Firmware security starting method and device, computing equipment and readable storage medium
A computing device and secure boot technology, applied in the computer field, can solve problems such as untrustworthy, untrustworthy application programs and upper-layer security mechanisms, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application. In the description of the present application, the terms "first", "second" and the like are only used for distinguishing descriptions, and cannot be understood as indicating or implying relative importance.
[0046] In order to clearly describe the solution of this embodiment, the nouns involved are defined as follows:
[0047] UEFI: Unified Extensible Firmware Interface, Unified Extensible Firmware Interface.
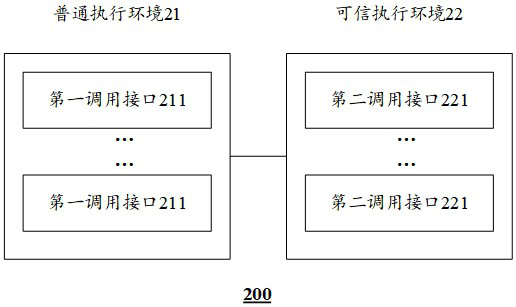
[0048] TEE: Trusted Execution Environment, trusted execution environment, TEE is based on trustzone technology to build a trusted program operating environment isolated from the non-secure world.
[0049] OP-TEE: Open Portable TEE, Open Portable Trusted Execution Environment, OP-TEE is an open source project that completely implements a trusted execution software and hardware environment, in ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap