Trusted device and computing system
A trusted computing and trusted technology, applied in computing, transmission systems, digital transmission systems, etc., can solve problems such as inapplicable cloud computing or equipment sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
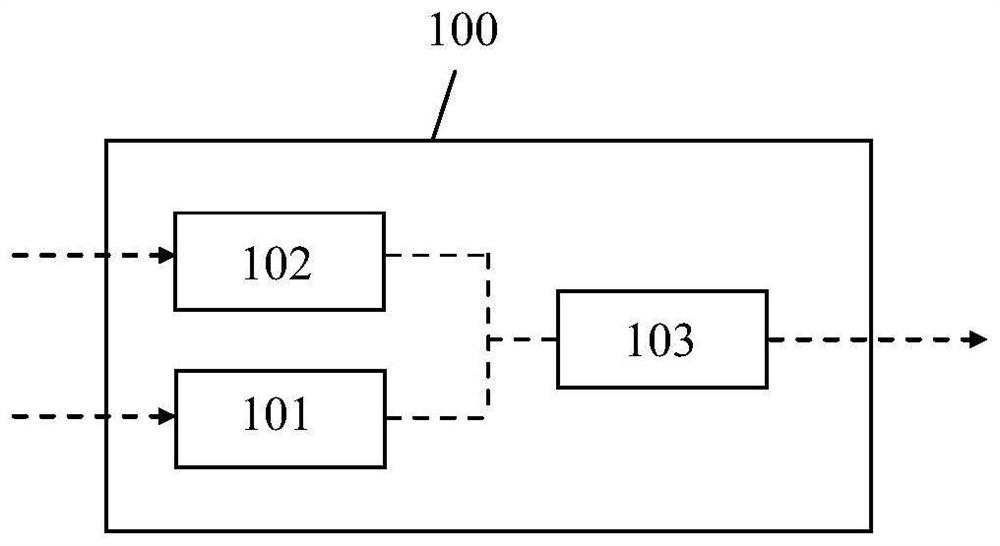
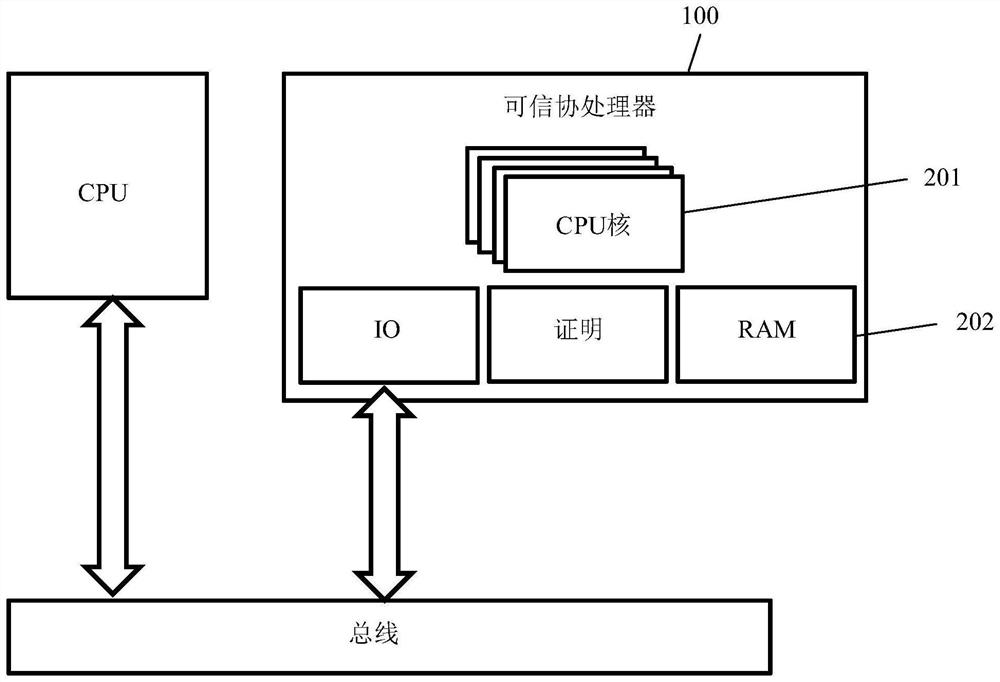
[0080] figure 1 A schematic diagram of the trusted device 100 provided by the embodiment of the present invention is shown. Trusted device 100 may be used in trusted computing system 400, as referenced below Figure 4 describe. Trusted device 100 and trusted computing system 400 are particularly well suited for cloud computing.
[0081] Trusted device 100 is used to obtain numerical value 101 and program code 102 from user equipment 501 (user equipment 501 will also be referred to below Figure 5 describe). User device 501 is not part of trusted device 100 . According to the numerical value 101 and the program code 102 , the trusted device 100 can calculate a hash value 103 and sign the hash value 103 . Then, the signature hash value 103 is provided to the verification device 401 (also described below).
[0082] Therefore, it can be verified that the program code 102 provided to the trusted device 100 is also the program code 102 executed by the trusted device.
[0083]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com