A Lattice Homomorphic Proxy Re-encryption Method Against Strong Collusion Attacks
A proxy re-encryption and collusion attack technology, applied in the field of information security, can solve problems such as being unable to resist strong collusion attacks, and achieve the effect of saving interaction overhead and ensuring homomorphism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
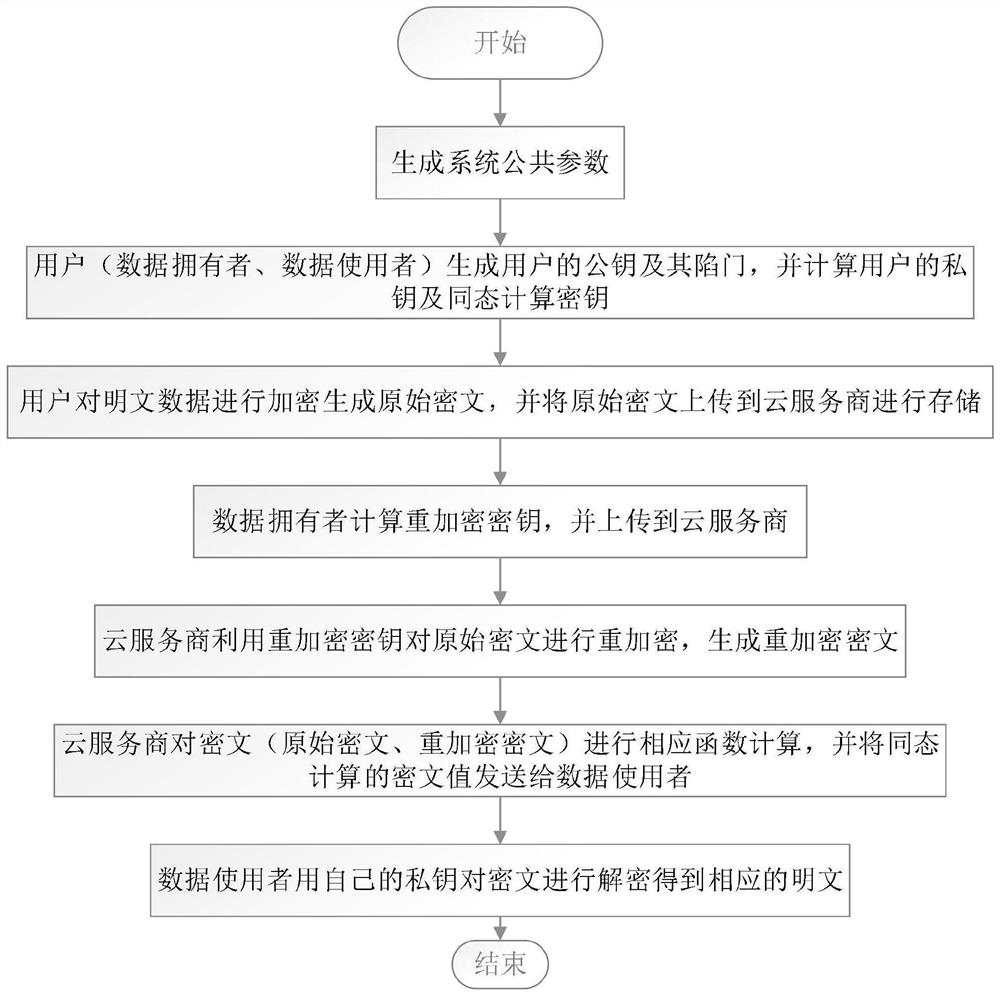
[0039] according to figure 1 As shown, the present invention provides a lattice-based homomorphic proxy re-encryption method against strong collusion attacks, specifically:
[0040] A lattice-based homomorphic proxy re-encryption method against strong collusion attacks, comprising the following steps:
[0041] Step 1: According to the input security parameters, randomly select vectors to generate system public parameters;
[0042] The step 1 is specifically:
[0043] According to the input security parameter k, select the prime number q, the n-dimensional vector set on the remaining class modulo q A vector chosen uniformly at random on The set of residual classes modulo q The Gaussian distribution χ on , the arithmetic circuit f of depth L, the output system public parameters
[0044] Step 2: According to the public parameters of the system, the public key, private key and homomorphic computing key are respectively generated by users, and the users include data owner...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com