Data processing method and device for network beacon tampering detection
A data processing device and tamper detection technology, which is applied in the field of network security, can solve problems such as difficult to judge network beacon tampering in real time, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
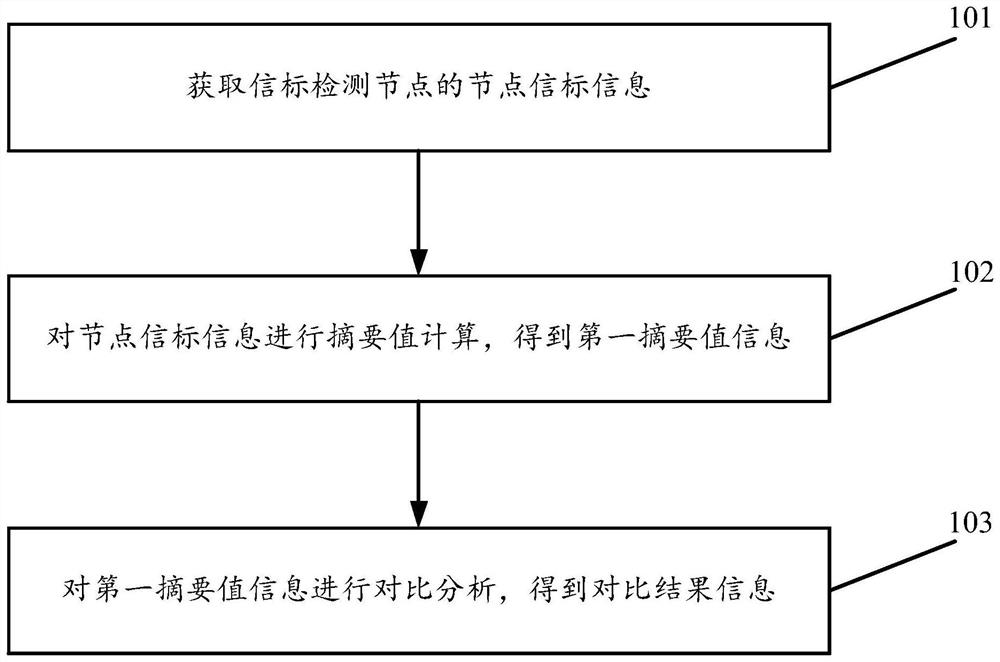
[0083] see figure 1 , figure 1 It is a schematic flowchart of a data processing method for network beacon tampering detection disclosed by an embodiment of the present invention. in, figure 1 The described data processing method for network beacon tampering detection is applied to a network security management system, such as a local server or a cloud server for data processing and management of network beacon tampering detection, which is not limited in the embodiments of the present invention. Such as figure 1 As shown, the data processing method for network beacon tampering detection may include the following operations:
[0084] 101. Obtain node beacon information of a beacon detection node.
[0085] 102. The root performs digest value calculation on node beacon information to obtain first digest value information.
[0086] 103. Perform comparative analysis on the first summary value information to obtain comparison result information.
[0087] In the embodiment of t...
Embodiment 2
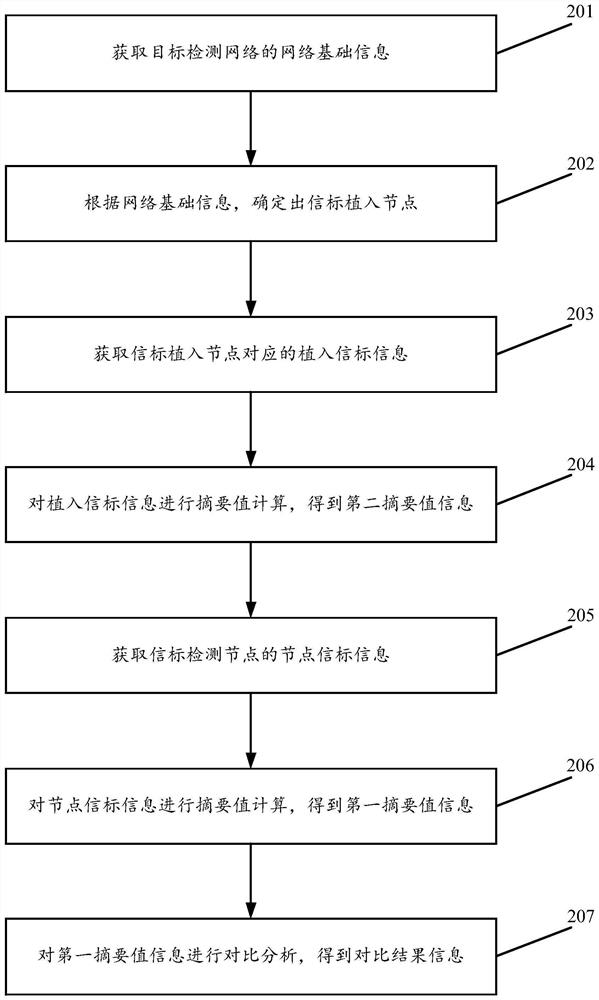
[0129] see figure 2 , figure 2 It is a schematic flowchart of another data processing method for network beacon tampering detection disclosed in the embodiment of the present invention. in, figure 2 The described data processing method for network beacon tampering detection is applied to a network security management system, such as a local server or a cloud server for data processing and management of network beacon tampering detection, which is not limited in the embodiments of the present invention. Such as figure 2 As shown, the data processing method for network beacon tampering detection may include the following operations:
[0130] 201. Acquire basic network information of a target detection network.
