Dynamic ciphertext retrieval and verification method and system supporting full vector operations
A vector and ciphertext technology, applied in the field of access control ciphertext retrieval, can solve problems such as the inability to support dynamic operations of data addition and deletion, cloud server is not completely trusted, attacks, etc., to achieve storage overhead, resist file injection attacks, Validating the effect of improved efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to facilitate the understanding and implementation of the present invention by those skilled in the art, the present invention will be described in further detail below with reference to the accompanying drawings and embodiments. It should be understood that the embodiments described herein are only used to illustrate and explain the present invention, not The invention is limited.
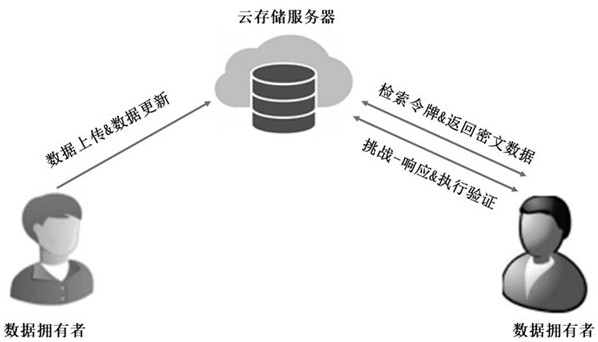
[0030] see figure 1 and figure 2 , a dynamic ciphertext retrieval method supporting full vector operations provided by the present invention,
[0031] During the system initialization management process, input security parameters , generate the pseudo-random function, hash function, public key PK, private key SK and public parameter PP required by the entire system, and distribute the public key PK and public parameter PP to the participants in the system, including the data owner, cloud Storage server; private key SK data owner saves it;
[0032] In this embodiment, the pseu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com