Identification updating method and equipment
An update method and identification technology, applied in the field of communication, can solve problems such as inconsistency in understanding, communication interruption, etc., and achieve the effect of improving the effectiveness of communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
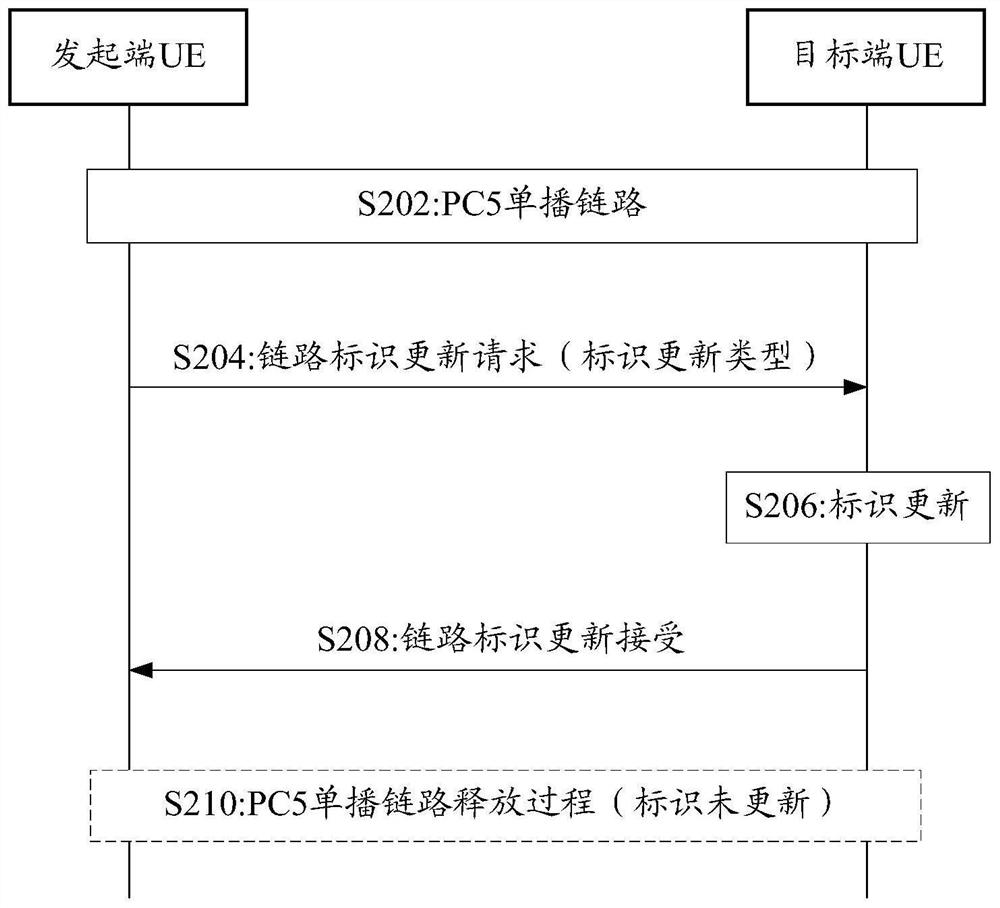
[0078] In this embodiment, the initiator terminal device (initiator UE, or called the sender UE) carries an identifier update type indication in the PC5 unicast link identifier update request message, and the target terminal device (target UE) according to The identification update type indicates whether to update related identification information.
[0079] Such as figure 2 Shown, this embodiment comprises the following steps:
[0080] S202: There is an established PC5 unicast communication link between the initiator UE and the target UE.
[0081] S204: The initiator UE sends a PC5 unicast link identity update request message carrying an identity update type indication to the target UE. The above identity update type indication may include:
[0082] 1) Identity update triggered by privatization configuration; or
[0083] 2) Identity update triggered by non-privatization configuration. For example, the Layer 2 ID of the initiator UE conflicts or receives an ID update inst...