[0131] 202. Determine the beacon implantation node according to the basic network information.
[0132] 203. Obtain implanted beacon information corresponding to the beacon implanted node.
[0133] In the embodiment of the present invention, the above-mentioned...
Embodiment 3
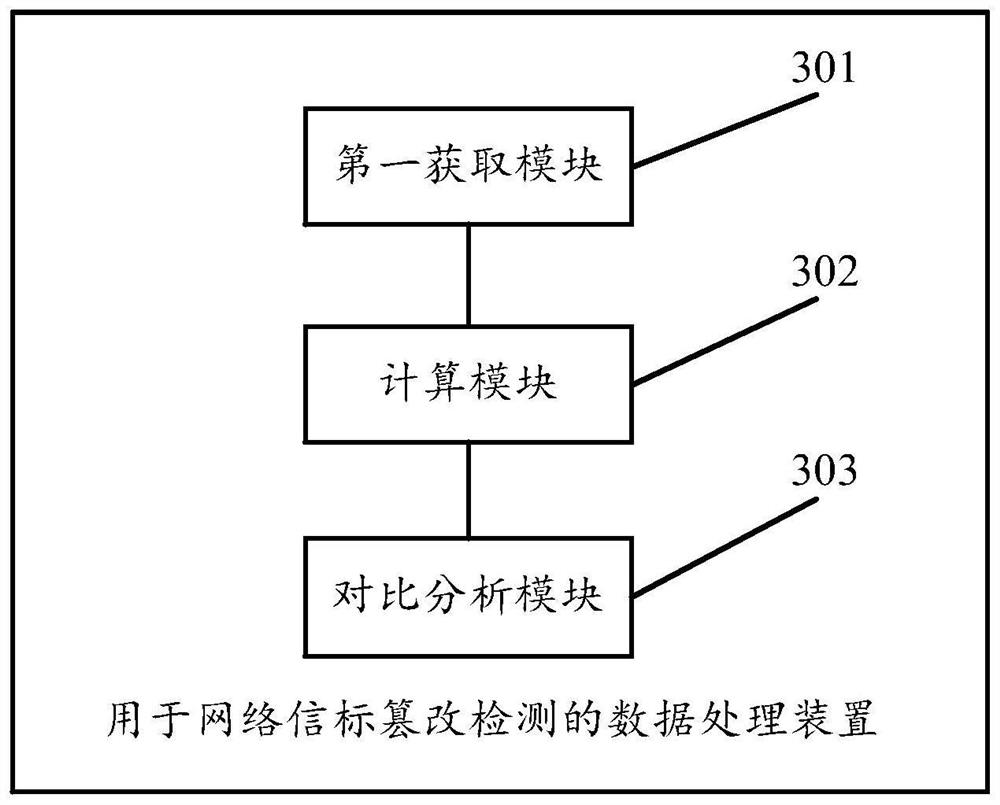
[0159] see image 3 , image 3 It is a schematic structural diagram of a data processing device for network beacon tampering detection disclosed in an embodiment of the present invention. in, image 3 The described device can be applied to a network security management system, such as a local server or a cloud server used for data processing and management of network beacon tampering detection, which is not limited by the embodiments of the present invention. Such as image 3 As shown, the device may include:
[0160] The first acquiring module 301 is configured to acquire node beacon information of a beacon detection node;
[0161] Calculation module 302, configured to perform summary value calculation on node beacon information to obtain first summary value information;
[0162] The comparison and analysis module 303 is configured to perform comparison and analysis on the first summary value information to obtain comparison result information; the comparison result info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com