Full-link monitoring method and device for monitoring alarm system
An alarm system and full-link technology, applied in the field of Internet operation and maintenance, can solve problems such as failure of monitoring alarms, failure to achieve self-monitoring, failure of monitoring solutions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
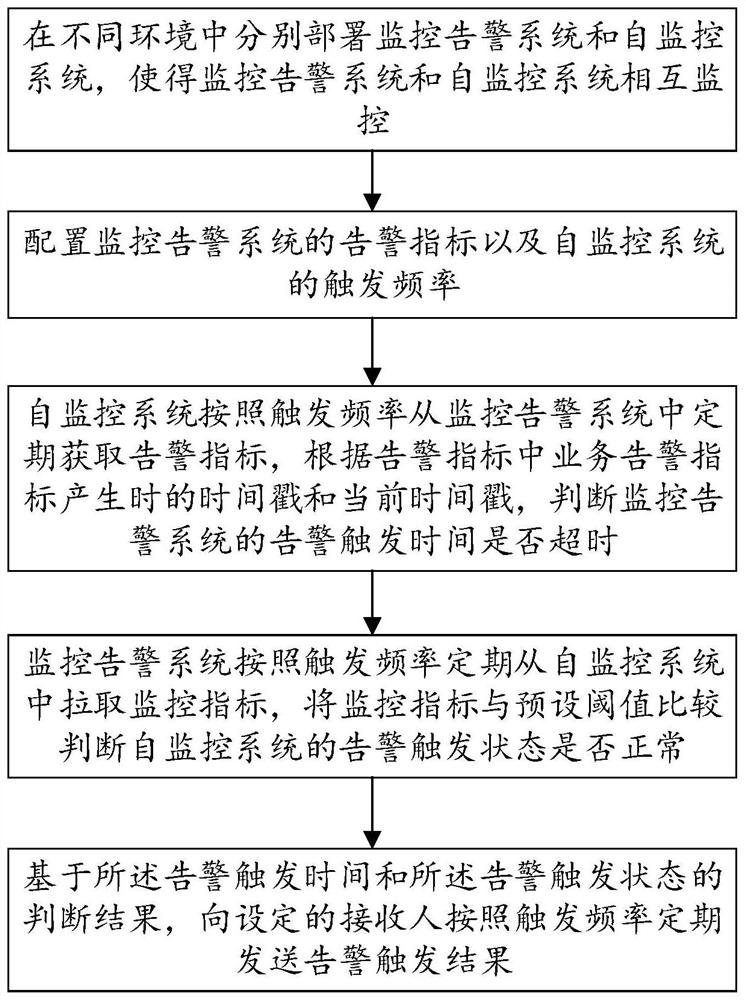
[0049] see figure 1 , this embodiment provides a full-link monitoring method for monitoring an alarm system, including:
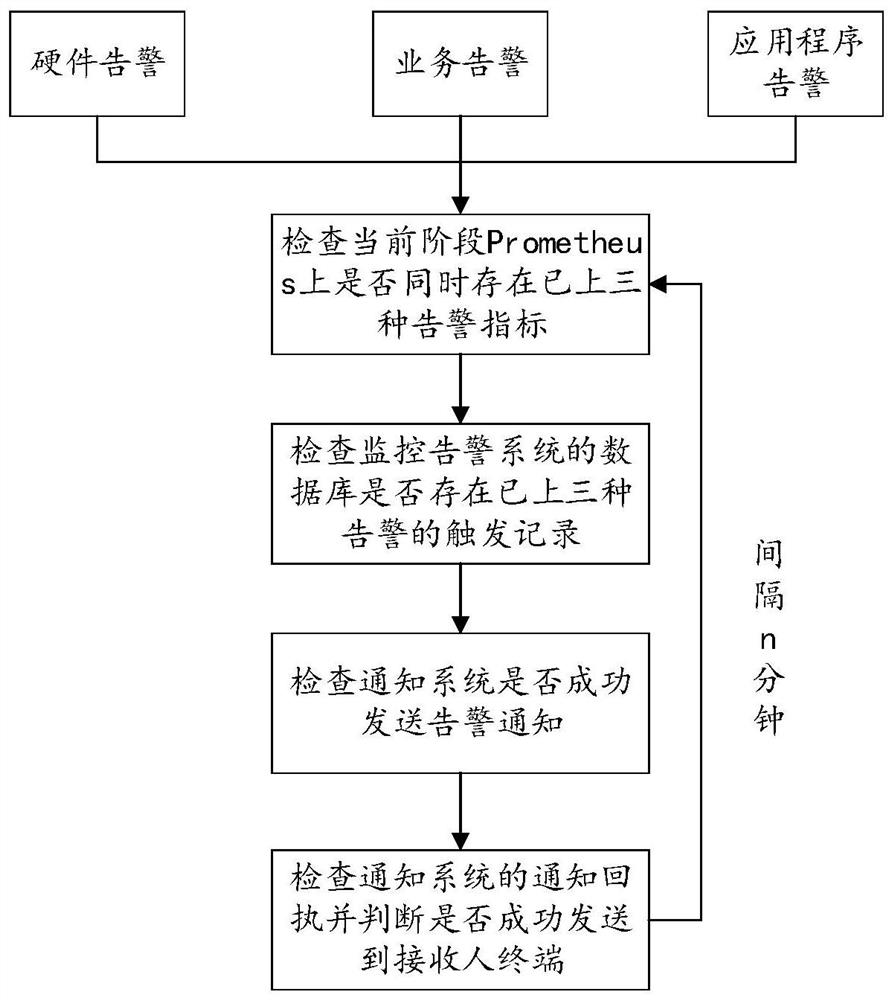
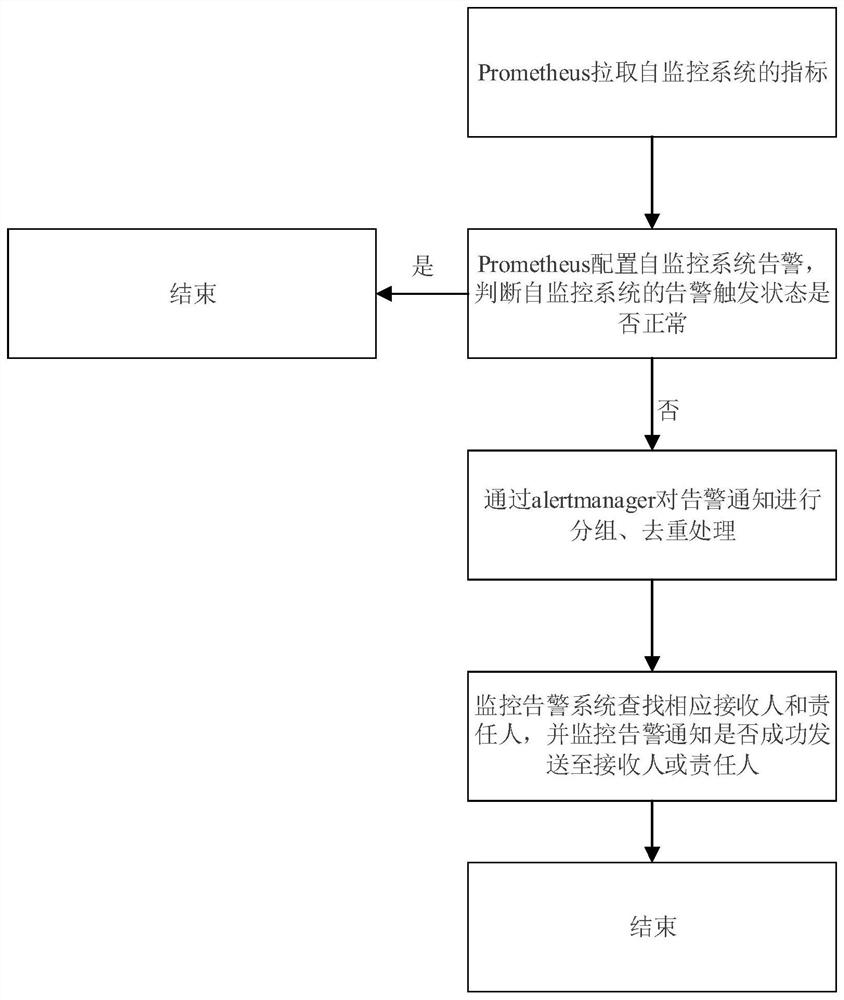
[0050] Deploy the monitoring and alarm system and the self-monitoring system in different environments, so that the monitoring and alarm system and the self-monitoring system can monitor each other; configure the alarm indicators of the monitoring and alarm system and the trigger frequency of the self-monitoring system; According to the time stamp when the business alarm indicator in the alarm indicator is generated and the current time stamp, it is judged whether the alarm trigger time of the monitoring alarm system has expired; the monitoring alarm system periodically pulls monitoring indicators from the self-monitoring system according to the trigger frequency , comparing the monitoring index with the preset threshold to judge whether the alarm trigger state of the self-monitoring system is normal; based on the judgment result of the alarm trigger time a...
Embodiment 2
[0083] This embodiment provides a full-link monitoring device for monitoring an alarm system, including:
[0084] The deployment unit is used to deploy the monitoring and alarm system and the self-monitoring system respectively in different environments, so that the monitoring and alarm system and the self-monitoring system can monitor each other;
[0085] The configuration unit is used to configure the alarm indicators of the monitoring and alarm system and the trigger frequency of the self-monitoring system;
[0086] The first monitoring unit is used to periodically obtain alarm indicators from the monitoring and alarm system through the self-monitoring system according to the trigger frequency, and judge whether the alarm trigger time of the monitoring and alarm system is time out;
[0087] The second monitoring unit is used to regularly pull monitoring indicators from the self-monitoring system according to the trigger frequency through the monitoring and alarm system, an...
Embodiment 3
[0120] This embodiment provides a computer-readable storage medium. A computer program is stored on the computer-readable storage medium. When the computer program is run by a processor, the steps of the above-mentioned full-link monitoring method for monitoring an alarm system are executed.
[0121] Compared with the prior art, the beneficial effect of the computer-readable storage medium provided by this embodiment is the same as that of the full-link monitoring method for monitoring the alarm system provided by the above technical solution, and will not be repeated here.
[0122] Those of ordinary skill in the art can understand that all or part of the steps in the above-mentioned inventive method can be completed by instructing related hardware through a program. The above-mentioned program can be stored in a computer-readable storage medium. When the program is executed, it includes: For each step of the method in the above embodiments, the storage medium may be: ROM / RAM, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com