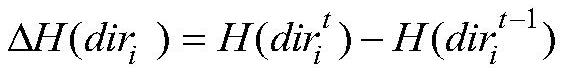Fair rational secure two-party computing protocol
A secure two-party computing, rational technology, applied in the field of rational cryptography, can solve problems such as uncertainty, inconsistent with realistic scenarios, and inability to measure the amount of information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] The technical solution of the present invention is clearly and completely described below. The present invention provides a fair, rational and secure two-party computing protocol, and the specific steps are as follows:
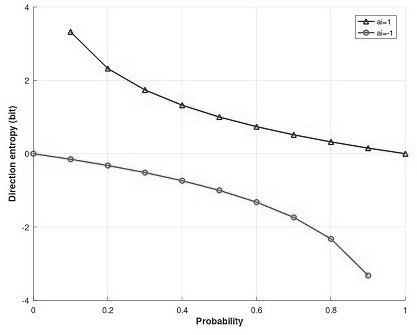
[0013] Step 1: Initialization of direction entropy
[0014] Step 1.1: In the initial stage of the protocol, it is assumed that each participant has an initial direction entropy H(dir), and the initial direction entropy is
[0015] Step 1.2: Assume that there is a trusted third party (TTP) who selects the secret S and divides it into n shares, and sends n shares of secrets to P i ∈P(i∈{1,2}).
[0016] Step 1.3: TTP will with as information x and respectively by P 1 and P 2 hold.
[0017] Step 1.4: P 1 and P 2 Exchange n shares with Last P 1 and P 2 Integrate n secrets respectively to form S.
[0018] Step 2: Information exchange based on direction entropy
[0019] Step 2.1: Participant P i ∈P(i∈{1,2}) (assumed to be P 1 ) selects a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com