Dual-system security policy isolation method between containers, electronic equipment and storage medium
A security policy and system security technology, applied in the field of vehicle system security, can solve problems such as policy isolation not being realized, historical policy loss, and inability to upgrade host machines and containers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
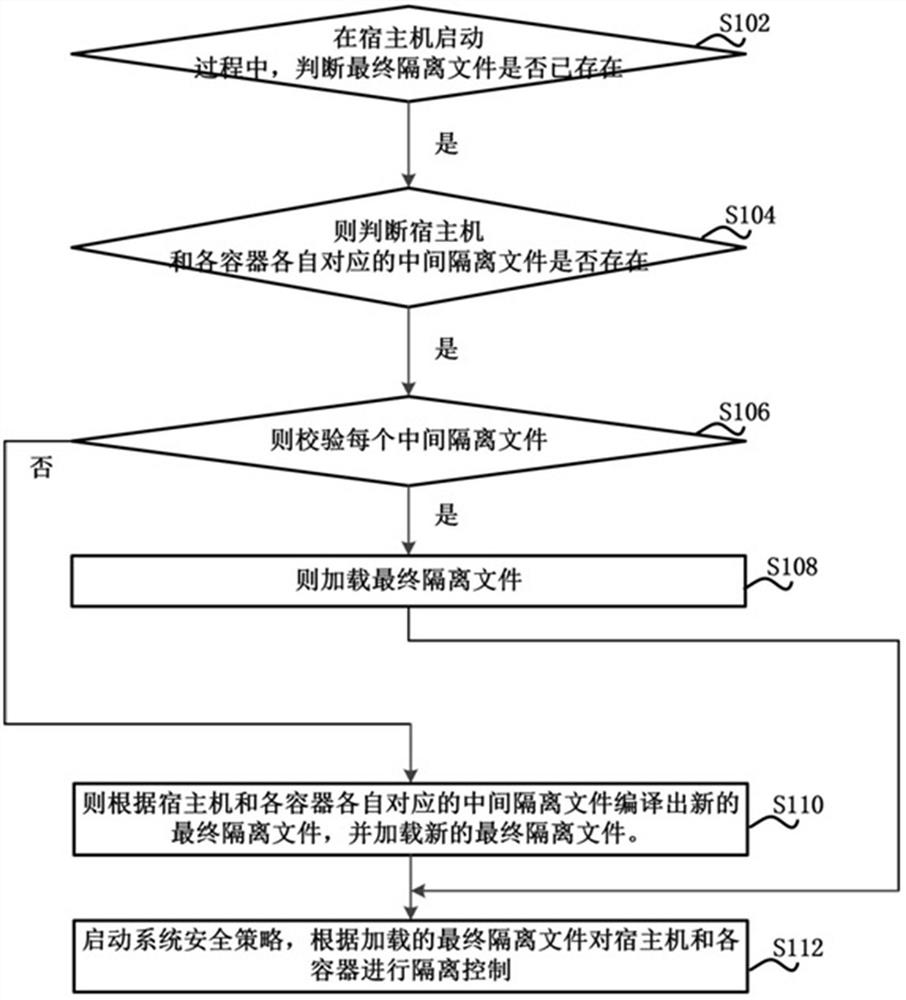
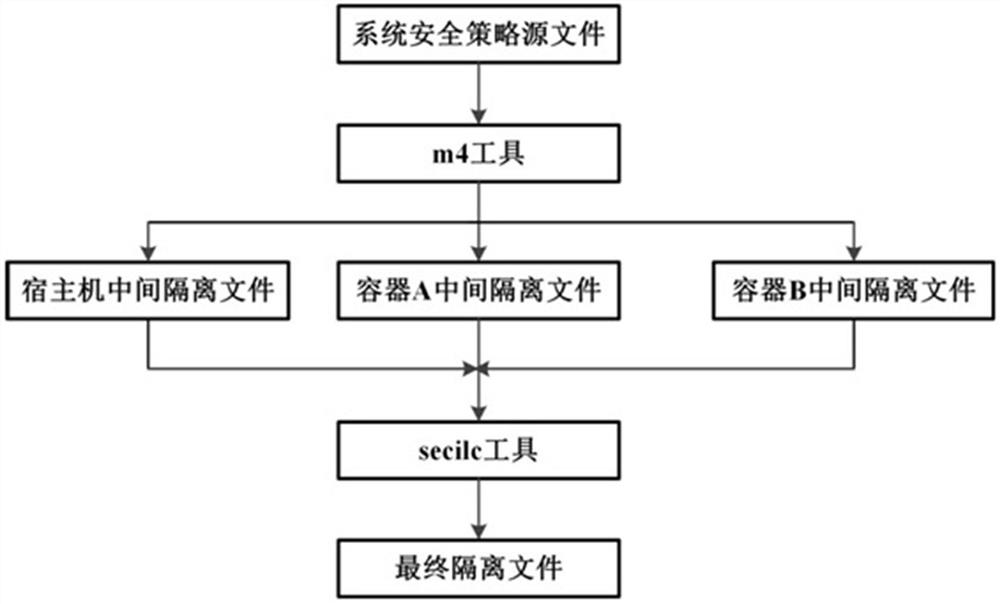
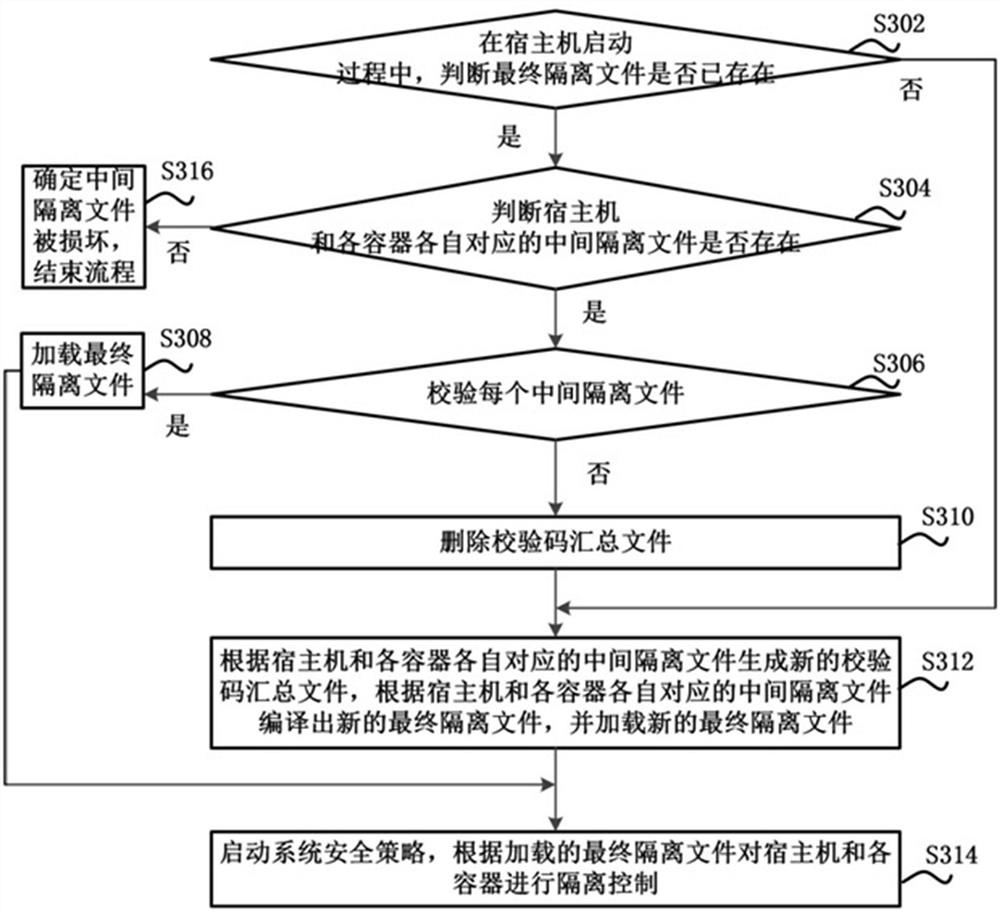
[0035] At present, the security policy isolation between the host and each container has not been realized. Specifically, for example, the host and each container cannot be upgraded independently, and the policies of the host and each container (such as the SEPolicy policy) cannot be upgraded multiple times. ), it is also easy to cause the loss of historical strategies. If the security policy isolation between the host machine and each container cannot be realized, the resources between the on-board systems on the vehicle cannot be fully shared. Being fully utilized not only increases the cost, but also reduces the communication efficiency between the two.
[0036] In view of the above problems, an embodiment of the present invention provides a dual-system security policy isolation method between containers. This approach could ultimately enable independent upgrades between in-vehicle systems. The security policy isolation may be SELinux (SecurityEnhanced Linux) policy isola...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com