User login authentication method based on two-stage deployment
A login authentication, user technology, applied in the field of user login authentication based on two-level deployment, can solve the problems of increasing user troubles and increasing development costs, and achieve a good effect of popularization and application value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
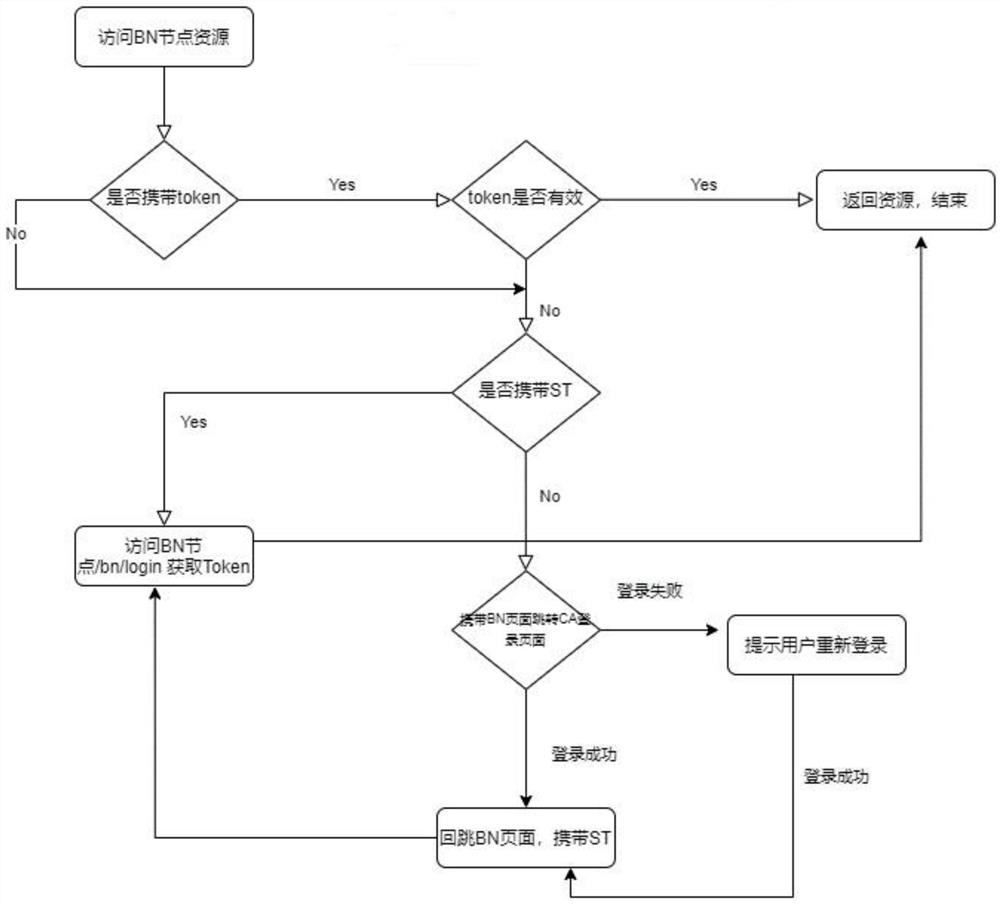
[0032] Such as figure 1 As shown, the user login authentication method based on two-level deployment of the present invention includes the following steps:
[0033] S1. The user accesses BN node resources.
[0034] S2. Judging whether to carry the token, if it is carried out, step S3 is executed, otherwise, step S4 is executed.
[0035] S3, whether the token is valid, if so, execute step S9, otherwise, execute step S4.
[0036] S4. Whether to carry ST, if yes, execute step S5; otherwise, execute step S6.
[0037] S5. Visit the BN node, and execute step S9.
[0038] S6. Whether the jump to the CA login page with the BN page is successful, if so, execute step S7, otherwise execute step S8.
[0039] S7. Call back the BN page, carry ST, and return to step S5.
[0040] S8. Prompt the user to log in again, and return to step S7.
[0041] S9. Return the resource.
[0042] BN stands for Business Node, which is the business node of each autonomous region.
[0043] CA is the CAS...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap