Method for realizing user authentication of wide-band network special bus
A user authentication and broadband network technology, applied in the field of user authentication in broadband networks, can solve problems such as general limitations, inability to use authentication servers, increase costs, etc., and achieve the effect of simple Internet access, increased versatility and scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
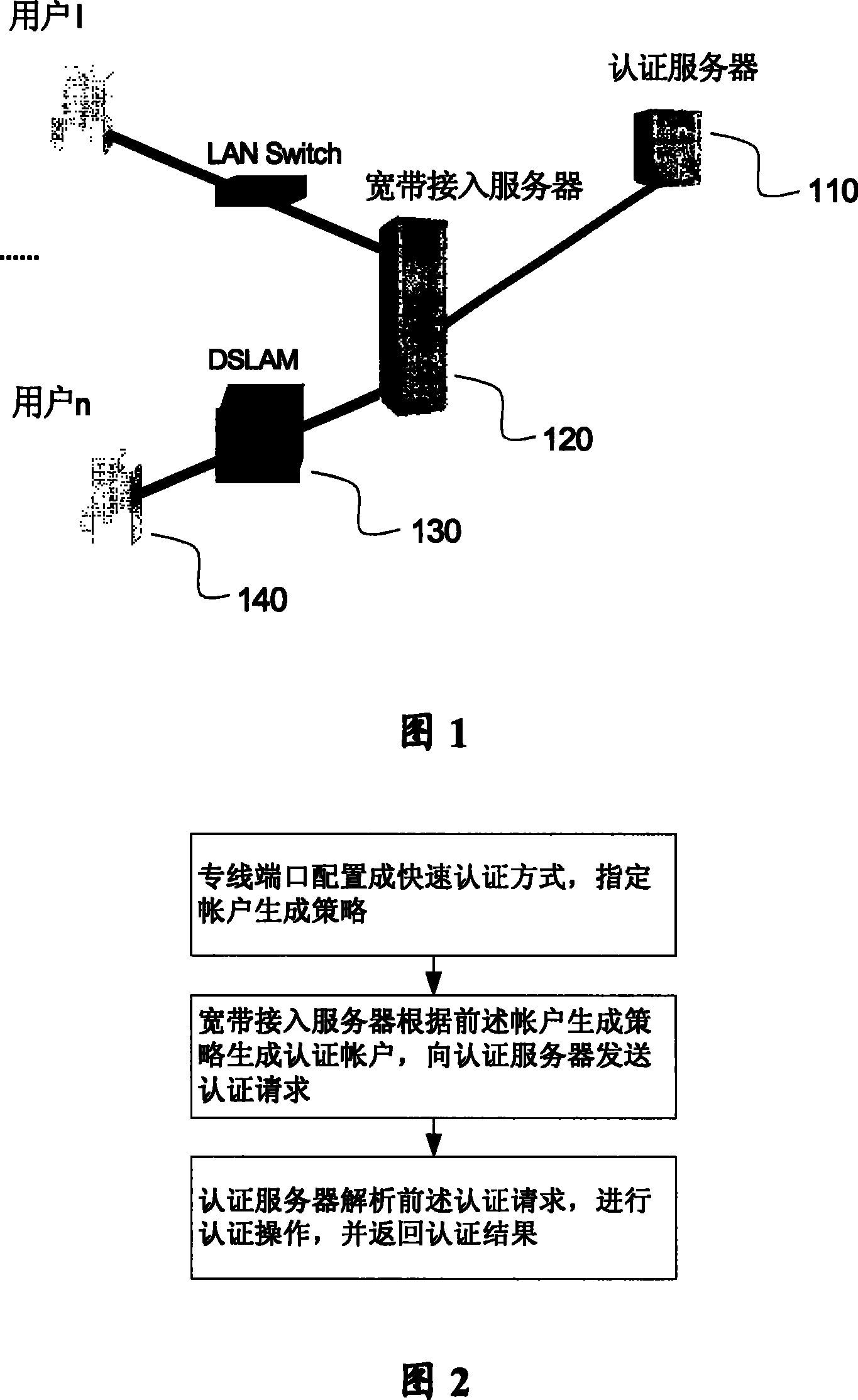
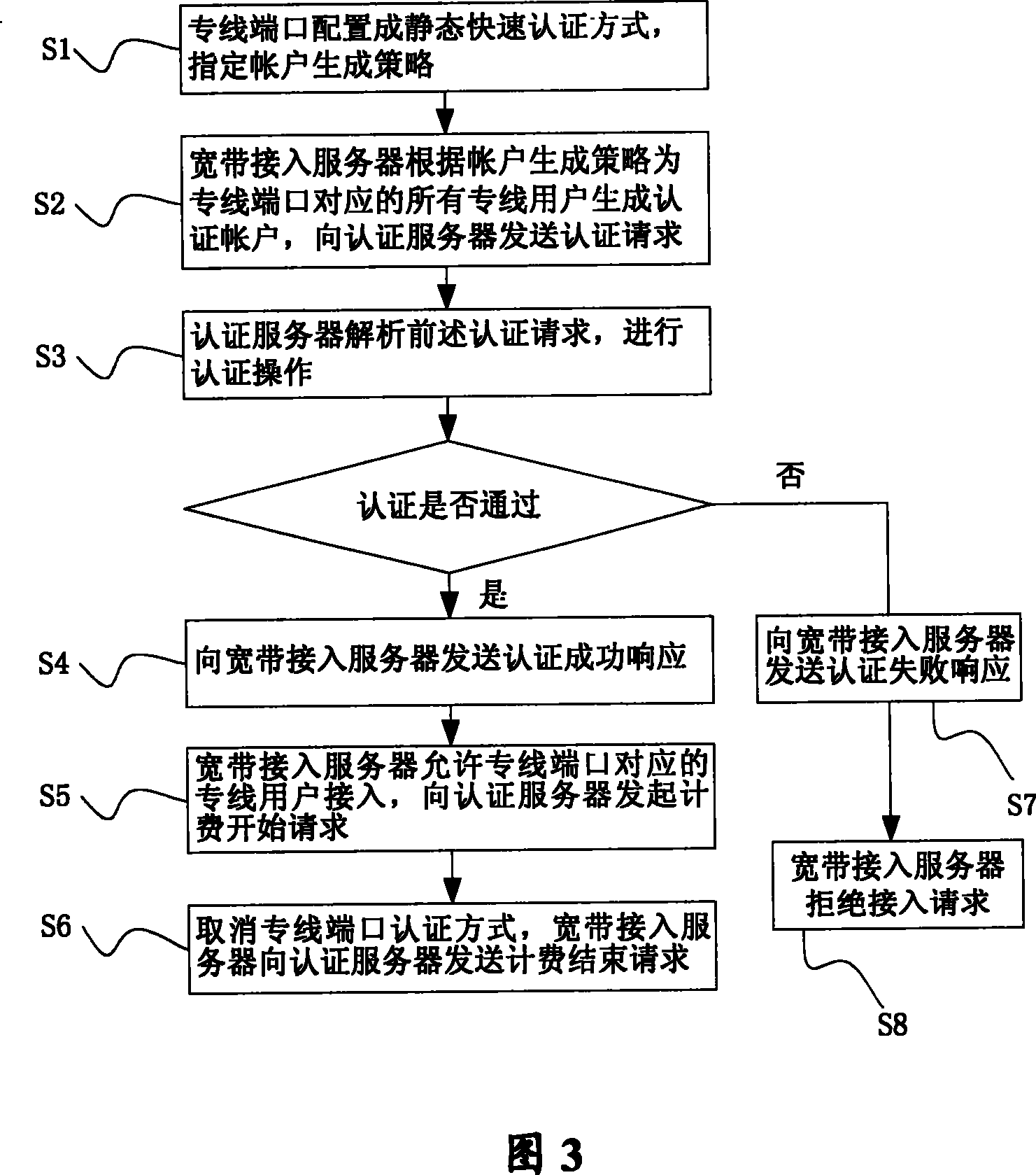
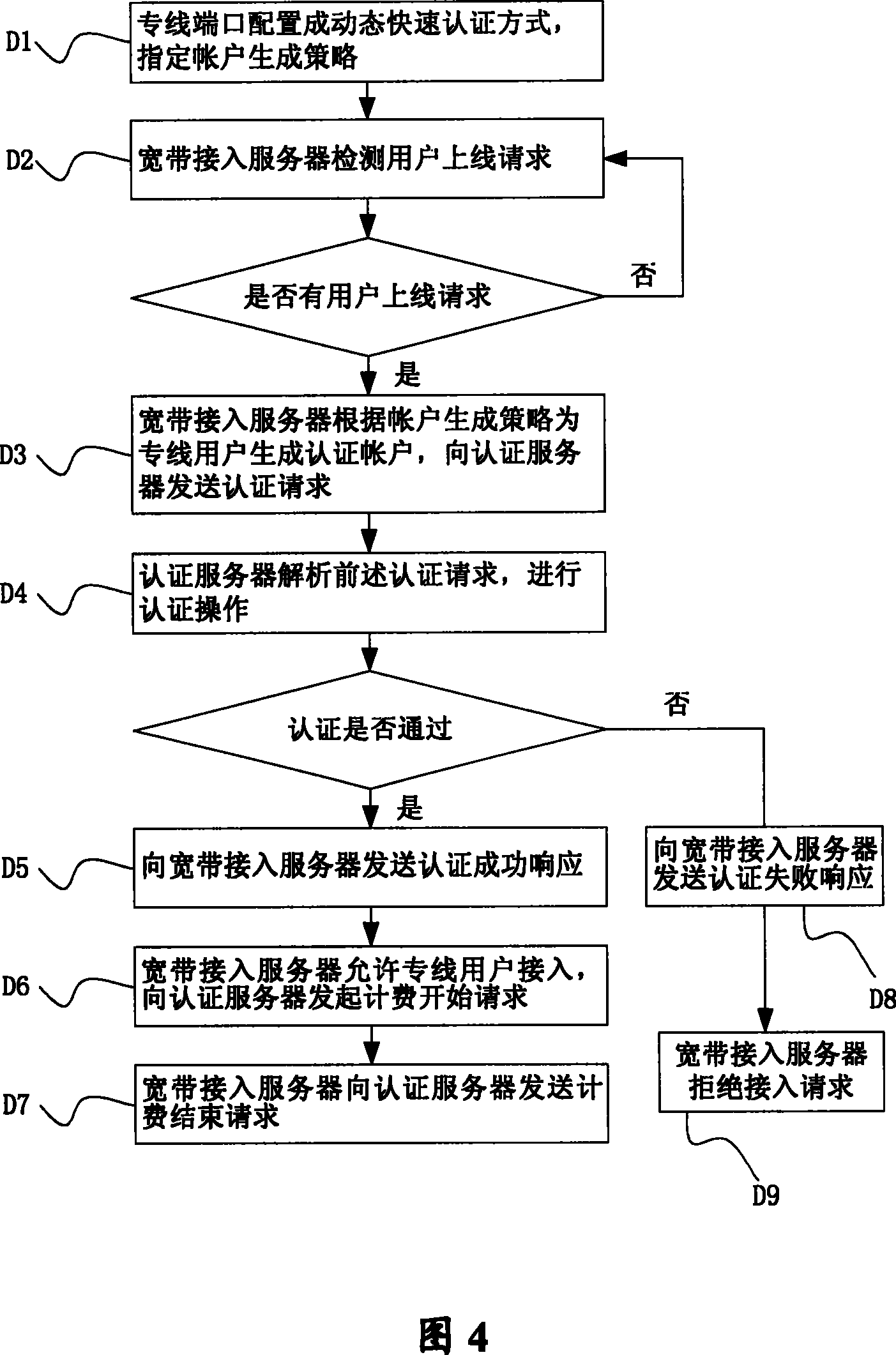
[0028] see figure 1 , the method for realizing broadband network dedicated line user authentication in the present invention is applied to a broadband access system, and the system includes an authentication server 110 , a broadband access server 120 , a switch 130 and a user terminal 140 .
[0029] Wherein, the authentication server 110 provides functions such as authentication, authorization, and accounting for leased line users, and is also called Remote Authentication Dial-In User Service (RADIUS, Remote Authentication Dial-In User Service). It includes a user authentication management module, which is used to limit the legal use of the network by leased line users, and is combined with a broadband access server to achieve one-to-one correspondence between leased line users, IP addresses and time periods; a user account management module, which is used to identify users Effective management of accounts; billing module, used for billing dedicated line users; database, used ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com