Embodiment 2
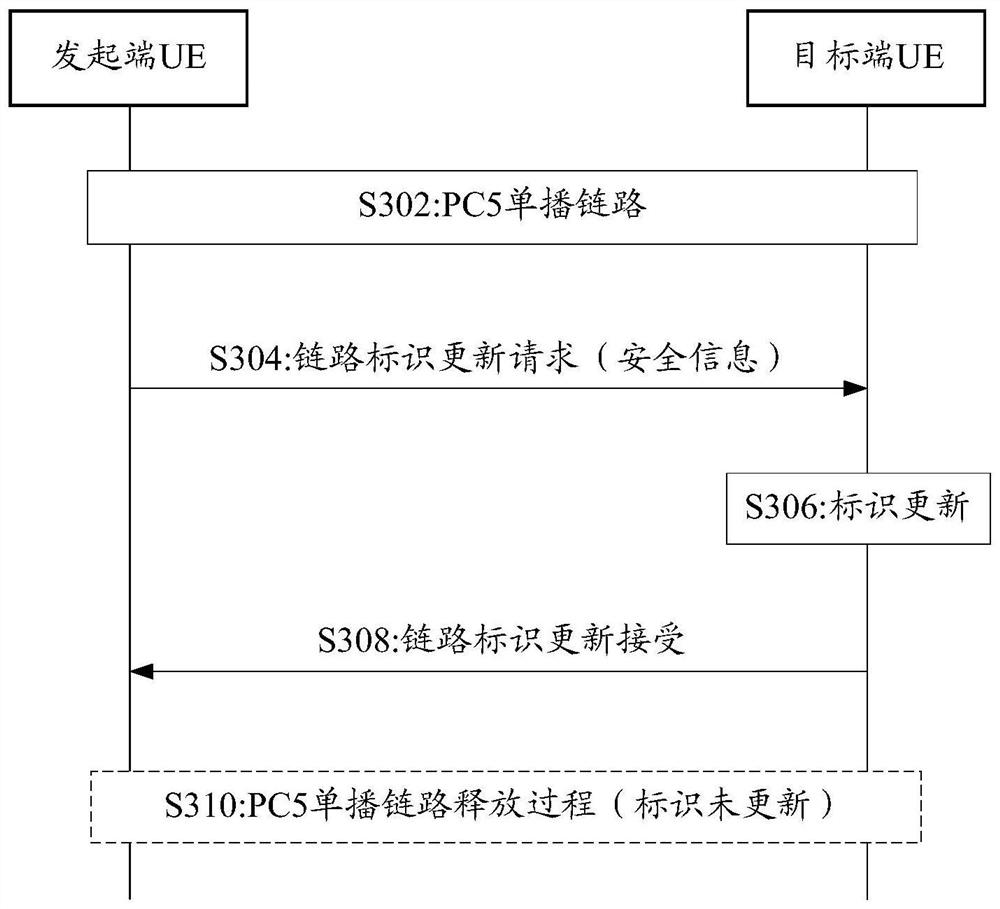
[0096] In this embodiment, the initiating UE selects whether to carry security information in the PC5 unicast link ID update request message, that is, the carrying of security information is equivalent to an indication for indicating that the target UE needs to update its own ID information. If the PC5 unicast link identifier update request message does not carry security information, the target UE determines whether to update its own identifier information according to the implementation of the terminal equipment (UE implementation).
[0097] Such as image 3 Shown, this embodiment comprises the following steps:
[0098] S302: There is an established PC5 unicast communication link between the initiator UE and the target UE.
[0099] S304: The initiator UE sends a PC5 unicast link identifier update request message carrying security information to the target UE.
[0100] S306: After receiving the PC5 unicast link identifier update request message, the target UE updates its ow...
Embodiment 3
[0110] In this embodiment, the initiator UE carries an information element of "identifier update required" in the PC5 unicast link identifier update request message, and the target UE determines whether to update relevant identifier information according to the identifier update requirement.
[0111] Such as Figure 4 Shown, this embodiment comprises the following steps:
[0112] S402: There is an established PC5 unicast communication link between the initiator UE and the target UE.
[0113] S404: The initiating UE sends a PC5 unicast link identifier update request message carrying "Identity Update Need" to the target UE. The above "Identity Update Need" may include:
[0114] 1) "identifier update required"; or
[0115] 2) "identifier update required".
[0116] S406: After receiving the PC5 unicast link identifier update request message, the target UE updates its own identifier information.
[0117] In this embodiment, it is assumed that the above information element of "i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com