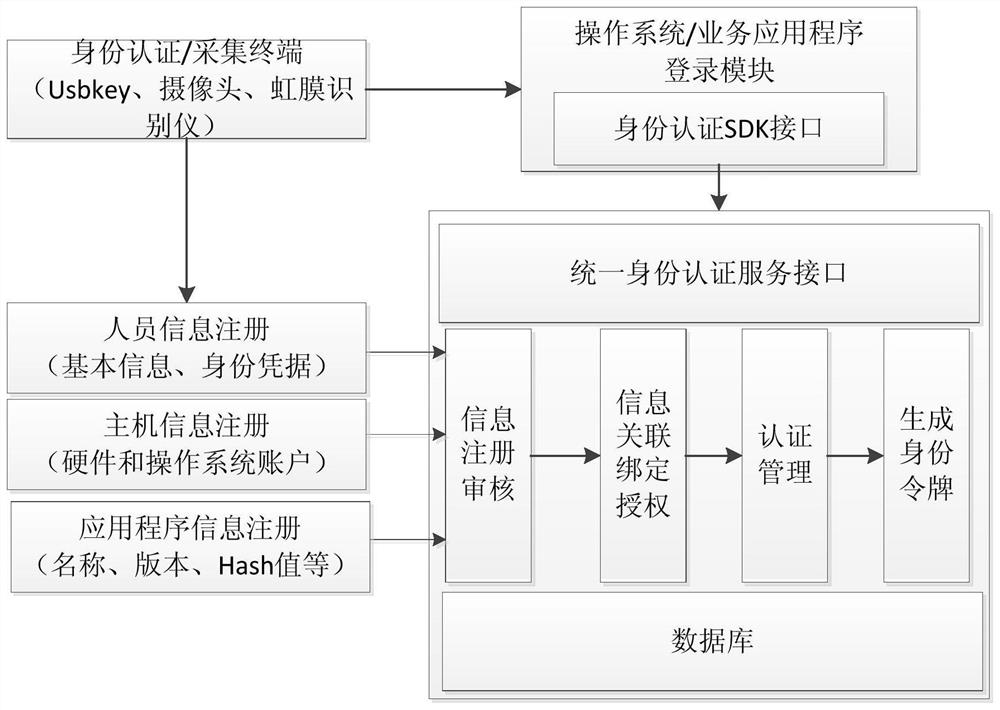
[0068] Correspondingly, the present invention provides an operating system and business application unified security login authentication device, which is characterized in that it includes an information registration module, an information association module, an authentication information acquisition module, an authentication module, an operating system login module and an application program login module ,in:
[0069] The information registration module is used to register user information, host device information and business application program information; where the user information includes the user's basic information and identity authentication data, and the host device information includes the virtual account of the operating system;
[0070] An information association module, used for associating user information with a virtual account of the operating system;
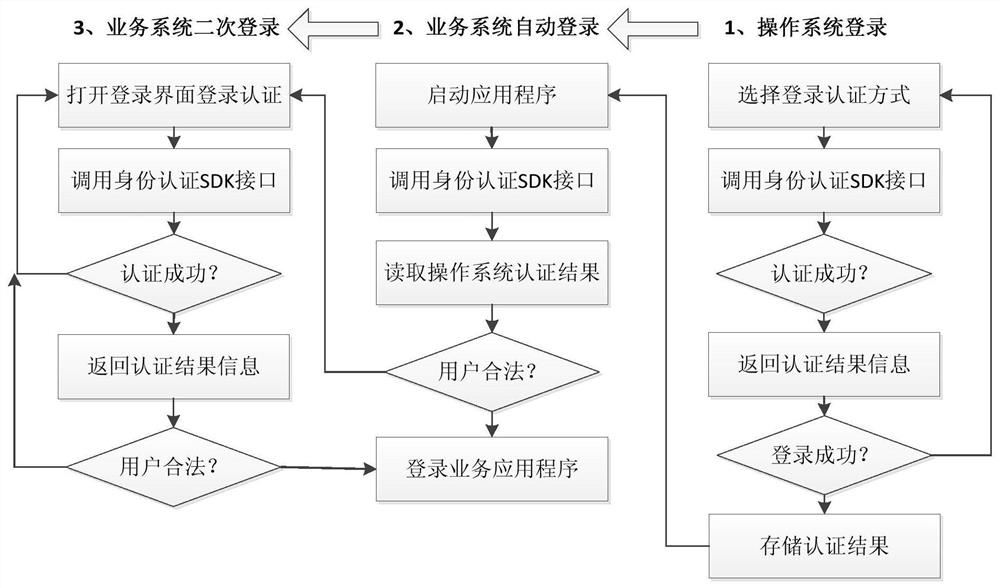
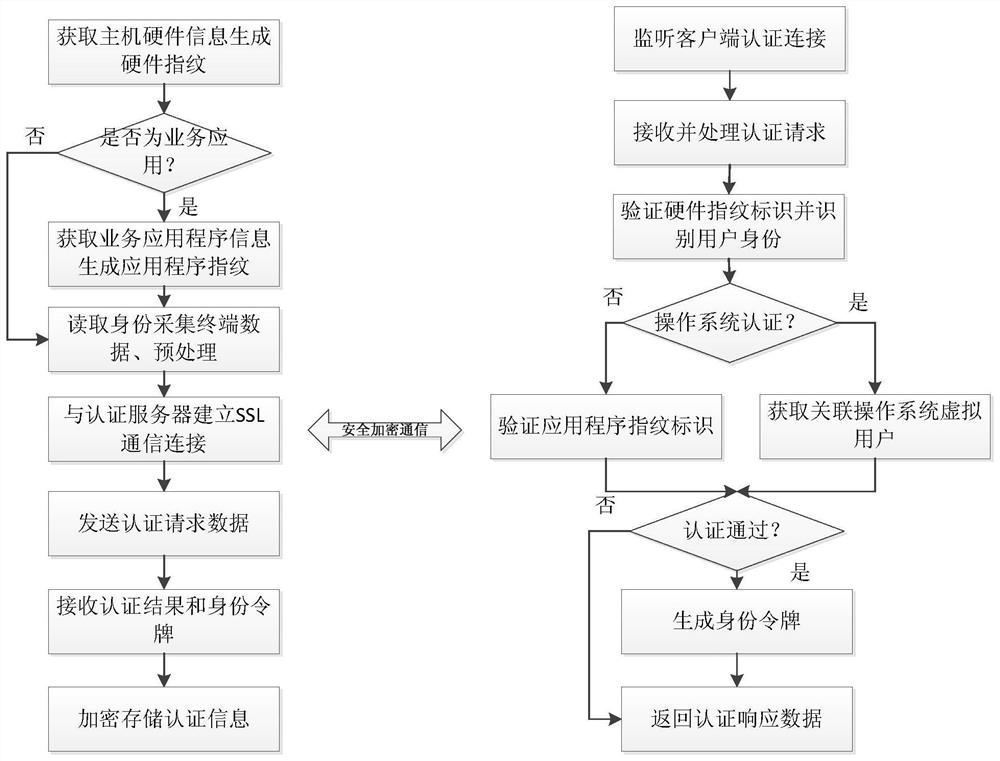
[0071] The authentication information acquisition module is used to respond to the operation of the user lo...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap